Could Roger Stone Be Charged in a CFAA Conspiracy?
I just did an extended rant on Twitter about Jonathan Chait’s latest attempt to pretend to be covering the Russian investigation. Basically, though, I was making the same point I made in this post: Mueller is not going to charge Roger Stone just for talking to WikiLeaks — or even having advance knowledge about what WikiLeaks planned to do. So to try to understand what Mueller is after, you need more than a Chait-like titillation that Stone exchanged some DMs with Guccifer 2.0 or, much later, WikiLeaks.
In response to that, a number of people suggested that Mueller might charge Stone for conspiracy to hack (under the Computer Fraud and Abuse Act) after the fact.
You don’t charge people for entering into a conspiracy after the crimes have been committed.
In fact, in one of Roger Stone’s denials, to Chuck Todd earlier this year, he tried to make this point — that he can’t be held responsible for any hacking because the hacking happened before he started interacting with the purported hacker, Guccifer 2.0.
Todd: Why did you reach out to Guccifer? Why did you reach out to Wikileaks?
Stone: First of all, my direct messages with Guccifer 2.0, if that’s who it really is, come six weeks, almost six weeks after the DNC emails had been published by Wikileaks. So in order to collude in their hacking, which I had nothing whatsoever to do with, one would have needed a time machine.
And (at least based on what we know) I believe that’s true, with respect to the March 19, 2016 hack of John Podesta and the May 25, 2016 exfiltration of the DNC emails. Nothing we know suggests Stone was part of a conspiracy with the Russians that early (though I don’t rule it out, particularly given his recruitment of Paul Manafort around the same time as the Podesta hack). Nothing we know says Stone can be shown to have entered into a conspiracy with Russia before the hack of Podesta or the DNC.
But it is not the case that no hacking occurred after Trump and his allies are suspected of entering into a conspiracy. Mueller provided a really remarkable example in the GRU indictment, showing that after Trump asked the Russians for Hillary’s emails, they launched a new wave of attacks on targets close to Hillary.
The Conspirators spearphished individuals affiliated with the Clinton Campaign throughout the summer of 2016. For example, on or about July 27, 2016, the Conspirators attempted after hours to spearphish for the first time email accounts at a domain hosted by a third-party provider and used by Clinton’s personal office. At or around the same time, they also targeted seventy-six email addresses at the domain for the Clinton Campaign.
There’s another example in the indictment, involving Stone, which is more subtle.
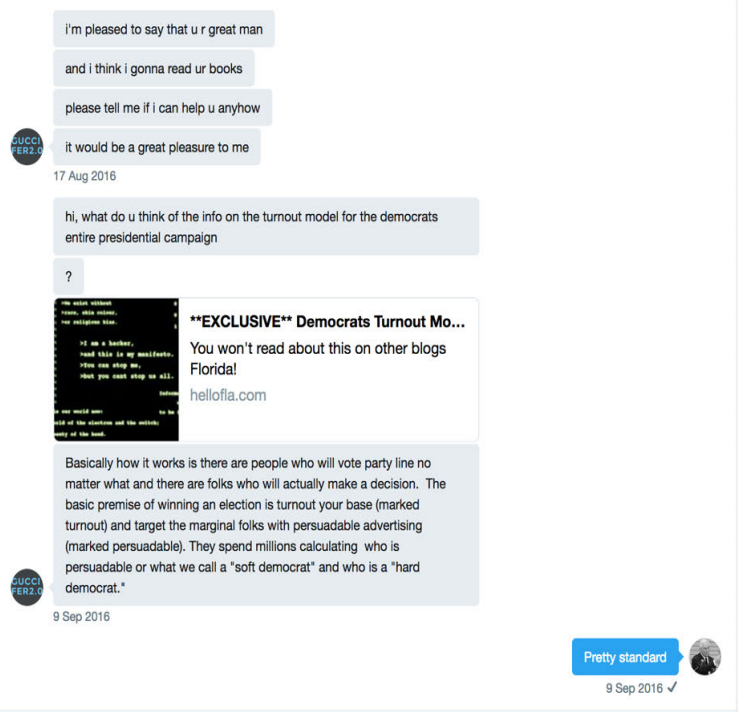
The indictment summarizes key parts of Stone’s conversation with Guccifer 2.0, describing him as someone who “was in regular contact with senior members of the presidential campaign of Donald J. Trump.” It describes how Guccifer 2.0 asked Stone if he could be of assistance, then asked him what he thought of a turnout model earlier released to and highlighted by Aaron Nevins (whom the indictment describes as a “a then-registered state lobbyist and online source of political news”). As the indictment describes, Stone said that that turnout model was “pretty standard.”
The Conspirators, posing as Guccifer 2.0, also communicated with U.S. persons about the release of stolen documents. On or about August 15, 2016, the Conspirators, posing as Guccifer 2.0, wrote to a person who was in regular contact with senior members of the presidential campaign of Donald J. Trump, “thank u for writing back . . . do u find anyt[h]ing interesting in the docs i posted?” On or about August 17, 2016, the Conspirators added, “please tell me if i can help u anyhow . . . it would be a great pleasure to me.” On or about September 9, 2016, the Conspirators, again posing as Guccifer 2.0, referred to a stolen DCCC document posted online and asked the person, “what do u think of the info on the turnout model for the democrats entire presidential campaign.” The person responded, “[p]retty standard.”
It looked like this:
Sometime in September — the indictment is coy about whether it happened before or after September 9 — Russian hackers accessed the DNC’s analytics on an AWS server and made a copy, thereby stealing it.
In or around September 2016, the Conspirators also successfully gained access to DNC computers hosted on a third-party cloud-computing service. These computers contained test applications related to the DNC’s analytics. After conducting reconnaissance, the Conspirators gathered data by creating backups, or “snapshots,” of the DNC’s cloud-based systems using the cloud provider’s own technology. The Conspirators then moved the snapshots to cloud-based accounts they had registered with the same service, thereby stealing the data from the DNC.
Accessing the Democratic analytics program updated daily — even if, as I’ve been told happened, the Democrats discovered and shut down this effort before Russians could obtain more valuable trend data — would presumably be far more valuable than leaking a targeting document dating to February 9. It would be far more damning, too, if that theft came after a close associate of the candidate (and the recently departed campaign manager) had poo-pooed the dated targeting data as standard fare, suggesting Trump’s team wanted something more valuable.
We don’t know what happened to that analytics data after Russia stole it. But the GRU indictment does show not only that Stone was interacting with Guccifer 2.0 before that theft in September, but that he may have even provided feedback about similar information before the theft of more valuable, timely turnout information.
That probably still doesn’t get you to a CFAA conspiracy by itself (which is a different matter than a ConFraudUS conspiracy based off accepting a thing of value from a foreigner, for which there’s more solid evidence). But the two events taken in tandem suggest Russian hackers may have been responding to feedback from both the candidate and his longtime political advisor Roger Stone. The question, then, is what kind of agreement that responsiveness took part in.
As I disclosed in July, I provided information to the FBI on issues related to the Mueller investigation, so I’m going to include disclosure statements on Mueller investigation posts from here on out. I will include the disclosure whether or not the stuff I shared with the FBI pertains to the subject of the post.




So here’s a reason why there’s a compelling case that CFAA charges are appropriate and will likely move forward for both the campaign and Stone, provided the evidence supports them:
The CFAA makes it a misdemeanor to gain unauthorized access to a computer network, BUT it makes it a felony to then conduct fraudulent activity worth over $5000 as a result. The GRU hacking the DNC is actually not a big deal, its just regular espionage of the sort every nation conducts. I don’t even think they’d bring charges against GRU officers who only did that. What made it a felony, aggravated it, was the subsequent conduct of releasing the stolen material and use to cause harm (including financial harm) and to do so at the highest cost for the affected parties. Roger Stone’s involvement, and coordination between the Russians, Assange and the Trump campaign undoubtedly helped the conspirators cause financial harm in a way that turned the hacks into felonies. He is thus right in the middle of the crime.
Is it about financial harm amounts (to the victim) or financial gain amounts (to the perp)? I would think the value to the perps would be extraordinary since they had made (via the press, etc) free campaign smears against an opponent.
CFAA: I had to look it up.
https://en.wikipedia.org/wiki/Computer_Fraud_and_Abuse_Act
Looks like J Chait had better do a little homework if he’s going to keep his reporting relevant. Meanwhile, more reporters need to be able to explain this to the voting public, and why it matters. A nation of people screwed by Identity Theft is probably going to pay pretty close attention to the general storyline, particularly if the reporter(s) can convey it clearly.
(I’ll go out on a limb and hazard a wild-arse guess that this kind of story doesn’t really fit well within the Fox News bailiwick. Their audience won’t get the technical issues, and their reporters won’t be able to get their heads around it– no matter how many tax havens and how much money laundering Murdocks engage in. OTOH, this is the kind of story that IMVHO a lot of Millenials and gamers will instinctively understand and be genuinely pissed about: Roger Stone as something even more heinous and soulless than Voldemort, as it were.)
Thanks.
Lawfare had an article last year theorizing about this. AFAIK the CFAA hasn’t been used like that but according to their theory it could.
September and October 2016 are very vaguely described in the GRU indictment, even as it says the hack activity went on till the voting system stuff in late October. September is also when Peter Smith’s operation was seriously ramping up, per Matt Tait. I think this time window — between “Russia, if you’re listening” at the end of July and the Podesta dump in early October — is where Stone and others ought to feel very nervous.
Along with the analytics server on AWS, there’s some deliberate vagueness in that first cited graf:
which strongly suggests other spearphishing rounds took place during the period G2.0 was also in direct contact with American political actors. And the government didn’t want to talk about them in that particular indictment.
I’ve been told that the attacks on Hillary’s campaign were a series of expanding waves as the election went on, with the wave in response to Trump’s “Russia if you’re listening” comment being one. So yeah, it kept getting more aggressive. As grown-ups took over security succeeding became harder, but not for lack of trying.
if you take every single act or set of related actions for which roger stone has publicly stated an alibi, then i would guess you’d be close to having a list of the specific acts of skulduggery in which stone has been involved, and in many cases initiated. the timings might be off from what we would expect a priori, but one should not, at first brush, worry about seemingly sensible/unsensible timing (dates). the key question is: why would stone bother to think someone else might think he was involved with, say, hacking? he clearly had been going over this in his mind before articulating the alibi. why did roger bother?
i raise this point because i have become sensitive to it. damn near every time i read about roger stone, he seems to be communicating one clear, articulate explanation or another of something he has been suspected of but did could not have done. my sense of the man is he is like a defense attorney explaining how the world misunderstands his client and his client’s actions. stone claims he is misunderstood with respect to credico, with respect to corsi, with respect to trump, with respect to assange, and, here, with respect to hacking.
one could attribute this to self-aggrandizement and own-p.r. and let it go. but roger stone has a cause in life, a fanatic motivation – he wants to pay the world, and most particularly the democratic party, back for impeaching nixon and running him out of the presidency. stone has been expressing this fanatic motive for decades. in addition to his fanaticism, he has a lot of skills, no conscience whatever, and by 2016 a lifetime of dirty tricks experience. with stone, as with a serial killer, i think the detective’s approach would be to assume he did “x” and then look for opportunities that might have presented themselves to him to do exactly that.
“… In fact, in one of Roger Stone’s denials, to Chuck Todd earlier this year, he tried to make this point — that he can’t be held responsible for any hacking because the hacking happened before he started interacting with the purported hacker, Guccifer 2.0.
And (at least based on what we know) I believe that’s true, with respect to the March 19, 2016 hack of John Podesta and the May 25, 2016 exfiltration of the DNC emails. Nothing we know suggests Stone was part of a conspiracy with the Russians that early (though I don’t rule it out, particularly given his recruitment of Paul Manafort around the same time as the Podesta hack). Nothing we know says Stone can be shown to have entered into a conspiracy with Russia before the hack of Podesta or the DNC. ..”
well didn’t ol rog have that all neatly worked out in his head?
so was stone engaged in presidential anti-democratic party activity in 2015, e.g., aiding the congressional benghazi witch hunt? was he chewing the fat with trump about the presidency then? if so, maybe he was working with manafort and russia on hacking long before 2016. did he become an intermediary with the russians and republicans once he sniffed out that putin had it in for clinton, and that the russian army general staff was happy to put their destructive social media computer skills to work.
i’m not weded to this speculation, but it frustrates me that this evil litte weasle has been so hard to trap while busily killing the chickens. and the weasel keeps telling us why he could never have gotten in the chicken coop – not me, no way!
if you take every single act or set of related actions for which roger stone has publicly stated an alibi, then i would guess you’d be close to having a list of the specific acts of skulduggery in which stone has been involved, and in many cases initiated. the timings might be off from what we would expect a priori, but one should not, at first brush, worry about seemingly sensible/unsensible timing (dates). the key question is: why would stone bother to think someone else might think he was involved with, say, hacking? he clearly had been going over this in his mind before articulating the alibi. why did roger bother?
i raise this point because i have become sensitive to it. damn near every time i read about roger stone, he seems to be communicating one clear, articulate explanation or another of something he has been suspected of but did could not have done. my sense of the man is he is like a defense attorney explaining how the world misunderstands his client and his client’s actions. stone claims he is misunderstood with respect to credico, with respect to corsi, with respect to trump, with respect to assange, and, here, with respect to hacking.
one could attribute this to self-aggrandizement and own-p.r. and let it go. but roger stone has a cause in life, a fanatic motivation – he wants to pay the world, and most particularly the democratic party, back for impeaching nixon and running him out of the presidency. stone has been expressing this fanatic motive for decades. in addition to his fanaticism, he has a lot of skills, no conscience whatever, and by 2016 a lifetime of dirty tricks experience. with stone, as with a serial killer, i think the detective’s approach would be to assume he did “x” and then look for opportunities that might have presented themselves to him to do exactly that.
“… In fact, in one of Roger Stone’s denials, to Chuck Todd earlier this year, he tried to make this point — that he can’t be held responsible for any hacking because the hacking happened before he started interacting with the purported hacker, Guccifer 2.0.
And (at least based on what we know) I believe that’s true, with respect to the March 19, 2016 hack of John Podesta and the May 25, 2016 exfiltration of the DNC emails. Nothing we know suggests Stone was part of a conspiracy with the Russians that early (though I don’t rule it out, particularly given his recruitment of Paul Manafort around the same time as the Podesta hack). Nothing we know says Stone can be shown to have entered into a conspiracy with Russia before the hack of Podesta or the DNC. ..”
well didn’t ol rog have that all neatly worked out in his head?
might stone have been engaged in anti-democratic party activity at the presidential level in 2015, e.g., aiding the congressional benghazi witch hunt? was he chewing the fat with trump about the presidency then? if so, maybe he was working with manafort and russia on hacking long before 2016. did he become an intermediary with the russians and republicans in 2015 or early 2016 once he sniffed out that putin had it in for clinton, and that the russian army general staff was happy to put their destructive social media computer skills to work.
i’m not weded to this speculation, but it frustrates me that this evil litte weasle has been so hard to trap while busily killing the chickens. and the weasel keeps telling us why he could never have gotten in the chicken coop – not me, no way!
i’ve been looking for it but i can’t find it – within the last month a commenter here left a citation on an article about roger stone. it was more detailed than others i had read. most interesting to me was the assertion that roger stone had gone deep diving into the realm of the rightwing/republican kooks, into 4chan for example, and had engaged with them in some of their schemes. i had pictured stone as more rational than that, but perhaps not – was he there to wholeheartedly join in extreme politics, or there to exploit the kooks for his own political purposes?
i have gotten the impression that some of the denizens of this realm are receptive to communication with russian government. if so, that might have been a channel that covertly established the initial communications between the republican party in the person of stone and the russian government (or its customary non-gov standins).
Hi, orion-
Not sure if this is what you are looking for, but it fits the description (as it was discussed in a convo Rayne and I were having here):
Brett Kavanaugh and the Information Terrorists Trying to Reshape America | WIRED
https://www.wired.com/story/information-terrorists-trying-to-reshape-america/
thank you.
thank you.
I’ve been thinking lately that Stone brought Manafort in then for the express purpose of trying to get in on the RU game, i.e. jockey for position with the first place start of Mercer/Bannon/Cruz. So I think the recruitment of Manafort then may support your first clause as well.
I’ve also been entertaining the unorthodox notion that we may be better off with trump having won than Cruz, in a Mercer-inspired parlor game I’ll call The Tale of Two Steves (but don’t forget Stephen). Can you imagine if Cruz won, how the current awfulness would have a patina of ‘dignity’ a la the normative Republican way? The POTUS would be seen as reasonable, Steve King would be the public Trump, Bannon would be genius Jared. Good grief, Roy Moore may have even gotten elected. Am debating what Stephen Miller would be doing. I’m distracted by the latest Stone-slapfights-Bannon stories, not entirely caught up.
I’d not necessarily have thought things could be worse than they are now, but am of late appreciating that Cruz would have been more dangerous in this role. Ultimately capitalism prevailed, and we have a market for Never Trumpers.
More on the milieu of March:
Republican Party presidential primaries, 2016 – Wikipedia
https://en.wikipedia.org/wiki/Republican_Party_presidential_primaries,_2016
Ted Cruz presidential campaign, 2016 – Wikipedia
https://en.wikipedia.org/wiki/Ted_Cruz_presidential_campaign,_2016
Also, we have not heard of any Rs prepping Tad Devine/Bernie RU-ties oppo research papers in March 2016, have we?
(I’m sticking this comment here as it relates to the March milieu I was citing above, but with the interlinked posts it could really go to the ‘Why Did Rebekah Mercer…’ page, or to the Stone-Bannon fight club page).
One “throwaway comment” from Stone that he has since denied was when he allegedly stated he “had dinner” with Julian Assange, then waved off the implications with an alibi of being elsewhere.
I just automatically assume the “dinner” really happened as a videoconference at a shared meal time.
Just like anyone who is inaccessible for irl meetings, Assange likely tries to maintain a semblance of normalcy through various video streaming get togethers.
Being in the same time zone isn’t a requirement in today’s world to “dine together,” fwiw.
I’ve always thought that the message about “dining with Julian Assange” was some kind of cryptic coded message.
Since this message was sent to Nunberg, I assume that cracking its meaning may be accomplished by scrutinizing Nunberg’s communications with others.
Which explains Nunberg’s hysteria over the rectal examination his communications received by the special counsel.