Why Did Tom Bossert Claim WannaCry Was Spread Via Phishing?
Writing this post made me look more closely at what Trump’s Homeland Security Czar Tom Bossert said in a briefing on WannaCry on Monday, May 15.
He claimed, having just gotten off the phone with his British counterpart and in spite of evidence to the contrary, that there had been minimal disruption to care in Britain’s DHS.
The UK National Health Care Service announced 48 of its organizations were affected, and that resulted in inaccessible computers and telephone service, but an extremely minimal effect on disruption to patient care.
[snip]
And from the British perspective, I thought it was important to pass along from them two points — one, that they thought it was an extremely small number of patients that might have been inconvenienced and not necessarily a disruption to their clinical care, as opposed to their administrative processes. And two, that they felt that some of those reports might have been misstated or overblown given how they had gotten themselves into a position of patching.
Of course, this may be an issue in the upcoming election, so I can see why Theresa May’s government might want to downplay any impact on patient care, especially since the Tories have long been ignoring IT problems at DHS.
He dodged a follow-up question about whether there might be more tools in the Shadow Brokers haul that would lead to similar attacks in the future, by pointing to our Vulnerabilities Equities Process.
Q I guess a shorter way to put it would be is there more out there that you’re worried about that would lead to more attacks in the future?
MR. BOSSERT: I actually think that the United States, more than probably any other country, is extremely careful with their processes about how they handle any vulnerabilities that they’re aware of. That’s something that we do when we know of the vulnerability, not when we know we lost a vulnerability. I think that’s a key distinction between us and other countries — and other adversaries that don’t provide any such consideration to their people, customers, or industry.
Obviously, the VEP did not prevent this attack. More importantly, someone in government really needs to start answering what the NSA and CIA (and FBI, if it ever happens) do when their hacking tools get stolen, an issue which Bossert totally ignored.
But I’m most interested in something Bossert said during the original exchange on NSA’s role in all this.
Q So this is one episode of malware or ransomware. Do you know from the documents and the cyber hacking tools that were stolen from NSA if there are potentially more out there?
MR. BOSSERT: So there’s a little bit of a double question there. Part of that has to do with the underlying vulnerability exploit here used. I think if I could, I’d rather, instead of directly answering that, and can’t speak to how we do or don’t do our business as a government in that regard, I’d like to instead point out that this was a vulnerability exploit as one part of a much larger tool that was put together by the culpable parties and not by the U.S. government.
So this was not a tool developed by the NSA to hold ransom data. This was a tool developed by culpable parties, potentially criminals of foreign nation states, that was put together in such a way so to deliver it with phishing emails, put it into embedded documents, and cause an infection in encryption and locking. [my emphasis]
Three days into the WannaCry attack, having spent the weekend consulting with DHS and NSA, Bossert asserted that WannaCry was spread via phishing.
That is a claim that was reported in the press. But even by Monday, I was seeing security researchers persistently question the claim. Over and over they kept looking and failing to find any infections via phishing. And I had already seen several demonstrations showing it didn’t spread via phishing.
Now, Bossert is one of the grown-ups in the Trump Administration. His appointment — and the cybersecurity policy continuity with Obama’s policy — was regarded with relief when it was made, as laid out in this Wired profile.
“People that follow cybersecurity issues will be happy that Tom is involved in those discussions as one of the reasoned voices,” Healey says.
“Frankly, he’s an unusual figure in this White House. He’s not a Bannon. He’s not even a Priebus,” says one former senior Obama administration official who asked to remain unnamed, contrasting Bossert with Trump’s top advisers Stephen Bannon and Reince Priebus. “He has a lot of credibility. He’s very straightforward and level-headed.”
And (as the rest of the profile makes clear) he does know cybersecurity.
So I’m wondering why Bossert was stating that this attack spread by phishing at a time when open source investigation had already largely undermined that hasty claim.
There are at least three possibilities. Perhaps Bossert simply mistated here, accidentally blaming the vector we’ve grown used to blaming. Possibly (though this would be shocking) the best SIGINT agency in the world still hadn’t figured out what a bunch of people on Twitter already had.
Or, perhaps there were some phished infections, which quickly got flooded as the infection spread via SMB. Though that’s unlikely, because the certainty that it didn’t spread via email has only grown since Monday.
So assuming Bossert was, in fact, incorrect when he made this claim, why did have this faulty information?




The malware exploit is alleged to have had two components: an initial delivery by a phishing email with a compromised message, which then acts on a vulnerable computer and starts pushing the second vector through SMB. NHS or any of the major organizations in Europe hit by the malware should have the ability to do the forensics on email traffic and port 445 traffic.
Actually, no one believes that anymore. See this piece, linked in the post.
(Just lost a comment I wrote in reply. That will teach me not to draft outside the box, so to speak.)
I read so much about WannaCry this week that I can’t recall now where I read a refutation that NHS was hit by phishing email. “They don’t click on links,” or something to that effect, which on the face of it seems like braggadocio. But it was obvious to the infosec community late in the day on 12-MAY this was not email dispersion; the vector was something more like a worm. The way WannaCry ripped through Telefonica and at least two other telecoms suggests it was built to follow communications systems, and perhaps the use of a vulnerability affecting Win Server 2003 and 2008 worked that end. It focused on systems that were up 7/24/365 with larger numbers of users and not individuals’ PCs.
What I have yet to run across is a report indicating location of the infection’s Patient Zero. Neither the Malwarebytes’ report nor the subsequent Wired mag report noted it. Was there someone who got what might have been the one and only phishing email? In which case Bossert’s comment about phishing email wouldn’t be absolutely wrong, just off by number. And maybe his reference to phishing emails wasn’t an error but obfuscation. Because if Patient Zero didn’t get a phishing email, how did the first infection receive an injection?
Did you watch the Malwarebytes’ heat map? I find it odd their report doesn’t clearly callout the first observed cluster of detections —
a quick seven cases[1] — occurred in a quaint small city located on the Volga River. The second cluster of four cases was in the heart of Ukraine; among the next clusters is Moscow, and the heat map explodes after that. Let’s keep in mind WannaCry hit ~1,000 machines across Russia, including the ministry of internal affairs.Perhaps WannaCry’s dispersion tells the real story of its purpose — tracing a route. It certainly isn’t a very effective get-rich-quick scheme.
UPDATE: 6:09 pm EDT — Hah! Must be slower-witted than usual; it just occurred to me why anyone connected to NHS would be confident “they don’t click on links.” Because the UK’s government hoovers up all internet traffic, that’s why. Any click on a link would be monitored. Creeptastic assurance of conformance with safe internet surfing!
UPDATE: 6:30 pm EDT — [1] Correction – I thought it read ‘cases’, now I’m not certain if it’s ‘cities’ due to the crappy resolution. If it’s cities, it’s possible Patient Zero may not be in the cluster located on the Volga, but the heat map suggests the cluster is still the location of the first infection. Screenshot so you see what I see:
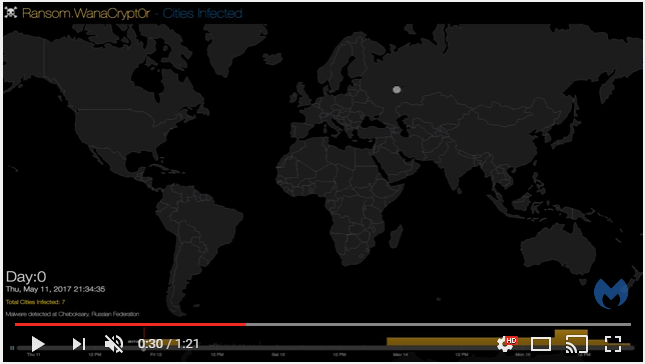
It is, well, all phishy. As in misdirection.
Look at who is his boss.
Why did he also say that US Government systems were largely NOT impacted?
Is he implying that all US government workers are all educated now and will not bite on a phishing email?
Riiight. Even Comey did.
No, there has to be another exploit (I have my theory), that was used to implant Wannacry before 2017-05-12. It was laying in wait.