USA F-ReDux Is Non-Exclusive, but the Second Circuit Might Be
I’m still trying to figure out WTF Mitch McConnell is doing with his Senate machinations over USA F-ReDux. Currently, he has both his short-term reauthorization and USA F-ReDux prepped for a vote, which probably means he’ll bring USA F-ReDux up for cloture or a vote, show that it doesn’t have enough support, and then use that to scaremonger the short-term reauthorization through as a way to wring more concessions out of the House.
Still, given what a dead-ender he is on a bill, USA F-ReDux, that gives the Intelligence Community so many goodies, I can’t help but wonder if there’s another explanation for his intransigence. I can think of one other possibility.
The House Judiciary Committee made it clear USA F-ReDux would be the exclusive means to obtain prospective Call Detail Records under Section 215:
This new mechanism is the only circumstance in which Congress contemplates the prospective, ongoing use of Section 501 of FISA in this manner.
But it made it equally clear it is not the exclusive means to obtain Call Detail Records. That’s because the report envisions conducting federated queries including “metadata [the government] already lawfully possess.”
The government may require the production of up to two ‘‘hops’’—i.e., the call detail records associated with the initial seed telephone number and call detail records (CDRs) associated with the CDRs identified in an initial ‘‘hop.’’ Subparagraph (F)(iii) provides that the government can obtain the first set of CDRs using the specific selection term approved by the FISC. In addition, the government can use the FISC-approved specific selection term to identify CDRs from metadata it already lawfully possesses. Together, the CDRs produced by the phone companies and those identified independently by the government constitute the first ‘‘hop.’’
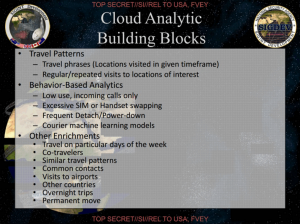
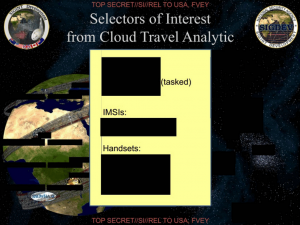
I suggested here that that other “lawfully possessed metadata” probably consisted of data collected under EO 12333 (and permissible for chaining on US persons under SPCMA) and PRISM metadata.
But maybe that’s not all it includes. Maybe, the government has devise a way by which AT&T (or some other backbone provider) will still provide phone records in bulk on a daily basis? Maybe — as Richard Burr claimed before he later unclaimed — the government secretly maintains an IP dragnet under some other authority?
If that was the plan (though keep in mind, USA F-ReDux passed the House after the Second Circuit decision), then the Second Circuit may have ruined that effort. The ruling should limit all collection under a “relevant to” standard, not just that conducted under Section 215. And, as Faiza Patel argued, the decision should also affect collection where the government has dodged Fourth Amendment issues by focusing on “searches” rather than “seizures.”
[A]s Jennifer Daskal explained last Friday, “collection matters.” The Second Circuit rejected the government’s contention that there was no cognizable injury until plaintiffs’ phone records were actually analyzed and reviewed. It ruled that collection is properly analyzed as “seizure,” which if unlawful constitutes a separate injury from the “search” that takes place when records are analyzed either by a human being or a computer.
As the Supreme Court has recognized, in Fourth Amendment cases the analysis of standing is intertwined with the merits question of whether there has been an invasion of a protected privacy interest. Thus, the Second Circuit’s position on collection could have serious implications for other government programs beyond the standing question.
I’ve already suggested the decision might create problems for the virgin birth DOJ secretly gave to EO 12333 data used in SPCMA.
But who knows what else it applies to?
After all, USA F-ReDux was written so as to allow other dragnets (which is what EO 12333 is, after all). But the Second Circuit may pose problems for such dragnets that USA F-ReDux did not.
Going back to Richard Burr’s odd colloquy — which his office’s excuses simply cannot rationally explain — I think it (very remotely) possible the government is dragnetting IP addresses (perhaps for cybersecurity rather than counterterrorism purposes), but worries it has lost authority to do so with the Second Circuit decision. If so, it might be using this fight over counterterrorism data collection to lay congressional support for broader dragnet collection, to be able to sustain whatever other dragnets it has in place.