Spying on Americans: A “Team Sport” Since 2004
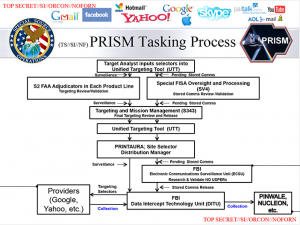 One of the more colorful revelations in today’s Guardian scoop is the newsletter piece that describes increased sharing of PRISM (Section 702) data with FBI and CIA.
One of the more colorful revelations in today’s Guardian scoop is the newsletter piece that describes increased sharing of PRISM (Section 702) data with FBI and CIA.
The information the NSA collects from Prism is routinely shared with both the FBI and CIA. A 3 August 2012 newsletter describes how the NSA has recently expanded sharing with the other two agencies.
The NSA, the entry reveals, has even automated the sharing of aspects of Prism, using software that “enables our partners to see which selectors [search terms] the National Security Agency has tasked to Prism”.
The document continues: “The FBI and CIA then can request a copy ofPrism collection of any selector…” As a result, the author notes: “these two activities underscore the point that Prism is a team sport!”
But that’s something that has actually been built into the program for years. While the Joint IG Report on the illegal wiretap program claimed,
NSA also was responsible for conducting the actual collection of information under the PSP and disseminating intelligence reports to other agencies such as the Federal Bureau of Investigation (FBI), the Central Intelligence Agency (CIA), and the Office of the Director of National Intelligence (ODNI) National Counterterrorism Center (NCTC) for analysis and possible investigation.
The Draft NSA IG Report explained,
Coordination with FBI and CIA. By 2004, four FBI integrees and two CIA integrees, operating under SIGINT authorities in accordance with written agreements, were co-located with NSA PSP-cleared analysts. The purpose of co-locating these individuals was to improve collaborative analytic efforts.
And the minimization procedures released by the Guardian (which date to 2009), make it clear NSA can provided unminimized content to CIA and FBI on whatever selectors they request.
6(c)
(1) NSA may provide to the Central Intelligence Agency (CIA) unminimized communications acquired pursuant to section 702 of the Act. CIA will identify to NSA targets for which NSA may provide unminimized communications to CIA. CIA will process any such unminimized communications received from NSA in accordance with CIA minimization procedures adopted by the Attorney General, in consultation with the Director of National Intelligence, pursuant to subsection 702(e) of the Act.
(2) NSA may provide to the FBI unminimized communications acquired pursuant to section 702 of the Act. FBI will identify to NSA targets for which NSA may provide unminimized communications to the FBI. FBI will process any such unminimized communications received from NSA in accordance with FBI minimization procedures adopted by the Attorney General, in consultation with the Director of National Intelligence, pursuant to subsection 702(e) of the Act.
And none of that should be surprising, given the tasking slide — above — that was first published by the WaPo. FBI, at least, is solidly in the midst of this collection, for a program deemed to be foreign intelligence collection.
There have been a variety of claims about all this team sport participation. But I’m not convinced any of them explain how all this works.
And in perhaps related news, the Fifth Circuit today said that Nidal Hasan could not have access to the FISA material on him, in spite of the fact that William Webster published a 150 page report on it last year. Legally, that material should be utterly distinct from PRISM, since a wiretap on Anwar al-Awlaki would require a specific FISA warrant (and the latest Guardian scoop refers to expanded cooperation since 2012). But I suspect the reason Hasan, the FISA evidence against whom has already been extensively discussed, can’t see it is because we would see what this actually looks like from the FBI side.
DOJ has to protect its team, you know.

So, after reading the last post, I was going to post a comment. But I got bogged down trying to locate a clip from “Airplane!” that seemed related, which I couldn’t find. I come back to see the new post here. And I’m just going to post here what I was going to say earlier, because it applies to both posts. So here goes:
We are all so friggin’ screwed!
Before its acquisition by Microsoft, Skype had a reasonable privacy policy, which was one reason it had garnered its hundreds of millions of global users, including quite a few Americans.
On (and before) its acquisition by the Microsoft hive, that policy went down the virtual rabbit hole. The result was entirely predictable. It was, no doubt, one of the reasons Microsoft paid so handsomely for Skype. (Added to which, Skype is now part of the hive, and not a high value-add independent.)
As John D. Rockefeller could have said, it’s always easier to buy a monopoly than to invent one. The trick is persuading the government to leave you alone afterwards; that trick no longer seems a secret to anyone but the American public.
Does anyone still wonder why Mr. Snowden felt obligated to share his knowledge with his fellow citizens?
I particularly liked that codename, Team Sport. EVILOLIVE is still my favorite though, in a sickening kind of way. I am happy that they are so clever with some their code names though because they reveal often something about the program, and the attitude of the people who build them and direct the projects.
From the LiveEvil sessions,
The man was nothing if not prescient.
@prostratedragon:
The last few notes at the end, that mark a sudden change of tone, quote another piece titled “Sanctuary.”
Sport SPORT! I bite my tongue.
Sometimes it helps to go simple.
And your last two posts point up, not the venality of Microsoft (who knew?)but what seem to me to be two major extensions in our knowledge.
By the way, from where I sit in the UK, though I do of course recognise the US constitutional issue, the fact that the US is spying on me personally and as I very frequently email the US they can have a picture of some importent elements of my life, seems even more evil than that it can spy on you.
But to the extensions.
How can video be metadata? We are being sold regularly by the securocrats that all that is really being kept universally is essentially “who and when”. But I absolutely don’t understand how metadata gets extracted from actual video rather than the fact of there being a videocall.
They have access to the cloud?!!!! Many people never think of the cloud as even being communication; to them it is part of their home computer system. Now I would never ever consciously use the cloud for storage for a myriad of reasons, but now I have the best one.
Suppose theoretically I had privately mused for my own edification and analysed in detail the justification of the actions of Hamas when every other course is closed to them and they are under illegal occupation (I haven’t Mr NSA! Don’t bother looking). I press “save” and off it goes to the cloud. Have I “communicated” that view to Microsoft’s cloud if I merely keep my musings there? Am I thus supporting terrorism and working against “fridom”? Do I trust some crazed right-wing bureaucrat not to think that and act upon it at some time? The answer to the last question is clearly “No”.
Do they read my comments on your site and report me to MI6 as a potential subversive, to be put on the list of those who can properly be spied upon by undercover UK secret policemen posing as my friends (see recent UK stories)?
For the first time I am actually scared.