How Google’s GeoFence Captured “Lions Not Sheep” Lisa Homer
Over the course of the January 6 investigation, I have repeatedly looked at the role several geofences — warrants collecting the identifiers of those who accessed cell sites in the vicinity of a crime — have played in the investigation. The FBI has relied on such geofence data from at least AT&T and Verizon (a recent arrest affidavit revealed that there were “significantly fewer devices in the T-Mobile data” from that day “than the company would expect”), as well as Google. There’s reason to believe the FBI obtained similar data from Facebook, perhaps identifying all those who livestreamed from inside the Capitol, but the scope of the collection time and place of that data remains obscure.
I’d like to revisit that discussion as part of a review of the arrest affidavit for Lisa Anne Homer/Boisselle. She was charged on November 15 with just trespassing, and arrested Monday, two weeks during which she may have been under close surveillance.
A word about her trespassing charges. In the initial days after the riot, FBI was arresting the people who most visibly mugged in videos, whether or not they had engaged in violence. In the days after the riot, FBI Director Christopher Wray explained that they were using arrests to understand the extremist networks they had missed before the attack.
The more arrests we make, the more from those cases we learn about who else their contacts are, what their tactics are, what their strategies are, et cetera. And that makes us smarter, better able to get in front of the threat going forward.
In many cases, those initial trespassing charges would lead to far more serious charges.
The number of trespassing arrests has significantly tailed off since then (and if DOJ believes these misdemeanors have a one-year statute of limitation, it will stop altogether next month). Indeed, for many of the more recent trespassing arrests, the FBI seems to have a specific purpose in arresting the people. Very often, the arrest affidavits focus on photos or videos the defendant obviously took during the insurrection. In some cases, the FBI seems to be looking for footage that might show what more serious participants did that wasn’t fully captured by CCTV. That’s definitely true of the events leading up to Ashli Babbitt’s shooting, and seems to be true for Kelly Meggs’ hunt for the Speaker after he broke into the Capitol.
In other cases, DOJ is arresting friends or accomplices of existing defendants on trespassing charges. That may be an attempt to be thorough, or it may be an effort to collect evidence about a primary target that accompanied the person to insurrection.
In some cases, such as with InfoWars personality Owen Shroyer, the government seems to have arrested people because they are key witnesses in the larger plot and DOJ can easily sustain a trespassing prosecution against them.
There are probably a slew of reasons why the FBI prioritized arresting Homer (who in June, legally changed her last name back to her maiden name, Boisselle, after a divorce). She did, in fact, film key scenes at the riot and she was wearing a GoPro under her chin.
She must also be someone of interest from a networking standpoint. For example, she lives or lived in AZ (indeed, the sole AUSA on her case right now, a detailee on Jan 6 cases who first filed notices of appearance on September 30, is located there), whence the siblings Konold traveled to insurrection; like Felicia Konold, Homer was standing next to Billy Chrestman as he riled up the crowd.
But the FBI suggests there may be a far more significant reasons for their interest later in her arrest affidavit. More than with virtually any of the Proud Boy or even Oath Keeper defendants, the FBI focuses on Homer’s attendance (and photography at) the November 2020 Proud Boys protest in DC.
The events of the November and December events in DC are undoubtedly central to the government’s investigation of the planning and networking that made January 6 happen. The government must be focused closely on it. They’ve just been very coy about sharing details of the key players at those earlier events., which seems a deliberate effort to shield what they know of those lead-up events from defendants (who, after all, are not charged for crimes committed in November and December). Nevertheless, in this case, FBI makes the November 2020 Proud Boy event central to the story they tell about Homer.
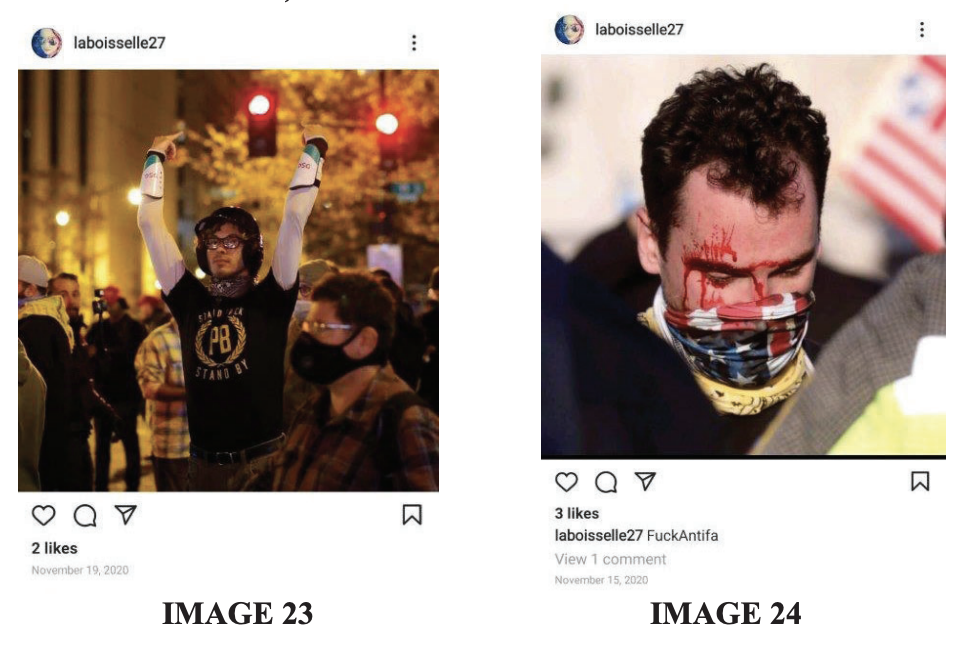
Indeed, the big reveal at the end of her arrest affidavit is a photo, which the FBI says was taken at the November 2020 Proud Boy event, that Homer posted on Instagram just weeks before she was charged. Her caption for the photo suggests that some guy — whose identity the FBI obscures but who surely can ID himself in the picture — “took my hand that night” is proof for her that “miracles can happen.”
It appears to be a love story wrapped inside an insurrection — a compelling story indeed.
But it starts (or at least, the FBI claims it started) with the Google GeoFence.
To be clear: The FBI likes to “parallel construct” investigative stories. To hide a sensitive investigative source (something like sensitive investigative methods, classified intelligence, or a cooperating witness), the FBI will often tell a story that suggests their investigation that ended with a big reveal — a love story wrapped inside an insurrection, perhaps — started with something totally innocuous, like a Google GeoFence that collected on everyone who trespassed on January 6.
And that’s how, the FBI suggests, this story started, with Homer tripping the Google GeoFence by entering the Capitol on January 6.
Again, there’s no reason to believe this is what really happened, but the FBI suggests they found Homer’s ID in the Google GeoFence, that led to “additional investigation,” that provided her phone and email information, which led to discovery of her travel records (which might have led to discovery of her trip to the November 2020 event), which made it very easy for the FBI to know where in all the video of from January 6 to find the photos that proved the figure whose face was hidden by a gaiter and glasses while inside the Capitol was the same person who showed her face freely outside of it.
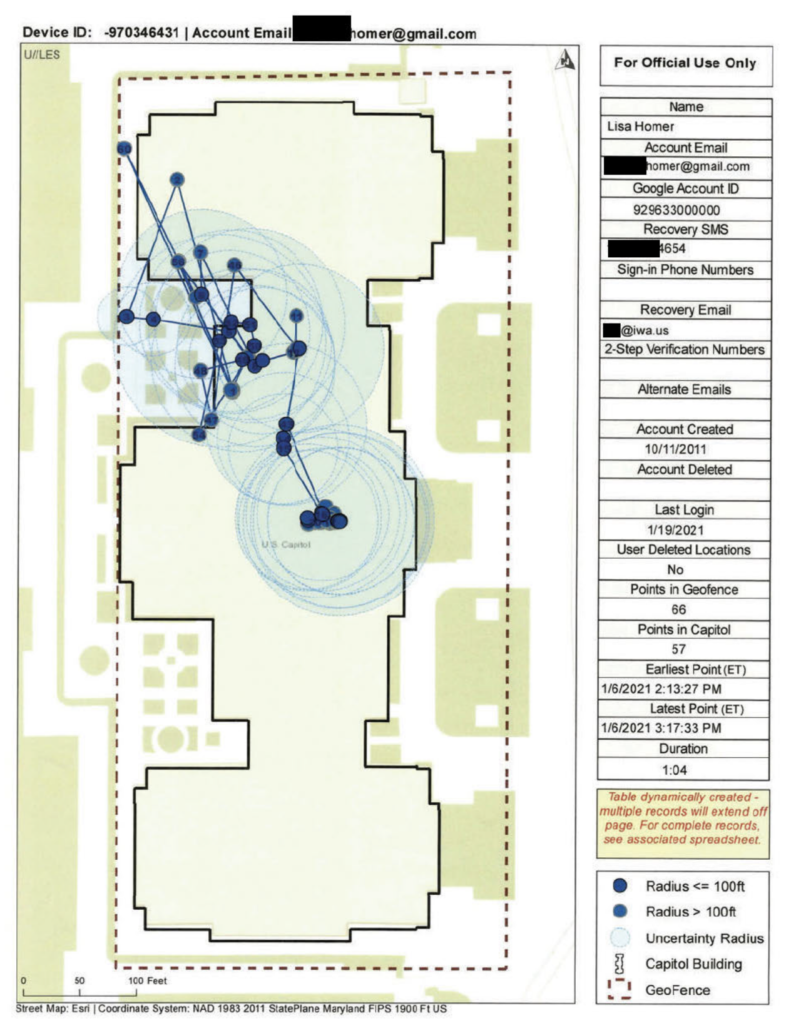
One reason I’m amused by this story is that, for whatever reason, the FBI Agent failed to obscure what most affidavits including Google GeoFence Reports hide, which is that the GeoFence includes in the report the information that FBI claimed required “additional information:” Homer’s email, her Google ID, her SMS recovery number, her recovery email, her account creation date, as well as the map itself showing the points both in and outside the Capitol itself where she tripped the GeoFence. Normally, the FBI can obtain all this information with a subscriber request (or an NSL, in the case of national security cases), so it’s not treated as very sensitive and would require just one additional step to get in any case. But if the government has obtained a GeoFence including everyone recognizable to Google who trespassed that day, along with selectors that would form part of the subscriber information for other social media providers, such as the Instagram account that forms a key part of the rest of Homer’s affidavit, then it is really powerful data.
To date, we don’t know how much of this GeoFence data Google collected and included in individualized reports in response to a request in the immediate aftermath of January 6, how much these reports reflect reports done in response to individualized requests after the fact, based on preserved data, or whether it’s a mix (such as that Google provided the initial identifiers to the FBI, which the FBI then used to cross-reference with other investigative materials, leading them to prioritize certain requests for more detailed reports). The FBI could obtain this information via a warrant for the GeoFence or via individualized warrants served months later (and Google surely has carefully preserved all investigative information tied to the event).
But this report provides a clue: it says that Homer last logged into Google on January 19, 2021.
It would take unbelievable amounts of discipline for someone to go ten months without logging into Google one way or another, the kind of discipline not exhibited by a person who doesn’t delete user location and who also posts incriminating photos to Instagram from a year earlier. So this report was presumably finalized much closer to January 19, not long after she had logged into Google, than November.
Maybe that Google GeoFence really is where this apparent love story started.








You didn’t mention Apple. Don’t they track the location of every iPhone? Did they provide any data in response to geofence requests? If not, why not?
There’s no evidence of an Apple geofence. There’s some use of iCloud content, but even that is relatively rare.
While they need location, I don’t think they use aggregated data as much as Google, and therefore wouldn’t have this kind of data in such readily accessible form.
It’s worth noting that any Google products installed on an iPhone will aggregate data the same way an Android phone would. Apple may not be tracking location but Google certainly is, even if all that’s installed is the YouTube app.
Correct, Apple doesn’t much care about aggregated location data and they have no need to store it on their servers. They can leave it on the device. It’s always easier to get an individual device’s location from the carrier. Google, on the other hand, has to store the location data they collect on their own servers and in an easily queryable form.
There is a one year statute for misdemeanors in many states, including mine. But the only federal crime I can find with only a one year statute is contempt of court, other than that it is still the five year general statute.
I tried to nail this down, which is why I wrote what I wrote. My guess is they may try to wrap up the 5104s by Jan 6, though, for that reason.
I can say I have never heard of any such thing. Here is the CRS paper on it. So, pretty sure it is still the five year general statute. If I’m right, January 6 (would actually be January 5 for these purposes) is no hard deadline.
Fair enough. I’m not all that invested in the question–they seem to be tailing off those anyway, and there’s a huge backlog of assault cases to charge yet.
Yes. But it is important to have backups for the assault and obstruction cases, so it remains a reason to care.
I would think, attacking a nation would override or supersede any & all offenses. This is not a violation of Jaywalking. Of course, I’m always wrong when it comes to the law.
So, you would just blithely ignore viable backup charges? Let’s do a little exercise here. If you want to prosecute someone for murder, but may not be able to convict them for that, you would not also charge manslaughter and assault? Really? There is a reason backups are charged.
I thought jury decisions were entirely predictable.
Lol.
Mason: They are, Paul, when we’re involved!
Della:
Fair point.
While I’m personally familiar with the types of technologies involved, and the potential range of data that can be collected, the persistence of stored data is beyond my ken. We used to scrub data when storage was relatively expensive, but now? How long do organizations keep data, and what drivers and rules control storage?
Given what has been publicly shared (sometimes leaked), is it safe to assume that the person who placed pipe bombs the night of January 5th had turned off or not carried a cell phone? Both behaviors would suggest a level of sophistication not exhibited by many of those involved in the insurrection. The doofuses are worrying, but the non-doofuses more so.
I would assume that person used very good OpSec.
It’s actually surprising how few people used better OpSec than they did on Jan 6. Homer is one of the few that succeeded in obscuring her face for the entirety of the time she was inside, but of course, that didn’t do much good.
It’s open to interpretation, but this video provided by the FBI suggests that the bomber carried a cell phone, though it could have been in “airplane mode”:
https://www.fbi.gov/video-repository/jan-5-pipe-bomb-footage-of-suspect-3-090821.mp4/view
As you point out, geofence data can be a powerful tool. Given (now outdated) testing my team did for grocery stores, it’s also possible to know who and what has been in close proximity to a person of interest, even if there was no intentional communications among the people/things involved.
Yes. Billy Chrestman didn’t trigger the phone geofences himself (he triggered the Google one). You can’t trace proximity with that density, but I believe they did elsewhere.
I would keep an open mind about what listening and detection technology is actually in play that will not be revealed for years. The standard way is what was discussed here about laundering the existence and use of the Stingray by law enforcement.
Back when I was working on classified type technology in the late 70s it was the standard for the Gov’t to always be 5-7 years ahead of the public sector.
Can you point to where I was discussing Stingray?
Wow, many many moons ago. Not recently. There was a discussion, I would swear here, (FDL days?) about how the Gov’t was dropping cases rather than admit they were using it to keep it out of discovery. Had to be back during Bush’s reign.
The discussion was how they would find other sources of the same information to cover the original source.
I think the legal question was that it is indiscriminate about what it intercepts.
I knew of the technology’s existence elsewhere, not on line.
Googled it.
MORE VISIBILITY ON STINGRAYS
January 6, 2015/4 Comments/in EO 12333 /by emptywheel
Wouldn’t it make sense to have an “authorized” stingray set up around the Capitol (or throughout the federal DC area.) Of course an authorized stingray may be competing with ones owned by other players….
Google “stingray in use around whitehouse”
I had the impression they were questionable legally anywhere due to their indiscriminate nature even with a warrant.
That is you guy’s territory, I am a tech guy who tries, with limited success, to understand legal stuff by reading here. Half this blog is way over my head, but I try.
BTW, the stingray is just a portable device, it is no problem to get all the same information if you have low level design access to cell tower equipment. Something like say, NSA or FBI would have.
The other technical detail I’ve read in several places is the “through the air” connectivity inside the Capitol is inconsistent at best, and frequently awful/inadequate. So, the Capitol Architect and the Sergeants at Arms have built out an extensive alternative. As the Washington Post put it:
“The Capitol, more than most buildings, has a vast cellular and wireless data infrastructure of its own to make communications efficient in a building made largely of stone and that extends deep underground and has pockets of shielded areas. Such infrastructure, such as individual cell towers, can turn any connected phone into its own tracking device.”
It’s going to be SOP for a group’s tankies to round robin swap devices with the group’s intellectuals for physical operations for sole purpose of confounding electronic and photo evidence, or some other swap activities which serve to break link between geo and photo evidence.
I could be wrong, but thought at least one of the bomber videos released by the FBI showed them sitting on bench and apparently fiddling with a phone (?).
L. Eslinger shared a link to video in this same thread showing just that. But because of the quality of the video we the public can’t be certain the suspect is fiddling with a phone or a different phone-sized object/device.
After looking at a few documents that have Google geofence data included (this one, Jeremy Baouche, and the Millers (Brandon and Stephanie)), I have drawn a few conclusions about all this. The FBI obtained (via a search warrant) all this data from a single data dump from Google. That data was dumped by Google on Jan 19 or shortly thereafter. Someone built a reporting app that produces the screenshots that are being used. The app must have been completed by March 9 when the output was included in the Miller’s arrest warrant. There’s no way any investigation starts from that data.
In the case of Boisselle (formerly Homer), somebody ratted her out to the Feebs, likely in July (because they knew who she was before talking to the cops in Scottsdale on July 14).
If anyone has links to other documents that contain the Google geofence images, I would love to take a look at them.
I’ll keep in mind–I know there are other Google reports, but it was fairly late in the process before the report itself got included. Billy Chrestman triggering the Google Geofence was the first I took significant notice of it, which would be after that dump.
https://www.justice.gov/usao-dc/case-multi-defendant/file/1366441/download
My GUESS is this report comes from Google or a contractor. But I was generally inclined to believe it came as a data dump–it would explain why FBI went through the trouble of whitelisting those legally present.
As for Homer, I suspect much of the Chrestman cell has pleaded out, including one or both of the Konolds. If that’s the case, one of them may have narced her out.
Interesting comparison between the language used in the Chrestman, et. al. arrest warrant, that used in Jeremy Groseclose’s (22-Feb), and finally that used in Millers’ arrest warrant (09-Mar):
The Chrestman language is pretty vague:
The Groseclose and Miller language is almost cut and paste:
(Differences in bold)
What’s interesting to me that this suggests that the FBI’s ability to exploit the data clearly evolved over time.
[ed: closed a blockquote]
I remember thinking at the time that DOJ had decided to show more of their work for the later ones (and perhaps for this one, with the subscriber information). After all by that point defendants would be getting their own GeoFence info.
This makes me wonder what the “whitelist” criteria is, and whether it includes anyone not scheduled in advance, or not member of Congress. For example “ad hoc” journalists who showed up to newsworthy event, or journalists who were tossed behind barricades over stairs by rioters?
Interesting comparison between the language used in the Chrestman, et. al. arrest warrant, that used in Jeremy Groseclose’s (22-Feb), and finally that used in Millers’ arrest warrant (09-Mar):
The Chrestman language is pretty vague:
The Groseclose and Miller language is almost cut and paste (diffs in bold):
Groseclose
Millers
What’s interesting to me that this suggests that the FBI’s ability to exploit the data clearly evolved over time.
(Note to mods: You can delete the version of this comment that’s hung up in moderation. I forgot to alter the email addresses in the quotes.)
From my brief use of Google for tracking my activity a couple of years ago, I’m not surprised. If there were a pre-existing Google Geofence along the physical walls of the Capitol building, that would explain much.
Miracles do happen. People get hurt. Love is a many-spleened O.R. thing.
Point of Information: Experts reporting to our nation’s government collect this granular info to protect us all from evildoers, yet presumably, ex-presidents and their entourage know these techniques and more – such magic tricks as we phone-peons remain unaware of. How many in the crowd on January 6 were insiders versed in this knowledge? Had they all gone home to let foot-soldiers take the rap? What’s planned for after the legal play ends? As the supremes get ready to gut privacy? Whoa.
The reason I pose these questions is not rhetorical. I deleted my FB after downloading its contents and realizing half of “advertisers” interested in me were Koch related entities or scandal-tinged repubs from Missouri – while I am a progressive person. I could also not help but note that it “messaged” privately my new (Google-connected) phone number without my knowledge. There were also third-party comments invisible to me about whom I met, what was discussed. I believe this information was used by neo-Confeds to track and harass me LONG before Trump. Started in the FDL days. Thanks for being there as a truth-seeker. Don’t know how I would have survived otherwise.
I just re-read this and I think one of the examples of higher-ups in the conspiracy who left the scene to the foot soliders were the Kremers, mother and daughter, who went back to the Willard after the speeches and ordered dinner which was probably paid for by the donors who funded the whole shebang but weren’t on site at the Capitol.
The same twosome who ensured burner phones were purchased for the purpose of organizing the January 5-6 events.