Now that the Section 215 Sunset draws nearer, the debate over what reformers should do has shifted away from whether USA Freedom Act is adequate reform to whether it is wise to push for Section 215 to sunset.
That debate, repeatedly, has focused almost entirely on the phone dragnet that Section 215 authorizes. It seems most of the people engaging in this debate or reporting on it are unaware or uninterested in what the other roughly 175 Section 215 orders authorized last year did (just 5 orders authorized the phone dragnet).
But if Section 215 sunsets in June, those other 175 orders will be affected too (though thus far it looks like FISC is approving fewer 215 orders than they did last year). Yet the government won’t tell us what those 175 orders do.
We know — or suspect — some of what these other orders do. NYT and WSJ reported on a Western Union dragnet that would probably amount to 4-5 orders a year (and would have been unaffected and hidden in transparency reporting under USA Freedom Act).
The FBI has previously confirmed that it used Section 215 to collect records of explosives precursors — things like large quantities of acetone, hydrogen peroxide, fertilizer, and (probably now) pressure cookers; given that the Presidential Review Group consulted with ATF on its review of Section 215, it’s likely these are programmatic collection. (If the government told us it was, we might then be able to ask why these materials couldn’t be handled the same way Sudafed is handled, too, which might force the government to tie it more closely to actual threats.) This too would have been unaffected by USAF.
The government also probably uses Section 215 to collect hotel records (which is what it was originally designed for, though not in the bulk it is probably accomplished). This use of Section 215 will likely be reinforced if and when SCOTUS affirms the collection of hotel records in Los Angeles v. Patel.
But the majority of those 175 Section 215 orders, we now know, are for some kind of Internet records that may or may not relate to cyber investigations, depending on whether you think FBI talks out of its arse when trying to keep authorities, but which they almost certainly collect in sufficient bulk that FISC imposed minimization procedures on FBI.
Which brings me to my argument that reauthorizing Section 215 will forestall any ECPA reform.
We know most Section 215 orders are for Internet records because someone reliable — DOJ’s Inspector General in last year’s report on National Security Letters — told us that a collection of Internet companies successfully challenged FBI’s use of NSLs to collect this stuff after DOJ published an opinion on ECPA in 2008.
The decision of these [redacted] Internet companies to discontinue producing electronic communication transactional records in response to NSLs followed public release of a legal opinion issued by the Department’s Office of Legal Counsel (OLC) regarding the application of ECPA Section 2709 to various types of information. The FBI General Counsel sought guidance from the OLC on, among other things, whether the four types of information listed in subsection (b) of Section 2709 — the subscriber’s name, address, length of service, and local and long distance toll billing records — are exhaustive or merely illustrative of the information that the FBI may request in an NSL. In a November 2008 opinion, the OLC concluded that the records identified in Section 2709(b) constitute the exclusive list of records that may be obtained through an ECPA NSL.
Although the OLC opinion did not focus on electronic communication transaction records specifically, according to the FBI, [redacted] took a legal position based on the opinion that if the records identified in Section 2709(b) constitute the exclusive list of records that may be obtained through an ECPA NSL, then the FBI does not have the authority to compel the production of electronic communication transactional records because that term does not appear in subsection (b).
That report went on to explain that FBI considered fixing this problem by amending the definition for toll records in Section 2709, but then bagged that plan and just moved all this collection to Section 215, which takes longer.
In the absence of a legislative amendment to Section 2709, [2.5 lines redacted]. [Deputy General Counsel of FBI’s National Security Law Branch] Siegel told us that the process of generating and approving a Section 215 application is similar to the NSL process for the agents and supervisors in the field, but then the applications undergo a review process in NSLB and the Department’s National Security Division, which submits the application to the Foreign Intelligence Surveillance Court (FISA Court). According to Siegel, a request that at one time could be accomplished with an NSL in a matter of hours if necessary, now takes about 30-40 days to accomplish with a standard Section 215 application.
In addition to increasing the time it takes to obtain transactional records, Section 215 requests, unlike NSL requests, require the involvement of FBI Headquarters, NSD, and the FISA Court. Supervisors in the Operations Section of NSD, which submits Section 215 applications to the FISA Court, told us that the majority of Section 215 applications submitted to the FISA Court [redacted] in 2010 and [redacted] in 2011 — concerned requests for electronic communication transaction records.
The NSD supervisors told us that at first they intended the [3.5 lines redacted] They told us that when a legislative change no longer appeared imminent and [3 lines redacted] and by taking steps to better streamline the application process.
The government is, according to the report, going through all sorts of hoop-jumping on these records rather than working with Congress to pass ECPA reform.
Why?
That’s not all the Report told us. Even earlier than that problem, in 2007, the IG identified other uncertainties about what the FBI should be obtaining with an NSL, and FBI actually put together a proposal to Congress. The proposed definition included both financial information and what could be construed as location data in toll records. That bill has never been passed.
But while Internet companies have shown reluctance to let the FBI secretly expand the meaning of toll record, two telecoms have not (a third, which I suspect is Verizon, backed out of closer cooperation on NSLs in 2009, and presumably a fourth, which probably is T-Mobile, was never a part of it).
And here’s what happened to the kinds of records FBI has been obtaining (almost certainly from AT&T) in the interim:

FBI is collecting 7 kinds of things from (probably) AT&T that the Inspector General doesn’t think fits under ECPA.
Now, I’m not sure precisely why ECPA reform has gone nowhere in the last 8 years, but all this redaction suggests one reason is the government doesn’t want to be bound by a traditional definition of toll record, so much so it’s willing to put up with the aggravation of getting Section 215 orders for (what may be the same kind of) information from Internet companies in order to not be bound by limits on its telecom (or at least AT&T) NSLs.
Don’t get me wrong. I’d rather have the Internet stuff be under Section 215 orders, where it will be treated with some kind of minimization (the FBI is still completely ignoring the 2006 language in Section 215 requiring it to adopt minimization procedures for that section, but FISC has stepped into the void and imposed some itself).
But ultimately what’s going on — in addition to the adoption of a dragnet approach for phone records (that might have been deemed a violation of 18 USC 2302-3 if litigated with an adversary) and financial records (that might have been deemed a violation of 12 USC 3401-3422 if litigated with an adversary), is that the government is also, apparently, far exceeding the common understanding of NSLs without going back to Congress to get them to amend the law (and this goes well beyond communities of interest — two or maybe three hop collection under an NSL — which isn’t entirely redacted in this report).
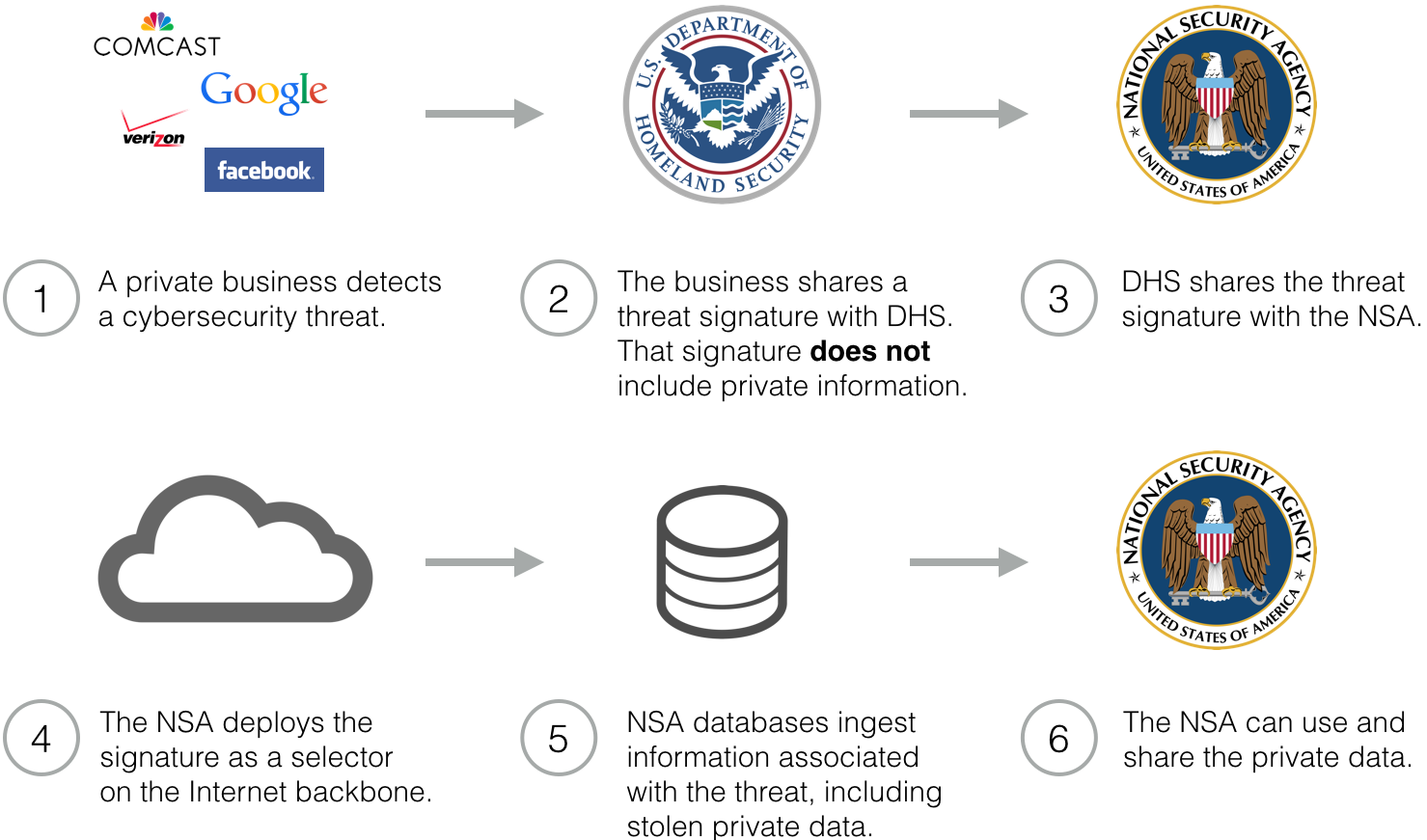
It may be moot anyway. I actually wonder whether Internet companies will use the immunity of CISA, if and when it passes, to turn whatever they’re turning over without a Section 215 order.
And it’s not like Pat Leahy and Mike Lee have been successful in their efforts to get ECPA reform that protects electronic communications passed. ECPA isn’t happening anyway.
But maybe it might, if Section 215 were to lapse and the government were forced to stop kluging all the programs that have never really been approved by Congress in the first place into Section 215.