WaPo Is Suppressing Information that Might Debunk Devlin Barrett’s Latest Spin
Last week, I asked the WaPo if they would release the two reports — one from Johns Hopkins professor Matt Green and the other from InfoSec expert Jake Williams — that were the basis of this report on the “Hunter Biden” “laptop.”
I had asked once before, in May 2022.
But since I had originally asked, a bunch of things had happened to make those reports more newsworthy. Hunter Biden had countersued John Paul Mac Isaac (here’s the WaPo’s report). James Comer has stumbled over and over in his unabashed effort to manufacture a scandal (in which the WaPo has played along, still treating it as a credible investigation). Delaware US Attorney David Weiss’ office released a plea deal to which Hunter Biden is expected to plead guilty next week (here’s the WaPo report). IRS agents claiming to be whistleblowers, Gary Shapley and Whistleblower X, shared notes that raised questions about the FBI treatment of the device (but WaPo didn’t mention that in their report). Abbe Lowell claimed that Shapley misidentified Hunter Biden’s interlocutors in some key WhatsApp messages (something else WaPo didn’t mention even while repeating the substance of the contested WhatsApp texts). Denver Riggleman, who has been working as part of a Hunter Biden team to examine what has been released, has alleged some of the data has been manipulated (something WaPo hasn’t bothered to cover at all).
That all led me to start looking at the publicly released (but unreliable) emails at BidenLaptopEmails dot com, where I’ve discovered that during a period when Hunter Biden was getting Ketamine treatment and bookended by two communications from him that indicated he was not getting outside comms, someone:
- Split Hunter’s Uber account, on which his two iCloud accounts had previously been joined
- Accessed Hunter’s rhb iCloud account from a browser
- Changed the password and related phone numbers to his rhb iCloud account
- Installed and gave full access to his droidhunter gmail account a real app, called Hunter, that can send email on someone else’s behalf
- Signed into that droidhunter account using a new device
- Again changed emails and phone numbers associated with his rhb account
- Asked for a full copy of his rhbdc iCloud account
- Reset the password of that rhbdc iCloud account
- Made droidhunter account the notification email for the rhbdc account
- Downloaded all Hunter’s Apple Store purchases
- Made changes to the Uber (and Waze) account associated with an XS phone that would be included in the “laptop”
- Restored rhb as an alternate address to the account
- Restored contacts from an unidentified prior change
- Obtained — including at the droidhunter email account — a download link of the entire rhbdc iCloud account
- Backed up the XS phone to the laptop
- Gotten a trial app of a photo editor
- Backed up an iPad to the laptop
- Changed the iTunes password
- Added the Dr. Fone account, allowing you to adopt a chosen second phone number for a phone, to a second of Hunter’s accounts
- Signed into the droidhunter account from a burner phone
- Restored the prior trusted phone number
- Added software that could record calls
- Started erasing and then locked a laptop — probably the one that would eventually end up in Mac Isaac’s store
- Got a new Mac phone for the droidhunter account
That series of changes are not the only emails in the MarcoPolo set that should raise questions about whether Hunter Biden’s digital identity may have been compromised.
Two that are important to the topic of this post are, first, that a great many devices logged into Hunter Biden’s iCloud accounts in 2018 and 2019, yet many of them don’t appear to be tied to him getting his own new iPhone or computer, and only rarely are the existing devices shut down or passwords changed afterwards. The sheer number should have raised alarms that people had broken into Hunter Biden’s iCloud accounts when the IRS asked Apple for Hunter Biden’s subscriber information in November 2019, in advance of writing a subpoena for the laptop in custody of John Paul Mac Isaac. Additionally, there were a bunch of attempts to get into Hunter Biden’s Venmo account, and the account added two new Remembered Devices within 12 minutes of each other in August 2018, one in the LA foothills and the other in Las Vegas. That and other details (including texts and emails) might have raised questions about whether sex workers from the very same escort service on which the IRS had predicated this entire investigation took steps to compromise Hunter Biden’s devices.
But the timeline above provides some reason to believe that at the time the “laptop” was packaged up for delivery to John Paul Mac Isaac, Hunter Biden did not have complete — if any — control of his own communications.
I wouldn’t be able to prove whether Hunter Biden was hacked during this key period in 2019. It would require subpoena power and access to reliable data. But as it happens, Whistleblower X had subpoena power — and was already watching Hunter Biden closely — in precisely the period this happened.
For those of us who don’t have subpoena power, though, we have to rely on publicly available evidence, filtered through partisan gatekeepers alleged to have tampered with the device.
The two reports done for the WaPo are the only known assessments of the drive containing the “laptop” primarily using forensic — as opposed to a correlative — methodology. The correlative methodology, which shows all the communications on the drive confirm the others, unsurprisingly concludes that the “laptop” came from one of Hunter Biden’s several iCloud accounts.
The forensic methodology looked for digital verification — not just of email signatures, but also of the drive itself. Both Green and Williams raised questions about the treatment of and missing digital signatures on the drive, questions that seem to match what Riggleman’s team is seeing.
Indeed, the concerns that Green and Williams raised may explain something the FBI itself found. Shapley’s notes recorded that on March 31, 2020, someone wrote an email “about quality and completeness of imaged/recovered information from the hard drive” — an email that was being intentionally withheld from the agents (especially Whistleblower X) who might one day testify at trial.
This sounds like it might reflect the same concerns raised by anyone external examining the drive forensically. If it does, it would suggest that some of the irregularities everyone can see in drives released via Rudy Giuliani and Steve Bannon always existed, including in the one shared with the FBI and in any separate drive shared with Republicans in Congress.
Because of all the new questions raised about the “laptop,” and because of the centrality that the Republicans want it to have on the upcoming election, I thought it reasonable to ask the WaPo to do what even the Washington Examiner was willing to do: show their work. While the Examiner’s report from Gus Dimitrelos tellingly excludes many of the details I’ve laid out above and hides both some key later device accesses and types of apps — especially spyware — loaded onto Hunter Biden’s iCloud accounts, while the way the Examiner released it exacerbated the privacy violations on Hunter Biden himself, it nevertheless was useful for explaining how two iCloud accounts were loaded up onto one laptop and how the government was able to obtain WhatsApp texts that don’t show up on the unencrypted parts of the laptop.
After I made several requests, WaPo PR manager Savannah Stephens declined to release the reports, calling the two reports, “foundational reporting documents.”
Marcy, thank you for reaching out. We do not release foundational reporting documents. Our coverage at the time was transparent about how the study was conducted, including this report.
Even though it has two reports that could significantly impact fairly pressing debates — debates the WaPo itself treats as important — the WaPo refuses to release more on these expert reports on the laptop.
Instead of doing that, the WaPo is instead paying Devlin Barrett to do what he does best — write down as true what right wingers tell him to write, not what the public evidence actually shows.
In a story with Matt Viser (the same guy who repeated the content of contested WhatsApp texts without revealing that Abbe Lowell had contested them), Barrett wrote that the testimony of the men he calls “whistleblowers” “show Hunter Biden’s laptop had little role in the investigation into Hunter Biden.”
Barrett and Viser utterly misrepresent the debate over the laptop — dodging the question, in the lede, at least, of whether the laptop can help get to the truth — something once considered the purview of journalism and something WaPo’s own report on this drive had previously done.
For more than two years, Democrats and Republicans have hotly debated the importance of the “Hunter Biden laptop” — insisting that it was either key evidence of corruption or fool’s gold meant to con 2020 voters into abandoning then-candidate Joe Biden.
Both theories were largely wrong, according to two of the agents closest to the investigation of tax crimes allegedly committed by President Biden’s son.
[snip]
But the agents’ accounts also indicate that the laptop played at best a small role in the criminal investigation into potential tax and gun-purchasing violations. Far from a smoking gun, the laptop appears to have been mostly an afterthought to the reams of text messages, emails and other evidence that agents gathered from Hunter Biden’s cloud data. A lawyer for one of those agents said he nevertheless was frustrated by the Justice Department’s refusal to let them review the laptop’s contents.
I’m very interested in the project of this column, because not only is this not what Shapley and Whistleblower X’s testimony said, but it misrepresented and misunderstands how evidence works.
This is a tax investigation. It came from, per Whistleblower X, his examination of what is probably a Russian escort service. But it’s a tax investigation: it relies on financial data that comes directly from banks and other financial institutions, institutions that are — to the extent they aren’t tainted by identity theft or hacking, like people seem to have tried to do to Hunter Biden’s Venmo — inherently reliable.
As for emails and texts, the IRS agents’ testimony (taken in conjunction with the report that the Washington Examiner was ethical enough to release), shows that the IRS didn’t obtain what is probably Hunter Biden’s rhb iCloud account — from which the cited, contested WhatsApp messages were probably obtained a second time — until August 2020, after it got some of the same material on the laptop. That potential taint may be why someone told Barrett to downplay the import of the laptop.
While the laptop may not have played a key role in substantiating a tax case against Hunter Biden, it may well have tainted the evidence in the case. It may well be part of the reason why Hunter Biden is getting to plead to misdemeanor rather than felony tax charges — because as even Whistleblower X explained that he had been told, there are emails that raised concerns about whether this could be charged at all, suggesting this case couldn’t withstand discovery.
Plus, WaPo is being coy here: The laptop may have played little part in a tax investigation reliant on bank records. But it did play a central part in allegations, including WaPo’s own reporting, of foreign influence peddling involving (among others), Burisma, the hack of which became public between the time the IRS started using this laptop as evidence and the time they learned Rudy Giuliani had a role in it.
That part is all pitch, though — yet another instance where Devlin Barrett writes down what right wingers tell him to say and WaPo reports it as if it were true. It’s what WaPo pays him to do.
It’s the claims about the laptop — from an outlet sitting on two reports that raise questions about its reliability — that I find especially curious. Start with this paragraph, which conflates the steps FBI took in November 2019 to authenticate that the laptop was Hunter Biden’s — subscriber information from Apple, a purchase record in Delaware, two but maybe only two phone calls with Mac Isaac, and “other intelligence” — with what the AUSA on the case said about it almost a year later.
After being handed the device by a Wilmington, Del., computer shop owner in 2019, the FBI quickly concluded by examining computer data as well as Hunter Biden’s phone records that the laptop was genuinely his and did not seem to have been tampered with or manipulated.
That last bit — “did not seem to have been tampered with or manipulated” — published by an outlet sitting on two reports that show the laptop was tampered with? It is a paraphrase from a meeting in October 2020, not a description of legal process served in November 2019. And therein lies a big part of the scandal.
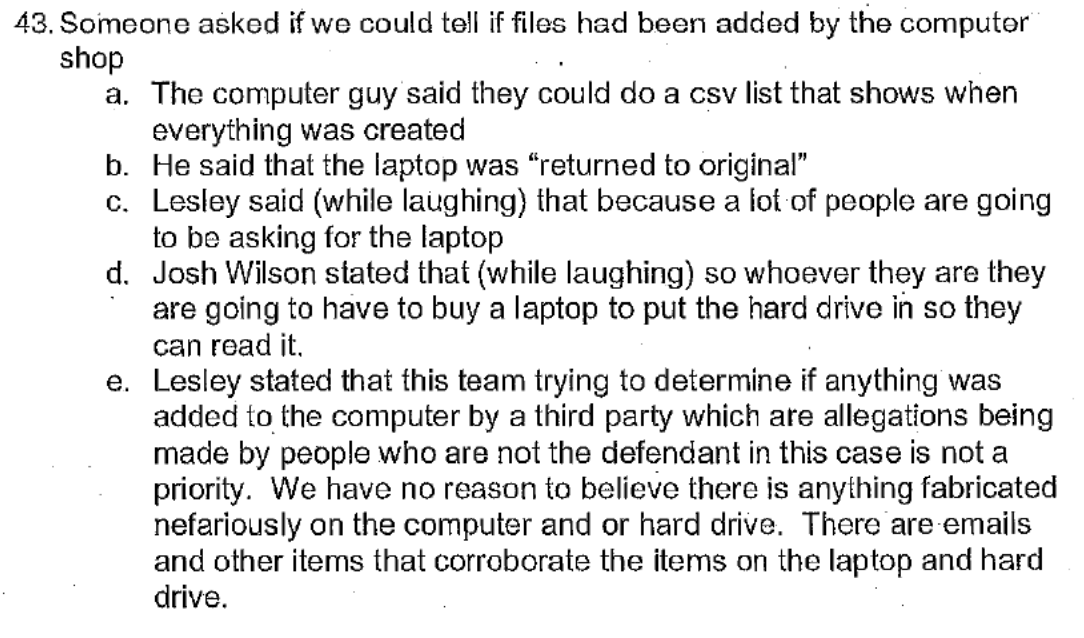
In the actual quote, Wolf — painted as the bad guy here by the IRS agents — was saying that it “is not a priority” for the investigative team to see “if anything was added to the computer by a third party” even after learning that the lawyer for the President, whose demands for this investigation had raised influence problems from the start of the investigation, had some kind of tie to it.
This is as if Peter Strzok, rather than just failing to make sure people writing FISA applications had adverse information about the Steele dossier (which is what frothers think the IG Report showed), had instead said, “fuck it, I don’t care if it is tainted.” These notes show the Hunter Biden investigative team did what right wingers accuse the Crossfire Hurricane team of doing, blowing off the import of the involvement of a campaign in a key piece of evidence.
When the WaPo conflates those two items again later in the piece, they date the quote to May 2020.
Democrats suggested the data might have been doctored or possibly a Russian-backed disinformation campaign. The information provided by IRS agents to Congress seems to put both the accusations and counter-accusations to rest.
FBI agents were able to determine in early November 2019 that the device they had was registered to Hunter Biden, and phone records showed he had been in contact with the computer shop owner.
“We have no reason to believe there is anything fabricated nefariously on the computer and or hard drive. There are emails and other items that corroborate the items on the laptop,” Shapley wrote in notes that dated that determination to around May 2020.
Dating Lesley Wolf’s comment saying they had no reason to believe anything on the laptop was fabricated to May 2020 is either a deliberate error or a confession that two journalists proclaiming the laptop to lack any taint have no fucking clue what they’re reading.
Wolf said this, at a meeting the investigative team had on October 22, 2020, in the wake of the discovery that Rudy Giuliani had some tie to the laptop, as the team scrambled to memorialize how they had treated a key piece of evidence about which a bunch of questions would now be raised.
A Yes. So there are a couple significant parts of this. One was that, at this time, the laptop was a very big story, so we were just making sure that everything was being handled appropriately.
So we wanted to go through the timeline of what happened with the laptop and devices.
Because the laptop had become a huge story, “we were just making sure that everything was being handled appropriately,” Devlin Barrett’s star “whistleblower” explained.
And Shapley shows Wolf saying that they had no knowledge, in October 2020, of any fabrications on the laptop. But he records her saying that after “computer guy” said “they could do a csv list that shows when everything was created.”
That is, Wolf said this after “computer guy” described something they had not yet done ten months after obtaining the laptop, had not yet done two months after getting warrants relying on the laptop, that they would need to do to make sure the laptop had not been altered by third parties. Wolf said this after “computer guy” described that the FBI had not done very basic things to verify the integrity of the laptop they should have done ten months earlier, before relying on it.
Again, I’m not sure whether WaPo’s journalists are dishonest or just stupid. But this exchange is critical for another reason. Lesley Wolf’s assertion about the integrity of the laptop relied on correlation: by matching emails on the laptop with emails that could be obtained directly from the provider.
There are emails and other items hat corroborate the items on the laptop and hard dive.
This is the method that Washington Examiner’s expert used to proclaim the laptop authentic. It’s the method that a bunch of other right wing journalists have gotten experts to use to validate the laptop.
If you steal someone’s iCloud account, the way to prove that it is authentic is by proving that it is their iCloud account, which is what correlation does.
But “computer guy” was suggesting using a forensic method, ten months after the fact, to test the integrity of the laptop itself. DDOSecrets has done this test on the publicly released emails — and half of them have a last modified date of February 11, 2019, right towards the end of the timeline I show above.
Lesley Wolf made her comment on October 22, 2020. No one in Gary Shapley’s interview asked him what happened after that. Nor does Devlin Barrett seem curious to ask.
If “computer guy” subsequently did this test, there’s good reason to believe he would have found what DDOSecrets did: that while these emails match the ones in Hunter Biden’s accounts, they were all packaged up on February 11, 2019, at a time it’s not clear Hunter Biden had control of his own digital accounts.
If you use a forensic method to validate these files, you’re not going to get the same results as a correlative method. That’s why it would be very useful for the debate about the laptop for WaPo to share the two known expert reports done using forensic methods on the drive itself, rather than correlation.
There’s one more hilarious thing about this Devlin Barrett creation. He, predictably, repeats his “whistleblower’s” complaints about not getting stuff pertaining to the laptop.
Shapley said a federal prosecutor on the case, Lesley Wolf, told him that the IRS agents couldn’t see the laptop. “At some point, they were going to give a redacted version, but we don’t even think we got a full — even a redacted version. We only got piecemeal items,” Shapley told the committee, voicing his frustration that he would have liked to see all the data.
Devlin Barrett — dishonest or stupid? — quotes Shapley’s testimony out of context. The full quotation makes it clear Shapley is referring, again, to a discussion that took place on October 22, 2020. More importantly, Shapley is not referring to the laptop!!
And when it came down to item number 33 on page 2, Special Agent [Whistleblower X] is saying like, well, I haven’t seen this information. And AUSA Lesley Wolf says, well, you haven’t seen it because, for a variety of reasons, they kept it from the agents. And she said that at some point they were going to give a redacted version, but we don’t even think we got a full — even a redacted version. We only got piecemeal items [my emphasis]
That particular quotation, identified clearly as item number 33, is the report about the laptop — which I’ll copy again here to make it so easy even Devlin Barrett might understand it:
To help a right winger allege corruption, Devlin Barrett quotes his complaint that his team was not given the actual forensic report about the laptop. Corruption, in this story, is withholding a forensic report that might tell people what they need to know about the laptop.
And yet that is precisely what WaPo itself refuses to do: release two reports that raise questions about the quality and completeness of the drive.
According to Devlin Barrett’s own standard — at least the standard he applies when he’s parroting right wingers — withholding such a report is a sign of corruption.
Even the plain language of Gary Shapley’s contemporaneous notes show that Devlin’s claim that, “information provided by IRS agents to Congress” “put[s] … the accusations” that “the data might have been doctored or possibly a Russian-backed disinformation campaign” … “to rest” is wildly false (dishonest or stupid?). It does the opposite: It shows that ten months after beginning to rely on the laptop, the FBI still had not done basic forensic checks of the data on it and the AUSA leading the investigation didn’t think doing so was a priority.
That should be the story. That’s the scandal.
And true to form, Devlin Barrett spins the exactly opposite tale.
The WaPo has in its possession some of the only available information that can help to explain what the FBI saw by March 2020, two independent equivalent reports to the one that Shapley implies it is corrupt to withhold.
And unlike the Washington Examiner, they won’t release it.