Serving as Julian Assange’s Unwitting Data Mule to Israel Shamir Is Not Journalism
It’s a testament to how effective WikiLeaks’ propaganda is that almost none of the people implicated by things Julian Assange did years ago and almost none of the people who brainlessly repeat Julian Assange’s propaganda now know about this May 16, 2022 filing, submitted last year in the Josh Schulte case, which I wrote about here.
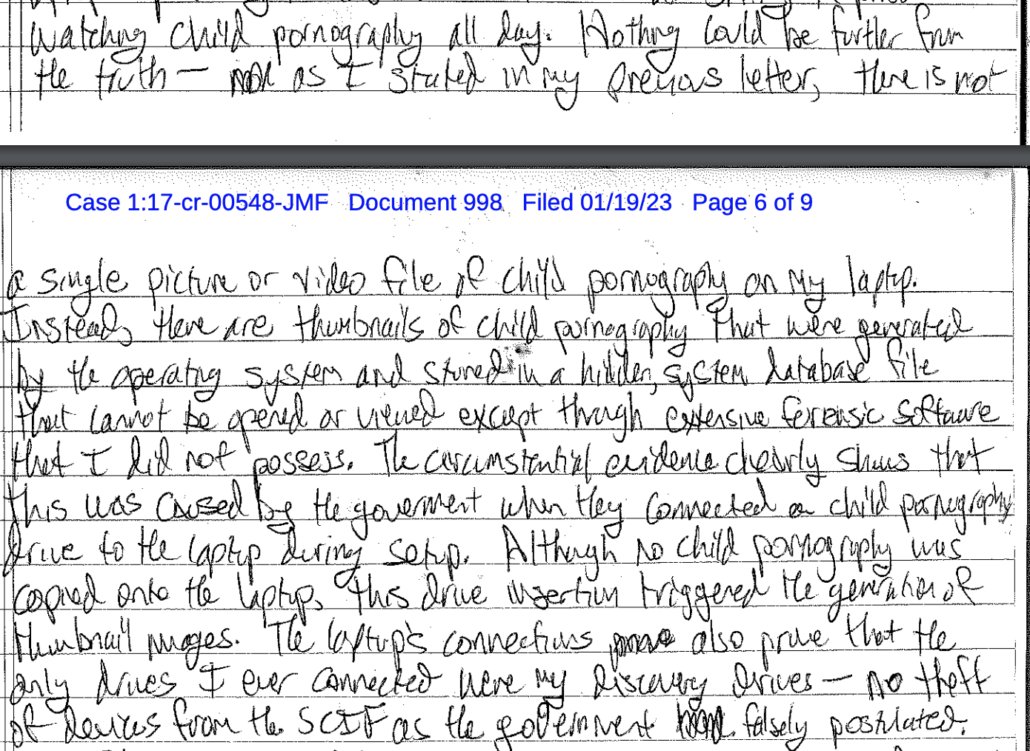
The redacted bits of the filing almost certainly describe things obtained in an ongoing investigation of WikiLeaks that pertain to how the data stolen by Schulte was used. The unredacted parts, however, describe that what must be the WikiLeaks investigation is both ongoing and has a scope that, “is neither known to the public nor to all of the targets of the investigation.”
“All of the targets.” That phrase is telling. At least one target — Assange — knows he is a target. The other targets (and DOJ uses the jargon to describe people who almost certainly will be charged, not just people who might be) don’t know.
The WikiLeaks investigation — which is ongoing and not just, as many boosters claim, an attempt to shore up the case against Assange — is not an investigation into Assange, exclusively. There are other targets.
Key WikiLeaks people almost certainly know about this filing, because they treated Schulte’s second trial — where he defended himself and repeatedly tried to publicly share classified information, almost certainly including details of the discovery about the ongoing WikiLeaks investigation he had received — differently than the first.
They’re just not telling you that there are other targets of the WikiLeaks investigation.
They’re not telling you, in part, because it ensures that when the Met or FBI or other investigators approach people to obtain information about those other targets, they’ll refuse, because they don’t want to be part of a prosecution of Julian Assange for what they’re telling themselves is journalism.
James Ball is the latest person describing how that happened.
In a Rolling Stone post describing the two year effort to obtain his cooperation, he claims journalists are being asked to cooperate against Assange.
And he claims he’s being approached — for information that clearly pertains to Israel Shamir — as a journalist.
He asserts that he’s being approached as a journalist by claiming that DOJ wants to talk to him about this 2013 article, rather than about his own conduct described in the article.
As the article described, in 2010, he unwittingly served as Assange’s data mule, handing off 90,000 State Cables to Israel Shamir, who then exploited them — by sharing them with Belarusian dictator Alexandr Lukashenko and/or selling them — before the entire Cable set was released.
Shamir is an anti-Semitic writer, a supporter of the dictator of Belarus, and a man with ties and friends in Russian security services. He and Julian—unknown to us—had been in friendly contact for years. It was a friendship that would have serious consequences.
Introduced to WikiLeaks staff and supporters under a false name, Shamir was given direct access to more than 90,000 of the U.S. Embassy cables, covering Russia, all of Eastern Europe, parts of the Middle East, and Israel. This was, for quite some time, denied by WikiLeaks. But that’s never a denial I’ve found convincing: the reason I know he has them is that I gave them to him, at Assange’s orders, not knowing who he was.
Why did this prove to be a grave mistake? Not just for Shamir’s views, which are easy to Google, but for what he did next. The first hints of trouble came through contacts from various Putin-influenced Russian media outlets. A pro-Putin outlet got in touch to say Shamir had been asking for $10,000 for access to the cables. He was selling the material we were working to give away free, to responsible outlets.
Worse was to come. The NGO Index on Censorship sent a string of questions and some photographic evidence, suggesting Shamir had given the cables to Alexander Lukashenko of Belarus, Europe’s last dictator. Shamir had written a pro-Belarus article, shortly before photos emerged of him leaving the interior ministry. The day after, Belarus’s dictator gave a speech saying he was establishing a WikiLeaks for Belarus, citing some stories and information appearing in the genuine (and then unpublished) cables. [my emphasis]
As he admits, at least by 2013, Ball was aware that Shamir had ties to Russian spooks.
What Ball describes in the piece is that he entered into an agreement with Assange to provide data to someone, Shamir, that Shamir did not publish, but instead shared with a repressive dictator and, probably, with Russian intelligence services.
That’s not journalism. That’s spying.
To be sure: as Ball describes, he realized his error and promptly left WikiLeaks (and, as he described in the 2013 article, refused to sign some of the NDAs Assange was pushing). That’s why he was approached as a witness and not a subject, because he made affirmative efforts to leave the conspiracy that has already been charged against Assange and almost certainly will be charged against Shamir, if it hasn’t already been, under seal.
After having served as an unwitting data mule for Assange in a handoff that would result in Lukashenko (and possibly Russian spies) getting advance access to the content of the Cables, Ball subsequently became a journalist. But that does not retroactively change what happened in 2010. Nor does that mean FBI approached him as a journalist. They approached him as a guy who once unwittingly served as a data mule for the part of the Cable releases that undermines all the claims that Assange is nothing but a publisher.
Here’s what people miss about the publication charges against Julian Assange, including the Cable count. They charge him for, “distributing them and then by publishing them.” Proving that Assange distributed the State Cables via unwitting data mule James Ball to Shamir is all DOJ would have to do to prove that charge against Assange, to prove that Assange shared them with someone not authorized to receive them. At a hypothetical trial of Assange (and whoever else gets charged), they’ll undoubtedly explain that after first giving privileged access to the Cables to Shamir, who handed them onto people who would use them to suppress dissent, Assange published all of them. That’s part of the cover. That’s part of what leads people like Ball to imagine he was involved in journalism when he shared the Cable files with Shamir.
For a number of WikiLeaks releases, there’s some story like this, about how before publication, files were either removed from the publication set or provided exclusively to someone in advance. The publication is, in part, cover for that earlier sharing. Schulte even described how if Russia got the source code he shared with WikiLeaks but which WikiLeaks, with limited exceptions, did not publish, they would never publish it, because it would be more useful to reverse engineer what the CIA had been doing.
These tools are MUCH more valuable undiscovered by the media or the nation that lost them. Now, you can secretly trace and discover every operation that nation is conducting.
Schulte is one of the people that anyone charged in a larger WikiLeaks conspiracy would be charged with conspiring with.
That’s the tough thing about US conspiracy law: Once you enter into a conspiracy, you’re on the hook for the actions of anyone who later enters into that conspiracy — like Shamir or Schulte — whether or not you know about it personally. You’re on the hook unless and until you take affirmative actions to leave the conspiracy. Lots of people with ties to WikiLeaks want no tie to Assange’s relationship with Shamir, but if DOJ adds him as a co-conspirator, then they’re not going to have much choice in the matter.
In any case, because so few of WikiLeaks’ boosters know that there are other targets in this investigation, they seem to be getting unfortunate legal advice, such as regarding the import of the detail that FBI obtained a statement from Shamir — whose statements, if and when he is charged as a co-conspirator, can be entered at trial — stating that Ball provided Cables, which he claimed to be about “the Jews,” to him.
The U.S. government cannot make much use of what I revealed in the article in a court of law unless I testify to it — and it is not hard to see how I could be useful if they were trying to strengthen the political case against Assange. In the article, I admit that I was the one who gave Shamir the material, albeit on Assange’s orders, without knowing who he was. If I testified to all this, it could, at least in theory, open me to criminal charges of my own.
[snip]
When, after months of delaying tactics had run out of road, we said a final “no”, there was a small sting in the tale from a DOJ prosecutor to my lawyers. Sending a statement in which Shamir had falsely claimed I had provided him with cables on “the Jews,” the prosecutor noted:
“Upon seeing those words from Shamir, I cannot help but ask whether Mr. Ball would reconsider his decision about speaking to the investigators, even if only just to respond to Shamir’s allegations.”
Yeah, it was a sleazy tactic, but also one designed to alert his lawyer that Ball does not currently have exposure but at a trial in which Shamir is a co-conspirator, Ball’s own conduct will be introduced at trial as part of proving that Cable charge and can be introduced without the article Ball wrote in 2013. Ball was advised they can’t use his article without his testimony — and because he had already left any agreement with Assange that’s probably right — but FBI can certainly introduce Shamir’s claims that he got the Cables from Ball, along with whatever other evidence they have about what Shamir did with them afterwards.
One more reason the fact that this is an ongoing investigation into targets not publicly identified matters: DOJ may or may not or may already have gotten the UK to approve superseding the existing indictment against Assange, the one that has led people to believe he is the only target of it. But they certainly have the ability to charge a conspiracy in which Assange is an uncharged co-conspirator, showing a seven year conspiracy involving Russian spooks — starting no later than that handoff of cables to Shamir — charging everyone else that entered into a conspiracy via Assange with Russian spooks. Back in 2020, prosecutors implied to Jeremy Hammond that the long extradition process of Assange would provide the opportunity to charge Assange’s involvement in the 2016 Russian hack-and-leak. And because at least one of the people who would be charged in such a conspiracy, Josh Schulte, appears to have continued his efforts to leak through last year, any statute of limitations might go through 2027. That’s why they’re in no rush to charge Shamir publicly: because the way conspiracy law works in the US, they can charge everyone who didn’t affirmatively leave the WikiLeaks conspiracy so long as the conspiracy remains ongoing.
Ball may well be right that the other people the FBI has approached are being approached for coverage of WikiLeaks they did, as journalists (though there are some edge cases). But of the descriptions I’ve seen, there’s always another as yet uncharged target about whom the FBI is asking. That may not change their calculus about whether they want to cooperate, but it means, whether they know it or not, that their refusals are not limited to a bid to protect Assange’s conduct.
I think the people approached for their coverage of WikiLeaks should definitely tell the FBI to fuck off.
But there’s more going on here, particularly with the request to Ball.