The Logic of Assange’s EDVA Indictment Is Inconsistent with Mueller’s Apparent Logic on Assange’s Declination
As Emma Best has noted, shortly before GRU targeted John Podesta in a spear-phishing attack, WikiLeaks offered a reward for Hillary’s speech transcripts like the excerpts that were released as part of the John Podesta release.
Hours before Russian hacking operations targeted Hillary Clinton’s campaign in the spring of 2016, WikiLeaks discussed offering a monetary reward for transcripts of her speeches at Goldman Sachs. Soon after, Russian hackers launched a spear phishing campaign that resulted in John Podesta’s email account being compromised. Emails containing excerpts from the speeches were included in the first day of the Podesta email releases. A week later, emails containing the transcripts themselves were released. WikiLeaks heralded these transcripts as their “holy grail.”
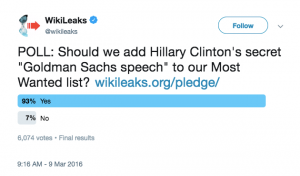
The story began on March 9, 2016, when WikiLeaks sent a tweet with a poll asking if they should add Hillary Clinton’s Goldman Sachs speeches to their ”Most Wanted” page for six figure rewards for materials. When the poll completed twenty four hours later, 93% of respondents said that WikiLeaks should offer a reward for the speeches. The Russian hackers at Fancy Bear may have been listening and been inspired by WikiLeaks’ comment. Unpublished targeting data collected by Secureworks shows the hacking campaign began earlier than the Mueller indictment reveals. A week and a half later, after dozens of attempts to penetrate the accounts of Podesta and other Clinton staffers and associates, Fancy Bear sent the phishing email that successfully tricked Podesta into compromising his account and the Goldman Sachs speeches along with it.
Secureworks’ unpublished breakdown of the Russian spear phishing and hacking effort, which AP described last year, shows that the campaign to penetrate the account began hours after WikiLeaks teased the possibility of offering a reward for the information. The tweet first mentioning the potential of a reward for the Goldman Sachs transcripts was sent at 8:16 P.M. Moscow time. At 11:56 AM the next day, less than sixteen hours later, Russian hackers began a campaign that would target “over 300 individuals affiliated with the Clinton Campaign, DCCC, and DNC.“ Podesta’s emails accounts were targeted in the days that followed and successfully compromised a week later, resulting in the exfiltration of nearly 60,000 emails.
Under what I’ve called Theory One of the superseding Julian Assange indictment, WikiLeaks’ publication of a wish list that was subsequently fulfilled would qualify it (or Julian Assange) for a conspiracy charge. Given what we’ve seen of Roger Stone’s actions, it might qualify him for a conspiracy charge as well (though we still don’t know via what means he contacted WikiLeaks).
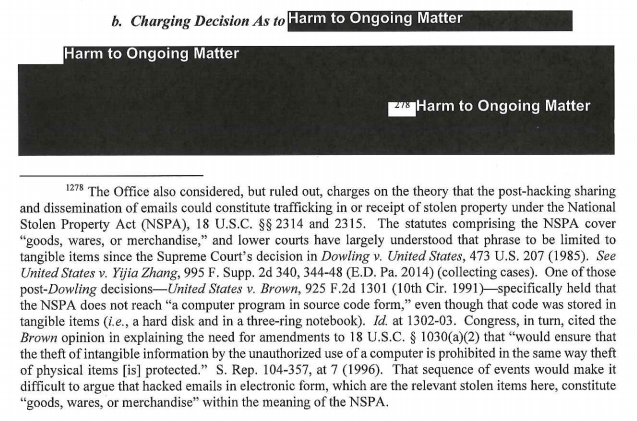
But this 2.5 page redaction in the Mueller Report appears to explain why they didn’t charge WikiLeaks (and so by association, Stone) in that conspiracy.
We don’t know what that redaction says, though the unredacted footnote makes it clear that in the case of emails stolen from Hillary, DOJ determined that sharing of stolen property does not constitute a crime.
We do, however, have a sense of how the Attorney General understands this declination, because he used it to exonerate Trump, even in spite of Trump’s active role in pushing Roger Stone to optimize the WikiLeaks releases for the campaign. In one of his explanations for the WikiLeaks declination — one that may more directly allude to Stone’s involvement — Bill Barr said that publication of stolen emails would not be criminal “unless the publisher also participated in the underlying hacking conspiracy.”
The Special Counsel also investigated whether any member or affiliate of the Trump campaign encouraged or otherwise played a role in these dissemination efforts. Under applicable law, publication of these types of materials would not be criminal unless the publisher also participated in the underlying hacking conspiracy. Here too, the Special Counsel’s report did not find that any person associated with the Trump campaign illegally participated in the dissemination of the materials.
In the case of election interference, then, Barr does not consider the publication of documents identified on a wish list that hackers subsequently steal to amount to joining a conspiracy.
But in the case of Chelsea Manning’s leak, his DOJ does.
There’s obviously a distinction: John Podesta’s risotto recipes are not classified, whereas much of the stuff (but not all) Manning leaked was. But the role of a wish list is not functionally different, and Russian officers were charged both for hacking and dissemination.
I’m still working on a post describing how unbelievably stupid the EDVA case is, both for the press and for DOJ’s hopes to lay a precedent.
But at least at a structural level, the prosecution is also inconsistent with the decisions DOJ made about WikiLeaks on the election year operation.
As I disclosed last July, I provided information to the FBI on issues related to the Mueller investigation, so I’m going to include disclosure statements on Mueller investigation posts from here on out. I will include the disclosure whether or not the stuff I shared with the FBI pertains to the subject of the post.






It sounds like the Assange case is using “whatever makes the powers that be happy” – with Tr*mp as the major power.
I actually think that Barr chose to have Assange indicted under the Espionage Act for a dual purpose. First, it is questionable whether he can actually be convicted of it and might make the British more reluctant to extradite Assange to the United States (that is, Barr doesn’t really want Assange on American soil but he does want to seem like he is ready to throw the book at him). Second, it is designed to intimidate media organizations which disseminate classified information as public interest journalism by effectively criminalizing what has long been a bread and butter aspect of American journalism going back to the Pentagon Papers and even earlier.
Terrapin
I agree with both your points, the purposes are shrewd and calculating and go to show that they are Barr’s product and not Trump’s. If Trump gave it any thought he would be demanding Assange be extradited immediately and be screaming about the enemy of the state throughout the proceedings. Never considering for a moment the comparison of the allegations to his own actions, and oblivious to the law. But it makes one wonder how far down the rabbit hole Barr is.
Not the actual crime of hacking, but participation in a conspiracy to hack. Leaves a Barr-sized hole one could drive the DoJ through.
Yep, and on my mind since the post where EW ID’d this as Barr sentence #2 of a triad she broke down, I wonder if Andrew Miller (or a closer look at Stone’s devices) has anything to offer as to Guccifer, Stone, and the analytics hack, etc.. Note the MR said that “the investigation” found nothing more of _Guccifer_-_Stone_ contacts (besides what is listed in report, last being the September 9th DMs; but see below re other public ways to communicate).
As a separate but related matter, Guccifer was also a publisher.
Third, it’s so odd that Stone’s twitter account only publicly tweeted with Guccifer for a few days in August, given stated shared interests. Deafening silence.
On August 16th, Stone published a piece in The Hill about election rigging. Beyond FUD or propaganda, it’s full of road-mappy statements for Russian targeting including via outlinks to other articles and multiple methods. More interesting, he cites Tony Fabrozio’s “encouraging” post- convention polling re swing states. It’s almost like the article could be seen as clarifying or elaborating on conversations that took place on August 2.
The next day, and apropos of nothing identified in the MR, Guccifer DMs Stone (PDF 52):
Can the 2016 election be rigged? You bet | TheHill
[https://thehill.com/blogs/pundits-blog/presidential-campaign/291534-can-the-2016-election-be-rigged-you-bet]
Roger Stone’s Russian Hacking “Hero” | The Smoking Gun
[http://thesmokinggun.com/documents/investigation/roger-stone-and-guccifer-913684]
Forgot to note: Guccifer also retweeted Stone’s tweet about the article, after tweet-saying “paying u back” (screen shots are in The Smoking Gun article linked).
And see for more context (this was _after_ Stone _asked_ for the retweet- see screenshots):
The Universe of Hacked and Leaked Emails from 2016: Podesta Emails – emptywheel
https://www.emptywheel.net/2018/10/23/the-universe-of-hacked-and-leaked-emails-from-2016-podesta-emails/
As EW has noted, there is so much publicly available about Stone and his activities that is redacted (or omitted) from the Mueller Report. That concerns me as to how to ‘collect’ it all so that MOC acting now have their eyes on all of the conspiracy-related details as they set about hearings.
Beyond that, there things like that Stone ‘The Hill’ piece that deserve fresh looks in light of additional public details as to context, like the Aug 2 meeting polling data transfer.
Sorry to have to ask, but what is “EDVA”?
Sorry: Eastern District of Virginia, where Assange was charged.
Maybe l’affaire Assange is a space to negotiate his silence, and the Barr authorization is quid to inform FSB pro quo. Gopus delendus est ⚡️
EW:
Have you addressed sham “press” posing or what it takes to contaminate someone out of press protections — I mean like extorting a government for a pardon or ambassadorship.
What about RT sending a wish list to the GRU?
I am fully in agreement with the crass hypocritical and deceptive positions taken by the Barr DOJ. We all know that journalistic rights have a complicated boundary with, for example, security. But the Barr DOJ, is playing for keeps to rig the system. What motivates he man isn’t hard to fathom.
But, Could we move from calling ideas, thoughts or expressions “property”. For example “…DOJ determined that sharing of stolen property is does not constitute a crime.” Likewise, documents are something physical and these were not stolen.
Then we can consider when ideas ideas, thoughts or expressions should be considered private, and what rights should exist, for whom and to what ends to breach that privacy.
This isn’t just a matter of approaching language pedantically. So called “Intellectual property rights” are ATMO one of the cornerstones for maintaining the status of elites, and furthering the gap between them and everyone else. And the more we treat ideas, thoughts and expressions as property, the further we get stuck down that hole.
If the Russians had stolen an American weapon, and given it over to Assange, he could easily be prosecuted for possession of stolen goods, even if he never used it. Ideas, thoughts and expressions, however, are a very different thing.
[Welcome back to emptywheel. Auto-moderation held your comment because this is your second username apart from ‘AngryMan’. Please use the same username each time you comment so community members get to know you. Thanks. /~Rayne]
You might be a little more understanding if it were your work being stolen….
Or your friends work being stolen. #notsogoodtimes
Interesting points raised about intellectual and property rights. However, what I think the point of this post by EW is is that there is an inconsistency in application of the law or legal theories emanating from Barr and the DoJ to suite the political needs of the moment. Good law is consistent “yet flexible”. Bad law is flexible to suit the needs of bad actors and leads to injustice and abuse. What were are concerned here is about bad law, inconsistent application for bad reasons in a specific case, not in the broader, generalized discussion of what is and is not property per se, etc, etc, blah blah blah. #sorrynotsorry
Are you referring to emails as “ideas thoughts and expressions?”
If so I agree with you that ‘ideas thoughts and expressions’ should be treated differently than property but in my case at least, I don’t think emails would apply. Just like in the good old days my mailbox now might have a personal note or two in it but it’s a lot of work crap and bills and advertisements and invitations and work back and forths.
As for my online diary or notes from my therapy sessions…
Actually now that my brain is churning I know of a fraternity that was shut down last year because of a closed facebook group that included several members of a fraternity. The groups page was hacked by an (angry) ex-girlfriend. Not much of a hack, she was able to figure out her boyfriends password, but clearly she illegally invaded a space that was thought to be private where they were free to express “ideas thoughts and expressions” and I think that this gets to your point which is interesting. She didn’t “steal” anything, but if that’s the case, how do you explain the fact that she “got” something?
In short she was the topic of several posts, unkind things were said about her and they included sexual insults. She took screen shots of the comments became a #metoo sensation on campus and on youtube and 4 months later the fraternity was officially shut down.
Side note; My hope is she is on some reality show somewhere doing whatever it is those people do, and those idiot frat boys have learned from their foolishness and are on their way to becoming much better men because of it, I know they appeared to take it seriously at the time so here’s hoping…
They used to raise people with the thought that they shouldn’t do or say anything that they wouldn’t want to see on the front page of a newspaper. (Clearly Tr*mp thinks that that’s all good, but he’s also not good at thinking past what he wants right then.)
If I offer 100K to kill my husband isn’t that solicitation of a crime?
I can’t remember if it was this particular “tease” of an offer (as EW described it) or one wikileaks had offered more openly in the past but the justification Assange gave for offering money was that journalists and law enforcement pay for information all the time.
I’m not sure how that works though since he had to know that the only way this information could have been obtained was by committing a crime.
On another note, correct me if I am wrong but to “conspire” don’t the parties need to be working for the same cause?
If Assange was trying to throw the election and the hackers were simply hacking for the reward money two crimes STILL seem to have been committed. I understand that being able to prove Assange “conspired” with others would help in a case against him but isn’t is still illegal for an INDIVIDUAL to interfere with an election?
Is there strong evidence that Assange was trying to throw the election? There appears to be strong evidence that Assange tried to get Manning to commit a crime but that was well before this election per se… at least according to the government’s documentary evidence (as such). Now, if there is evidence that Trump associates were offering Assange immunity or a pardon in exchange for help, that might well be evidence of a conspiracy in the offing. My mind is fuzzy there though—did Trump say something to that effect at some point publicly? (He says so many things it’s like looking into a kaleidescope that is continually turning and that if one looks away from one might lose all. So tiring. And one must choose to look away from time to time just to remain sane!)
Yup.
Read the post, looked away and lost track of the fact that despite Assange being charged for what seems to be the same damn activity as he did to help Trump beat Hillary in 2016 (encouraged someone else to do the hacking and then post the results of the crime online.)
What a freaking mess. Hopefully it will be easy to convince the UK to refuse to extradite because of the political spectacle being made but then again depending on who is taking over for May…
Anyone else think that Assange is perhaps among a handful of bears that Trump should be afraid of poking?
And how about someone conspiring on “Catch and Kills” in the few weeks before a Presidential Election? Do they still get press protections? How is that not ConFraudUS on both sides including Individual 1 — I mean the thing of value is right there on the contract and on the check stubs?
Which reminds me that I have heard nothing about AMI- National Enquirer loss of immunity based on their Bezos actions. And I think NY State may have been looking at them too.
I mean, talk about a treasure trove of “catch and kills” and other creepy stuff “in the vault”.
Just prior to the GRU phishing, on June 9th trump tweeted “How long did it take your staff of 823 people to think that up–and where are your 33,000 emails that you deleted?”. It would be interesting to have the Clinton campaign/ DNC /DCCC confirm how many people were on their email server staff/contact list then. If it was 823 then or shortly prior (on the date of GRU’s preceding hack), then that indicates trump knew of the impending phishing and number of potential targets?
Marcy wrote about that tweet here:
WHY DID TRUMP TWEET AN “IN THE BALL PARK” ACCURATE NUMBER FOR HILLARY’S TOTAL STAFFERS ON JUNE 9, 2016?
https://www.emptywheel.net/2018/01/25/why-did-trump-tweet-an-in-the-ball-park-accurate-number-for-hillarys-total-staffers-on-june-9-2016/
January 25, 2018
Thank you harpie, that’s a useful post and commentary. Attempting to keep up with present and past analysis is burning my news candle at both ends
Yes, it’s like living in a hurricane.
High anxiety constantly. Very stressful. Thank goodness EW is here to help us sort through the mess.
The hurricane season runs June 1 – Nov. 30. But primary time is the end of August to mid October. At least in this neighborhood. We had one here in 2016 and 2017. I had to get a new roof, ceiling, floor. Ugh.
Last year was a reprieve here. Looks like this year may be, too. Hopefully, we’ll get some kind of reprieve from the Hurricane-in-Chief, too.
—– “In the case of election interference, then, Barr does not consider the publication of documents identified on a wish list that hackers subsequently steal to amount to joining a conspiracy. But in the case of Chelsea Manning’s leak, his DOJ does. There’s obviously a distinction” —–
One distinction is that Assange worked with Manning, whereas the Trump campaign did not work with any of the hackers or leakers or publishers of Democrat emails. It’s a rather obvious distinction that takes effort to overlook.
This is also Trump sent garbage. The Mueller Report itself, and the many indictments along the way, disprove your trollish claim. But, hey, thanks for playing!
[Adding, it is a holiday, and things are a tad boring, so I let your baloney though just for grins]
yes, their use of “Democrat” as an adjective is a tell.
Indeed.
It’s quite the tell. Any normal person would write out “Democratic National Committee, Democratic Congressional Campaign Committee, and chairman of the presidential campaign of the leading nominee of the Democratic Party”.