Why Swim Upstream Overseas?
 In 2011, when John Bates declared the existing upstream collection illegal, he didn’t stop the practice. Instead, he imposed new minimization procedures on part of the collection (just that part that included transactions including communications that were completely unrelated to the search terms used). He required that collection be segregated. And he wrung assurances from NSA they wouldn’t do things — like search on data collected via upstream collection — that they could do with data collected under PRISM.
In 2011, when John Bates declared the existing upstream collection illegal, he didn’t stop the practice. Instead, he imposed new minimization procedures on part of the collection (just that part that included transactions including communications that were completely unrelated to the search terms used). He required that collection be segregated. And he wrung assurances from NSA they wouldn’t do things — like search on data collected via upstream collection — that they could do with data collected under PRISM.
In short, it was actually a pretty permissive ruling, allowing the NSA to continue to collecting upstream data, at least for the terms and purposes they had claimed they were using it for.
So why go to the trouble of stealing data from Google and Yahoo links overseas instead of through PRISM — a question The Switch asks here — and upstream collection here?
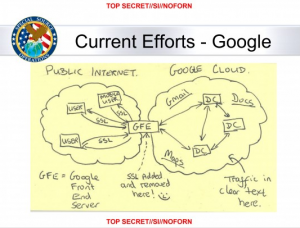
Obviously, one of the problem is encryption. The graphic above makes it very clear NSA/GCHQ are trying to avoid Google’s default and Yahoo’s available SSL protection. Which mean they can’t do the same kind of upstream collection on encrypted content.
Now it’s clear from the aftermath of the 2011 ruling — in the way Google and Yahoo had to invest a lot to keep responding to new orders — that PRISM collection in the US is tied in some way to that upstream collection. Julian Sanchez suggests Google and Yahoo may now be unwilling to do keyword (actually key-selector, since some of these would be code) searches. And that may be the case (though it’s hard to see how they could refuse an order requiring that, given that the telecoms were responding to similar orders).
There are a few other possibilities, though.
First, remember that NSA wanted to continue its collection practice as it existed, with no changes. It considered appealing Bates’ decision. And it resisted his demands they clean up existing illegally collected data.
So it may be they simply continued doing what they were doing by stealing this data overseas. But that would only make sense if MUSCULAR dates to 2012, when Bates imposed new restrictions.
It’s also possible some of the restrictions he imposed wouldn’t allow NSA to accomplish what it wanted to. Two possibilities are his requirement that NSA segregate this collection. Another is his refusal to let NSA search “incidentally” collected data.
A third possibility is that other FISC restrictions — such as limits on how many contact chains one could do on Internet metadata (WaPo makes it clear this collection includes metadata) — provided reason to evade FISC as well.
Finally, I wonder whether the types of targets they’re pursuing have anything to do with this. For a variety of reasons, I’ve come to suspect NSA only uses Section 702 for three kinds of targets.
- Terrorists
- Arms proliferators
- Hackers and other cyber-attackers
According to the plain letter of Section 702 there shouldn’t be this limitation; Section 702 should be available for any foreign intelligence purpose. But it’s possible that some of the FISC rulings — perhaps even the 2007-8 one pertaining to Yahoo (which the government is in the process of declassifying as we speak) — rely on a special needs exception to the Fourth Amendment tied to these three types of threats (with the assumption being that other foreign intelligence targets don’t infiltrate the US like these do).
Which would make this passage one of the most revealing of the WaPo piece.
One weekly report on MUSCULAR says the British operators of the site allow the NSA to contribute 100,000 “selectors,” or search terms. That is more than twice the number in use in the PRISM program, but even 100,000 cannot easily account for the millions of records that are said to be sent back to Fort Meade each day.
Given that NSA is using twice as many selectors, it is likely the NSA is searching on content outside whatever parameters that FISC sets for it, perhaps on completely unrelated topics altogether. This may well be foreign intelligence, but it may not be content the FISC has deemed worthy of this kind of intrusive search.
That’s just a wildarsedguess. But I do think it possible FISC has already told the NSA — whether it be in the 2011 opinion, opinions tied to the Internet dragnet problems (which themselves may have imposed limits on just this kind of behavior), or on the original PAA/FAA opinions themselves — that this collection violated the Fourth Amendment.
In which case the prediction Russ Feingold made back in 2007 — “So in other words, if they don’t like what we [or the FISA Court] come up with, they can just go back to Article II” — would prove, as so many Feingold comments have, prescient.

“…Obviously, one of the problem is encryption. The graphic above makes it very clear NSA/GCHQ are trying to avoid Google’s default and Yahoo’s available SSL protection. Which mean they can’t do the same kind of upstream collection on encrypted content…”
i thought nsa had busted ssl encryption.
“Collect it all”. These are the masters of the universe, part of a bigger group of masters of the universe. You are all (all of us) too lowly to try to place any limits on them.
If data goes under an ocean, McRaven’s guys and the Navy unit under Alexander will get it. And who is going to question or stop McRaven and the US military?
@joanneleon: That’s a very odd looking bunch of people.
And who the hell ‘Bings’ ?
“So why go to the trouble of stealing data from Google and Yahoo links overseas instead of through PRISM — a question The Switch asks here – and upstream collection here?
Obviously, one of the problem is encryption.”
Raw data I/O is one thing, but when that data is in context, much less work is needed for spies to interpret it.
Secret spy bases on military bases train military spies by having them go to news websites and blogs, and follow the commenter in an operation that has a context.
It is easier to train neophyte spies that way (Army “Intelligence” Watching The Tubes – 2). If they were all as old as Alexander and Clapper they would not last long.
Darkmail opens: New email encryption standard aims to keep government agencies out; Alex Hern; The Guardian; 10/30/13
@orionATL: There’s no evidence that they’ve busted ssl encryption. It seems that they put a lot effort into acquiring/compromising keys, something they wouldn’t have have to do if they could just decyrpt any arbitrary ssl communications.
@Dredd: That’s a very good point. The data flows behind the Google Front End are far more complex than the data flows from the front end to users. What Google sends between its data centers won’t easily correspond to something tangible like “email from alex to bob”. It would take a lot more work to reassemble them into something useful.
quoting admiral mcraven (nice cumberbund):
“.. “Not since World War II has there been such a lethal combination of intelligence officers and special operations warriors. Not since the fight against Hitler have we had such a talented group of government civilians, intellectuals, businessmen, writers, philosophers, engineers, tinkers, tailors, soldiers, and spies.” He took a pause before declaring, “but, still, there will be some who doubt this resurgence. So let me put those doubts to rest…”
and for no purpose whatsoever that matches that firepower.
i’m here to tell admiral mcraven that the dust-up with a-q ain’t anywhere near as big or as serious as wwii.
why do we have this hidden military force?
because we’ve allocated inordinate and unnecessary amounts of money to the cause.
because we believe in the magic of mighty morphing rangers.
because we are foolish enough to believe if we focus on killing/capturing individuals, we can stop a movement.
does the good admiral have an end-game or does this shoot’em up go on and on into our future?
@Saul Tannenbaum:
thanks for that info.
@harpie:
this sounds very interesting. i hope it can take off.
@harpie: And here I’ve been waiting for Startmail.
– https://beta.startmail.com/
– http://www.youtube.com/watch?v=_3BXXblHVDA
But I think I’d rather have the USPS offer e-mail. I want to touch the Constitution.
http://www.emptywheel.net/2013/10/30/nsa-returns-to-stealing-from-yahoo-and-google/#comment-649273
@joanneleon: The OSS was a notorious failure that ended up accomplishing very little. Which is a lot of the reason why Truman abolished it. Why would anyone want to resurrect it?