A bunch of human rights groups have started a campaign calling on President Obama to pardon Edward Snowden, to coincide with the release of the Snowden movie today.
With regards to Snowden’s fate, I believe — as I have from the start — that US interest would have been and would be best served if a safe asylum for Snowden were arranged in a friendly country. I had said France at the time, but now Germany would be the obvious location. Obama is not going to pardon Snowden, and Presidents Hillary or Trump are far less likely to do so, not least because if a president pardoned Snowden it would be an invitation for a metaphorical or literal assassination attempt. But I also think it would have always served US interests to keep Snowden out of a place like Russia. That ship has already sailed, but I still think we insist on making it impossible for him to leave Russia (by pressuring allies like Germany that might otherwise have considered asylum) largely out of self-destructive motives, an urge to prove our power that often overrides our interests.
That’s all background to recommending you read this post from Jack Goldsmith arguing against pardon for Snowden. While I disagree with big parts of it, it is the most interesting piece I’ve seen on the Snowden pardon question, for or against.
Like me, Goldsmith believes there’s no chance Snowden will get a pardon, even while admitting that Snowden’s disclosures brought worthwhile transparency to the Intelligence Community. Unlike me, he opposes a pardon, in part, because of the damage Snowden did, a point I’ll bracket for the moment.
More interestingly, Goldsmith argues that a pardon should be judged on whether Snowden’s claimed justification matches what he actually did.
Another difficulty in determining whether a pardon is warranted for Snowden’s crimes is that the proper criteria for a pardon are elusive. Oliver Wendell Holmes once declared that a pardon “is the determination of the ultimate authority that the public welfare will be better served by inflicting less” than what the criminal law specified. But how to measure or assess the elusive public welfare? The Constitution delegates that task exclusively to the President, who can use whatever criteria he chooses. Many disagreements about whether a pardon is appropriate are at bottom disagreements about what these criteria should be. Some will question whether Snowden should be pardoned even if his harms were trivial and the benefits he achieved were great. Indeed, presidents don’t usually grant pardons because a crime brought benefits. My own view is that in this unusual context, it is best to examine the appropriateness of a pardon in the first instance through an instrumental lens, and also to ask how well Snowden’s stated justification for his crimes matches up with the crimes he actually committed.
Goldsmith goes on to engage in what I consider a narrowly bracketed discussion of Snowden’s leaks about violations of US law (for example, he, as everyone always does, ignores NSA double dipping on Google and Yahoo servers overseas), claiming to assess whether they were violations of the Constitution, but in fact explicitly weighing whether they were a violation of the law.
His exposure of the 702 programs (PRISM and upstream collection) is harder to justify on these grounds, because these programs were clearly authorized by public law and have not sparked nearly the same criticism, pushback, or reform.
After substituting law for Constitution, the former OLC head (the guy who approved of much of Stellar Wind by claiming FISA exclusivity didn’t really mean FISA exclusivity) makes what is effectively an Article II argument — one nowhere nearly as breathtaking as Goldsmith’s Stellar Wind one. Most of Snowden’s leaks can’t be unconstitutional, Goldsmith argues, because they took place overseas and were targeted at non-US persons.
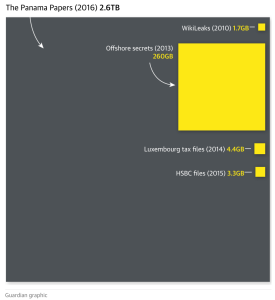
What I do not get, and what I have never seen Snowden or anyone explain, is how his oath to the U.S. Constitution justified the theft and disclosure of the vast number of documents that had nothing to do with operations inside the United States or U.S. persons. (Every one of the arguments I read for Snowden’s pardon yesterday focused on his domestic U.S. revelations and ignored or downplayed that the vast majority of revelations that did not involve U.S. territory or citizens.) To take just a few of hundreds of examples, why did his oath to the Constitution justify disclosure that NSA had developed MonsterMind, a program to respond to cyberattacks automatically; or that it had set up data centers in China to insert malware into Chinese computers and had penetrated Huawei in China; or that it was spying (with details about how) in many other foreign nations, on Bin Laden associate Hassam Ghul’s wife, on the UN Secretary General, and on the Islamic State; or that it cooperates with intelligence services in Sweden and Norway to spy on Russia?; and so on, and so on. These and other similar disclosures (see here for many more) concern standard intelligence operations in support of national security or foreign policy missions that do not violate the U.S. Constitution or laws, and that did extraordinary harm to those missions. The losses of intelligence that resulted are not small things, since intelligence information, and especially SIGINT, is a core element of American strength and success (and not just, as many seem to think, related to counterterrorism). It doesn’t matter that leaks in this context sparked modest reforms (e.g., PPD 28). The Constitution clearly permits foreign intelligence surveillance, and our elected representatives wanted these obviously lawful practices to remain secret.
Having laid out a (compared to his Stellar Wind defense) fairly uncontroversial argument about the current interpretation of the Constitution reserving wiretapping of non-Americans to the President (though my understanding of the actual wiretapping in the Keith decision, of Americans in Africa, would say Presidents can’t wiretap Americans overseas without more process than Americans’ communications collected under bulk collection overseas currently get), Goldsmith goes onto make his most important point.
The real defense of Snowden stems not from our own Constitution, but from a moral and ethical defense of American values.
What might be the moral and ethical case for disclosing U.S. intelligence techniques against other countries and institutions? (I will be ignore possible cosmopolitan impulses for Snowden’s theft and leaks, which I think damage the case for a pardon for violations of U.S. law.) I think the most charitable moral/ethical case for leaking details of electronic intelligence operations abroad, including against our adversaries, is that these operations were harming the Internet, were hypocritical, were contrary to American values, and the like, and Snowden’s disclosures were designed to save the Internet and restore American values. This is not a crazy view; I know many smart and admirable people who hold it, and I believe it is ethically and morally coherent.
This is a remarkable paragraph. First, it defines what is, I think, the best defense of Snowden. American values and public claims badly conflict with what we were and still are doing on the Internet. I’d add, that this argument also works to defend Chelsea Manning’s leaks: she decided to leak when she was asked to assist Iraqi torture in the name of Iraqi liberation, a dramatic conflict of US stated values with our ugly reality.
But the paragraph is also interesting for the way Goldsmith, almost as an aside, “ignore[s] possible cosmopolitan impulses for Snowden’s theft and leaks, which I think damage the case for a pardon for violations of U.S. law.” I take this to argue that if you’re leaking to serve some universal notion of greater good — some sense of world citizenship — then you can’t very well ask to be pardoned by US law. Perhaps, in that case, you can only ask to be pardoned by universal or at least international law. I’ll come back to this.
Goldsmith contrasts the moral and ethical case based on American values with his own, a moral and ethical one that justifies US spying to serve US interests in a complex and dangerous world.
But it is also not a crazy view, and it is also ethically and morally coherent, to think that U.S. electronic intelligence operations abroad were entirely lawful and legitimate efforts to serve U.S. interests in a complex and dangerous world, and that Snowden’s revelations violated his secrecy pledges and U.S. criminal law and did enormous harm to important American interests and values.
For the record, I think Snowden has said some of US spying does serve US interests in a complex and dangerous world. But from that view, the old defender of Article II argues that a President — the guy or gal who by definition is the only one can decide to pardon Snowden — must always adhere to the latter (Goldsmith’s) moral and ethical stance.
Unfortunately for Snowden’s pardon gambit, President Obama, and any one who sits in the Oval Office charged with responsibility for American success around the globe, will (and should) embrace the second moral/ethical perspective, and will not (and should not) countenance the first moral/ethical perspective, which I take to be Snowden’s.
Goldsmith then ends where I began, with a more polite explanation that any president that pardoned Snowden would be inviting metaphorical or literal assassination. He also suggests the precedent would lead to more leaks. But that seems to ignore 1) that Snowden leaked even after seeing what they did to Manning (that is, deterrence doesn’t necessarily work) 2) the Petraeus precedent has already exposed the classification system as one giant load of poo.
Anyway, by my reading, Goldsmith argues that this debate pits those motivated out of American values versus those motivated out of perceived American interests, and that any President must necessarily operate from the latter.
I’m interested in that because I think the former motivation really does explain a goodly number of the leakers and whistleblowers I know. People a generation older than me, I think, may have been true believers in the fight against the Evil Empire during the Cold War, only to realize we risk becoming the Evil Empire they spent their life fighting. Every time I see Bill Binney, he makes morbid cracks about how he was the guy who invented “Collect it all,” back when he was fighting Russia. People a generation younger than me — Snowden, Manning, and likely a lot more — more often responded out of defense of all that is great in America after 9/11, only to find that that we have not adhered to that greatness in prosecuting the war on terror. These are gross generalizations. But I think the conflict is real among a lot of people, and it’s one that will always fight increasingly diligent efforts to tamp down dissent.
That said, I want to note something else Goldsmith did, while making his aside that anyone making a cosmopolitan defense of Snowden cannot ask for a pardon under US law (a view I find fairly persuasive, which may be why I think a reasonable outcome is for Snowden to live out his life in Germany). In making that aside, Goldsmith effectively dismissed the possibility that living US values rather than interests might be both cosmopolitan and in our national interest.
I’ve talked about this repeatedly — the degree to which Snowden’s disclosures (and, to a lesser extent, Manning’s) served to expose some lies that are critical to American hegemony. Our hegemonic position relies — according to people like Goldsmith and, perhaps in reality, though the evidence is mixed — on our global dragnet, which in turn serves our global military presence. But it has also relied on an ideology, every bit as important as ideology was during the Cold War, that espoused democracy and market capitalism and, underscoring both of those, a belief in the worth of every individual (and by extension, individual nation) to compete on equal terms. Without that ideology, we’re just a garden variety empire, which is a lot harder to sustain because it requires more costly (in terms of dollars and bodies) coercion rather than persuasion.
And Snowden’s leaks showed we used our preferential position astride the world’s telecommunications network and our claim to serve freedom of expression to serve as the hegemon. Hell, the aftermath of that shows it even more! Country after country has backed off giving Snowden asylum — the proper cosmopolitan resolution — because the US retains enough raw power and/or access to the fruits of the dragnet to persuade countries that’s not in their “interest.”
This is an issue that has gotten far too little attention in the wake of the Snowden leaks: to what degree is the cost of the Snowden leaks measured in terms of exposing to the subjects of our hegemon facts that their leaders already knew (either because they were and are willing co-participants in the spying or knowledgeable adversaries engaged in equally ambitious but less effective surveillance)? I don’t doubt there are individual programs that have been compromised, though thus far the IC has badly hurt its case by making claims (such as that Al Qaeda only adopted encryption in response to Snowden, or that Snowden taught terrorists how to use burner phones) that are easily falsifiable. But a big part of the leaks are about the degree to which the US can (and does passively in many cases via bulk collection) spy on everyone.
But to me, the big cost has been in terms of exposing America’s hegemonic ideology as the fiction that ideologies always become if they aren’t from the start.
Note, I fully accept that that may be an unacceptable cost. America’s hegemony was already weakening; I believe Snowden’s disclosures simply accelerated that. It is absolutely possible that the weakening of US hegemony will create a vacuum of power that will leave chaos. That chaos may, may have already, led to a desire for strongmen in response. There were outside factors playing into all of this. The Iraq War did far more to rot America’s hegemonic virtue than Edward Snowden’s leaks ever could have. And it’s not clear that an empire based on oil can provide the leadership we need to fight climate change, which will increasingly be the source of chaos. But I accept that it is possible Snowden accelerated a process that may lead to horrible outcomes.
Here’s the thing, though: this younger generation of leakers — of dissident servants of the hegemon — don’t need to be cured of a lifetime of ideology. It may take, as it did with Manning, no more than critical assessment of some flyers confiscated by our so-called partners in liberation for the ideology cementing our hegemonic authority to crumble.
Our hegemony depends on the ideology of our values. That seems to both have been the trigger for and may justify the cosmopolitan interest in exposing our hypocrisy. And whether or not Americans should give a shit about the freedom of non-American subjects of the hegemon, to the extent that servants of that ideology here find the hypocrisy unsustainable, we’re likely to have more Mannings and more Snowdens.
Our global dragnet may very well serve the ethics of those who serve presidentially-defined American interests. As such, Snowden’s leaks are surely seen as unforgivable damage.
But it is also possible that American hegemony is only — was only — sustainable to the degree that we made sure that global dragnet was limited by the values that have always been critical to the ideology underlying our hegemony.