NSA Conducts FISA Section 704 Collection Using Transit Collection
Please consider donating to support this work. It’s going to be a long four years.
The Intercept has a fascinating new story confirming what many people already intuited: AT&T’s spooky building at 33 Thomas Street is a key NSA collection point, and the NSA has equipment inside the building (it’s almost certainly not just NSA; this is probably also where AT&T collects much of their Hemisphere database and it likely includes AT&T’s special service center for FBI NSLs).
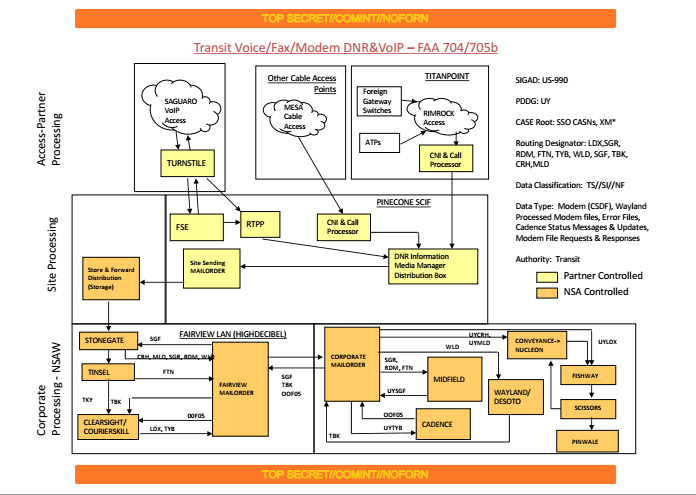
The Intercept released a bunch of documents with the story, including this one on FAIRVIEW.
It shows that FISA Section 704/705a are among the authorities used with FAIRVIEW, ostensibly collected under “Transit” authority, but with the collection done at TITANPOINT (which is the code name for 33 Thomas Street).
As I explain in this post, there are three authorities in the FISA Amendments Act that are supposed to cover US persons: 703 (spying with the help of domestic partners on Americans who are overseas), 704 (spying on Americans who are overseas, using methods for which they would have an expectation of privacy), and 705, which is a hybrid.
But Snowden documents — and this IG Report — make it clear only 704 and 705b are used.
Unsurprisingly, the disclosure standards are higher for 703 — the authority they don’t use — than they are for 704. In other words, they’re using the authority to spy on Americans overseas that is weaker. Go figure.
But here’s the other problem. 704/705b are two different authorities and — as reflected in Intelligence Oversight Board reports — they are treated as such. Which means they are using 704 to spy on targets that are overseas, not just defaulting to 705b hybrid orders (which would require the person to be in the US some of the time).
But they are doing it within the US, using the fiction that the collection is only “transiting” the US (that is, transiting from one foreign country to another). This seems to indicate the NSA is conducting electronic surveillance on US persons located overseas — which seems clearly to fall under 703 — but doing it under 704 by claiming traffic transiting the US isn’t really collection in the US. Correction: Because the person is located overseas, it doesn’t count as electronic surveillance. In any case, this seems to be effectively a way around the intent of 703.




No surprise at all.
1st or 4th Ammendment,
Fascists are just Honey Badgers.
https://www.techdirt.com/articles/20161116/08482936055/rutgers-lecturer-forcibly-sent-psych-evaluation-nypd-some-tweets-about-election.shtml
https://www.techdirt.com/articles/20161113/06093636030/appeals-court-to-cops-if-you-dont-have-time-constitutional-bullshit-you-dont-get-immunity.shtml
The three ‘core sites’.
641 Folsom Street (SF)
33 Thomas Street (NY)
12976 Hollenberg Drive (Bridgeton, MO. Suburb of STL – lots of lit fibre)
https://cryptome.org/eyeball/attwu/attwu-eyeball.htm
It is *NOT* about foreign intel.
I have commented before. I suspect basis is no warrant required for anything within 100 miles of a port of entry, including international airports, no warrant required for anything in the ether. I suspect the reason targeted individuals actually get their phones back at port of entry is that they crack the phone in the back room, download it all before giving it back. I suspect the primitive filter described in the SF ATT tap drawings was obsolete when it was written. There was a revolution in the fiber cable industry when multiple frequency bandwidths could be used on the same cable. The timing can be traced to sometime before they stopped the crazy mad laying of fiber and transmission costs fell for the public. I believe a garden hose fiber cable literally became a 1000 fire hoses overnight. It was now possible to vacuum up all net traffic. They drop the porn and netflix and other dross on the floor. One can presume that multiple agencies have been through the same drill for other signal traffic. If someone is using a higher frequency or frequency hopping techniques that you cannot digitally capture, you capture the analog preferably close to the transmitter and store for such time as you can decode it. One can also guess that use of the 100 mile port of entry search without warrant was used before the internet. Not something anyone would talk much less write about. They want it all for years in the past, so that if they get a connection in the present then they can find the connections in the past. Throwing the past away is a mugs game. Also interesting are the DNS pings used to analyse the Trump named server with the Russian bank server. More meta data to store without warrant.
Worked for them and now retired. They pull right off the fiber to and from the Backbone: cameras monitor access. none of this was a secret☪️
“None of this was a secret” Exactly, when you don’t want something known, you never leave a trail, you never generate a classified document, you never get a legal opinion. Who knows what is done on a wink and a nod. Is the guy making the pitch really still working for the government? See Bay of Pigs, Watergate, Rewald, BCCI, Blackwater, Stratfor, CACI, Cheney, fourth branch of government. [ All just a guess ]. Might take a Snowden to drop a clue on this.