“Super:” The Day after IRS Got a Warrant for the Hunter Biden Laptop, DOJ Sent Bill Barr a Laptop
Thanks to Gary Shapley, we have notes from an October 22, 2020 meeting at which the Hunter Biden investigative team scrambled to make sure they had taken care on their handling of the two devices — a laptop that once belonged to Hunter Biden, and a hard drive containing the attempted recovery of the items on the laptop — turned over by John Paul Mac Isaac.
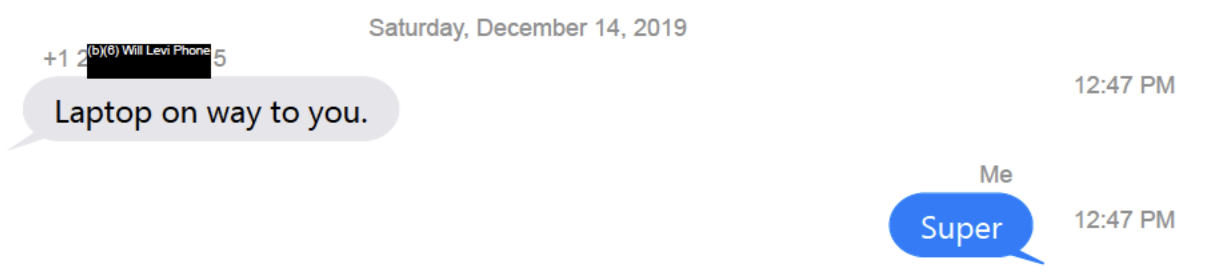
Among other things, Shapley’s notes reflect that on December 9, 2019, the FBI took possession of the laptop. Even before that, starting on December 3, IRS case agent Joseph Ziegler started drafting a warrant to access it.
On December 12, DOJ’s Office of Enforcement Operations authorized seeking a warrant for it. Then on December 13, Ziegler got a magistrate judge, probably in Delaware, to approve his warrant.
In advance of the October 22 meeting, on October 19, Shapley sent an email that has not been made public. In it, he expressed a belief that John Durham had a copy of the laptop.
On October 19th, 2020, I emailed Assistant United States Attorney Wolf: “We need to talk about the computer. It appears the FBI is making certain representations about the device, and the only reason we know what is on the device is because of the IRS CI affiant search warrant that allowed access to the documents. If Durham also executed a search warrant on a device, we need to know so that my leadership is informed. My management has to be looped into whatever the FBI is doing with the laptop. It is IRS CI’s responsibility to know what is happening. Let me know when I can be briefed on this issue.” [my emphasis]
That’s one of the reasons I find it acutely interesting that on December 14 — the day after a magistrate approved the first known warrant for the “Hunter Biden” “laptop,” Will Levi — who was heavily involved in Barr’s micromanagement of the Durham investigation (including in setting up meetings with the UK, Australia, and Italy) — texted his boss’ personal cell phone and told him a laptop was “on way to you.”
Leading up to December 14, Durham was in the thick of a Russian-Ukrainian disinformation operation. It is totally possible that he did get a copy of the laptop. That’s one reason I pointed to DOJ’s discussion of Patrick Byrne’s disinformation in August 2019. Bill Barr’s DOJ was willing to go anywhere to get information discrediting the Russian investigation into Trump, even Russian-backed sources.
Durham’s consideration of Ukrainian disinformation became a prominent issue during the impeachment investigation, the next month, September 2019.
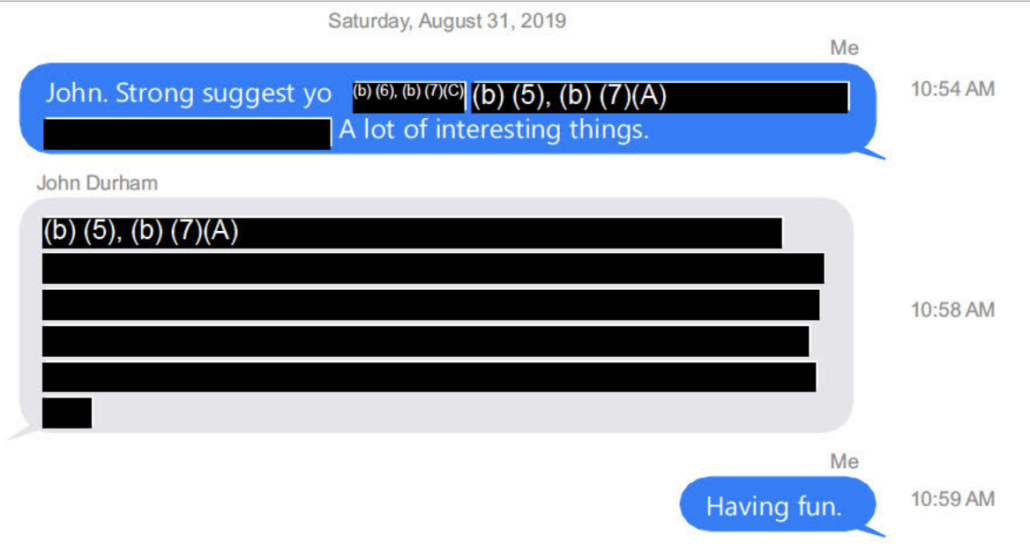
In the FOIA releases showing Barr’s involvement in the Durham investigation released so far, it’s not clear when Durham met with the Ukrainians. It could be this exchange on August 31, 2019, in which Barr suggested Durham reach out to someone. After Durham responded, Barr commented, Having fun.
Levi sent Barr a text, which remained totally redacted on most recent release, the day after the whistleblower complaint went public.
That may not be related.
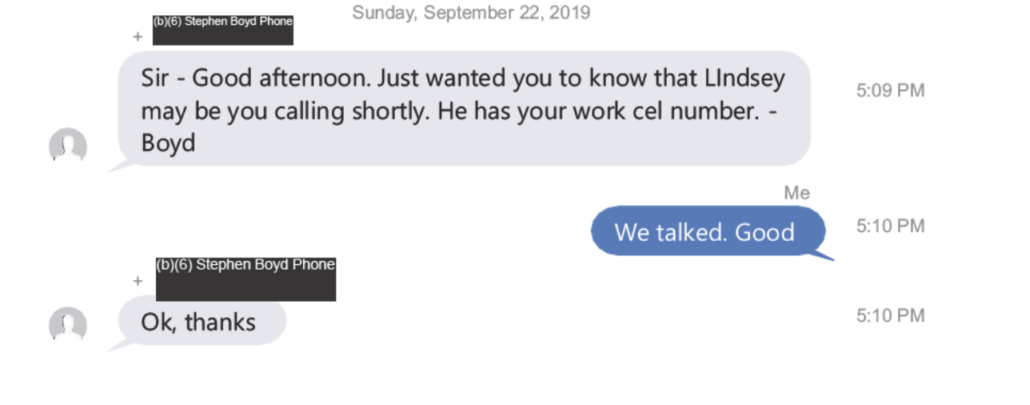
But by September 22, Barr was definitely in damage control mode, reaching out to Lindsey Graham.
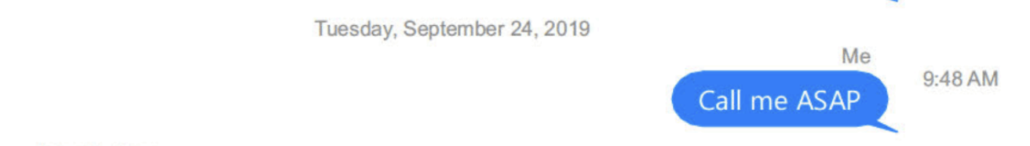
On the morning of September 24, the day Nancy Pelosi would announce support for impeachment and the day the White House declassified “the perfect transcript” showing Trump instructed Volodymyr Zelenskyy, two months earlier, to coordinate with Barr on investigations of Biden, Barr texted Durham and told him to call ASAP.
That night, Barr texted Will Levi to call ASAP.
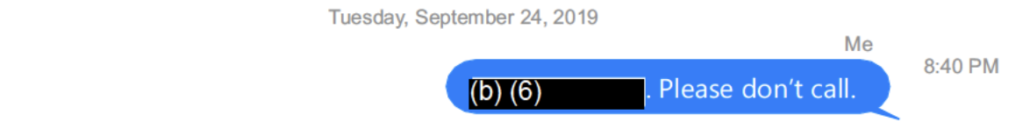
An hour and a half later, he texted what is probably Eric Herschmann — who at that point was still at Marc Kasowitz’s firm (though he would soon join Trump’s impeachment team) — and instructed him not to call.
Herschmann, of course, would attempt to pitch the laptop himself a year later, before Rudy blew its credibility.
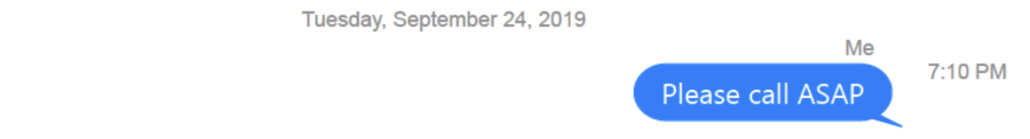
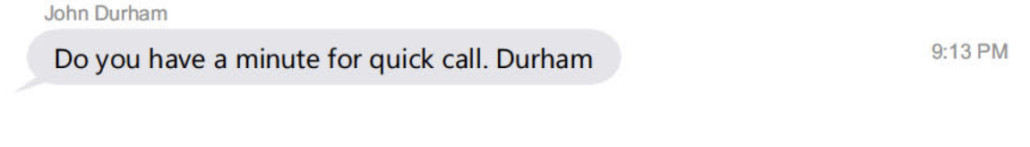
Then later on the night of September 24, Durham texted Barr asking to talk, which may have been a second call that day.
The next day, September 25, DOJ issued a statement revealing that Durham had received information from several Ukrainians who weren’t part of government.
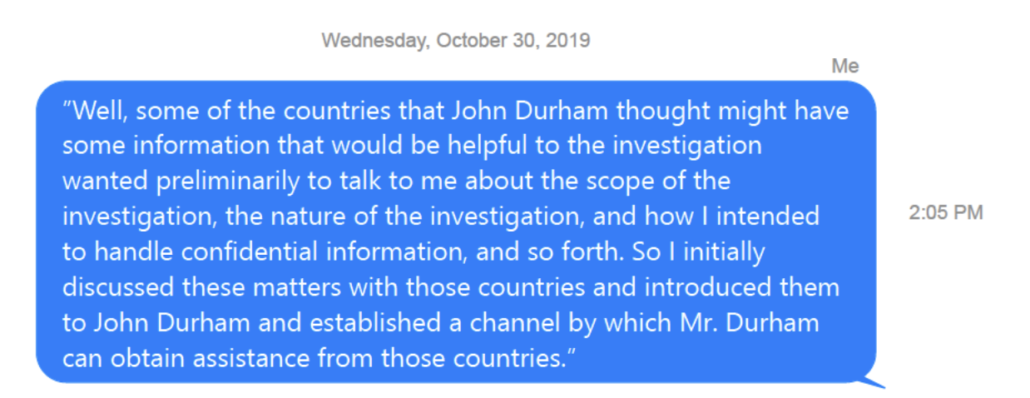
A Department of Justice team led by U.S. Attorney John Durham is separately exploring the extent to which a number of countries, including Ukraine, played a role in the counterintelligence investigation directed at the Trump campaign during the 2016 election,” DOJ spokeswoman Kerri Kupec said Wednesday. “While the Attorney General has yet to contact Ukraine in connection with this investigation, certain Ukrainians who are not members of the government have volunteered information to Mr. Durham, which he is evaluating.”
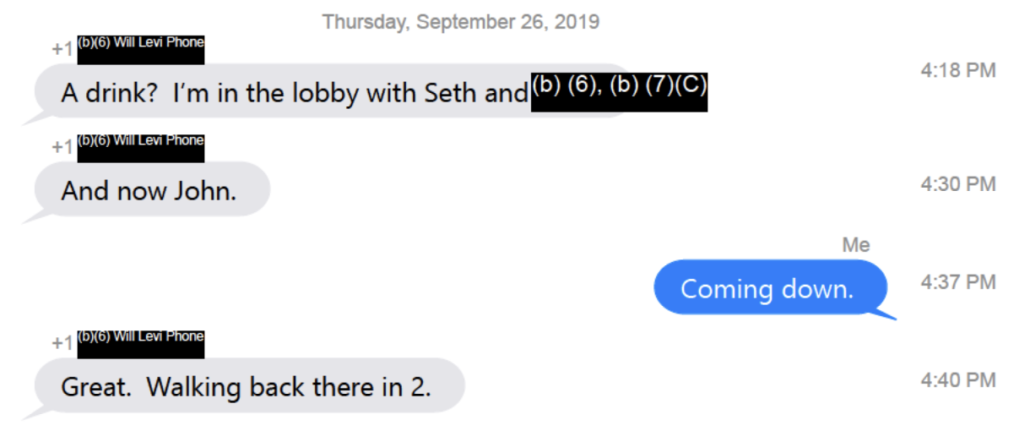
At 3:44 PM on September 26, the day the White House released the whistleblower complaint, someone from Durham’s team — probably Durham himself — participated in a chat with 8 people.
Less than an hour later, a bunch of people — including Will Levi, Seth DuCharme, and “John” — convened in a lobby bar together, waiting for Barr to arrive.
The following day, when Kurt Volker resigned, there was another group chat.
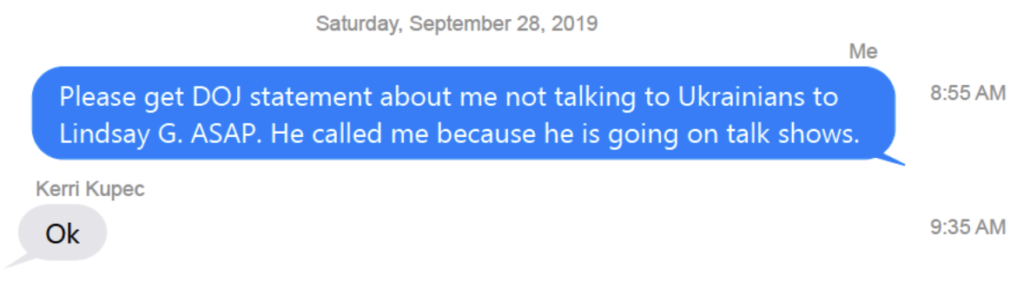
Barr was still focused on CYA regarding his own involvement. In advance of Lindsey Graham going on the Sunday shows, Barr made sure to get Lindsey his statement claiming not to have spoken to the Ukrainians personally.
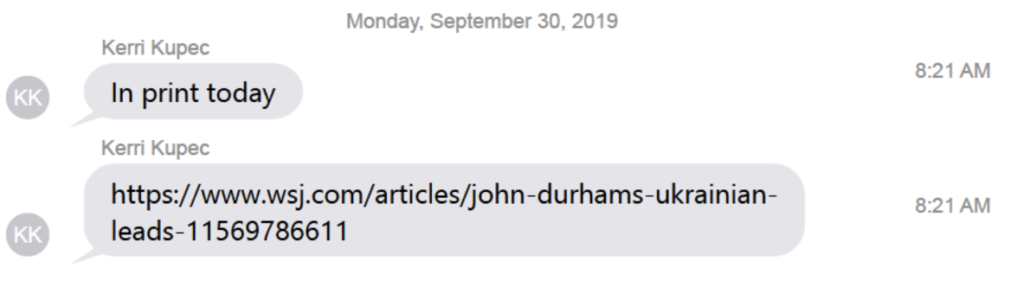
On September 29, Michael Mukasey did a column in the WSJ where he pitched the value of speaking to Ukrainians. He suggested that Durham might find the Ukraine leads Trump was looking for.
That Justice Department statement makes explicit that the president never spoke with Attorney General William Barr “about having Ukraine investigate anything relating to former Vice President Biden or his son” or asked him to contact Ukraine “on this or any other matter,” and that the attorney general has not communicated at all with Ukraine. It also contains the following morsel: “A Department of Justice team led by U.S. Attorney John Durham is separately exploring the extent to which a number of countries, including Ukraine, played a role in the counterintelligence investigation directed at the Trump campaign during the 2016 election. While the Attorney General has yet to contact Ukraine in connection with this investigation, certain Ukrainians who are not members of the government have volunteered information to Mr. Durham, which he is evaluating.”
The definitive answer to the obvious question—what’s that about?—is known only to Mr. Durham and his colleagues. But publicly available reports, including by Andrew McCarthy in his new book, “Ball of Collusion,” suggest that during the 2016 campaign the Federal Bureau of Investigation tried to get evidence from Ukrainian government officials against Mr. Trump’s campaign manager, Paul Manafort, to pressure him into cooperating against Mr. Trump. When you grope through the miasma of Slavic names and follow the daisy chain of related people and entities, it appears that Ukrainian officials who backed the Clinton campaign provided information that generated the investigation of Mr. Manafort—acts that one Ukrainian court has said violated Ukrainian law and “led to interference in the electoral processes of the United States in 2016 and harmed the interests of Ukraine as a state.”
I can fathom no way Mukasey would have written this without Barr’s support, and so Barr’s support for continued outreach with Durham.
Barr’s press secretary Kerri Kupec sent him the Mukasey column first thing the next day.
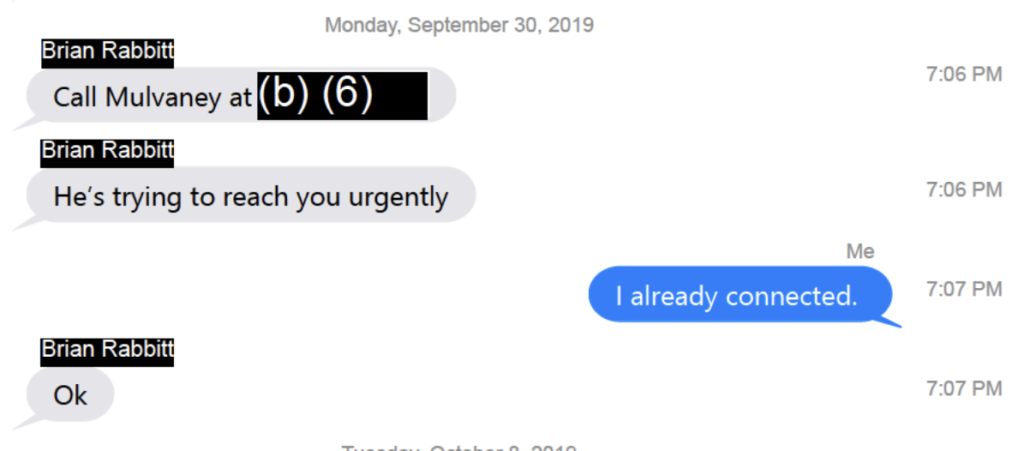
On September 30, Brian Rabbitt told Barr to contact Mick Mulvaney.
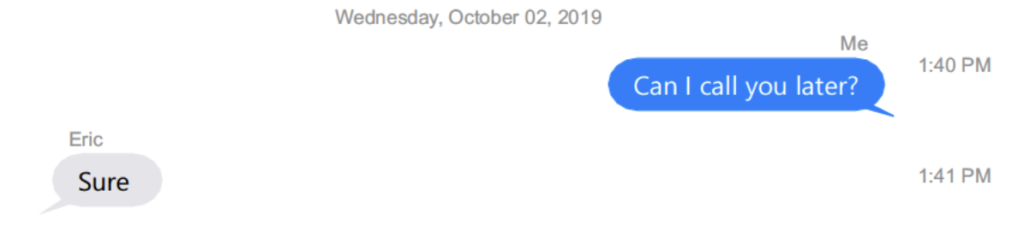
On October 2, Barr asked the same Eric — probably Herschman given the person’s contacts with Jared Kushner and Pat Cipollone — if he could call.
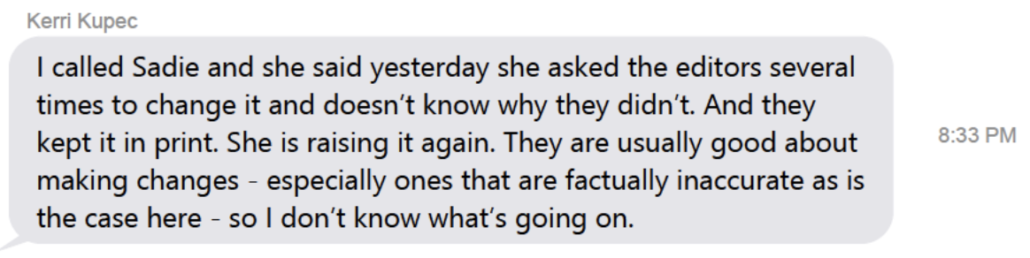
Later on October 2, Kerri Kupec apologized to Barr that “Sadie” hadn’t gotten editors to change a particular story, probably a reference to this WSJ story, which discusses Barr’s request that Trump give introductions to some foreign leaders.
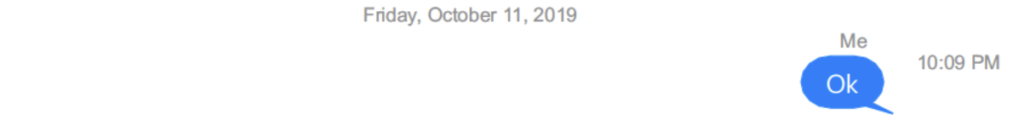
On October 11, the day after Igor Fruman and Lev Parnas were arrested, Barr sent Eric a one word text — “Ok.”
On October 30, the day after the Democrats released the impeachment resolution, Kupec sent Barr the statement he had made about Ukraine back in September.
A minute later Barr sent that statement to Will Levi, with no further comment.
In spite of all this, DOJ still made little effort to convince Trump to stop Rudy Giuliani from flying to meet Andrii Derkach in December 2019, in precisely the same period Levi sent Barr a laptop. FBI prepared but did not give Rudy a defensive briefing.
Sometime shortly after this, in 2020, IRS Agent Joseph Ziegler got a new supervisor, Gary Shapley. Shapley replaced Matt Kutz, who had concerns about — and documented — what are probably confrontation clause problems (meaning the investigation was relying on sources that Hunter Biden would never be able to cross-examine) and Trump’s push for this investigation.
Around the same time in 2019, I had emails being sent to me and the Hunter — and the prosecutors on the case, the Hunter Biden prosecutors, from my IRS supervisor. So this was Matt Kutz still. From what I was told by various people in my agency, my IRS supervisor, Matt Kutz, created memos which he put in the investigative files regarding the investigation potentially violating the subject’s Sixth Amendment rights. He also referred to Donald Trump’s tweets at the time.
I recall that at one point I had to go around my supervisor and ask his boss, ASAC George Murphy, to tell him to stop sending me and the Hunter Biden prosecution team these emails and that I was searching media articles on a weekly basis and was aware of everything being written in the media regarding the case.
[snip]
A So it was actually Matthew Kutz. He was my supervisor at the time and from the articles that he was sending me, I would say he had more of a liberal view than I had and it was pretty obvious from the things he would send me and discuss. And that’s just me making an observation.
So I later found out about these memos that were put in the file regarding the issues that he saw with the investigation, the fact that we even had it opened. So I only learned about those after. And then it came to a point to where he’s sending us so many media articles about different issues that I had to tell him stop, please.
And I had to go around him. And that’s when I went to my ASAC at the time, George Murphy, who was above him.
Per Shapley’s testimony, he became the primary managerial liaison interacting directly with David Weiss’ office in October 2020, the same month as the laptop was made public.
By that point, someone else was in charge of ingesting Russian disinformation. Scott Brady’s assignment pushing Russian from Rudy may have simply represented a reassignment of the task, from Durham to Brady.
But Durham didn’t stop thinking about it. On January 11, Durham sent an aide the group chats that had occurred at the height of DOJ’s panic on September 26 and 27.
January 11 is the day Treasury sanctioned several more Ukrainians as part of Andrii Derkach’s 2020 influence operation.
Former Ukrainian Government officials Konstantin Kulyk, Oleksandr Onyshchenko, Andriy Telizhenko, and current Ukraine Member of Parliament Oleksandr Dubinsky have publicly appeared or affiliated themselves with Derkach through the coordinated dissemination and promotion of fraudulent and unsubstantiated allegations involving a U.S. political candidate. They have made repeated public statements to advance disinformation narratives that U.S. government officials have engaged in corrupt dealings in Ukraine.
I don’t know whether Bill Barr got a copy of the laptop or not.
I know that years latter — at a time when he was selling a book that attempted to distance himself from all this criming — Barr was nevertheless joining in false claims about the laptop.
So when former staffer Larry Kudlow on Thursday interviewed former attorney general William P. Barr for his Fox Business show, the conversation operated from shared assumptions about Trump’s successes and the toxicity of the political left. The result was that Barr outlined a remarkable hierarchy of importance for actions that might have affected the results of a presidential contest.
Russian interference in 2016, he said, was just “some embarrassing emails about Hillary Clinton and Bernie.” The effort to “suppress” information about Hunter Biden’s laptop, meanwhile, was “probably even more outrageous” and “had much more effect on an election.”
And I know that when Hank Johnson mocked John Durham because he hadn’t indicted Hillary Clinton, Barack Obama, Joe Biden — and “couldn’t even indict Hunter Biden” — Durham responded, “We didn’t investigate Mr. Hunter Biden.”
Obtaining a warrant for Hunter Biden’s laptop would surely qualify as investigating Mr. Hunter Biden.
In 2020, the right wing’s favorite so-called whistleblower believed that John Durham got a copy. And one day after the IRS first obtained a warrant for the laptop, DOJ sent the Attorney General, who was micromanaging the Durham witch hunt, a laptop.