Google Kills the Geofence Capability that Will Show ~30,000 Trump Supporters Swarmed the Capitol on Trump’s Orders
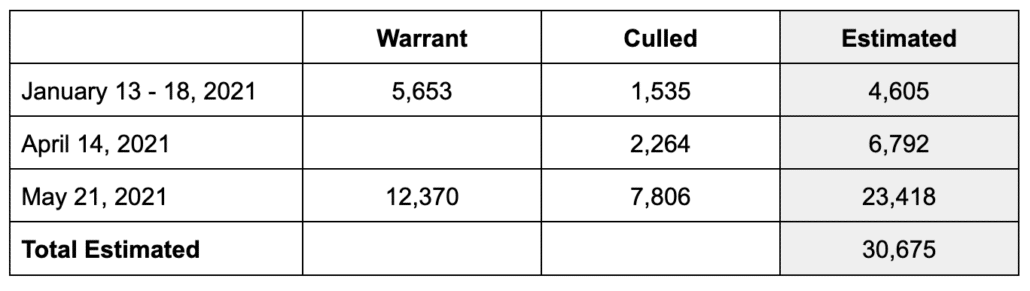
At Trump’s trial, prosecutors will use Google Location data to show how Trump’s mobs responded to his order to march to the Capitol by doing just that: swarming the Capitol. That data will show that roughly a quarter of the people at the Ellipse, around 30,000 people, entered the restricted grounds outside the Capitol, committing at least trespassing on Trump’s instruction, of which 11,500 would be identified by their Google Location data.
Jack Smith’s prosecutors revealed that they will do this on Monday in an expert notice filing.
On Wednesday, Google announced that it will soon change the way Google Location works to make such analysis impossible in the future.
If you’re among the subset of users who have chosen to turn Location History on (it’s off by default), soon your Timeline will be saved right on your device — giving you even more control over your data. Just like before, you can delete all or part of your information at any time or disable the setting entirely.
If you’re getting a new phone or are worried about losing your existing one, you can always choose to back up your data to the cloud so it doesn’t get lost. We’ll automatically encrypt your backed-up data so no one can read it, including Google.
Additionally, when you first turn on Location History, the auto-delete control will be set to three months by default, which means that any data older than that will be automatically deleted. Previously this option was set to 18 months. If you want to save memories to your Timeline for a longer period, don’t worry — you can always choose to extend the period or turn off auto-delete controls altogether.
These changes will gradually roll out through the next year on Android and iOS, and you’ll receive a notification when this update comes to your account.
Orin Kerr first identified the significance of the change to surveillance capabilities: that it will make Google geofence warrants all but impossible. Forbes confirmed that Google is making the change with the intent of making it impossible to respond to geofence warrants.
But they missed one aspect of the timing. The announcement — of a change Google is implementing prospectively, a change that will take a year to implement — came days after prosecutors revealed they had obtained a Google warrant showing the movement of people from the Ellipse to the Capitol.
Expert 1
Expert 1 has knowledge, skill, experience, training, and education beyond the ordinary lay person regarding the interpretation and visual representation of geographic location data. The Government expects that Expert 1 will testify about his/her use of ArcGIS (Geographic Information Systems) software to create a map of the Google location history data produced in response to a search warrant. Specifically, Expert 1 plotted the location history data for Google accounts and devices associated with individuals who moved, on January 6, 2021, from an area at or near the Ellipse to an area encompassing the United States Capitol building. His/her testimony will describe and explain the resulting graphical representations of that data, and it will aid the jury in understanding the movements of individuals toward the Capitol area during and after the defendant’s speech at the Ellipse. [my emphasis]
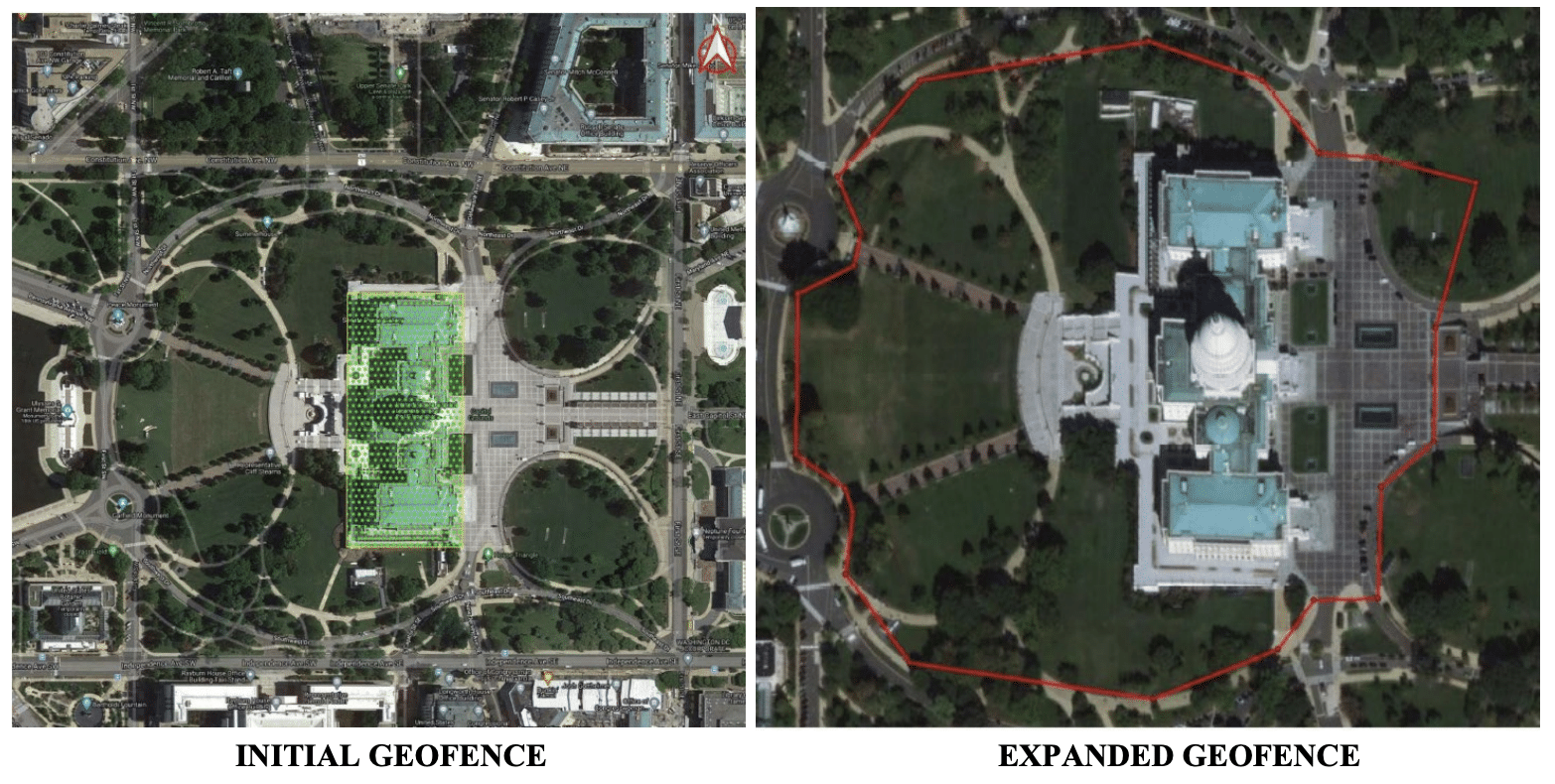
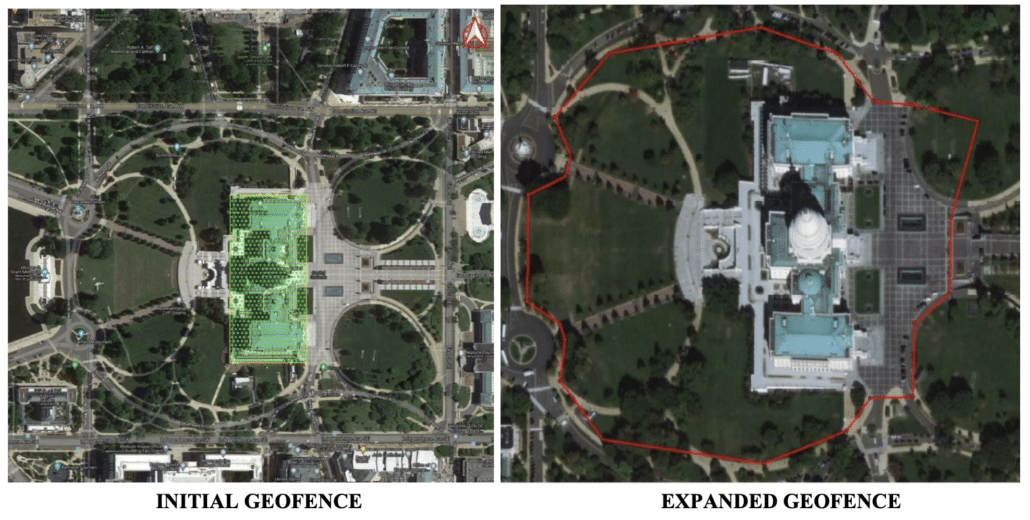
We had known that the FBI used Google geofence warrants — which identify all the people using Google Location services in a given geographic area — to identify individual January 6 suspects.
Challenges to the geofence — first by trespasser David Rhine and then by cop-sprayer Isreal Easterday — revealed that the FBI had gotten two geofence warrants (and had done three sets of de-anonymization of the data obtained): the first, on January 13, 2021, for just the Capitol building itself, and then the second, for the entire restricted area outside the Capitol, on May 21, 2021.
The warrant described in Tuesday’s expert notice must be a third warrant, one building off the May 2021 one. Perhaps the FBI asked Google for all the selectors found in the May 2021 warrant (who, with the important exception of journalists, were either victims, first responders, or trespassers), that also showed up in a geofence at the Ellipse while Trump was speaking.
There would be no need to de-anonymize these selectors. Those of investigative interest for their own actions at the Capitol would have been de-anonymized with one of the earlier warrants. This warrant is about capturing the effect of Trump’s speech, measuring how many people who attended the speech itself — Trump claims 120,000 did so — then moved to the Capitol.
Of those who moved, only a third or less would trigger the geofence (and fewer among Apple users). But it would include most of the 11,500 people who had already been identified and de-anoymized. altogether, that’s consistent with 30,000 people being at the Capitol.
Trump is claiming that just 1% of those who heard his incitement went on to join the insurrection. This expert witness will show it’s closer to a quarter of the total.
There were, undoubtedly, a range of reasons why Google made the decision to end its ability to respond to geofence requests. As Forbes noted, the Fourth Circuit also heard the government’s appeal of Okello Chatrie’s successful challenge of a geofence this week. Early next year the DC Circuit will review Rhine’s appeal of its use with him. The Easterday challenge made it clear that Google geofences work best on Android devices — meaning Google was making it easier for law enforcement to investigate its customers over Apple’s.
But Google announced this decision — of prospective changes — months ahead of the time when a geofence will be used to prove the crimes of Donald Trump.
It’s likely at least partly an attempt to pre-empt the blowback that is bound to result.
Update: To clarify some responses I’m getting to this. Killing the geofence capability won’t affect the evidence against Trump at all. Prosecutors already got the warrant and did the analysis on the results. This will only prospectively make Google geofence warrants impossible, and not even immediately.
Easterday challenge
une 30, 2023: Motion to Compel, Declaration
August 22, 2023: Opposition Motion to Compel
September 26, 2023: Motion to Suppress Geofence
October 10, 2023: Opposition Motion to Suppress
October 17, 2023: Reply Motion to Suppress
October 26, 2023: Guilty Verdict
November 25, 2023: Supplement Opposition Motion to Suppress