On June 10, 2017, according to affidavits submitted as part of the Mueller investigation, Roger Stone DMed Julian Assange and told him he was doing everything he could to “address the issues at the highest level of Government.”
57. On or about June 10, 2017, Roger Stone wrote to Target Account 2, “I am doing everything possible to address the issues at the highest level of Government. Fed treatment of you and Wikileaks is an outrage. Must be circumspect in this forum as experience demonstrates it is monitored. Best regards R.” Target Account 2 wrote back, “Appreciated. Of course it is!”
On June 19, 2017, according to the Mueller Report, the President dictated a message for Corey Lewandowski to take to Jeff Sessions, telling the (recused) Attorney General to meet with Robert Mueller and order him to limit his investigation only to future election meddling, not the election meddling that had gotten Trump elected.
During the June 19 meeting, Lewandowski recalled that, after some small talk, the President brought up Sessions and criticized his recusal from the Russia investigation.605 The President told Lewandowski that Sessions was weak and that if the President had known about the likelihood of recusal in advance, he would not have appointed Sessions.606 The President then asked Lewandowski to deliver a message to Sessions and said “write this down.” 607 This was the first time the President had asked Lewandowski to take dictation, and Lewandowski wrote as fast as possible to make sure he captured the content correctly.608 The President directed that Sessions should give a speech publicly announcing:
I know that I recused myself from certain things having to do with specific areas. But our POTUS . .. is being treated very unfairly. He shouldn’t have a Special Prosecutor/Counsel b/c he hasn’t done anything wrong. I was on the campaign w/ him for nine months, there were no Russians involved with him. I know it for a fact b/c I was there. He didn’t do anything wrong except he ran the greatest campaign in American history.609
The dictated message went on to state that Sessions would meet with the Special Counsel to limit his jurisdiction to future election interference:
Now a group of people want to subvert the Constitution of the United States. T am going to meet with the Special Prosecutor to explain this is very unfair and let the Special Prosecutor move forward with investigating election meddling for future elections so that nothing can happen in future elections.610
Days after Roger Stone told Julian Assange that he was trying to resolve matters at the highest level of government, the President of the United States tried to issue a back channel order that would shut down the investigation into Assange — and by association, Stone.
According to Lewandowski, neither he nor Rick Dearborn (on whom he tried to pawn off the task) actually delivered the message. But according to Andrew Weissmann, when he and Jeannie Rhee first got briefed on the investigation into how Russia released the documents it had stolen around that time, they learned no one was investigating it.
This effort didn’t start in June 2017, though. It started at least seven months earlier.
The SSCI Report reveals that the day before the Podesta emails got released, Stone probably had a six minute phone call with the candidate via Keith Schiller’s phone.
On the afternoon of October 6, Stone received a call from Keith Schiller’s number. Stone returned the call about 20 minutes later, and spoke-almost certainly to Trump–for six minutes.1663 The substance of that conversation is not known to the Committee. However, at the time, Stone was focused on the potential for a WikiLeaks release, the Campaign was following WikiLeaks’s announcements, and Trump’s prior call with Stone on September 29, also using Schiller’s phone, related to a WikiLeaks release. Given these facts, it appears quite likely that Stone and Trump spoke about WikiLeaks.
The SSCI Report and the affidavits reveal that Stone postponed a lunch with Jerome Corsi on October 8 to go meet with Trump.
On or about October 8, 2016, STONE messaged CORSI at Target Account 2, “Lunch postponed- have to go see T.” CORSI responded to STONE, “Ok. I understand.”
According to Mike Flynn, in the wake of the Podesta release, senior campaign officials discussed reaching out to WikiLeaks.
Beginning on October 7, 2016, WikiLeaks released emails stolen from John Podesta, the chairman of Hillary Clinton’s 2016 presidential campaign. The defendant relayed to the government statements made in 2016 by senior campaign officials about WikiLeaks to which only a select few people were privy. For example, the defendant recalled conversations with senior campaign officials after the release of the Podesta emails, during which the prospect of reaching out to WikiLeaks was discussed.
And then, days later, Roger Stone tried to reach out to WikiLeaks — seemingly in response to WikiLeaks’ public disavowal of any tie to Stone — only to be rebuffed.
On October 13, 2016, while WikiLeaks was in the midst of releasing the hacked Podesta emails, @RogerJStoneJr sent a private direct message to the Twitter account @wikileaks. This account is the official Twitter account of WikiLeaks and has been described as such by numerous news reports. The message read: “Since I was all over national TV, cable and print defending WikiLeaks and assange against the claim that you are Russian agents and debunking the false charges of sexual assault as trumped up bs you may want to rexamine the strategy of attacking me- cordially R.”
Less than an hour later, @Wikileaks responded by direct message: “We appreciate that. However, the false claims of association are being used by the democrats to undermine the impact of our publications. Don’t go there if you don’t want us to correct you.”
On October 16, 2016, @RogerJStoneJr sent a direct message to @Wikileaks: “Ha! The more you \”correct\” me the more people think you’re lying. Your operation leaks like a sieve. You need to figure out who your friends are.”
But after the election, it was WikiLeaks that reached out to Stone.
On November 9, 2016, one day after the presidential election, @Wikileaks sent a direct message to @RogerJStoneJr containing a single word: “Happy?” @Wikileaks immediately followed up with another message less than a minute later: “We are now more free to communicate.”
At Stone’s trial, Randy Credico testified that in that same period after the election, he put Roger Stone in touch with Margaret Kunstler, Credico’s tie to WikiLeaks and one of the 1,000 lawyers (per a snarky answer from Credico) who represented Assange, to discuss a pardon.
Q. Had you put Mr. Stone directly in touch with Ms. Kunstler after the election?
A. Yes, I did.
Q. And why had you done that?
A. Well, sometime after the election, he wanted me to contact Mrs. Kunstler. He called me up and said that he had spoken to Judge Napolitano about getting Julian Assange a pardon and needed to talk to Mrs. Kunstler about it. So I said, Okay. And I sat on it. And I told her–I told her–she didn’t act on it. And then, eventually, she did, and they had a conversation.
Credico is very evasive about the timing of all this. Texts between him and Stone, introduced as an exhibit at Stone’s trial, show that Credico raised asylum on October 3, three hours before he boasted that he was best friends with Assange’s lawyer, meaning Kunstler.
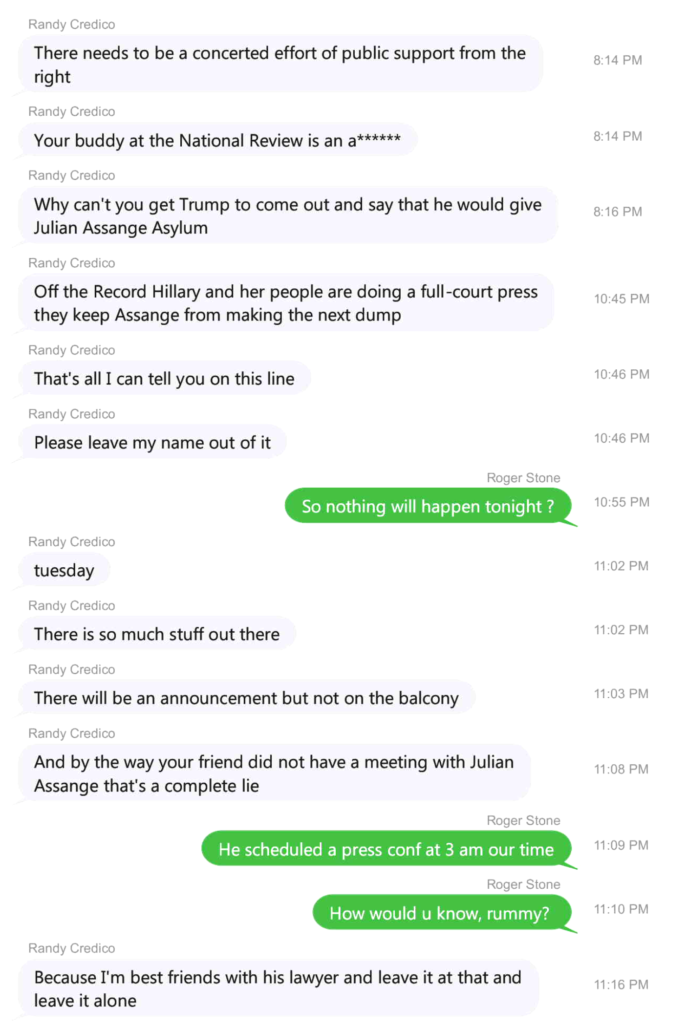
But when asked about the timing, Credico refused to answer, or even answer a yes or no question about whether discussions began before the election. Note, these texts were ones that neither Credico nor Stone provided at first, on Credico’s part because he no longer had them; the government ultimately subpoenaed them from Stone after Stone shared them with Chuck Ross. The texts Stone produced go through November 14, but the ones released at trial stop on October 3.
Later affidavits make clear, however, that on November 15, seven days after Trump won an election with Julian Assange’s help, Trump’s rat-fucker sent Kunstler a link to download Signal and asked her to call him, which she said she’d do. (This was the first day Stone was using the iPhone 7 on which he sent her these texts.)
Additionally, text messages recovered from Stone’s iCloud account revealed that on or about November 15, 2016, Stone sent an attorney with the ability to contact Julian Assange a link to download the Signal application. 15 Approximately fifteen minutes after sending the link, Stone texted the attorney, “I’m on signal just dial my number.” The attorney responded, “I’ll call you.”
15 This attorney was a close friend of Credico’s and was the same friend Credico emailed on or about September 20, 2016 to pass along Stone’s request to Assange for emails connected to the allegations against then-candidate Clinton related to her service as Secretary of State.
So the pardon discussions Credico testified about under oath began no later then a week after Assange helped Trump get elected and Credico refused to rule out that they started on November 9 or even earlier. The SSCI Report notes Credico had a 12 minute call with Stone on October 5 and five more calls on October 6.
After Trump was inaugurated in early 2017, via an attorney he shared with Oleg Deripaska, Assange tried to leverage CIA’s hacking tools believed to have been stolen the previous April to obtain an immunity deal. Even while those discussions were ongoing, on March 7, 2017, WikiLeaks released the first installment of CIA’s hacking tools, a release they called Vault 7. According to witnesses at the trial of the accused source, Joshua Schulte, the Vault 7 release brought CIA’s hacking-based spying virtually to a halt while the agency tried to figure out who would be compromised by the release.
But that didn’t stop the pardon discussions between WikiLeaks, including Assange personally, and Stone. After another spat about whether Stone had had a back channel to WikiLeaks which they aired on CNN, Stone returned to a discussion of a pardon on April 7.
On or about March 27, 2017, Target Account 1 wrote to Roger Stone, “FYI, while we continue to be unhappy about false \”back channel\” claims, today CNN deliberately broke our off the record comments.”
On March 27, 2017, CNN reported that a representative of WikiLeaks, writing from an email address associated with WikiLeaks, denied that there was any backchannel communication during the Campaign between Stone and WikiLeaks. The same article quoted Stone as stating: “Since I never communicated with WikiLeaks, I guess I must be innocent of charges I knew about the hacking of Podesta’s email (speculation and conjecture) and the timing or scope of their subsequent disclosures. So I am clairvoyant or just a good guesser because the limited things I did predict (Oct disclosures) all came true. ”
On or about April 7, 2017, Roger Stone wrote to Target Account 1, ” I am JA’s only hope for a pardon the chances of which are actually (weirdly) enhanced by the bombing in Syria (which I opposed) . You have no idea how much your operation leaks. Discrediting me only hurts you. Why not consider saying nothing? PS- Why would anyone listen to that asshole Daniel Ellsberg.”
On April 13, in the wake of the Vault 7 hack, Mike Pompeo declared WikiLeaks a non-state hostile intelligence service often abetted by Russia.
It is time to call out WikiLeaks for what it really is – a non-state hostile intelligence service often abetted by state actors like Russia. In January of this year, our Intelligence Community determined that Russian military intelligence—the GRU—had used WikiLeaks to release data of US victims that the GRU had obtained through cyber operations against the Democratic National Committee. And the report also found that Russia’s primary propaganda outlet, RT, has actively collaborated with WikiLeaks.
In response, Stone took to InfoWars on April 18, calling on Pompeo to either provide proof of those Russian ties or resign, defending the release of the Vault 7 tools along the way.
The Intelligence agencies continue to insist that Julian Assange is an active Russian Agent and that Wikileaks is a Russian controlled asset. The agencies have no hard proof of this claim whatsoever. Assange has said repeatedly that he is affiliated with no nation state but the Intelligence Agencies continue to insist that he is under Russian control because it fits the narrative in which they must produce some evidence of Russian interference in our election because they used this charge to legally justify and rationalize the surveillance of Trump aides, myself included.
[snip]
President Donald Trump said on Oct, 10, 2016 “I love Wikileaks” and Pompeo who previously had praised the whistleblowing operation now called Wikileaks “a non-state hostile Intelligence service often abetted by state actors like Russia”. Mr. Pompeo must be pressed to immediately release any evidence he has that proves these statements. If he cannot do so ,the President should discharge him.
[snip]
Julian Assange does not work for the Russians. Given the import of the information that he ultimately disclosed about the Clinton campaign, the Obama administration and the deep secrets in the CIA’s Vault 7, he has educated the American people about the tactics and technology the CIA has used to spy on ordinary Americans.
Assange personally DMed Stone to thank him for the article, while claiming that Pompeo had stopped short of claiming that WikiLeaks had gotten the stolen DNC emails directly, thereby making WikiLeaks like any other media outlet.
On or about April 19, 2017, Assange, using Target Account 2, wrote to Stone, “Ace article in infowars. Appreciated. But note that U.S. intel is engages in slight of hand maoevers [sic]. Listen closely and you see they only claim that we received U.S. election leaks \”not directly\” or via a \”third party\” and do not know \”when\” etc. This line is Pompeo appears to be getting at with his \”abbeted\”. This correspnds to the same as all media and they do not make any allegation that WL or I am a Russia asset.”
It’s in that context — in the wake of Trump’s trusted CIA Director (and a former WikiLeaks booster himself) asserting serial cooperation between Russia and WikiLeaks — that Stone and Assange had the exchange that directly preceded Trump’s attempt to shut down any investigation into the leaks to WikiLeaks.
On June 4, Stone threatened to “bring down the entire house of cards” if the government moved on Assange (Stone kept a notebook during the campaign detailing all the calls he had had with Trump), then raised a pardon again, suggesting Assange had done nothing he needed to be pardoned for.
56. On or about June 4, 2017, Roger Stone wrote back to Target Account 2, “Still nonsense. As a journalist it doesn’t matter where you get information only that it is accurate and authentic. The New York Times printed the Pentagon Papers which were indisputably stolen from the government and the courts ruled it was legal to do so and refused to issue an order restraining the paper from publishing additional articles. If the US government moves on you I will bring down the entire house of cards. With the trumped-up sexual assault charges dropped I don’t know of any crime you need to be pardoned for – best regards. R.” Target Account 2 responded, “Between CIA and DoJ they’re doing quite a lot. On the DoJ side that’s coming most strongly from those obsessed with taking down Trump trying to squeeze us into a deal.”
57. On or about June 10, 2017, Roger Stone wrote to Target Account 2, “I am doing everything possible to address the issues at the highest level of Government. Fed treatment of you and Wikileaks is an outrage. Must be circumspect in this forum as experience demonstrates it is monitored. Best regards R.” Target Account 2 wrote back, “Appreciated. Of course it is!”
According to texts between Stone and Credico, Stone at least claimed to be pursuing a pardon in early 2018 (though he may have been doing that to buy Credico’s silence).

And it wasn’t just Stone involved in the discussions to free Assange.
Manafort’s Ecuador trip
While it’s not clear to what end, Paul Manafort took steps relating to Assange as well.
There’s the weird story by Ken Vogel, explaining that between those two Stone-Assange exchanges in April and June, 2017, long-time Roger Stone friend Paul Manafort went to Ecuador to negotiate Assange’s expulsion.
In mid-May 2017, Paul Manafort, facing intensifying pressure to settle debts and pay mounting legal bills, flew to Ecuador to offer his services to a potentially lucrative new client — the country’s incoming president, Lenín Moreno.
Mr. Manafort made the trip mainly to see if he could broker a deal under which China would invest in Ecuador’s power system, possibly yielding a fat commission for Mr. Manafort.
But the talks turned to a diplomatic sticking point between the United States and Ecuador: the fate of the WikiLeaks founder Julian Assange.
In at least two meetings with Mr. Manafort, Mr. Moreno and his aides discussed their desire to rid themselves of Mr. Assange, who has been holed up in the Ecuadorean Embassy in London since 2012, in exchange for concessions like debt relief from the United States, according to three people familiar with the talks, the details of which have not been previously reported.
They said Mr. Manafort suggested he could help negotiate a deal for the handover of Mr. Assange to the United States, which has long investigated Mr. Assange for the disclosure of secret documents and which later filed charges against him that have not yet been made public.
The story never explained whether Manafort wanted Assange handed over for trial, for a golf vacation, or for Russian exfiltration (as was reportedly planned for Assange later in 2017).
That Manafort went to Ecuador and negotiated for an Assange release accords, however, with the 302 of a witness who called in to Mueller’s team. The witness described that Manafort had told him or her, in real time, that he had gone to Ecuador, “to try to convince the incoming President to expel Assange from the Embassy in order to gain favor with the U.S.”
Neither of these stories should be considered reliable, as written. 302s that Bill Barr’s DOJ is willing to release in unredacted form, as this one is, tend to be false claims that make Trump look less suspect than he really is. And Manafort-adjacent sources were using Ken Vogel to plant less-damning cover stories during this period. Further, as we’ll see, the dates of them, November 28 and December 3, 2018, respectively, puts them in a period after Trump knew that Mueller was investigating efforts to pardon Assange.
Manafort went to Ecuador in May of 2017. At the time, his lifelong buddy Roger Stone was still pursuing some means to get Assange released. It’s unclear precisely what Manafort asked Lenín Moreno to do.
WikiLeaks cultivates Trump’s oldest son
A more interesting parallel timeline (one that becomes more interesting if you track the communications in tandem, as I do below) is the dalliance between Don Jr and WikiLeaks. The failson’s communications with WikiLeaks are one area where all of the Roger Stone stories withhold key details. The Mueller Report, for example, covers only three of the Don Jr-WikiLeaks exchanges, which it caveats by explaining that it addresses the ones “during the campaign period” (again, only the one where Don Jr accesses a non-public website using the private password WikiLeaks shared involved a prosecutorial decision and so needed to be included).
Like the Mueller Report, the SSCI Report describes in the body of the report Don Jr’s exchange with WikiLeaks in a period around the time that Trump and his closest advisors had discussed reaching out to WikILeaks.
(U) WikiLeaks also sought to coordinate its distribution of stolen documents with the Campaign. After Trump proclaimed at an October 10 rally, “I love WikiLeaks” and then posted about it on Twitter,1730 WikiLeaks resumed messaging with Trump Jr. On October 12, it said: “Strongly suggest your dad tweets this link if he mentions us … there’s many great stories the press are missing and we’re sure some of your follows [sic] will find it. btw we just released Podesta Emails Part 4.”1731 Shortly afterward, Trump tweeted: “Very little pick-up by the dishonest media of incredible information provided by WikiLeaks. So dishonest! Rigged System!”1732 Two days later, Donald Trump Jr. tweeted the link himself: “For those who have the time to read about all the corruption and hypocrisy all the @wikileaks emails are right here: wlsearch.tk.”1733 Trump Jr. admitted that this may have been in response to the request from WikiLeaks, but also suggested that it could have been part of a general practice of retweeting the. WikiLeaks releases when they came out. 1734
But it only presents one part of the exchange that Jr and WikiLeaks had on November 8 and 9, and it relegates that to a footnote.
1738 (U) Ibid., pp. 164-166. WikiLeaks continued to interact with Trump Jr. after the general election on November 8, 2016. On November 9, 2016, WikiLeaks wrote to Trump Jr.: “Wow. Obama people will surely try to delete records on the way out. Just a heads up.”
As to the affidavits, the warrant application for Julian Assange’s Twitter account described having earlier obtained Don Jr’s Twitter account, but didn’t refer to him by name. Instead, it referred to him as “a high level individual associated with the Campaign,” and described just the September exchange between the two of them.
After the Atlantic provided more of those DMs, Don Jr, as he had earlier with his June 9 emails, released them himself. The Election Day exchange of which SSCI made no mention pushes Don Jr to adopt a strategy Russia was also pushing — to refuse to concede (a strategy that Trump will undoubtedly adopt on November 4 if he loses).
Hi Don; if your father ‘loses’ we think it is much more interesting if he DOES NOT conceed [sic] and spends time CHALLENGING the media and other types of rigging that occurred–as he has implied that he might do. He is also much more likely to keep his base alive and energised this way and if he is going to start a new network, showing how corrupt the old ones are is helpful. The discussion about the rigging can be transformative as it exposes media corruption, primary corruption, PAC corruption etc. We don’t like corruption ither [sic] and our publications are effective at proving that this and other forms of corruption exists.
That doesn’t pertain to pardons (though it does demonstrate that WikiLeaks was not involved in a journalistic enterprise).
But a DM from December 16, 2016 the SSCI similarly excerpted in a footnote does discuss what amounts to a pardon:
Hi Don. Hope you’re doing well! In relation to Mr. Assange: Obama/Clinton placed pressure on Sweden, UK and Australia (his home country) to illicitly go after Mr. Assange. It would be real easy and helpful for your dad to suggest that Australia appoint Assange ambassador to DC “That’s a really smart tough guy and the most famous australian you have! ” or something similar. They won’t do it, but it will send the right signals to Australia, UK + Sweden to start following the law and stop bending it to ingratiate themselves with the Clintons. Background: justice4assange.com
When these DMs were released on November 14, 2017, Assange tweeted out a follow-up to the December 2016 one, adding a threat by hashtagging, Vault8, the source code to the CIA files, a single example of which WikiLeaks had just released on November 9, 2017.

Meanwhile, the one other example where WikiLeaks provided the President’s son advice — a pitch for him to release his own June 9 emails via WikiLeaks in July 2017 — WikiLeaks explicitly suggested that Don Jr contact Margaret Kunstler, the same lawyer who had been discussing pardons with Assange nine months earlier.
There appears to be more — far more — to Margaret Kunstler’s role. Two 302s identifiable as hers have been released in response to the BuzzFeed FOIA, an interview on October 29, 2018 involving Stone prosecutor Aaron Zelinsky and Obstruction prosecutor Andrew Goldstein, and a second interview, this one by phone, on November 20, 2018, this one adding Russian prosecutor Rush Atkinson along with Zelinsky and Goldstein. Both 302s were released on October 1, 2020, the most recent release. In the first interview, only Kunstler’s response stating that she did not pass on Stone’s September request for information about Libya to Julian Assange was partly unsealed; there are at least five more paragraphs that remain redacted as part of an ongoing investigation. The second is eight pages long and appears to have at least four sub-topics with separate headings. Aside from the introductory paragraph, it remains entirely redacted, with over half covered by a b7A ongoing investigation exemption.
The investigation into much of Stone’s activities appears to have been shut down. But the investigation into the pardon discussions appears to have been ongoing just three weeks ago.
The Mueller question
The discussion of efforts to free Julian Assange appears, primarily, in two versions of the Roger Stone story. Prosecutors at Stone’s trial used the discussions to explain which of Stone’s threats — those naming Kunstler directly — worked most effectively to delay Credico’s cooperation. It also appears in affidavits, though with Don Jr’s identity obscured.
The SSCI report relegates both the Don Jr and Stone pardon discussions with WikiLeaks to footnotes and doesn’t quote Stone using the word “pardon” in the excerpts it includes. It does so even though the SSCI Report describes Dana Rohrabacher’s attempt to broker an Assange pardon in August 2017 in the body of the text.
The Mueller Report doesn’t discuss pardon efforts for Assange where you might expect it, along with discussions of pardons for Manafort, Flynn, Stone himself, and Michael Cohen. Mention of the effort to free Assange appears in just one place: amid the questions asked of Trump in an appendix.
Did you have any discussions prior to January 20, 2017, regarding a potential pardon or other action to benefit Julian Assange? If yes, describe who you had the discussion(s) with, when, and the content of the discussion(s).
I do not recall having had any discussion during the campaign regarding a pardon or action to benefit Julian Assange.
That appendix explains that Mueller’s team submitted these questions on September 17, 2018 (before both of Kunstler’s interviews) and Trump returned them on November 20, 2018.
In the interim period, on October 30, 2018, Don Jr’s close buddy, Arthur Schwartz, for the first time in years of having listened to former Sputnik employee Cassandra Fairbanks’ lobbying for Julian Assange in the right wing chat room they both (along with Ric Grenell) participated in responded by telling her that he would be charged and expelled from the embassy, that a pardon was not going to fucking happen and — at some point, if Fairbanks can be believed — suggesting someone with whom Schwartz was lifelong friends might be affected.
Arthur Schwartz warned me that people would be able to overlook my previous support for WikiLeaks because I did not know some things which he claimed to know about, but that wouldn’t be so forgiving now that I was informed. He brought up my nine year old child during these comments, which I perceived as an intimidation tactic.
He repeatedly insisted that I stop advocating for WikiLeaks and Assange, telling me that “a pardon isn’t going to fucking happen.” He knew very specific details about a future prosecution against Assange that were later made public and that only those very close to the situation would have been aware of. He told me that it would be the “Manning” case that he would be charged with and that it would not involve Vault 7 publication or anything to do with the DNC. He also told me that they would be going after Chelsea Manning. I also recollect being told, I believe, that it would not be before Christmas.
[snip]
The other persons who Schwartz said might also be affected included individuals who he described as “lifelong friends.”
Shortly after Trump submitted his answers, two stories — one public, one via witness testimony to Mueller — claimed that Manafort’s visit to Moreno, at a time when his buddy Stone was seeking a pardon, was actually an attempt to expel him from the embassy.
In spite of what Schwartz told Cassandra, however, the pardon discussions aren’t over. Just before Julian Assange’s extradition hearing started, Roger Stone’s buddy Tucker Carlson invited Glenn Greenwald on to make a three minute pitch — one in which Glenn explained what a good way this would be for Trump to stick it to the Deep State — for both Assange and Ed Snowden.
Timeline
September 20, 2016: WikiLeaks DMs Don Jr a link to putintrump site, including a password.
October 3, 2016: Credico raises asylum for Assange and tells Stone he’s best friends with Assange’s lawyer. WikiLeaks DMs Don Jr asking him to push a story about Hillary drone-striking Assange; Don Jr notes he has already done so and asks what is coming on Wednesday.
October 5, 2016: Credico and Stone speak for 12 minutes.
October 6, 2016: Stone probably has a six minute call with Trump. Stone has five calls with Credico.
October 7, 2016: The release of the Podesta email swamps the DHS/ODNI release attributing the DNC hack and tying WikiLeaks to Russia
October 8, 2016: Stone and Trump probably meet.
Shortly after Podesta release: Senior campaign officials discuss reaching out to WikiLeaks.
October 10, 2016: Trump tweets “I love WikiLeaks.”
October 12, 2016: WikiLeaks disavows any back channel with Stone. WikiLeaks also DMs Don Jr suggesting he get his father to tweet a link. Don Jr tweets it that day.
October 13, 2016: Stone and WikiLeaks exchange DMs.
October 14, 2016: Trump tweets the link WikiLeaks sent to Don Jr.
October 16, 2016: Stone tells WikiLeaks “You need to figure out who your friends are.”
October 21, 2016: WikiLeaks suggests that Don Jr release Trump’s tax returns to WikiLeaks.
November 8, 2016: WikiLeaks DMs Don Jr to suggest Trump not concede if he loses.
November 9, 2016: WikiLeaks DMs Don Jr to claim Obama’s people will delete records on the way out. WikiLeaks DMs Stone to say, “We are now more free to communicate.”
November 14, 2016: Stone gets a new phone.
November 15, 2016: Stone texts Margaret Kunstler a link to Signal and tells her to call him on it, which she said she would do.
December 16, 2016: WikiLeaks suggests that he ask his dad to suggest Australia appoint Assange as Ambassador to the US.
January 6, 2017: WikiLeaks DMs Don Jr a John Harwood tweet asking, Who do you believe, America?
March 7, 2017: WikiLeaks starts releasing the Vault 7 files, effectively halting CIA’s hacking capability for a period.
March 27, 2017: Stone and WikiLeaks exchange more complaints about whether Stone had a back channel.
April 7, 2017: Stone writes WikiLeaks that he is “JA’s only hope for a pardon.”
April 13, 2017: Mike Pompeo calls WikiLeaks a non-state hostile intelligence service often abetted by Russia.
April 18, 2017: Stone calls on Pompeo to release proof of WikiLeaks’ Russian ties or resign.
April 19, 2017: Assange thanks Stone for the attack on Pompeo, but claims that Pompeo has stopped short of calling WikiLeaks a Russian asset.
April 26, 2017: Assange DMs Don Jr some video on “Fake News.”
May 2017: Manafort meets in Ecuador with Lenín Moreno to discuss Assange.
June 4, 2017: Stone DMs Assange, threatening to “bring down the entire house of cards” if the US government moves on Assange.
June 10, 2017: Roger Stone tells Assange he is “doing everything possible … at the highest level of Government” to help Assange.
June 19, 2017: Trump tries to give a back channel order to Jeff Sessions to limit the Mueller investigation to future election meddling, not the meddling that helped him get elected.
July 11, 2017: WikiLeaks DMs Don Jr to suggest he release his June 9 emails via WikiLeaks, providing him Margaret Kunstler’s contact information as if she would take the submission.
October 12, 2017: Mueller’s team obtains Don Jr’s Twitter content.
November 6, 2017: Mueller’s team obtains WikiLeaks and Assange’s Twitter content.
November 14, 2017: Don Jr releases his Twitter DMs with WikiLeaks. Julian Assange publicly references the December 16 DM, suggests he can open “luxury immunity suites for whistleblowers,” and includes a Vault8 hashtag (referencing CIA’s source code).
December 21, 2017: Reported attempt to exfiltrate Assange from the embassy; DOJ charges Assange with CFAA conspiracy.
January 6, 2018: Stone claims “I am working with others to get JA a blanket pardon.”
September 17, 2018: Mueller submits questions to Trump, including one about a pardon for Assange.
October 29, 2018: Mueller’s team interviews Kunstler.
October 30, 2018: Arthur Schwartz tells Cassandra Fairbanks there’s not going to be a fucking Assange pardon.
November 20, 2018: Trump returns his questions to Mueller. Mueller’s team interviews Kunstler.
The movie Rashomon demonstrated that any given narrative tells just one version of events, but that by listening to all available narratives, you might identify gaps and biases that get you closer to the truth.
I’m hoping that principle works even for squalid stories like the investigation into Roger Stone’s cheating in the 2016 election. This series will examine the differences between four stories about Roger Stone’s actions in 2016:
As I noted in the introductory post (which lays out how I generally understand the story each tells), each story has real gaps in one or more of these areas:
- While the Mueller Report made it clear Trump’s pardon dangles to keep details of his conversations with Roger Stone secret amounted to obstruction, it didn’t tell just just how many conversations they had
- Rather than telling us whether, how, and why Roger Stone optimized the release of John Podesta’s emails on October 7, 2016, the Mueller Report instead gave us Jerome Corsi slapstick
- Just one story presents the significant amounts of evidence suggesting that on August 14, 2016, when he started a file called “Podesta,” Jerome Corsi had or knew the contents of the Podesta files that would become public on October 11, 2016
- The later stories focus on Podesta, rather than the evidence that Stone learned of the hack-and-leak while the burglary was still ongoing
- Stone pitched both Manafort and Bannon on a way to win ugly–but none of the Stone stories tell us what that was
- Trolling for Russia
- The “highest levels of government” attempt to shut down an investigation into Julian Assange
- Guccifer 2.0 as go-between
My hope is that by identifying these gaps and unpacking what they might say about the choices made in crafting each of these stories, we can get a better understanding of what actually happened — both in 2016 and in the investigations. The gaps will serve as a framework for this series.









