Ron Wyden’s History of Bogus Excuses for Not Counting 702 US Person Collection
The other day, Ron Wyden gave a long speech on FISA Section 702, purportedly explaining why he was voting against Dan Coats to be Director of National Intelligence. Wyden voted against Coats because his former colleague would not commit to providing a number of the number of Americans swept up under Section 702. Given that it’s always a good idea to read Wyden closely, I wanted to summarize what he said. I’ll look at his complaints in a separate post, but for now I wanted to focus on Wyden’s description of the bogus explanations James Clapper and others gave Wyden in his past efforts to get the number of Americans sucked up in 702. I summarized the known exchanges that occurred on this issue before Clapper’s famous “not wittingly” lie here.
In 2011, both Wyden and John Bates were asking for numbers at the same time — NSA refused both
The first request for a count is temporally significant(update: I think I just missed this one in the past). In April 2011, Wyden and Mark Udall asked for the number.
In April of 2011, our former colleague, Senator Mark Udall, and I then asked the Director of National Intelligence, James Clapper, for an estimate.
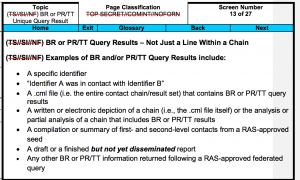
According to Clapper’s response, they sent a written letter with the request on July 14, 2011. The timing of this request is critically important because it means Wyden and Udall made the request during the period when NSA and FISA Judge John Bates were discussing the upstream violations (see this post for a timeline). As part of that long discussion Bates had NSA do analysis of how often it collected US person communications that were completely unrelated to a targeted one (MCTs). Once Bates understood the scope of the problem, he asked how many US person communications it collected that were a positive hit on the target that were the only communication collected (SCTs).
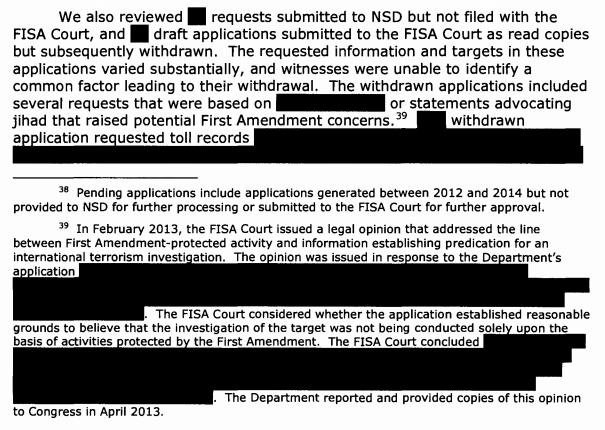
But the timing demands even closer scrutiny. On July 8, John Bates went to DOJ to express “serious concerns” — basically, warning them he might not be able to reauthorize upstream surveillance. On July 14 — the same day Wyden and Udall asked Clapper for this information — DOJ asked Bates for another extension to respond to his questions, promising more information. Clapper blew off Wyden and Udall’s request in what must be record time — on July 26. On August 16, DOJ provided their promised additional information to Bates. That ended up being a count of how many Americans were affected in MCTs.
That means Clapper claimed he couldn’t offer a number even as NSA was doing precisely the kind of count that Wyden and Udall wanted, albeit for just one kind of 702 collection. And, as Wyden suggested in his speech, Clapper’s answer was non-responsive, answering how many US persons had their communications reviewed, rather than how many had their communications collected.
In July of that year, the director wrote back and said, and I quote, it was not reasonably possible to identify the number of people located in the United States whose communications may have been reviewed under the authority of the Foreign Intelligence Surveillance Act. He suggested reviewing the classified number of disseminated intelligence reports containing a reference to a U.S. Person, but that is very different than the number of Americans whose communications have been collected in the first place. And that’s what this is all about.
Then, after the government presented the information on how many US persons were collected via MCTs to Bates in August, Bates asked them to go back and count SCTs.
NSA refused.
Both FISC and members of SSCI were asking for this information in the same time period, and NSA refused to provide the count.
Since NSA wouldn’t help him, Bates invented an estimate himself, calculating that some 46,000 entirely domestic communications were collected under upstream collection each year.
NSA’s manual review focused on examining the MCTs acquired through NSA’s upstream collection in order to assess whether any contained wholly domestic communications. Sept. 7, 2011 Hearing Tr. at 13-14. As a result, once NSA determined that a transaction contained a single discrete communication, no further analysis of that transaction was done. See Aug. 16 Submission at 3. After the Court expressed concern that this category of transactions might also contain wholly domestic communications, NSA conducted a further review. See Sept. 9 Submission at 4. NSA ultimately did not provide the Court with an estimate of the number of wholly domestic “about” SCTs that may be acquired through its upstream collection. Instead, NSA has concluded that “the probability of encountering wholly domestic communications in transactions that feature only a single, discrete communication should be smaller — and certainly no greater — than potentially encountering wholly domestic communications within MCTs.” Sept. 13 Submission at 2.
The Court understands this to mean that the percentage of wholly domestic communications within the universe of SCTs acquired through NSA’s upstream collection should not exceed the percentage of MCTs within its statistical sample. Since NSA found 10 MCTs with wholly domestic communications within the 5,081 MCTs reviewed, the relevant percentage is .197% (10/5,081). Aug. 16 Submission at 5.
NSA’s manual review found that approximately 90% of the 50,440 transactions in the same were SCTs. Id. at 3. Ninety percent of the approximately 13, 25 million total Internet transactions acquired by NSA through its upstream collection during the six-month period, works out to be approximately 11,925,000 transactions. Those 11,925,000 transactions would constitute the universe of SCTs acquired during the six-month period, and .197% of that universe would be approximately 23,000 wholly domestic SCTs. Thus, NSA may be acquiring as many as 46,000 wholly domestic “about” SCTs each year, in addition to the 2,000-10,000 MCTs referenced above.
Presumably, Wyden learned that NSA had been doing such a count in October, well after Clapper had given his first non-responsive answer.
The 2012 privacy violation claim
Wyden skips the next request he made, when on May 4, 2012, he and Udall asked the Intelligence Community Inspector General Charles McCullough for a number (I laid out the timing of the request in this post). When they also tried to include language in the FAA reauthorization requiring the IGs to come up with a number, SSCI refused, citing their outstanding request to McCullough. Of course, McCullough did not get back to the Senators with his refusal to do such a count until after the bill had passed out of committee. He responded by saying NSA IG George Ellard didn’t have the capacity for such a review, and besides, it would violate the privacy of Americans to find out how much NSA was violating their privacy.
I defer to his conclusion that obtaining such an estimate was beyond the capacity of his office and dedicating sufficient additional resources would likely impede the NSA’s mission. He further stated that his office and NSA leadership agreed that an IG review of the sort suggested would itself violate the privacy of U.S. persons.
Clapper blows off 12 Senators
In response, Wyden rounded up some privacy minded Senators to sign onto a letter asking for an estimate of the number. In this week’s speech, Wyden noted that he said he’d be willing to take an estimate. He didn’t remind his listeners that he and his friends also asked whether such an estimate had been done.
- Have any entities made any estimates — even imprecise estimates — about how many US communications have been collected under section 702 authorities?
The answer to that question — at least with regards to upstream collection — was yes. NSA had estimated the MCTs and Bates, using their estimate, had made an even rougher estimate of the SCTs. But as I noted here, members of Congress relying on the purported disclosure to Congress about the upstream violations wouldn’t know that — or that the upstream violations involved entirely US person collection. As Wyden noted in his speech, Congress didn’t get this information before the reauthorized FAA.
We still got no answer. And section 702 was reauthorized without this necessary information.
Clapper’s least untruthful answer
Wyden also doesn’t address Clapper’s famous March 2013 lie. Since the exposure of the phone dragnet, most discussions have assumed Wyden was probing only about that program. But the question, as asked, absolutely applied to incidental collection.
Wyden: Does the NSA collect any type of data, at all, on millions, or hundreds of millions of Americans?
Clapper: No sir.
Wyden: It does not?
Clapper: There are cases where they could inadvertently, perhaps, uh, collect, but not wittingly.
Indeed, several of Clapper’s many excuses claim he was thinking of content when he responded. Even if he were, his first answer would still be yes: the NSA collects on so many millions of Americans incidentally that it refuses to count it. But Clapper’s “not wittingly” response is almost certainly not a goof, since he gave it after Wyden had provided a day’s warning the question would be asked and after two different John Bates’ opinions that made it clear that he would forgive the collection of content so long as NSA didn’t know about it, but once they knew about it, then it would become illegal. The not wittingly response reinforces my firm belief that the reason the government refuses to count this is because then a great deal of their Section 702 collection would be deemed illegal under those two FISC precedents.
Clapper’s blow-off becomes Dan Coats’ blow-off
Which is where Wyden brings us up to date, with both house of Congress asking for such a number and — after promises it would be forthcoming — not getting it.
So last year looking at the prospect of the law coming up, there was a renewed effort to find out how many law-abiding Americans are getting swept up in these searches of foreigners. In April 2016 a bipartisan letter from members of the House Judiciary Committee asked the Director of National Intelligence for a public estimate of the number of communications or transactions involving United States persons are collected under section 702 on an annual basis. This letter coming from the House Democrats and Republicans, again asked for a rough estimate. This bipartisan group suggested working with director clapper to determine the methodology to get this estimate.
In December there were hints in the news media that something might be forthcoming, but now we’re here with a new administration considering the nomination of the next head of the intelligence community who has said that reauthorizing section 702 is his top legislative priority and that there is no answer in sight to the question Democrats and Republicans have been asking for over six years. How many innocent law-abiding Americans are getting swept up in these searches under a law that targets foreigners overseas?
There’s one tiny tidbit he doesn’t mention here. Coats never answered that he wouldn’t provide an answer. Rather, he said he didn’t understand the technical difficulties behind providing one (not even after participating in the 2012 vote where this was discussed). In his confirmation hearing, Coats explained one reason why he couldn’t learn what the technical difficulties were before he was confirmed. When he resigned the Senate, his clearance had lapsed, and during his confirmation process, his new clearance was being processed. That meant that for this — and any other classified question that Coats might want to consider anew — he was unable to get information.
The Senate doesn’t seem to care about this serial obstruction, however. Coats was confirmed with an 85-12 vote, with the following Senators voting against confirmation.
Baldwin (D-WI)
Booker (D-NJ)
Duckworth (D-IL)
Gillibrand (D-NY)
Harris (D-CA)
Markey (D-MA)
Merkley (D-OR)
Paul (R-KY)
Sanders (I-VT)
Udall (D-NM)
Warren (D-MA)
Wyden (D-OR)
Given how hard the IC is trying to hide this, the actual exposure of US persons must be fairly significant. We’ll see whether Congress finds another way to force this information out of the IC.
Updated with more granular timing on the 2011 exchange.