
WaPo Gives Bill Barr Platform to Attack Joe Biden without Mentioning Barr's Role in Framing Biden
If you're going to make a big deal about Bill Barr supporting Trump in this year's election, at least mention that the side channel Barr set up for Russian disinformation on Hunter Biden in 2020 ended up framing Joe Biden.

The Varieties Of Activist Judges
The Roberts Court is a mob of judicial activists
Elon Musk's Xitter Stalls a Criminal Investigation, Again
Elon Musk's Xitter is trying to stall DOJ investigations again.

Media Organizations Omit Mention of Trump's Allegedly Criminal Exploitation of 2020 Debates
Twelve media outlets claim that the only way they can display Trump's dystopian vision for America is by being complicit in it, by giving him a platform to stoke violence and frame his opponent.
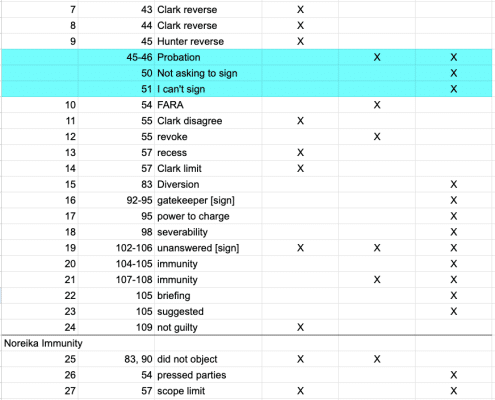
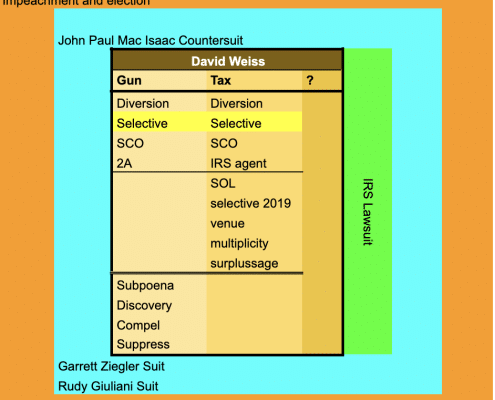
Judge Maryellen Noreika's Unconstitutional Concerns about Unconstitutional Concerns
In an opinion intervening in a diversion agreement between Hunter Biden and David Weiss, Judge Maryellen Noreika ruled that intervening in such decisions would be unconstitutional.
Alexander Smirnov Goes Missing -- from Judge Noreika's Opinions
Even though Judge Noreika observed that Leo Wise appeared to revoke the deal it offered Hunter Biden when he insisted on the terms of immunity he had been promised, Noreika ignored Alexander Smirnov's role in that process.

Fridays with Nicole Sandler
We spoke about Trump's imminent trial and other developments.

Judge Maryellen Noreika Confuses Hunter Biden's Memoir for the NYPost
Yet another participant in the Hunter Biden cases has made false claims about what's in his memoir. This time, Judge Noreika did so in her opinion denying Hunter's motion to dismiss.

Walt Nauta Claimed Trump Hoarded Hairspray Cans in His Storage Rooms
In his FBI interview, Walt Nauta claimed that Trump's storage rooms were fully of hairspray cans.
Leo Wise Has a Sex Worker [and Other False Statement] Problem
David Weiss' team, like Joseph Ziegler before them, keeps seeing sex workers where there were none.

Three Things: No News Isn’t Good News
U.S. media, Congress, and the citizens who elected them own some of the media fail. Why aren’t we demanding more protection of our personal data in order to protect our democracy?

emptywheel Makes CIPA History
Judge Jesse Furman has used my intervention as an excuse to order the government to release redacted transcripts of a CIPA conference from the Josh Schulte case.

Mr. Smith Goes to SCOTUS
Jack Smith submitted his brief responding to Trump's immunity claims to SCOTUS.

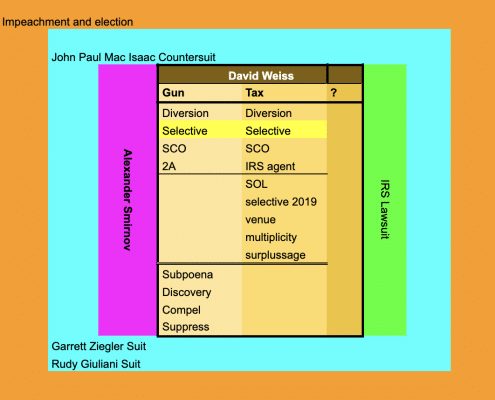
How Mark Scarsi Post Hoc Dismantled Abbe Lowell's Juicy Timeline
Mark Scarsi is an admirably meticulous judge. But in key areas of his opinion rejecting Hunter Biden's motions to dismiss, his failure to meet his own rigorous standards may make the decision more vulnerable on appeal.

Fridays with Nicole Sandler
We talk a lot about Aileen Cannon. And other stuff.
Maryellen Noreika and Mark Scarsi's Schrödinger's Cat
Judge Maryellen Noreika's role in determining the status of the immunity agreement signed by Hunter Biden is quite different than Judge Mark Scarsi. That's because after she, as a non-party to it, inquired into the already-signed contract, it led the contract to become a non-contract.

Bullshit and Also, Aileen Cannon, Post
My potty mouth has gone big time.

The Import of Judge Mark Scarsi's Truncated Klamath Quote
Both David Weiss and Judge Mark Scarsi relied on 9th Circuit precedent that says if the terms of the Hunter Biden diversion agreement are susceptible to different interpretations, then it is ambiguous and Hunter Biden's understanding of the agreement must hold.
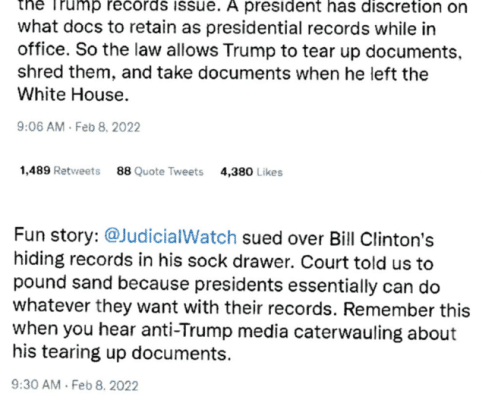
Jack Smith to Aileen Cannon: Treating Non-Lawyer Tom Fitton's Theories as Law Will Lead to Mandamus
Jack Smith has now formally informed Judge Aillen Cannon that she has been chasing a whack theory spun up by someone, Tom Fitton, who doesn't even have a JD.

Judge Mark Scarsi's Quantum Theory of Murdered Contract Law
Even Judge Mark Scarsi used a metaphor -- Schrödinger's cat -- intended to convey absurdity to describe his interpretation of Hunter Biden's diversion agreement.

