Leahy’s Freedom Act May Not Change Status Quo on Records Other than Call Records
Update: According to the DOJ IG NSL Report released today, the rise in number of Section 215 orders stems from some Internet companies refusing to provide certain data via NSL; FBI has been using Section 215 instead. However they’re receiving it now, Internet companies, like telephone companies, should not be subject to bulk orders as they are explicitly exempted.
WaPo’s MonkeysCage blog just posted a response I did to a debate between H.L. Pohlman and Gabe Rottman over whether Patrick Leahy’s USA Freedom includes a big “backdoor” way to get call records. The short version: the bill would prevent bulk — but not bulky — call record collection. But it may do nothing to end existing programs, such as the reported collection of Western Union records.
In the interest of showing my work, he’s a far more detailed version of that post.
Leahy’s Freedom still permits phone record collection under the existing authority
Pohlman argues correctly that the bill specifically permits the government to get phone records under the existing authority. So long as it does so in a manner different from the Call Detail Record newly created in the bill, it can continue to do so under the more lenient business records provision.
To wit: the text “carves out” the government’s authority to obtain telephone metadata from its more general authority to obtain “tangible things” under the PATRIOT Act’s so-called business records provision. This matters because only phone records that fit within the specific language of the “carve out” are subject to the above restrictions on the government’s collection authority. Those restrictions apply only “in the case of an application for the production on a daily basis of call detail records created before, on, or after the date of the application relating to an authorized investigation . . . to protect against international terrorism.”
This means that if the government applies for a production order of phone records on a weekly basis, rather than on a “daily basis,” then it is falls outside the restrictions. If the application is for phone records created “before, on, [and] after” (instead of “or after”) the date of the application, ditto. If the investigation is not one of international terrorism, ditto.
However, neither Pohlman nor Rottman mention the one limitation that got added to USA Freedumber in Leahy’s version which should prohibit the kind of bulk access to phone records that currently goes on.
Leahy Freedom prohibits the existing program with limits on electronic service providers
The definition of Specific Selection Term “does not include a term that does not narrowly limit the scope of the tangible things … such as–… a term identifying an electronic communication service provider … when not used as part of a specific identifier … unless the provider is itself a subject of an authorized investigation for which the specific selection term is used as the basis of production.”
In other words, the only way the NSA can demand all of Verizon’s call detail records, as they currently do, is if they’re investigating Verizon. They can certainly require Verizon and every other telecom to turn over calls two degrees away from, say, Julian Assange, as part of a counterintelligence investigation. But that language pertaining to electronic communication service provider would seem to prevent the NSA from getting everything from a particular provider, as they currently do.
So I think Rottman’s largely correct, though not for the reasons he lays out, that Leahy’s Freedom has closed the back door to continuing the comprehensive phone dragnet under current language.
But that doesn’t mean it has closed a bunch of other loopholes Rottman claims have been closed.
FISC has already dismissed PCLOB (CNSS) analysis on prospective collection
For example, Rottman points to language in PCLOB’s report on Section 215 stating that the statutory language of Section 215 doesn’t support prospective collection. I happen to agree with PCLOB’s analysis, and made some of the same observations when the phone dragnet order was first released. More importantly, the Center for National Security Studies made the argument in an April amicus brief to the FISC. But in an opinion released with the most recent phone dragnet order, Judge James Zagel dismissed CNSS’ brief (though, in the manner of shitty FISC opinions, without actually engaging the issue).
In other words, while I absolutely agree with Rottman’s and PCLOB’s and CNSS’ point, FISC has already rejected that argument. Nothing about passage of the Leahy Freedom would change that analysis, as nothing in that part of the statute would change. FISC has already ruled that objections to the prospective use of Section 215 fail.
Minimization procedures may not even protect bulky business collection as well as status quo
Then Rottman mischaracterizes the limits added to specific selection term in the bill, and suggests the government wouldn’t bother with bulky collection because it would be costly.
The USA Freedom Act would require the government to present a phone number, name, account number or other specific search term before getting the records—an important protection that does not exist under current law. If government attorneys were to try to seek records based on a broader search term—say all Fedex tracking numbers on a given day—the government would have to subsequently go through all of the information collected, piece by piece, and destroy any irrelevant data. The costs imposed by this new process would create an incentive to use Section 215 judiciously.
As I pointed out in this post, those aren’t the terms permitted in Leahy Freedom. Rather, it permits the use of “a person, account, address, or personal device, or another specific identifier.” Not a “name” but a “person,” which in contradistinction from the language in the CDR provision — which replaces “person” with “individual” — almost certainly is intended to include “corporate persons” among acceptable SSTs for traditional Section 215 production.
Like Fedex. Or Western Union, which several news outlets have reported turns over its records under Section 215 orders.
FISC already imposes minimization procedures on most of its orders
Rottman’s trust that minimization procedures will newly restrain bulky collection is even more misplaced. That’s because, since 2009, FISC has been imposing minimization procedures on Section 215 collection with increasing frequency; the practice grew in tandem with greatly expanded use of Section 215 for uses other than the phone dragnet.
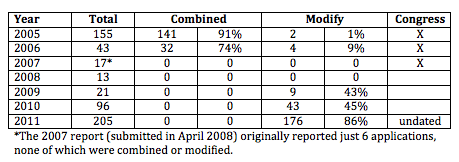
While most of the minimization procedure orders in 2009 were likely known orders fixing the phone dragnet violations, the Attorney General reports covering 2010 and 2011 make it clear in those years FISC modified increasing percentages of orders by imposing minimization requirements and required a report on compliance with them
The FISC modified the proposed orders submitted with forty-three such applications in 2010 (primarily requiring the Government to submit reports describing implementation of applicable minimization procedures).
The FISC modified the proposed orders submitted with 176 such applications in 2011 (requiring the Government to submit reports describing implementation of applicable minimization procedures).
That means the FISC was already requiring minimization procedures for 176 orders in 2011, only 5 of which are known to be phone dragnet orders. And while we don’t have the same language confirming this was about minimization, FISC modified 141 of 178 (79%) 215 applications last year, and 200 of 212 (94%) applications the year before. FISC is on pace to approve around 200 215 orders this year as well.
In other words, for several years, the majority of 215 orders have definitely (in 2011) or probably (the last two years) had minimization procedures attached to them. And it appears the FISC has required implementation reports for those minimization procedures; such reports are not specifically required under Leahy Freedom.
Also, there’s one big problem with the fact that Leahy’s Freedom doesn’t fundamentally rewire the Section 215 provision to account for the way it’s used. As written, it only applies to FBI. That includes, especially, section g, which mandates minimization procedures. The section, even as rewritten under Leahy’s bill, starts this way.
The Attorney General shall adopt specific minimization procedures governing the retention and dissemination by the Federal Bureau of Investigation of any tangible things, or information therein, received by the Federal Bureau of Investigation in response to an order under this subchapter.
See this post on how DOJ’s IG Glenn Fine tried to deal with this.
In any case, to the extent the Primary Orders we’ve seen impose minimization procedures, they do so on specific orders; this language is currently dealt with using a nod to the AG Guidelines.
Moreover, there is absolutely no reason to believe the minimization procedures imposed by Leahy’s Freedom will be any more stringent than what the FISC has already authorized. On the contrary, there’s at least one reason to believe they’ll be less stringent.
That’s because for the one set of minimization procedures we can compare, head-to-head, Leahy Freedom is not as strict as the status quo.
Emergency Procedure retention procedures are more lenient under Leahy’s bill
Here are the procedures for records obtained under the current emergency provision in case the Court subsequently denies the application, instituted in February.
In the event the Court were to determine that RAS was lacking [in an Emergency query], the government would be required to take appropriate remedial measures, including any steps the Court might direct (e.g., destroying the results of the emergency query and recalling any reports or other disseminations based on those results).
So under the current situation, the Court decides what to do if the Court finds an Emergency query doesn’t meet RAS standards, and the Court specifically envisioned this to include destroying the records.
Whereas, the procedures for a denied Emergency application under Leahy’s Freedom do not envision the destruction of the records at all, and they place compliance with them entirely with the Attorney General, not the FISC.
(5) If such application for approval is denied, or in any other case where the production of tangible things is terminated and no order is issued approving the production, no information obtained or evidence derived from such production shall be received in evidence or otherwise disclosed in any trial, hearing, or other proceeding in or before any court, grand jury, department, office, agency, regulatory body, legislative committee, or other authority of the United States, a State, or a political subdivision thereof, and no information concerning any United States person acquired from such production shall subsequently be used or disclosed in any other manner by Federal officers or employees without the consent of such person, except with the approval of the Attorney General if the information indicates a threat of death or serious bodily harm to any person.
(6) The Attorney General shall assess compliance with the requirements of paragraph (5).
This vesting of compliance authority with the AG rather than FISC parallels a troubling move to put the AG in charge of “privacy procedures” for PRTT collection.
So there’s no reason in the least to believe minimization procedures laid out in Leahy’s Freedom are even as strict as current procedures are.
Leahy’s minimization procedures still permit two hops
Moreover, on their face the minimization procedures mandated by Leahy’s Freedom permit two hops for the old fashioned “tangible things” authority, contrary to what Rottman claims here.
If it uses the new and more limited authority under the USA Freedom Act, the government can get records on all of the individuals in contact with the target and then all of the individuals in contact with those individuals. In the parlance of the FISC, the government can go two “hops” out from the target phone, which it would not be able to do under “tangible things” authority.
The “tangible things” minimization procedures permit the indefinite retention of information that “relate[s] to a person [1 hop] who is … in contact with or known to … a suspected agent [2 hop] of a foreign power who is associated with a subject of an authorized investigation” (see 103(c)(3), section (C)(iv)(II)).
If the government collected all of Western Union’s transfers between the US and the Middle East (using a corporate person as the Specific Selection Term, as permitted by the bill), and then conducted queries on the subject of an authorized investigation (the RAS seed), they could get Western Union records “related to” both any person who transferred money directly to that RAS seed (who would be a suspected agent of a foreign power by nature of transferring money to him), as well as anyone in contact with that person, perhaps because he sent the suspected agent money as well. Similarly, the government might be able to obtain all of Amazon’s purchase records or Google’s URL searches for pressure cookers, and cross reference the people associated with those records with the dragnet networks of the Tsarnaev brothers to see if any associate (one degrees) or person in contact with an associate (two degrees) of the brothers was looking for pressure cookers. (In an ideal world, Amazon would object to this on the grounds that they’re a protected cloud provider, especially since they provide the cloud for the intelligence community, but Amazon has never shown much interest in its customers’ privacy.) That search process — this is the NSA after all! — would be automated and quite easy.
But until the NSA did that analysis — and perhaps for as long as 5 years, just as is the case with today’s phone dragnet — the money transfers records and pressure cooker searches of entirely innocent people would be in the government’s possession.
We don’t consider precisely these minimization procedures adequate for phone records. There’s nothing in the Leahy bill that would impose any more restrictive minimization procedures for whatever bulk(y) programs remain. Why would such procedures be inadequate for financial records if they’re not for phone records?
Stewart Baker believes Leahy’s freedom protects security
And if you don’t believe all that consider what Stewart Baker, pro-surveillance troll extraordinaire, has to say about the bill.
Sen. Leahy’s rewrite of “specific selection term” in USA Freedom bill is better for privacy and for security.
Remember, Baker’s concern during Intelligence Committee testimony was for all the non-phone record applications — the use of Section 215 to collect acetone and hydrogen peroxide records (first exposed here!). If his concerns have been addressed, I’d suggest this bill leaves current non-phone record programs largely intact.
All of which is to say that for phone records — but electronic communication service provider and cloud provider records only — the loophole identified by Pohlman probably will be closed by Leahy’s bill. The government can still likely collect phone records prospectively; but it requires a fairly specific selector.
But for the great variety of other Section 215 bulk programs — which may have numbered as many as 137 orders last year and 195 the year before — might be able to continue as is, potentially even with less restrictive minimization procedures.

Is it any wonder why the average American hasn’t got a clue what statutes really mean? In this example, the Senate OOD has gone to extraordinary lengths to euphumize, shift, distort and obfuscate doublespeak language of such depth that it takes emptywheel’s “in other words” numerous times to decipher the bullshit in this bill. Which is EXACTLY what these scumbags intended. To wit:
quote”The definition of Specific Selection Term “does not include a term that does not narrowly limit the scope of the tangible things … such as–… a term identifying an electronic communication service provider … when not used as part of a specific identifier … unless the provider is itself a subject of an authorized investigation for which the specific selection term is used as the basis of production.”
In other words, ….”
sheezusHchrist. “does not include a term that does not …”(snip) “when not used as part of …”
If that isn’t the living definition of doublespeak..I don’t know what the fuck is.
One thing is blindingly clear though. The US Congress isn’t about to “reign in” the NSA..in ANY WAY, SHAPE, OR GODDAMNED FORM. On the contrary, they’ve used the so called “debate” to strengthening their statutory authority while cutting the leash tethering the NSA to constitutional restraint and accountability. AND LEAHY KNOWS IT.
All I can say is fuck these shameless conniving bastards. They mock the Church committee..the Constitution..and the American people, all the while removing the last remaining shred of resistance to the free fall of the republic towards the bottom of the abyss of tyranny.
This morning, I came across a statement by the new Captain on the bridge of the USS NSA.
who ironically has the same name as the pond scum house ICom member..Mike Rogers:
quote”Among those beacons are efforts designed to win back the trust of those Americans who feel (rightly or wrongly) that NSA has gone too far in its signals intelligence collection efforts and specific programmatic initiatives to enhance NSA’s cyber workforce and partnerships with the private sector.”unquote
Win back the trust of America. right. Dear Admiral Rogers. Fuck you. Notwithstanding all three branches of our government, Clapper/Alexander/Fisc destroyed what ever trust the Church committee gave you in the first place. And now, you want it back. Too fucking bad.
ps..wait…wait ..MY BAD…correction via addendum.. add to list of criminal liars of the IC…
The first and foremost scumsucking, lying, conniving traitor in the history of this country…MICHAEL HAYDEN.. the architect of the CIA war criminal torture and Murder Inc Hellfire missile programs of death and destruction, notwithstanding using his credentials to thwart the Fourth Amendment by secretly implementing the most Orwellian surveillance state ever known on the planet, by holding the entire Congress at arms length through political connections to Bush/Cheney et al, to perpetrate the most illegal massive shift of taxpayer money into the Deep State plans to control the ENTIRE population of the USA.
Yes..THAT Michael Hayden.