The Day after I Blew Off Josh Schulte He Started Deleting “Suspicious Emails”
On the evening of August 13, 2018, Joshua Schulte activated a Samsung phone he had just gotten in a swap with another detainee at Metropolitan Correctional Center.
On August 14, according to a page of his prison notebook introduced at trial, he wrote up the beginnings of his plan for an “information war” conceived — Schulte claimed at trial — after doing some kind of drugs on August 8.
The way is clear. I will setup a wordpress of joshschulte.wordpress.com and presumption of innocence.wordpress.com. From here, I will stage my information war.
“Give me a phone and a blog and I will change the world,” he wrote in the margin of the same page where he planned out how to manage the limited charge time on his phone: “1 charge per day//use from 3-death.”
On August 21, according to another of the pages introduced at trial, Schulte made plans to cover his tracks.
In between those two days, August 14 and August 21, 2018, Schulte, his cellmate, Omar Amanat, and/or Amanat’s brother, Irfan, pitched me via email that Schulte could, “prove to be the most valuable source of information you have ever had.” The day after I declined that offer, Schulte started “delet[ing] suspicious emails.”
At 6:52PM ET on August 14, I received this email from the psalms100@protonmail account. (I’ve replaced the bitly links with direct links indicating the bitly code, but have not fixed typos.)
Hello Marcy : Confidential Intelligence Source
Dear Marcy,
I am writing on behalf of a senior ex NSA/CIA Intellgence officer who spearheaded many of the CIA’s technology hacking and counter-hacking intelligence efforts against state sponsored hackers overseas between 2010-November, 2016. He is currently imprisoned inside MCC (aka Manhattan’s Guantanamo) next to El Chapo and the Chelsea Bomber. He is charged with the largest leak in the history of the CIA: the Vault 7 release to Wikileaks.
The Government does not allow him to electronically communicate with anyone outside the prison via its monitored electronic communication system because he is designated as a “danger to the facility.” Please keep this source confidential as if all goes well you will be able to speak to him and even meet with him in person to corroborate everything I am writing as an approved visitor. We know you disclosed that you revealed another source to the FBI before and that we are therefore taking a huge risk in contacting you. However in your writings and NPR interview we have gleaned that you are a truly thoughtful independent thinker and patriot unafraid to communicate with others if you deem their underlying intentions to be worthy. That is the case with this source, whom you will find to have a pristine moral clarity and intellect -despite the lurid false and totally unsubstantiated accusations against him.
If you protect his confidentiality he will prove to be the most valuable source of information you have ever had.
He has a lot of material information —- never before revealed to the public —-including, but not limited to, Trump principals and agents acquiescence in what’s going on under cover of night with Putin backed Russian Oligarchs —revealing their true agenda. Trumo had a 2 hour dinner at Nobu in Moscow in 2013 with 12 Oligarchs which laid all of this out in advance. These covert efforts are ill understood by media and political hacks but they are actually the single largest threat posed by Putin-backed Russian Cyberhackers on behalf of the Oligarchy : their successful attempts to target second tier—-but highly strategic—- economic assets using an innovative Russian incubated “disruptive business model innovation” they are now exporting to the West called Reiderstvo. See www.reiderstvo.org It is the mechanism that enabled 12 men to end up with 51% of the wealth of one of the wealthiest countries in the world. If it continues unabated it will end with them perpetrating the largest transfer of power and wealth in the history of the world. —via state sponsored legalized theft —-not new value creation and if followed to its logical conclusion the evolution of this virulent “Malware of the Mind” could possibly usher in the decline of western civilization as we know it by rendering the west’s judicial infrastructure and Federal Rules of Evidence completely comprised and ineffectual.
These reids are highly sophisticated legal campaigns that began in 2016 targeting wealthy Clinton backers and they are using President Trump’s own personal lawyer Marc Kasowitz —-who represents Putin’s own bank the largest bank in Russia -Sberbank. [bitly link 2P3oVSd to this NYT story]. Using a Kasowitz division called Intelligence Options which on its website [bitly link 2BafcX6 to Intelligence Options page] brags about its ability to take out business rival targets in highly coordinated efforts involving law enforcement authorities. He can confirm that the Kasowitz firm has been paid “mid 8 figures” by Russian oligarchs close to Putin to implement Reiderstvo targeting American and European citizens who are falsely arrested and their assets seized by the Oligarchs losing billions in the process using (and distorting) the American justice system. And they are just getting started. The Despite the furor over Peter Strzok the FBI itself is compromised by many recent ex Field Agents loyal to Trump working for Kasowitz Intelligence Options division including many who served as personal security guards for him and his family. We have their names.
Inception Hacks
Our ex CIA tech wiz can confirm that they have already used ‘near misses’ in these disinformation campaigns to convince prosecutors, judges and juries that “real info is fake” and have distorted justice in the process. They have developed a lethal technology that is the “nuclear bomb of hacking” that no other state actor has discovered : “Inception Hacking”: is the planting of fabricated emails onto ISP’s without leaving a trace behind. Imagine planting child pornography on an adversary’s computer without him ever knowing or anyone being able to prove it wasn’t his. No network intrusion. No trace.$6-9 billion of value has already been stolen from American citizens and another $150 billion is currently in the targets sights with $1Trillion in transfered assets by 2022 as their stretch goal. The targets of these campaign includes one in jail with the ex NSA/CIA intelligence officer who he met at MCC and whose case study you will find fascinating and disturbing.
Is there a phone number I can call you to discuss? I tried sending to your encrypted email but it doesn’t seem to work from protonmail.
Thanks
Jake
I declined the offer to connect with “the most valuable source of information you have ever had.”
Aside from an email I sent on October 29 after the contraband phones were revealed in a court filing (which went unanswered), our last contact was at at 3:49PM on August 21, the same day Schulte wrote a list of things to do to hide his tracks.
I wasn’t sure whether this pitch came from Schulte and/or someone working with him until the first trial. I’m still not sure who, specifically, sent the email. But evidence submitted at Schulte’s two trials revealed that the pitch used common content and the same email as were used in later efforts using contraband phones. It was Schulte or someone else involved in his efforts to communicate from jail.
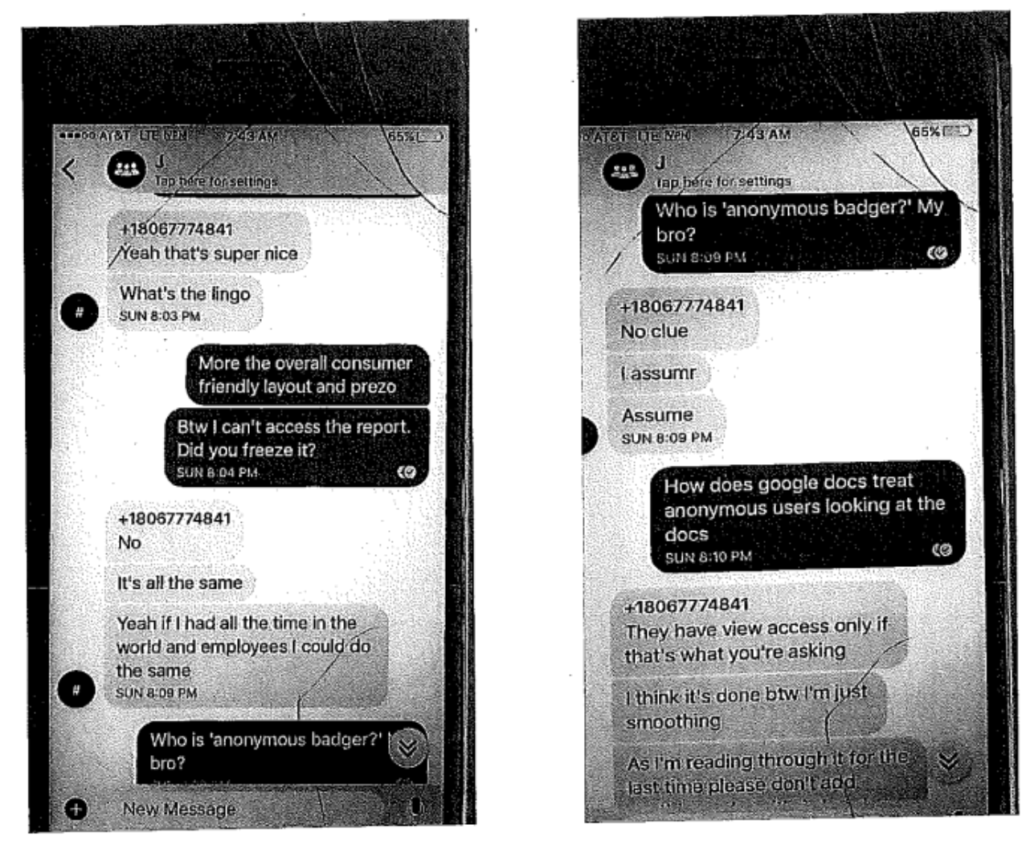
Most notably, the email address — [email protected] — is the same one mentioned in a Signal text sent to Shane Harris about seven weeks later, after Schulte was thrown in SHU on October 1. The text probably reflects Schulte cellmate Omar Amanat’s effort, using Schulte’s Samsung after Amanat’s own iPhone had been seized, to get Harris to move to an account he still had access to.
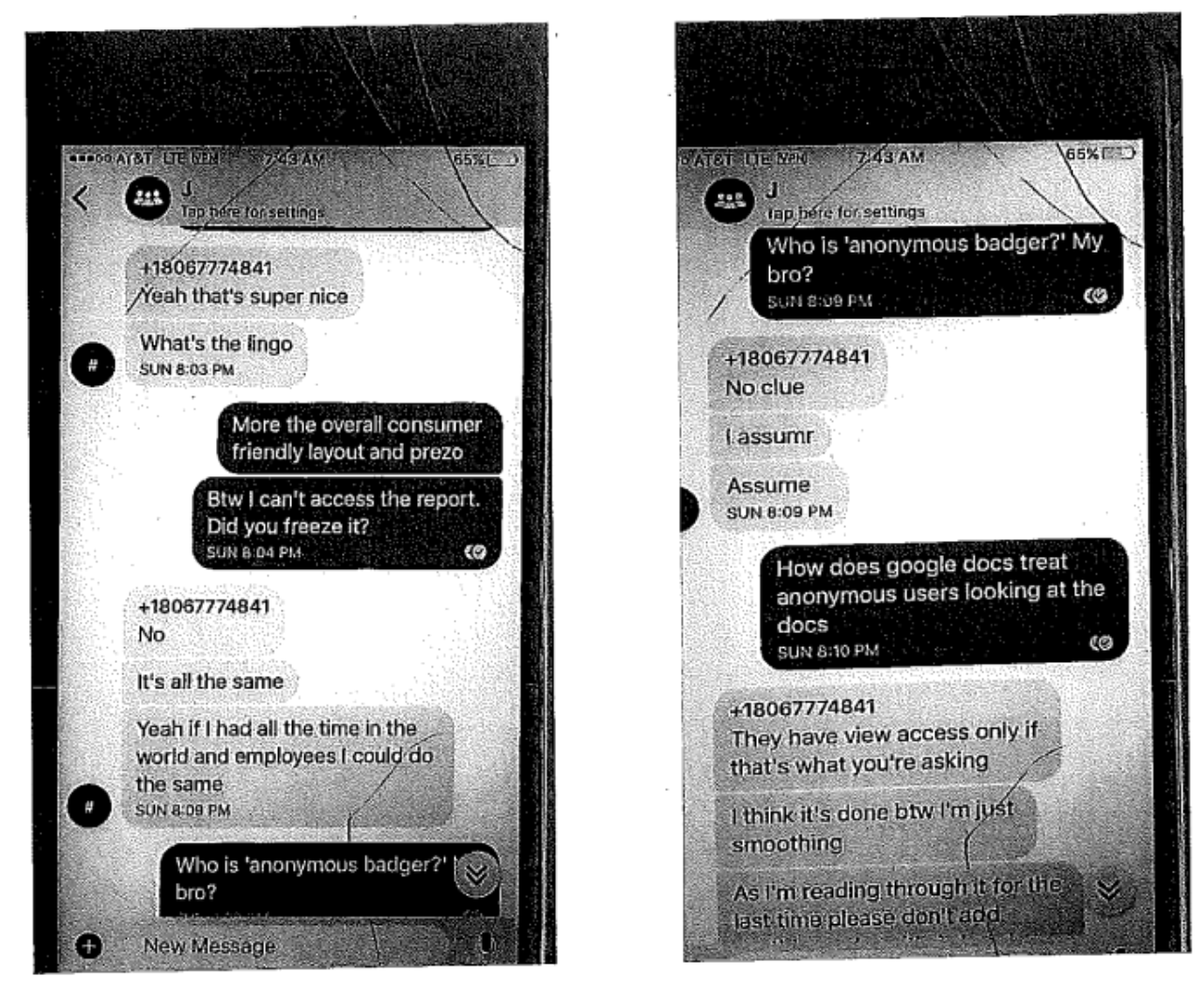
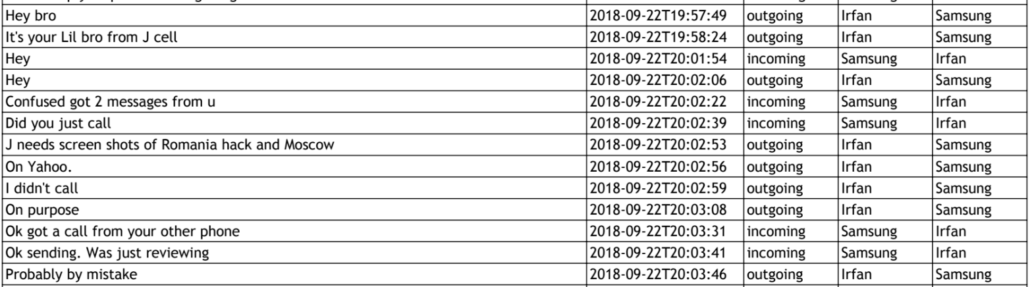
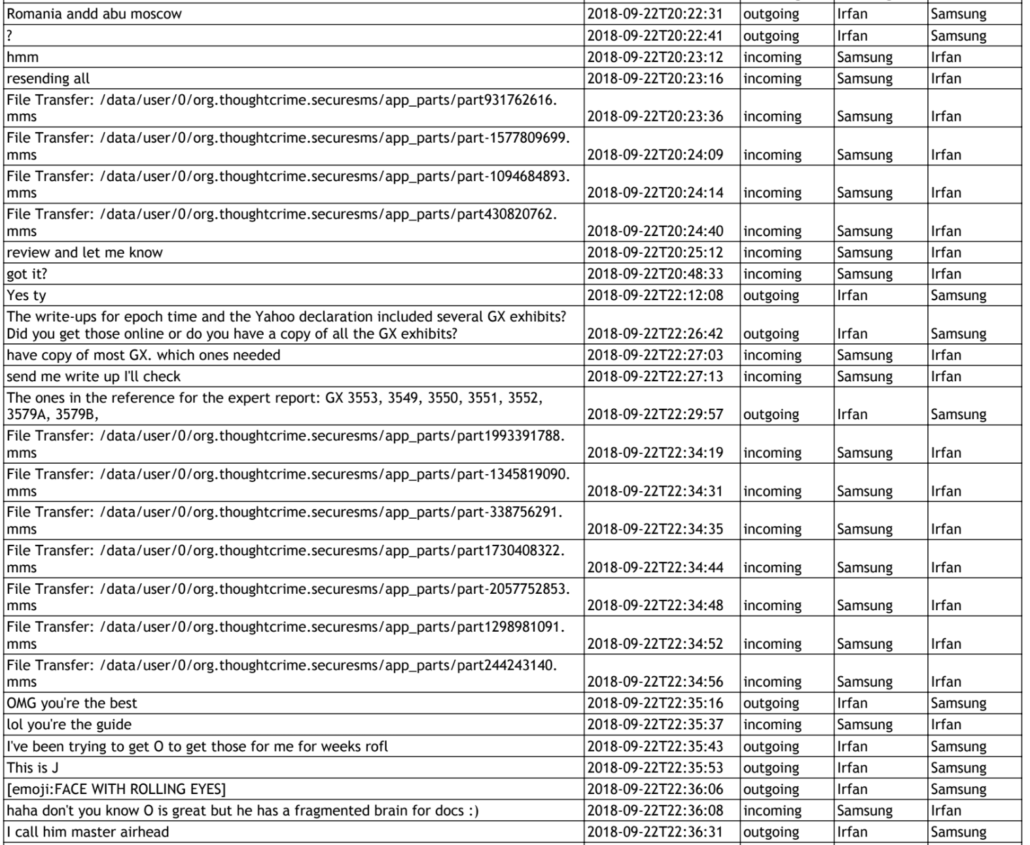
In what follows, I will use the pronoun, “they,” to reflect that the email was, for the reasons I lay out here, probably a collective effort. At least in the case of a very similar email sent to Shane Harris months later, Schulte, Omar, and Irfan Amanat all worked on a common Google Doc, chatting on the side via encrypted texts, to put together the content of the email. Given the similarity between the documents and the use of the common protonmail account, I think it likely that the same happened with the email sent to me.
I’m sharing this now for several reasons. Most notably, I’m intervening in the case in an attempt to liberate a discussion during a sealed CIPA hearing about DOJ’s application of the Espionage Act, and I don’t want DOJ to have any lingering suspicions that I ever pursued a secret back channel with Schulte. I’ve long wanted to be transparent about this, given how closely I have covered the case. But I wanted to wait until after the guilty verdict to avoid contributing in any way to Schulte’s prosecution (I had hoped to wait until his post-trial motions were adjudicated, which is why I didn’t do it during the summer, when I started drafting this post). And for a variety of reasons, the WikiLeaks crowd has belatedly decided to spin Schulte as a hero, so I wanted to explain why I’m so certain he’s a fraud.
I’m sharing it (but not subsequent emails) because I did not agree to confidentiality before they sent it and I’m certain this email and follow-ups are riddled with lies. For example, the claim that this email was sent from a Schulte cousin and their representations about communications in jail almost certainly served to hide the use of a contraband mobile phone to send it. While Schulte’s cousin was involved in contacting other journalists, according to a 2020 FBI interview he did, he only ever used a JohnGalt@protonmail account to do so, and Schulte demonstrably lied to Shane Harris later in the summer about the same cousin.
Court filings give reason to believe Schulte was a liar even before I got this email, but this correspondence is one reason I’m certain he is.
I’m sharing this email, too, because I think the way they pitched this may be of interest for others trying to understand what Schulte was up to. For example, whereas Schulte got WaPo’s Harris to make a series of agreements before sending this Reiderstvo pitch on September 22, 2018, they just gave it to me as the initial dangle. Boom. Here’s the purported good stuff! I regarded it then, as now, as a dangle, an attempt to package up what they imagined I most wanted to hear as a way to get me on the phone. Maybe they tried to raise the value of it with Harris by making it harder to get?
The content of the email sent to me, too, may be of interest. It’s unclear whether and if so how the “Reiderstvo” pitch evolved by the time they prepared to send it to Harris. But as it appears here, it seems, at least in part, a bid to create an alternative narrative that might undermine the viability of the evidence against both Schulte and Amanat. The idea laid out in the “Inception Hacking” passage of the email incorporates alibis that both Schulte and Amanat were offering in their own defense in 2018 (and still, in Schulte’s case): a claim that the FBI fabricated Yahoo emails in Amanat’s case, and a claim that the FBI planted Child Sexual Abuse Material on Schulte’s computer in his case.
The form of the claim capitalized on Schulte’s own hacking expertise.
Here’s how Schulte described that expertise in another document he wrote in jail.
Do you know what my speciality was at the CIA? Do you know what I did for fun? Data hiding and crypto. I designed and wrote software to conceal data in a custom-designed filesystem contained within the drive slackspace or hidden partitions. I disguised data. I split data across files and filesystems to conceal the crypto — analysis tools would NEVER detect random or pseudo-random data indicative of potential crypto.
This was part of the National Defense Information that Schulte was charged and convicted of leaking from jail. So there must be truth to it (to be clear, I have no reason to believe the things in the email to me are true, much less classified).
Significantly, the email sent to me also calls “Inception Hacking,” “Malware of the Mind,” which is the name Schulte gave to that larger document in which he described “disguis[ing] data.”
According to this pitch, the evidence of Schulte and/or Amanat’s guilt was instead proof they were victims of the kind of hack Schulte bragged he could do for the CIA, but here the culprit (in an email to someone they seemed to think would respond enthusiastically) was Russia, not CIA.
Equating Malware of the Mind with Inception in the email sent to me invokes another spy movie, like the Jason Bourne identity Schulte (predictably) adopted as his own, days after this email was sent.
Finally, I’m posting this because of the timing. While I can’t prove this email came from Schulte, as opposed to one of the Amanats or someone else tied to them, during the entirety of the first week Schulte had that Samsung phone, someone was trying to get me on the phone with him, promising that I could speak to him without jailhouse monitors knowing (a claim I found absurd at the time, but which made more sense once I learned of the contraband phones). The day I said, “no,” August 21, Schulte made a list of things to start deleting. The next day, August 22, he renewed his outreach to Harris.
I didn’t then and don’t now know what to make of this. On the one hand, Schulte attempted to speak to a number of journalists who cover this beat; at least five others have been identified in trial exhibits and court filings. In that, there’s nothing special about outreach to me.
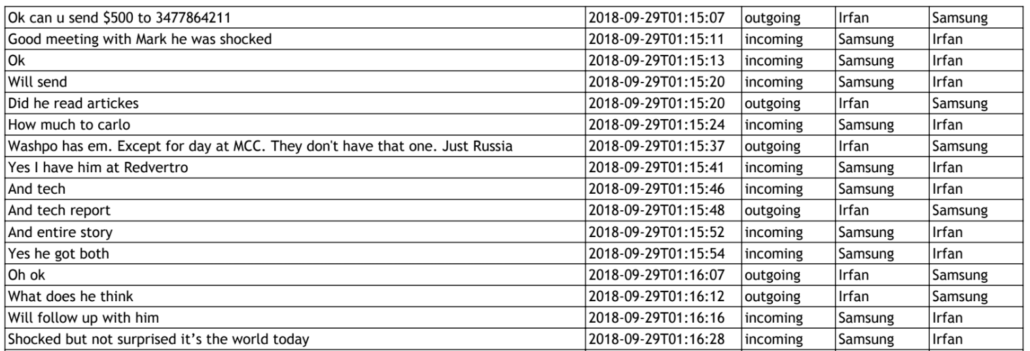
Plus, there’s a perfectly reasonable explanation for why they pitched some journalist at the time. At least according to jail house informant Carlos Betances, Schulte wanted the Samsung because, after someone that Betances believed to be Schulte’s cousin got raided by the FBI, Schulte grew paranoid that the FBI could be monitoring the phones Schulte and his buddies already had.
Q. Mr. Betances, what did the defendant say about why he didn’t want to use iPhones anymore?
A. Because of a conversation in Chino’s cell, he was very scared because his cousin — or, I don’t know who it was. The FBI had gone to that person’s house. They had taken his computer, and since then, he was very scared. So he wanted to replace all phones. He wanted to get all new phone chips, and because of something like that that had happened; he didn’t know what.
[snip]
Q. OK. But that has nothing to do with the FBI or my cousin, right?
A. It does have something to do, because we had that conversation, and you were there.
Q. OK. So when you described me as very scared, what is that based on?
A. Because you said we had to change the phones, we had to change everything. You were freaking out. You were freaked out, in panic mode.
Q. OK. So your description’s not based on the demeanor but based on what you say are requested actions from me, right?
A. I didn’t understand your question. Could you repeat it?
Q. Yes. It wasn’t my outward appearance but what we were discussing that led you to believe I was very scared, right?
MR. LOCKARD: Objection. Form.
THE INTERPRETER: I’m sorry, sir. Did you say something? The interpreter just wants — did you say something at the very end?
MR. SCHULTE: I think there was an objection.
THE COURT: The objection’s overruled.
A. It’s not that you made me believe. It’s the way that you were acting, your outward appearance. You were freaking out.
Q. OK. And what was I scared of?
A. The fact that we had to change our phones, you were pacing back and forth, because the FBI might be listening in on the calls; they might do something. And then, so I asked you why. You know, did you talk to somebody on the phones that we were all using? And that’s when you didn’t answer me. You didn’t say yes or no.
It may not have been his cousin, Shane Presnall, but instead his parents that Schulte was worried about.
DOJ had been ratcheting up pressure on Schulte’s attempts to leak from jail for months by August 2018, when I got this email. In response to journalists publishing information on Schulte’s affidavits in May, DOJ admonished Schulte for violating his protective order. In an attempt to learn how the affidavits had gotten shared, the FBI first interviewed, then served a subpoena on Presnall to appear before the Grand Jury on June 13.
On June 28, Schulte posted a pro se bail application that the CIA claimed included classified information, which led the FBI to ask his parents and attorney in Texas for any classified information, something he repeatedly called a “raid” during the trial.
Then, in early August, Presnall turned over to DOJ another of Schulte’s narratives, which by description may be the one his parents wouldn’t post for him.
On or about August 6, 2018, Presnall, through counsel, produced documents responsive to the subpoena and an index. The index described Articles 1 through 7 by Joshua Schulte, which corresponded to the articles published on the John Galt’s Legal Defense Fund Facebook page in April 2018; as well as an “Article 8 by Joshua Schulte” and the Schulte Article described as “Article entitled ‘. . .unalienable Rights, that among these are Life. Liberty and the pursuit of Happiness’ by Joshua Schulte.” ” (Ex. 4; id. at JAS_021890-JAS_021902). The latter two articles had not yet been published on Facebook. The Schulte Article has four chapter headings, including “Chapter 1: The confrontation,” “Chapter 2: my last experience at the CIA and my reason(s) for resigning,” “Chapter 3: Hell,” and “Chapter 4: The Red Pill.” As with his other articles, the primary thesis of Schulte Article is that the defendant is innocent and he is the victim of lawless, dishonest agents and a criminal justice system uninterested in civil liberties or truth.
As I have noted, this article not only referred to his colleagues whose identities were classified by name, which if published would have exposed their identities, but also described the benefit to Russia that advance access to CIA’s source code would provide. It was a really damning document.
Inexplicably, DOJ did not use it in either of the two trials against Schulte.
The government’s discovery of the materials from Presnall may explain the panic that shows up in Schulte’s notebook in this period, with two notes Schulte wrote reflecting concern that the government had compromised the IMEI numbers for “all 3” phones.
The reference to three phones is probably a reference to the contraband jail phones, but Schulte used three different phones in 2017, after FBI seized a first one, that he would have received discovery on. In any case, DOJ’s increased efforts to crack down on his leaking from jail would have come just as reviewing his own discovery may have led Schulte to belatedly realize the import of the basic investigative tools, such as subpoenas for subscriber records, which the FBI uses to track suspects. That is, at precisely the time he was pursuing a variety of means to leak from jail, Schulte discovered that he hadn’t covered his tracks anywhere nearly as well as he arrogantly believed he had.
So he got a new phone and tried to encrypt everything.
So it would be unsurprising for Schulte, believing his past communications with journalists to have been exposed, to try someone new — me. Then the day after I said no, Schulte turned to reestablish ties with Harris via a new channel and new false identity.
But let’s be honest: it was fucking insane for these guys to do a cold outreach to someone who (as they note!) had only recently publicly confessed to sharing information with the FBI. I’ve never spoken to the FBI about this, but if they did find evidence that Schulte had reached out to me, the outreach would be adjacent enough to the things I did share, it would set off alarms bells all over DOJ. Indeed, there are several non-public details –details that DOJ knows about — that make me uncertain, even today, whether Schulte wasn’t trying something more, and one of those details may have led DOJ to suspect the same.
Plus, Schulte had no reason to believe I’d be receptive to his story. Already, in my coverage of Vault 7, I had made observations — such as that someone may have used CIA’s own hacking tools against it or that Schulte violated release conditions to get back on Tor in the wake of an Assange tweet seeming to use the stolen CIA documents for leverage against Don Jr — that may have been of particular interest to Schulte. But my coverage of Schulte wasn’t particularly sympathetic at all. Even in 2018, Schulte was unlikely to convince me of his lies, and that should have been clear from what I had written.
It’s pretty likely that DOJ did discover traces of this outreach, which is another reason I’m not withholding it. Schulte laid out a plan to delete his Google Docs (given the length of the email and the hotlinks in this email, I assume it was drafted in Google Docs, as the documents later shared with Harris were) the same day I declined this offer, so DOJ may not have the banal content of this email. But even assuming he deleted drafts of this email written collectively on Google Docs, given all the references to other journalists submitted in exhibits and other court filings, I assume references to me would show up in the same places that their names did: in searches conducted using the other phones, in text threads conducted on WhatsApp before Schulte installed Signal, in Schulte’s notebook, in pictures that jailhouse informant Betances took of the phones he tended (by Betances’ description, the email to me was sent before Schulte changed the password to the Samsung). DOJ has a great deal of evidence about Schulte’s actions they didn’t share at trial, and given the timing, much of it would be precisely where any mention of my name would appear.
For example, my name doesn’t show up in unredacted form in what were described as the “Internet searches” done on the Samsung (this is the version introduced at the first trial), though those only start on August 13, by which point whoever sent the email presumably had already gotten contact information for me. But it’s likely it shows up on another phone — perhaps the iPhone that Amanat had been using, or in Google searches (at the first trial the jury got all of Schulte’s Google searches, but the exhibit was not released publicly). Someone went to my website to get both the email addresses I had listed at the time.
Nor does my name appear in the prison notebooks introduced at trial. But there are twenty pages in Schulte’s prison notebooks between the beginning of the August 14 entry and the beginning of the August 21 one, just one of which was included in the trial exhibit. So even assuming the FBI never got into the psalms100 ProtonMail account (something I think is unlikely), they probably learned of the existence of this email via the notebook and searches, and may have gotten the content from Google Docs. So the final reason I’m sharing this is to clarify for anyone at DOJ who might still wonder about this that I said “no” to this outreach. There’s probably nothing in the email Schulte sent me that they didn’t find in other places.
And, yes, whoever sent this really did use “Confidential Intelligence Source” in the subject line of an email sent to a Gmail email, and they really did mention Vault 7 in the first paragraph.
So Schulte and his buddies were not just liars and bad suck-ups, but also stupid.
Again, I had and have no idea what to make of this — though over the course of two trials, how it fits into Schulte’s efforts to work the press in 2018 makes more sense. But at the very least, it hints that there are a lot more things in evidence seized from Schulte’s jail cell that were likely of interest to investigators, but not evidence of a crime.








![[Photo: National Security Agency, Ft. Meade, MD via Wikimedia]](https://www.emptywheel.net/wp-content/uploads/2017/08/NationalSecurityAgency_HQ-FortMeadeMD_Wikimedia.jpg)