If Patrick Leahy Wants to End Bulk Collection, He Needs to Amend His USA Freedom Act
The other day, the government obtained another Primary Order to collect all our phone records.
In response, Senator Patrick Leahy released this statement:
Congress must ensure that this is the last time the government requests and the court approves the bulk collection of Americans’ records. We can make this a reality in the Senate if we act swiftly to pass the bipartisan USA FREEDOM Act. Stakeholders from across the political and ideological spectrum have urged us for months to do just that. We cannot wait any longer, and we cannot defer action on this important issue until the next Congress. This announcement underscores, once again, that it is time for Congress to enact meaningful reforms to protect individual privacy.
I heartily agree with Leahy that the government has to stop obtaining authorization to collect Americans’ records in bulk.
But I think Leahy is misleading when he says we can “make this a reality” by passing USA FREEDOM Act — at least as currently written. While USA Freedom Act prohibits the government from collecting Americans’ phone records in bulk, it doesn’t prevent the government from collection Americans’ records from non-communications companies in what normal people would call bulk.
The language in the bill prohibiting the use of a company name as a selector only applies to electronic communication service providers.
(II) a term identifying an electronic communication service provider (as that term is defined in section 701) or a provider of remote computing service (as that term is defined in section 2711 of title 18, United States Code), when not used as part of a specific identifier as described in clause (i), unless the provider is itself a subject of an authorized investigation for which the specific selection term is used as the basis of production.
The limit of this language to communications companies makes it clear that the bill envisions the use of a corporate person (persons are permitted for traditional Section 215 orders) names — so long as they aren’t communications providers — as a selector. You can’t get all records from Verizon, as the government does, but you can get all one-side foreign records from Western Union, as the government also currently does.
In this case, the secret surveillance court has authorized the Federal Bureau of Investigation to work with the CIA to collect large amounts of data on international transactions, including those of Americans, as part of the agency’s terrorism investigations.
The data collected by the CIA doesn’t include any transactions that are solely domestic, and the majority of records collected are solely foreign, but they include those to and from the U.S., as well. In some cases, it does include data beyond basic financial records, such as U.S. Social Security numbers, which can be used to tie the financial activity to a specific person. That has raised concerns among some lawmakers who learned about the program this summer, according to officials briefed on the matter.
Former U.S. government officials familiar with the program said it has been useful in discovering terrorist relationships and financial patterns. If a CIA analyst searches the data and discovers possible suspicious terrorist activity in the U.S., the analyst provides that information to the FBI, a former official said.
[snip]
The data is obtained from companies in bulk, then placed in a dedicated database. Then, court-ordered rules are applied to “minimize,” or mask, the information about people in the U.S. unless that information is deemed to be of foreign-intelligence interest, a former U.S. official said.
Moreover, even if this is the only financial program that exists right now, the only limit on such programs would be the imagination of the Intelligence Community and the indulgence of the FISA Court. James Clapper and John Bates both objected to interpreting the transparency provisions of USAF to include similar applications to new targets. Particularly as the fearmongering surrounding ISIS increases, they’ll be ratcheting up the domestic spying again.
In any case, there is abundant reason to believe the government also collects the records of certain bomb precursors — fertilizer, acetone and hydrogen peroxide in large quantities, and pressure cookers — to cross-reference with suspect targets. And while the government collects flight information directly, there may well be bulk travel record collection as well.
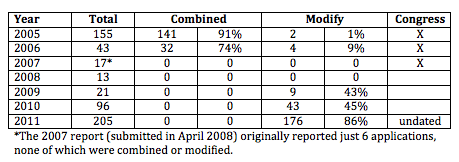
The bill enables this kind of bulk collection in its “transparency” provisions as well. Those provisions only conduct individualized counts for communications related orders under traditional Section 215, not for non-communications related orders.
(D) the total number of orders issued pursuant to applications made under section 501(b)(2)(B) and a good faith estimate of—
(i) the number of targets of such orders;
(ii) the number of individuals whose communications were collected pursuant to such orders; and
(iii) the number of individuals whose communications were collected pursuant to such orders who are reasonably believed to have been located in the United States at the time of collection;
This is obviously all by design (otherwise these two passages wouldn’t have this symmetry). And perhaps all it does is serve to hide this one (probably two, maybe three) programs. But again, there’s no guarantee that won’t change in the future, and the transparency provisions don’t do enough to ensure this would be properly briefed.
Of course the fix for this would be easy: extend the same prohibition against using a corporate person as a selector to all corporate persons, and extend the individualized reporting under traditional Section 215 to all Section 215 orders.
If Senator Leahy wants to prevent bulk collection, he needs to treat tangible things — the name of the provision at hand!!! — of all sorts, communications and non-communications — as the bill currently treats just communications-related orders.