Password: 0sbP@ss
Remember how infosec people made fun of John Podesta when they learned his iCloud password — which got exposed in the Wikileaks dump of his stolen emails — was Runner4567? 4Chan used the password to hack a bunch of Podesta’s accounts.
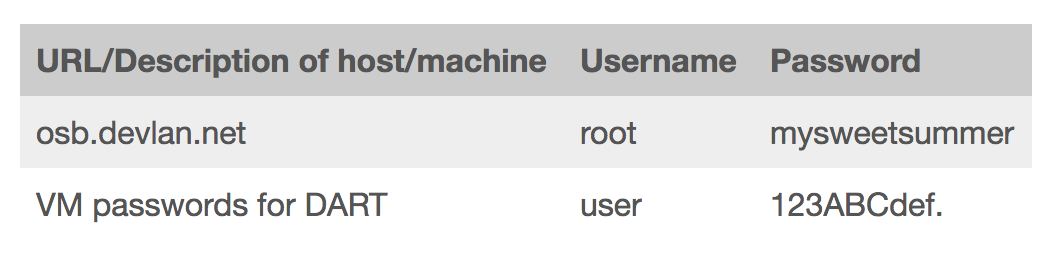
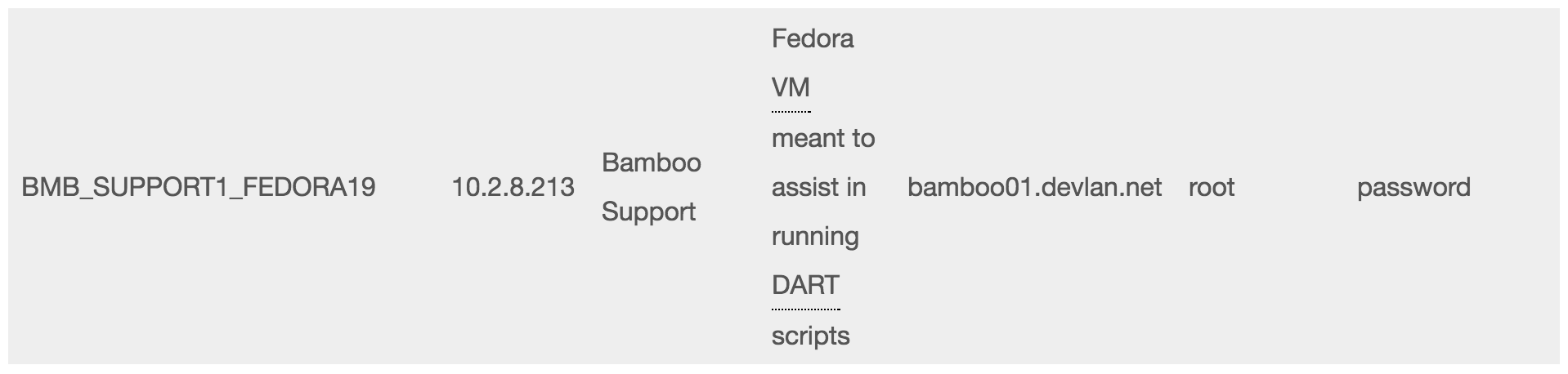
Among the pages that got exposed in this week’s Wikileaks dumps of CIA’s hacking tools was a page of Operational Support Branch passwords. For some time the page showed the root password for the network they used for development purposes.
These passwords, as well as one (“password”) for another part of their server, were available on the network site as well.
Throughout the period of updates, it included a meme joking about setting your password to Incorrect.
At the beginning of January 2015, it included the passwords for two unclassified laptops used by the department, one of which was the very guessable 0sbP@ass.
OSB unclass laptop #1 password (tag 2005K676, Dell service tag: 7731Y32): “OSBDemoLap9W53!” (Without quotes)
OSB unclass laptop #2 password (tag 2005K677, Dell service tag: CN81Y32): “0sbP@ss” (no quotes, first chracter is a zero)
Remember, Assange has claimed that CIA treated its exploits as unclassified so they could be spread outside of CIA facilities.
A discussion ensued about what a bad security practice this was.
2015-01-30 14:30 [User #14588054]:
Am I the only one who looked at this page and thought, “I wonder if security would have a heart attack if they saw this.”?
2015-01-30 14:50 [User #7995631]:
Its locked down to the OSB group… idk if that helps.
2015-01-30 15:10 [User #14588054]:
I noticed, but I still cringed when I first saw the page.
I have no idea whether these passwords exacerbated CIA’s exposure. The early 2015 discussion happened well before — at least as we currently understand it — the compromise that led to Wikileaks’ obtaining the files. The laptops themselves were unclassified, and would only be a problem if someone got physical custody of them. Though shared devices like laptops were one of the things for which CIA had a multi-factor authentication problem up until at least August of 2016.
But if we’re going to make fun of John Podesta for password hygiene exposed in a Wikileaks dump, we ought to at least acknowledge that CIA’s hackers, people who spent their days exploiting hygiene sloppiness like this, had (simple) passwords lying around on a server that — as it turns out — was nowhere near as secure as it needed to be.





quote “….people who spent their days exploiting hygiene sloppiness like this, had (simple) passwords lying around on a server that — as it turns out — was nowhere near as secure as it needed to be.”unquote
Call me conspiracy nut, but it seems too obvious to me. For some reason… maybe CIA *wanted* it that way. I mean, *disinformation* in some form, or code, malware or whatever?. On the other hand.. *DANGER Will Robinson!! DANGER! Brainfart alert!”
https://www.youtube.com/watch?v=V3FnpaWQJO0
crap. The functions on this comment section completely baffle me. One moment things work as expected.. the next they don’t. If I had deep pockets I’d donate to fix them. Alas..
note to self : deal with it.
(Cue Music) “It’s simple as ABC, 123, Baby you and Me!”
Unsecured, Personal Lap Tops so they can…
Whatever could go wrong? Oh, Yeah. Lions, Tigers, and Bears. Oh, My!
They obviously do not (or at best, did not) care about basic Operational Security. To joke about setting a password to INCORRECT says they either knew that basic password security was a waste of time due to use of Intel machines with ME or because they had to document the passwords via insecure means.
Just a note on the meme: it is very lame.
Note they were using a Fedora VM. Any *nix machine will never tell an attacker that the password is incorrect. It will tell you that username or password is incorrect. That is intentional so that an attacker can not glean that they have a valid username.
Also note that all *nix boxes have a root username. All attackers know it exists.
This us why you never allow remote logins to root. The attacker just keeps trying username of root and guessing passwords. These brute-force attacks happen constantly every second.
The way to attempt to thwart attackers is to make the legit users login via a non-root username first. Then they can become root as a second authentication via login or su.
“Also note that all *nix boxes have a root username. All attackers know it exists.”
Technically true, in practice, ehh. For some time now, the standard approach for the root account (on multi-user boxes) is to have it turned off by default and then someone with admin privileges has to turn it on. Additionally, (part of the ‘good’ practices bit) it only gets turned on for limited circumstances and then is turned back off, as well as limiting those users listed in the su doers file since su -s is only one small step below root. These may seem like distinctions without differences because in-real-life rarely resembles ‘good practices’, but it is an attempt to take away the low hanging fruit.
Maybe folks will start taking file level and application level types of encryption more seriously.
SELinux is security theatre.
It *may* help in a large multi-user environment with a sufficient number of naive users, but ultimately it is just security theatre.
Think wrapping a lot of gauze over a bandaid that will not stop the bleeding from a bad cut.
It will hide the bleeding for a while, but then it will become obvious that it is time for stitches.
I told you so.
https://www.emptywheel.net/2017/03/08/cia-did-not-have-multi-factor-authentication-controls-for-all-users-as-recently-as-august-2016/#comment-711626
Not even on a post-it. Worse!
Vindicated! For sure.
I’m reading a novel that posits some CIA operatives as being basically solders who murder on command. Is that accurate?
Why would you believe that to not be the case?
Marcy, I don’t think i’ve ever felt such despair over the totality of this decade:
• Obama continued Bush-era spying.
• Snowden wanted a national conversation — we never got it. Though there was initial media attention, turned out Americans preferred the spying to substantive discussion on privacy, freedom, whistleblowing.
• Hard to know what drives Julian Assange & wikileaks — initially both seemed heroic to me.
• Post-election analyses of most Americans getting news from facebook, the rise of fake news; worse, the now labeling of anything as fake news
• Russian involvement mysteries and lack of definitive anything; and if yes team Trump had any form of collusion, Apple-pie America doesn’t even care
• Twitter culture’s mob-escalations, insta-memes, lefty snobs
• reddit superiority syndrome, lulz fueled bastions like 4chan
Very hard to feel we are progressing — communication is deteriorating, not improving.
Even Tim Berners-Lee is aghast over what has become of the internet.
( http://www.usatoday.com/story/tech/news/2017/03/11/world-wide-webs-inventor-warns-s-peril/99005906/ )
I’ve looked to people like you for grounding.
CIA best practices doc. It is really all common sense stuff if you are the attacker.
Any real programmer knows tbis stuff, and there are millions around the world that will just nod their head over and over reading this.
A couple of items caught my eye. See below.
Note this doc is classified s/nf. (at this point, the secret/noforn is useless). Still no ts/ stuff yet, but suspect there will be later after they have time to redact properly, which I believe they will. Mike Morell says it came from a TS network, so must suspect more exploits will be leaked or discovered.
Which really makes one wonder why the passwords were not better secured.
https://www.wikileaks.org/ciav7p1/cms/page_14587109.html#efmAQ6AR7AYlAZXA-VBBJBBSBCQBCbBExBHXBKGBv9Bw9ByBBy-Bz2B0OB02B1yB8mB9jCQZCR1CSmCTR
” DO NOT leave data in a binary file that demonstrates CIA, USG, or its witting partner companies involvement in the creation or use of the binary/tool.”
[Witting partner]
(U//FOUO) DO use end-to-end encryption for all network communications.
NEVER use networking protocols which break the end-to-end principle with respect to encryption of payloads.”
“(S//NF) DO NOT solely rely on SSL/TLS to secure data in transit.”
“(S//NF) DO use ITEF RFC compliant network protocols as a blending layer. The actual data, which must be encrypted in transit across the network, should be tunneled through a well known and standardized protocol (e.g. HTTPS)”
“(S//NF) DO NOT break compliance of an RFC protocol that is being used as a blending layer.
(i.e. Wireshark should not flag the traffic as being broken or mangled)”
[Note to Comey: Do you understand the ‘going dark’ problem now? The CIA is practicing that NOW. They are double encrypting, tunneling encrypted traffic inside what appears to be ‘normal’ ssl/tls encrypted traffic. Who knew? Me. Always did because I am convinced RSA is broken. And if CIA is doing this double encryption, they obviously do not trust RSA either. They just want their traffic to blend in.]
SLF, much appreciated.
I did find a TS PDF in there today.
Hopefully you used Foxit instead of Adobe.
Else, you need to look at some serious scrubbing. Adobe is probably one of the ‘witting partners’ along with Microsoft.
Anything ‘leaked’ should only be opened on a throw-away machine that is not connected to the internet. And I literally mean throw away.
If on net, a persistent rootkit could get installed into such a low level that you can no longer trust the machine. Especially if you ever reconnect it to the internet. Seriously, it is no longer trustable and should be discarded (or used as a honeypot on a different subnet).
Re-installing the OS from scratch does not mean it is safe to use. Even if it was Windows out of box (extremely likely), and you then install Linux, you still can not trust the machine.
https://null-byte.wonderhowto.com/how-to/hack-like-pro-embed-backdoor-connection-innocent-looking-pdf-0140942/
https://www.offensive-security.com/metasploit-unleashed/client-side-exploits/
One more very important note that applies to anyone that gets a new computer but you want to run linux anyway:
Never ever let it go through first boot into Windows. Never.
You need to research from another computer how to get into the BIOS/EFI for that specfic machine. You need to plan. You need to know how to boot from your linux install media (Floppy, CD/DVD, USB, PXE) *INSTEAD* of booting from harddrive!
It is important that you never let Windows load. Even ONCE.
So, you must research the distro, the media, the BIOS/EFI setup and hopefully someone has been through the process before so you can avoid that first boot that you do not want.
The reason I say this is because of ASL/AML (ACPI) and that Microsoft always had their own ASL compiler instead of using the reference compiler from Intel. And for years now, flashing (updating) your BIOS/EFI firmware has been doable from *within* a windows environment, as opposed to the good old days where you had to boot from floppy and possibly change a jumper on the motherboard before you could update the boot firmware (BIOS).
So, because Windows and the motherboard manufacturers have been in bed, Windows has been given the priviledge to update the firmware without your explicit control (having to fash from standalone bootable media and possibly having to set the jumper on the mothetboard).
For these reasons, I highly recommend that you never boot Windows in the first place, as a firmware backdoor can be installed on first boot.
Note that the motherboard manufacturer can plead complete ignorance after the fact.
http://www.acpi.info/toolkit.htm
https://www.acpica.org
Did you find any of the photos from the ‘microwaves turned into cameras’? :)
It helps to not confuse unix systems with unix-like systems (such as linux). These may clear some things up — or not:
1) https://en.wikipedia.org/wiki/OpenBSD_security_features
2) http://www.makeuseof.com/tag/linux-vs-bsd-which-should-you-use/
TL;DR
Yes, I know the differences. Almost certainly, I have used all various *nixes.
Did you ever program on a 3B2?
Did you know that original 5ESS telephone switches were basically a bunch of 3B2 processors?
Ever been to Bellcore?
Do you know what x.25 is?
Ever seen yellow punched paper tape?
How about a Hollerith card?
Remember the days when it was posited that you could never transmit more than 9600 baud over a pair of copper wires?
Ever heard of RatFor?
Know the difference between EBCDIC and ASCII?
Ever build a system to transfer files between an IBM mainframe (EBCDIC) and a Tandem Guardian machine (ASCII) *BEFORE* FTP even existed? And do the translations?
Ever patched an OS kernel without the source code and create functionality where there was none? Without any branch instructions?
Ever found bugs in microcode?
Ever programmed a telephone switch?
Ever written code to emulate a human programming a telephone switch?
Ever heard of SystemX?
Trust me, SELinux is security theatre.
Yes sweetie. You left out knowing the differences between AIX and BSD. I started on an IMSAI-8080. Everything else in lists like this one are just old folks shaking their whatever at the sky and muttering ’bout back in the day.
SELinux is not the topic. Try to pay attention.
You are the one not paying attention.
HTH. HAND.
I was in chief of infosec for a SIGINT facility where multiple agencies worked together. I actively enforced a strong passwords and systematic change of passwords, especially since we had many contractors in and out of the site. Every week or so I’d capture some passwords on a network, so I could do what I called “a health and safety check”. When I found accounts with bad passwords, I would quietly talk to the offenders and help them come up with personal algorithms for creating new passwords.
One week I picked up the CoF’s password and saw that it was “87654321”. She was from Langley and on her last tour before retirement. I was gobsmacked by her poor choice and went to talk with her about it. She defended her use of that particular password by explaining by saying “That password is so easy, no one would expect me to use it!” She was quite pleased with herself for being so ingenious. I told her that I would lock her account and she said, “You can’t do that! I use that password for everything!” So, I asked her which bank she used, and she told me. (Apparently she had no idea what I had implied with that request.) So, yes, I went online and tried to access her account. Voila. Same name; same password. When I locked her out at work, I was threatened by her. My chief said to complain and run it up the chain. A week later, a virus from the Internet found its way into a host of TS networks.
Long story, short: I went up the chain, which led to nothing being done. Each of the higher-ups I spoke with said her infraction wasn’t really a problem, and each one admitted to basically doing the same thing. They pay lip service to infosec, but they really don’t like to be bothered with it; they think it’s a stupid thing to spend money on.
I told my bosses that we wouldn’t know if China or Russia had ever been in our networks because we simply didn’t have the staff or equipment for proper intrusion detection. They scoffed and said that no one could ever “find” our networks because they’re dark, etc. I warned them not to be so comfortable with that fact. Now I wonder if many of our C&C networks have been compromised.
I told her that I would lock her account and she said, “You can’t do that! I use that password for everything!”
[If so, she should not be working for IC. Period. But, yes you can do that as you did, and poor dear, get her a fainting couch, for she may have to remember more than one password]
So, I asked her which bank she used, and she told me. (Apparently she had no idea what I had implied with that request.)
[Definitely not a person I would have in IC, never to ever hired by me. You just social-engineered her. She should know better. If she is near retirement, and does not understand by now, working for IC, well wow. Just wow.]
So, yes, I went online and tried to access her account. Voila. Same name; same password.
[Again, just wow. She definitely should know better than to use the same passwords across sites. Even if she did, you can’t use an easily guessable password on a banking site]
A week later, a virus from the Internet found its way into a host of TS networks.
[Ever consider that event could have been *your* fault?]