I Con the Record Transparency Bingo (3): CIA Continues to Hide Its US Person Network Analysis
As I noted in this post on the single positive hit in a criminal back door 702 search and this post on the inexplicable drop in PRTT numbers, I’m going to clarify things I’m seeing confusion over in the I Con the Record Transparency Report, then do a full working thread.
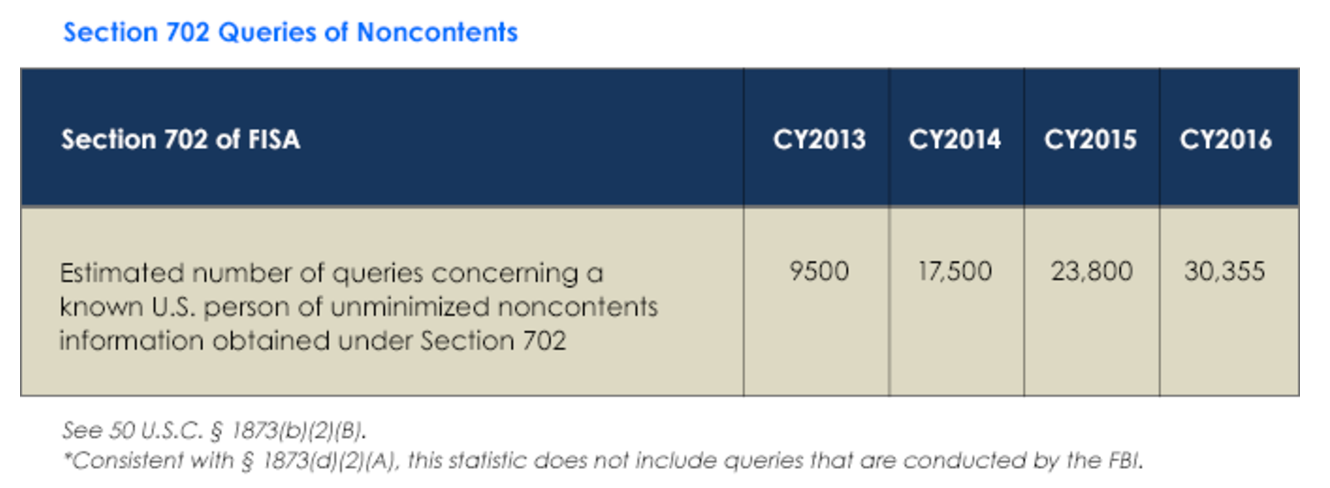
This year’s report shows a steady increase in the number of metadata searches in raw Section 702 data, a 22% (6,555 query) increase off year.
The graphic admits that these 30,355 queries don’t include the FBI (because the transparency procedures passed by USAF freedom pretty much exempted FBI from everything important). But then further down in the written text, I Con the Record admits that one agency of the IC could not estimate its metadata queries.
As with last year’s transparency report, one IC element remains currently unable to provide the number of queries using U.S. person identifiers of unminimized Section 702 non-content information.
That Agency is the CIA, not the FBI (which isn’t required to count its queries).
We know this from a number of places, including James Clapper’s original report on back door searches to Ron Wyden and the PCLOB 702 report (page 58). PCLOB’s most recent Recommendations update noted that CIA hasn’t implemented the recommendation to track foreign intelligence purpose for queries because it has not yet updated its data management. Nor do ODNI and DOJ review it.
The status of the CIA metadata queries remains the same as reported in the Board’s Recommendations Assessment Report of January 2015, namely with respect to the CIA’s metadata queries using U.S. person identifiers, the CIA accepted and plans to implement this recommendation as it refines internal processes for data management. Thus, the CIA’s new minimization procedures do not reflect changes to implement this recommendation with regard to metadata queries.
[snip]
U.S. person queries by the NSA and CIA are already subject to rigorous executive branch oversight (with the exception of metadata queries at the CIA), supplying this additional information to the FISC could help guide the court by highlighting whether the minimization procedures are being followed and whether changes to those procedures are needed.
CiA’s metadata-only repository does not have the capacity for documenting why the query is reasonably likely to provide foreign intelligence information. Upon opening the repository, however, users will be met with a pop-up reiterating the query standard and requiring their assent before they may proceed.
I officially bet a quarter that CIA will find a way to count this next year, as by then, many of these queries will have moved to EO 12333 querying, which does not get counted.
So the report on metadata searches only shows what NSA does. Since last year, we have confirmed that these metadata queries include upstream 702 data, which carry their own risks.
And we also now have a sense that those queries are automated. The I Con the Record report explains this is just a good faith effort.
The above is a good faith estimate of the number of queries concerning a known U.S. person that the government conducted of unminimized (i.e., raw) lawfully acquired Section 702 metadata.
That’s because this is done by algorithm and business rule, not by any kind of tracking (I’m guessing because of the way metadata is used to triage newly collected identifiers).
NSA will rely on an algorithm and/or a business rule to identify queries of communications metadata derived from the FAA 702 [redacted] and telephony collection that start with a United States person identifier. Neither method will identify those queries that start with a United States person identifier with 100 percent accuracy.
The privacy community made great celebration about shutting down a phone dragnet that was just used to query 200 or so selectors. Meanwhile, each year the NSA, alone, conducts thousands more such queries (and in a way that likely ties more closely to content searches). And 3 years after people started pressuring it to do so, CIA still doesn’t count how many queries it is doing.
Which likely means CIA is doing a whole bunch of network analysis on US persons that it doesn’t want us to know about.





OT?: SS7 hack
1. 2016-05-12 – Gee, what could go wrong?
http://www.bankingtech.com/490652/fidor-bank-and-telefonica-germany-to-launch-o2s-first-mobile-bank-account/
Telefónica Germany, in association with Fidor Bank, will be launching its mobile banking offering, “O2 Banking”, in Germany in late summer 2016.
Matthias Kröner, CEO of Fidor Bank, says the collaboration offers “the best of two digital worlds”. Namely, banking services via a mobile app and additional services from an O2 mobile contract.
Fidor says it will take a “few minutes” to open an O2 bank account – and it’s all done online.
The identity check is via a video link using a smartphone. To transfer money, customers have to enter the mobile phone number of the recipient in the address book and select it for a transaction.
2. 2017-05-03 – The SS7 hack is discovered
http://www.telespiegel.de/news/17/0305-ss7-hack-bankkonten.html
[Translate to english via google]
For several years, a hack has been known in the mobile radio system, which, among other things, has a considerable impact on the security of online banking. This makes possible a gap in SS7 , which is still not closed. Now criminals have apparently succeeded in exploiting this vulnerability and accessing bank accounts from O2 customers. According to a report from the Süddeutsche Zeitung, the mobile phone company confirmed this. Details of the number of victims or damage are not public.
OT: Another SS7 hack
http://www.worldtechgo.com/hack-facebook-account-2017-via-ss7-network/
The hackers uses SS7 flaw to spoof the victim to fool the network. Once the network is fooled, the hacker uses the Facebook’s “Forgot Account?” link on homepage of facebook.
The Hacker also fools the Facebook by making it believe that he is the real owner of that facebook account. So the facebook sends the verification code to the mobile no. of the user but what happens is that instead of sending the code to mobile phone it reaches to SS7 network. Now the hacker can use that code to change the password and login to the victim account.