Yahoo, the Law-Abiding Free Email Provider
![[NSA presentation, PRISM collection dates, via Washington Post]](http://www.emptywheel.net/wp-content/uploads/2013/06/WaPo_Prism-Slide5_06JUN2013_300pxw.jpg) The FISA Court has officially agreed to declassify that Yahoo was the company that challenged a Protect Amendment Act order in 2007.
The FISA Court has officially agreed to declassify that Yahoo was the company that challenged a Protect Amendment Act order in 2007.
Once this PRISM slide was published, it was always pretty likely that Yahoo — or maybe Google — was the company in question. Yahoo started complying around the time the FISC decision was reached; Google joined in after the FISCR decision was unsealed.
Which leaves … Microsoft, which started cooperating before the law and then the FISA Court forced it to (though collection may not have begun until after PAA passed and, as Rayne has pointed out, Microsoft’s code was being exploited by the government for entirely different purposes in precisely that timeframe).
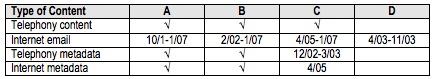
Now might be a good time to review what happened with the 7 companies the government asked to participate in an illegal wiretap program based solely on the President’s say-so. Per the 2009 NSA Draft IG Report, the companies are:
- Telecoms A, B, and C (probably AT&T, Verizon, and — definitely– MCI, respectively, since they were the 3 telecoms working onsite at FBI’s direct access office under another program). These companies were approached by people from NSA’s Special Source Operations unit as soon as the program was approved, and they agreed to participate “voluntarily.” In 2003, MCI got cold feet and demanded a letter from John Ashcroft stating that the request was lawful, in which he “directed” them to comply with NSA’s requests.
- Telecom E (Qwest). It was approached by SSO personnel in 2002, purportedly for collections related to the Olympics. After some discussion, Qwest’s General Counsel decided to not support the operation.
- Internet Provider D (probably Microsoft). This company was approached by “NSA legal and operational personnel” (not SSO) in September 2002. In response, this company provided “minimal” support, spanning roughly from October 9, 2002 through just after September 11, 2003. No person at this company was ever cleared to store letters from the NSA.
- Internet Provider F (probably Yahoo). This company was approached in October 2002 by NSA legal and operational personnel. In response to NSA’s request, Internet Provider F asked for a letter from Attorney General Ashcroft certifying the legality of the program. While in December 2002, NSA’s Commercial Technologies Group through Internet Provider F was participating, NSA’s GC says they did not because of corporate liability concerns.
- Private Sector Company G. This company was approached in April 2003 by NSA legal and operational personnel. This company’s GC said he or she wanted to consult outside counsel. NSA chose to drop the request. I have no idea what company this would be (CISCO?); any thoughts?
Here’s what these companies provided:
This table tells us a great deal about the program–and also the legal problems behind it.
Internet provider D — the one of two that cooperated — only did so for 7 months in 2003, and only provided Internet content (probably primarily Hotmail emails), not metadata.
Which left the government to get the other Internet data off of AT&T and Verizon’s switches (we know C is MCI because February 2005 is when Verizon bought it, which explains why it started handing over Internet content and metadata then). As the IG Report explains,
A, B, and C provided access to the content of Al Qaeda and Al Qaeda-affiliate email from communication links they owned and operated.
[snip]
The last category of private sector assistance was access to Internet Protocol (IP) metadata associated with communications of al Qaeda (and affiliates) from data links owned or operated by COMPANIES A, B, and C.
In other words, Microsoft and Yahoo, the biggest free email providers, were not crazy about providing content (though one, probably Microsoft, did for a period). And they were completely unwilling to provide IP metadata.
So the government just went to AT&T and Verizon’s switches and took it there.
Even the 2004 kluge to keep the Internet metadata program going after Jack Goldsmith and Jim Comey objected was a stretch, as the FISC Pen Register/Trap & Trace (PR/TT) solution was getting Internet metadata not from the Internet companies, but from the phone companies through whose networks the Internet providers’ data traveled. Before that, they were basically just stealing the Internet companies data.
Remember, in 2008 during the FISA Amendments Act debate, the trade group for tech companies including Microsoft, Yahoo, and Google, issued a letter stating,
The Computer & Communications Industry Association (CCIA) strongly opposes S. 2248, the “FISA Amendments Act of 2007,” as passed by the Senate on February 12, 2008. CCIA believes that this bill should not provide retroactive immunity to corporations that may have participated in violations of federal law. [my emphasis]
Basically, they wanted the telecoms to get busted for stealing their (customers’) stuff.


As you point out, a lot of this early post 9/11 “help” took place around the time of several large telecoms mergers. Each of which required antitrust clearance and approval from the Bush administration. Given the hundreds of millions in bonuses at stake, the hundreds of millions of promised cost cuts, and billions in projected profits (never mind the greater market concentration and oligopoly power), these companies had incentive to cooperate fully. Many of them did.
O/T but EW has posted about this person and the events leading to his death and here is an update from Carol Rosenberg @ miami herald
usa military faults guards in Guantánamo captive’s suicide by overdose
A usa military investigation found Guantánamo troops didn’t follow their own rules, allowing a captive to take a fatal overdose of an anti-psychotic drug a day after he was moved into a disciplinary cell from the detention center’s psychiatric ward.
A 79-page report, released Friday under the Freedom of Information Act, showed the “standard operating procedures,” or SOP, governing the us Army Military Police required soldiers to regularly check on captives kept in solitary cells at Camp 5, Guantánamo’s maximum-security lockup.
Troops didn’t do it for at least two shift changes before Yemeni captive Adnan Latif was discovered dead on the floor of his Camp 5 cell at the us Navy base in southeast Cuba on September 8, 2012.
http://www.miamiherald.com/2013/06/28/3475559/military-faults-guards-in-suicide.html
This explains the “you should use both” line in the slides. Clearly PRISM does an end-run aroud corporate unwillingness by providing a single mechanism that links the data no matter how it was collected (probably via ip and date) and allows the analyst to use nsl data for indexing the fat stream.
What and why did the NSA need this information? Did the NSA go to email providers for redundancy or economy? If the NSA was already filtering the internet backbone then why go to the email and web browser providers?
How does the SF ATT switching center tap fit into the scheme of things?
http://www.wired.com/threatlevel/2013/06/nsa-whistleblower-klein/
Where else in the internet backbone was the NSA siphoning data streams?
The way I read this, which may be wrong, if I sent gmail (Google mail) via AT&T DSL, then any emails captured would have been thanks to AT&T?
I also have a Yahoo mail account (required by flickr) but don’t use it to send email. But, if I had sent email, would the fact that I use AT&T DSL have trumped Yahoo?
I’m not clear about how the email provider and the internet connection provider are separated or not, for practical purposes.
@earlofhuntingdon: And the two that challenged this program in any way? Poof!
@C: Well, they’re ALSO getting some other materials from the switches. But yeah, that’s what they were doing in the Folsom street room.
@emptywheel:
how come i never read anything about comcast? have i just missed it?
they’ve got both internet and phone business.
What It’s Like to Get a National-Security Letter
http://www.newyorker.com/online/blogs/elements/2013/06/what-its-like-to-get-a-national-security-letter.html
@emptywheel: Refusal for NSA spying
In May 2006, USA Today reported that millions of telephone calling records had been handed over to the United States National Security Agency by AT&T, Verizon, and BellSouth since September 11, 2001. This data has been used to create a database of all international and domestic calls. Qwest was allegedly the lone holdout, despite threats from the NSA that their refusal to cooperate may jeopardize future government contracts, a decision which has earned them praise from those who oppose the NSA program.
Former Qwest CEO Joseph Nacchio, convicted of insider trading in April 2007, alleged in appeal documents that the NSA requested that Qwest participate in its wiretapping program more than six months before September 11, 2001. Nacchio recalls the meeting as occurring on February 27, 2001. Nacchio further claims that the NSA cancelled a lucrative contract with Qwest as a result of Qwest’s refusal to participate in the wiretapping program. Nacchio surrendered April 14, 2009 to a federal prison camp in Schuylkill, Pennsylvania to begin serving a six-year sentence for the insider trading conviction. The United States Supreme Court denied bail pending appeal the same day.
https://en.wikipedia.org/wiki/Qwest#Refusal_for_NSA_spying
@earlofhuntingdon:
maybe co-operation with the gov in spying on its customers facilitates this corporate behavior:
http://www.muninetworks.org/content/atts-many-broken-merger-promises
@orionATL: Several reasons.
1) This is still supposed to be foreign focused. Few terrorists in Yemen are using Comcast as their phone service.
2) I don’t THINK Comcast’s networks are built the same, meaning they don’t route stuff the same way the telecoms do.
In any case, this was primarily about phone calls and email sitting in servers here in the US.
thanks.
i was thinking of the portion of the spying involving u.s. citizens directly.
prism would do that only indirectly – though, i if read you correctly, quite effectively.
thanks.
i was thinking of the portion of the spying involving u.s. citizens directly.
prism would do that only indirectly – though, i if read you correctly, quite effectively.
OT — Last night we noticed we can’t directly access guardian.co.uk any more. When we type that in, it goes to guardiannews.com instead. In the context of military Internet blocking of the Guardian, we’re a little concerned… Has anyone else experienced anything similar?
NSA collects stuff super-wholesale.
@Hmmm: great catch. i just tried – having logged onto the UK site many times – and it redirects to the US version guardiannews.com. Can’t access the UK version.
something’s up.
@Hmmm: I think it’s actually something they’ve done in the last year to try to build their US-specific website. It was supposed to be in place some time ago. They may be pushing that now that they’re getting all that traffic.
There’s a little drop-down tab in the upper left corner marked “Edition”, with choices of UK, US, or AU. Hadn’t noticed that before, though it may have been there for a while.
This page can be reached on any edition:
http://www.guardian.co.uk/commentisfree/series/glenn-greenwald-security-liberty
If you change the edition, you start over, it doesn’t stay on the same page.
Marcy’s suggestion that they’re trying to accommodate greater traffic from the US sounds reasonable.
@omphaloscepsis: thx, just tried. Was able to access Australia, but “UK” redirects to USA site. FWIW.
@P J Evans:
and to answer a question ask by a commenter about u.s. companies being “u.s. persons” (using the orwellian legal jargon of the united states department of justice) posed in an earlier ew post:
“…And Binney recently told Zero Hedge that the government believes it can gather and use any information (including content) about American citizens living on U.S. soil if it comes from “any service provider … any third party … any commercial company – like a telecom or internet service provider, libraries, medical companies – holding data about anyone, any U.S. citizen or anyone else.”
this fills in another cell in the “matrix of lies, excuses and evasions” involving presidential and generalissimo assurances of adequate “checks and balances”, “transparency”, and “lawful laws” which i suggested politicians like wayden and udall need to construct to educate the public in detail about the false assurances of the prez and the generalissimos that citizens’ privacy is being protected from gov’t intrusion.
@orionATL:
I posted the first couple of paragraphs of the post on Wyden’s letter, at SFgate. I didn’t emphasize any of the list of databases, but I made clear that there isn’t anything they’ll skip if they want to track you.
I did that because there are people who figure going cash-only will keep them from being tracked.
Question from Corrente: Yahoo has just gone to scanning all their e-mail accounts. But the account holder has to hit a button saying “Switch now” (see screenshot) to agree to the new terms. I think G-mail has been doing that all along. There is no alternative — accept the new terms or never access your e-mail again.
What’s up with making you hit the button? What choice would you ever have had? Are there some rights we don’t know about?
http://correntewire.com/common_household_remedies_request_126
@thatvisionthing: Second part to that is suggestion that USPS should provide e-mail service and bring back Constitutional right to privacy:
So, wondering, all this focus on telecom — what about snailmail? Have they been warrantlessly opening your snailmail too?
@thatvisionthing: Your comment about snail mail made me think: is there supposed to be a higher standard of “warrants” for landlines vs. cell phones? Does a landline tap actually still require a warrant? Or is that just a quaint notion now?
@thatvisionthing:
I remember after the anthrax mailings, there was news that the USPS keeps “metadata” of the sender and receiver of the mail. I assume there are machines that can read through paper without having to physically open the envelope now. If so, then I guess it would be on the government’s to do list.
@pdaly: It’s just my feeling that if we wanted to connect privacy tangibly to the Constitution again, and what I assume is over two hundred years of law and legal theory on the right to privacy in your communications, and a commitment to open public information, the place to start is the place it started – the USPS. I see no reason why they can’t provide e-mail services and internet services. It’s just keeping up with the times, pony express carried forward. Plus many other suggestions for the post office, like simple banking, VOIP, wifi, cell phone service, etc. were given at Corrente, I guess they’ve been talking about this for a while. Turn all the evil NSA hardware over to the post office and let it be put to good public use. Sunshine!
Then we’d be reclaiming our commons, and our heritage. What a relief! I think it would be like recovering function of a numb limb. Joy, well-being, thankfulness, connectedness, wholeness.
Also, more thought: You’ve got a few hidden singular malevolencies behind this whole scheme, Cheney, Addington, Hayden, Brennan, and then you’ve got operatives like Feinstein and Holder and Obama and most of Congress who for all I know could be being blackmailed or just need to do the authority thing, you got greed-seeking corporate mofos, and then not too far from there you get to humanity, everybody else. Actually you take off the motu/mofo hats, they’re humanity too. My feeling is it’s just natural and simple human decency to want your privacy in your private communications. If you post something publicly, you’re sharing it with the world, and that’s fine. If you’re writing me to you, you expect privacy. A government that can’t see that and can’t DO that is a fail. America used to be able to do that, and the words are still there.
Giving up your right to privacy is not giving up a frill. It’s not perfecting our union. It’s rot, and it’s dissolving the union.
katiebird, 4/28/12: http://riverdaughter.wordpress.com/2012/04/28/save-the-post-office-make-up-for-the-drop-in-physical-volume-with-digital-services/
Check it re MCI and note where. Was told USG had access to all of MCI’s communications channels by 1996.
@posaune: From Marcy’s interview last week:
Don’t know if that answers your question, but land lines are included and Marcy still has questions about who does what with the data and how.
@thatvisionthing: late edit: Wait… Verizon? Land line?
@thatvisionthing: The Yahoo e-mail account came with AT&T DSL service. I found this story from 2006 — oddly familiar?
So wait. My question is, if AT&T has already been openly doing this for seven years, why would Yahoo – same account in this case – now require its own signoff to scan and track and disclose your e-mail? Again, are there rights e-mail account holders actually have now, before clicking the button to agree to new terms? So curious.
Last thing, in regard to earlier suggestion for USPS to become internet and e-mail provider as a means to regain privacy and commons. Marcy’s interview perhaps explains it from another direction. I was thinking the privacy would come from the post office’s constitutional origin and direct line to an actual effective Fourth Amendment, but perhaps it’s also because it’s two-party, you-to-USPS/govt, with no Third Party Doctrine involved:
(With three you get shell game and no privacy? Different with two?)