The 5-Eyes Tippecanoe — Er, Tipping & Cueing
 CBC has a scathing report about a pilot project their SIGINT agency, CSEC, did in 2012, tracking the free WiFi in Canadian airports. The article — with lots of quotes from furious people describing how illegal this is under Canadian law — is here, and the backup document is here.
CBC has a scathing report about a pilot project their SIGINT agency, CSEC, did in 2012, tracking the free WiFi in Canadian airports. The article — with lots of quotes from furious people describing how illegal this is under Canadian law — is here, and the backup document is here.
The PowerPoint is just as interesting for the methodological details as it is for the fact that CSEC is collecting off of airport (and hotel and other public) WiFi sites and doing so to hunt imagined kidnappers, not to find terrorists.
It shows how a joint 5-Eyes “Tipping and Cueing Task Force” is working on ways to track IP-based identities across many sites. (As a reminder, “5-Eyes” refers to the UK, US, Canadian, Australian, New Zealand intelligence partnership.)
Tipping and Cueing Task Force (TCTF)
- a 5-Eyes effort to enable the SIGINT system to provide real-time alerts of events of interest
- alert to: target country location changes, webmail logins with time-limited cookies etc.
I’m particularly interested in the name: “Tipping and Cueing.”
I’m interested in it for one more reason. We’ve heard the term “tipper” before — it’s what NSA calls query results that get sent to FBI from the phone dragnet. The term implies that data analysis shows something new, which then gets shared with other intelligence agencies and law enforcement.
But this presentation makes it clear that, unsurprisingly, it’s a two way street. This dragnet process serves not only to identify new leads, but also as a panopticon tracking identified “targets.”
I raise this for one more reason. At least as early as February 25, 2010, the language used to describe the information shared with FBI from the dragnet changed.
Previously, it had used the term “tipped” (and when this whole Snowden process started, that’s what NSA defenders used to describe the information — tippers).
The dragnet orders started referring to the information shared more generically: “any information the FBI receives as a result of this Order.”
Again, none of this is surprising. The existence of the “alert” list that caused all the troubles in 2009 made it clear this functions as part of a panopticon as much as it does a lead generation tool.
But it’s worth noting that the 5-Eyes are actually fighting a losing battle against “the Natives”* that is far more intrusive than all that.
Update: I noted above CSEC ran this test on an imagined kidnapper, not a terrorist. The Globe and Mail reports that the number of Mounty requests for help from CSEC is going up, and it may be a way to bypass warrant requirements.
* [Update] This was meant to be a joke that both the Battle of Tippecanoe and the 5-Eyes’ Tipping and Cueing target “natives” by deeming us foreign to our own land. Given joanneleon’s comment I realize I was being too subtle.


“…
tippicanoe and the kitchen sink too.
“… i’m interested in it for one more reason. We’ve heard the term “tipper” before — it’s what NSA calls query results that get sent to FBI from the phone dragnet. The term implies that data analysis shows something new, which then gets shared with other intelligence agencies and law enforcement.
But this presentation makes it clear that, unsurprisingly, it’s a two way street. This dragnet process serves not only to identify new leads, but also as a panopticon tracking identified “targets.” …”
for the very-well versed on electronic spying it is probably well understood, but for me (and i’d guess there a plenty like me) there are a lot of fuzzy issues.
one that relates to this post is this:
– is the fbi a client of the nsa?
asked slightly differently, does the fbi depend largely on the equipment and personnel of the nsa to meet its electronic spying needs?
or is it that the fbi merely benefits occassionally from tidbits handed it by the nsa?
– put another way, do the fbi and the nsa run two parallel but (mostly) independent electronic spying activities?
my initial assumption was that nsa machinery and personnel had been placed at the disposal of fbi, dea, dhs, cia, and whoever else needed electtonic spying, despite the legal prohibition that nsa cannot operate in the u.s.
i’m not sure now that spying matters are so neatly arranged.
if that’s the case i’d like to know more about the fbi’s spying.
“the Natives”? What am I missing?
I like the fact that you are focusing in on the working relationship between FBI and NSA, and the two-way data flow. There isn’t nearly enough reporting on FBI’s involvement in this, which gives a false sense of security to a lot of people, I think.
This pilot program in Canada doing location tracking — I’m surprised that it’s being presented as a tool developed by Canada that will be shared with other Five Eyes partners because almost certainly the NSA, working with our military, has been doing this kind of tracking in the Middle East. But most areas there don’t dense Wifi coverage, so maybe this is a new thing that only works well in areas densely populated with Wifi whereas in the Middle East this kind of tracking would be done with cell phone/telecom data. Done in Canada, you’re on the same continent as the US so the systems should be more easily portable into the US proper. I’m just ramble-speculating. The article mentions that the docs they read gave a sense that the Canadian spy agency was kind of trying to show off what they could do.
The kidnapping thing is an obvious fake justification for the kind of panopticon you mention. Since when do we have such urgent kidnapping issues that we have to gut democracy and every privacy law to address them? I’m sickened by the way they use crisis situations to justify these things when it is so freaking obvious what they might really be used for. How can such an overall intelligent mass of people in the world not see this coming? Well, based on polls, I think they do. All you have to do is read some of the comments on the CBC article to see that nobody is buying the terrorism or kidnapping smoke screen.
@joanneleon: It was a reference to the actual battle of Tippecanoe as well as a reference to the way these agencies say they’re not targeting Canadians (or Americans), when really they mean they’re doing so by calling us all foreign intelligence.
Too subtle, I guess?
@joanneleon: It was a reference to the actual battle of Tippecanoe as well as a reference to the way these agencies say they’re not targeting Canadians (or Americans), when really they mean they’re doing so by calling us all foreign intelligence.
Too subtle, I guess?
I recall kidnapping being used as a justification for towns and sheriffs getting military surplus vehicles and Bearcats, etc. Even though kidnappings are a rarity in the US, as far as I know, but pretty common in countries where we invade or run special operations, drone programs, etc.
Given that the wealthiest few are starting to worry more about the “class warfare” of the 99% against the poor, pitiful 1%, I’m guessing they’d be all for programs like this. The 1% don’t stand a chance against a real uprising of the 99%, though they might think that massive automation and surveillance could give them their best possible odds. In a sense, our military acts like the 1%, with one country and its partners trying to rule and police most of the world as a sole superpower trying to mainatain its position as sole superpower.
But what happens when that sole superpower usurps so much of the domestic resources and gave away so much of its economic power that it gutted the huge middle class who paid for it, not even knowing what they were paying for, and can no longer pay for it because of the economic ruin? It almost sounds like a particular island nation in the Atlantic a few centuries ago, needing to extract wealth from other places, like the New World, to maintain it’s imperial machine. There are probably plenty of parallels from the Roman empire too but I’m not knowledgeable enough about ancient history to cite them.
In any case, from a selfish standpoint, is one of the first steps to shut down the people at home who see what’s going on and speak out about it or protest against it or try to effect change against it?
@emptywheel: Oh duh, sorry about that. No, not too subtle, just me having less caffeine this morning and having my head wrapped up in the latest stories.
@joanneleon: Hey, stranger. Excellent commentary, Joanne! Thank you!
@joanneleon:
The 5 Eyes aren’t just “fighting crime”–and, as the FBI and various nations’ intelligence agencies have enabled same with regard to well over 200 domestic and international cases over the past few years: If there aren’t enough “terrists,” they simply manufacture/enable/finance them–because it’s what they’re “thinking” of doing, even if they don’t verbalize it (and can’t afford to carry out their “thoughts”), that matters.
But, our respective intelligence entities aren’t stopping there. They’re laser-focused upon ordinary/everyday pre-crime, as well!
From George Washington’s Blog and The Guardian over the past few days: (“Spy Agencies Work On Psychologically Profiling Everyone”) LINK: http://www.washingtonsblog.com/2014/01/future-spying-techniques.html.
Gotta’ feed those corporate beasts, ya’ know…
So how is it done, and how to avoid it?
There was one line in there that made me go “hmmmm”.
They mentioned arrivals not really being track-able due to not connecting to WiFi and just using (if at all) the GSM/CDMA networks.
So, they must either have pre-positioned WiFi sniffers at likely WiFi hotspots, or they have the co-operation of the operators of the routers, to either send data, or allow the IC to log into the routers.
What does a WiFi radio send out? Well, two pieces of information that would be very nice to have for tracking purposes, are the MAC Address and Host or Machine Name. Both of these are sent in the clear, over the air, and they also appear in router logs, per IP assignment.
MAC addresses are kept in an OUI database, per manufacturer. I wonder if the IC has the master list of every MAC address assigned to a piece of hardware. (The OUI database contains only the first 6 HEX…not sure if mfgs keep track of the last 6?)
The Host Name is randomly generated on mobile “John’s-iPhone” or “android-235926612”, or it can be defined by the user for computers. That name you type in when you install Windows, ie. “John-PC” is what gets logged in the router during DHCP assignment.
Think of them the same as the IMEI and IMSI for cell radios. But they don’t leave the local network, over the net…they stop at the router.
So, you buy a phone with a credit card. The mfg knows what MAC is in there (last 6 Hex too???), as well as the IMEI for cell. The carrier knows the same for the SIM IMSI…all tied back to you and your credit card. Sniffing any of these, if they have a database with mfg co-operation, can both track you, and ID you.
Going back to just the anonymous (but track-able) MAC and host name (went on a tangent there)… Don’t use WiFi anywhere but your house. Technical users on mobile devices can change their MAC and Host Name. Both can be done to laptops as well, and is a bit easier.
If that’s how this all works…
@orionATL:
this has a bearing on the how many americans or how many u.s. persons are surveilled in some unit of time.
nsa has authorized itsef to do “hops” – persons connected largely tangentially to the initial persons of interest. the more hops, the more people netted in the dragnet.
if the fbi, dea, dhs, et al also have their own electronic surveillance systems then the number of americans surveilled would be larger than the nsa figure (unless each happens to include the same people).
one would need to add together all the independent surveillance systems operating in the u.s. to get the true number of ameticans spyed on by their government.
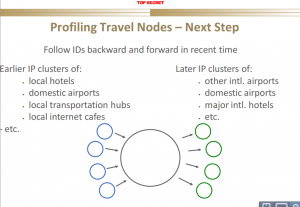
The Powerpoint is facinating reading to get a sense of how the intelligence agencies approach these problems and the sophistication of their computational and analytic techniques.
Take this, for example:
First, APL? Wow, I haven’t thought about APL in decades.
But second, it would seem that Canadian intelligence wasn’t using any of the standard “big data” techniques that are the bread and butter of Google/Facebook/Yahoo/Apple/Twitter/etc. That’s all that’s really being described here: a massively parallel Linux computing cluster running the NSA’s Accumulo. For Canada to be that far behind in 2012 is a little bit surprising.
Third, I would really love to see this methodology compared with how web advertising/marketing companies are building profiles to get a sense of its sophistication. They’re aiming to do the same sort of thing: aggregate web behavior across time and device, correlating back to an individual.