Scary Terror Metrics: Do Indicted “Terrorists” Really Measure Back Door Spying?
Given how often fellow Michigander Juan Cole and I demonstrate what a mendacious hack Mike Rogers is…
Mike Rogers voted to give arms to the Syrian rebels. And while he may hope they don’t go to the al-Qaeda affiliates (as happened when Ronald Reagan gave $5 billion to the Afghan Mujahidin in the 1980s), he has no guarantee that won’t happen and is willing to take the risk. If Rogers were really, really concerned about the Jabhat al-Nusra, he wouldn’t be risking upping its firepower with Americans’ tax dollars as a justification for monitoring who your 15 year old daughter calls on her cell phone.
Let us say that again. Feinstein and Rogers just came on television to scaremonger the American people with the Syrian jihadis, and both of them voted to give the Syrian rebels millions of dollars in arms.
… You’d think some of the MI press might look into it.
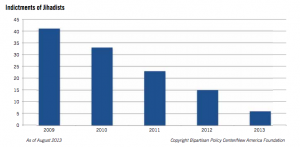
Thankfully, Cole and I are no longer the only ones asking substantive questions about Rogers and Dianne Feinstein’s fearmongering on this Sunday’s shows. Peter Bergen has a piece that — like Cole — looks at actual numbers to challenge their claims. He relies on a New America Foundation study of Americans and residents indicted or killed over the last decade, showing that those numbers show terrorism to be going down (and be propagated by smaller, less capable groups).
But is there any real reason to think that Americans are no safer than was the case a couple of years back? Not according to a study by the New America Foundation of every militant indicted in the United States who is affiliated with al Qaeda or with a like-minded group or is motivated by al Qaeda’s ideology.
In fact, the total number of such indicted extremists has declined substantially from 33 in 2010 to nine in 2013. And the number of individuals indicted for plotting attacks within the United States, as opposed to being indicted for traveling to join a terrorist group overseas or for sending money to a foreign terrorist group, also declined from 12 in 2011 to only three in 2013.
Of course, a declining number of indictments doesn’t mean that the militant threat has disappeared. One of the militants indicted in 2013 was Dzhokhar Tsarnaev, who is one of the brothers alleged to be responsible for the Boston Marathon bombings in April. But a sharply declining number of indictments does suggest that fewer and fewer militants are targeting the United States.
Recent attack plots in the United States also do not show signs of direction from foreign terrorist organizations such as al Qaeda, but instead are conducted by individuals who are influenced by the ideology of violent jihad, usually because of what they read or watch on the Internet.
None of the 21 homegrown extremists known to have been involved in plots against the United States between 2011 and 2013 received training abroad from a terrorist organization — the kind of training that can turn an angry, young man into a deadly, well-trained, angry, young man.
Of these extremists, only Tamerlan Tsarnaev, one of the alleged Boston bombers, is known to have had any contact with militants overseas, but it is unclear to what extent, if any, these contacts played in the Boston Marathon bombings. [my emphasis]
The post got me thinking about the validity of this metric. Are the number of people indicted since 2009 a reflection of the actual threat, or that Federal officials have exhausted all the leads they’ve gotten from backdoor searches of existing COMINT collections?
Consider what one anonymous source said in the months after Anwar al-Awlaki was killed.
U.S. intelligence analysts miss the publication, too, at least to the extent that it provided a window into the thinking of al-Qaeda in the Arabian Peninsula, as the Yemen-based group is known.
“It was something that helped us gain insight into the group,” said a U.S. defense official involved in tracking AQAP, who spoke on the condition of anonymity. The publication’s apparent demise is “an intelligence loss for us,” the official said.
Yet Inspire probably wasn’t just a window onto AQAP’s thinking (if it really was that). Particularly given the indications NSA had some access to its code (if I were NSA I would have attached some kind of flag to the code used to decrypt the document, and I would also search on that code in upstream collection), I would assume Inspire was a major source of leads. So did killing Awlaki and Samir Khan simply make it harder for US officials to find Muslims to trap in stings over time?
NAF’s data is inconclusive on this point. Read more →