Boeing 737 MAX 9: The Comment Heard Around The World
[NB: check the byline, thanks. /~Rayne]
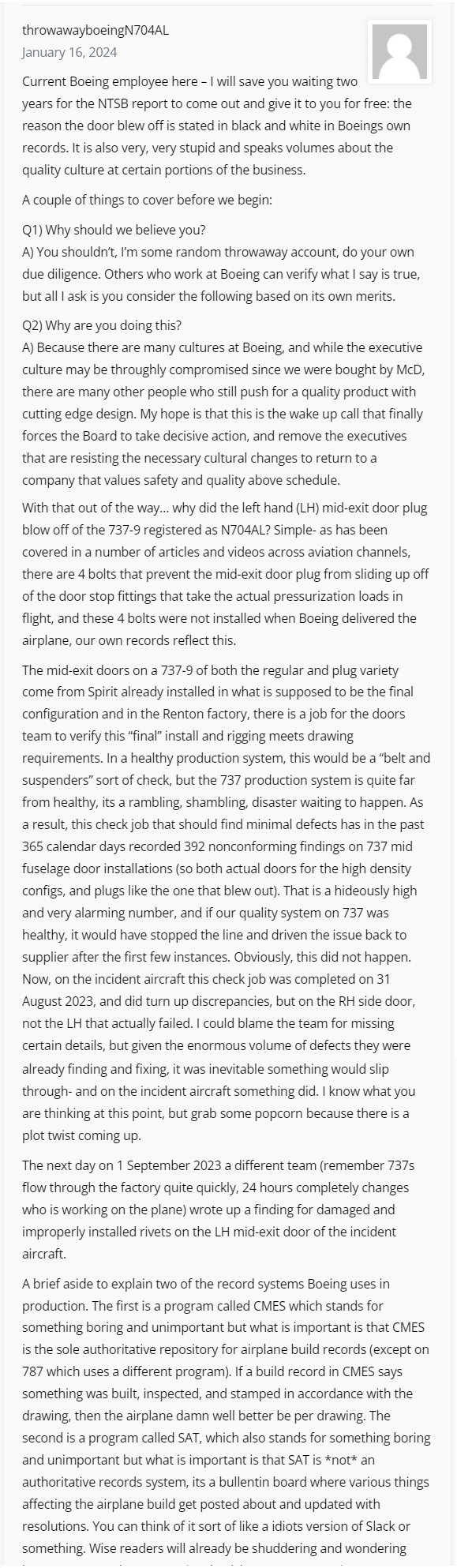
If I had any doubts this last week whether I should post about Boeing’s quality problems, a comment posted in Leeham News on January 16 convinced me the topic needs more attention. I had goosebumps several times as I read it.
Kudos to Leeham News for maintaining a comment section; it’s not easy but it’s clearly needed.
I’m not screenshotting the entire comment, only enough to convince you this is something worth reading and understanding amid a sea of layoffs and a surge of AI implementation across nearly every industry. Imagine as you read it how this could be made worse by fewer well-educated personnel and less communication between humans.
Before you scroll further, read the article which spawned the comment:
“Unplanned” removal, installation inspection procedure at Boeing
https://leehamnews.com/2024/01/15/unplanned-removal-installation-inspection-procedure-at-boeing
This story was published ten days after Alaska Air’s flight 1282 departed Portland OR’s PDX airport for California only to lose a door minutes later. The Boeing 737 MAX 9 safely returned to PDX roughly 20 minutes after takeoff.
The original comment both parts 1 and 2 can be found directly below the article — use keyword “throwawayboeing” to find them using Ctrl-F in your browser as many more comments have appeared since the article was first published.
If Leeham News should crash from high traffic volume or a possible attack, you can find parts 1 and 2 along with the article at the Internet Archive (keep in mind the earliest archived versions of the article may not have the comments beneath them):
https://web.archive.org/web/20240122193511/https://leehamnews.com/2024/01/15/unplanned-removal-installation-inspection-procedure-at-boeing/
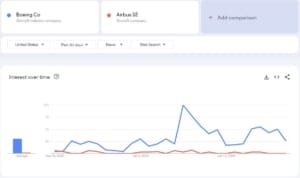
An observer in my social media feed whose name I didn’t record noted that every little problem Boeing planes experience is now news. United Airlines discovering loose bolts on Boeing 737 aircraft reported only days after the Alaska Air door failure would and should have made the news; Alaska Air has also found more problems with bolts since then.
Google Trends suggests there’s some truth to the claim every Boeing problem is now news:
How many of the increased mentions are well-deserved snark is hard to say:
Well-deserved if dark. So dark. Mentions of new resources like Is My Plane A 737 MAX may also magnify Boeing’s problems in the media, but if there wasn’t a safety problem tools like this wouldn’t be seen as necessary.
Commerce Committee chair Maria Cantwell (D-WA), Subcommittee on International Trade, Customs, and Global Competitiveness member Mark Warner (D-VA), and Commerce Committee ranking member Ted Cruz (R-TX) are scheduled to meet today with Boeing’s CEO Dave Calhoun about the aerospace manufacturer’s ongoing quality crisis.
Calhoun already met last week with the heads of the Federal Aviation Administration (FAA) and National Transportation Safety Board (NTSB). Seems rather late after the crazy stones Boeing manifested by asking on January 5 for its 737 MAX 7 to be exempted from safety rules to allow the aircraft to fly.
Let’s hope the FAA and NTSB are focused on the quality problems at Boeing and not on the source of the comment above until the comment’s veracity is called into question. The First Amendment should protect just this kind of speech from corporate suppression given the absolute risk all passengers take when boarding a Boeing aircraft.
You’ll note the image used on the front page for this post is a Boeing 737 — but it’s a military craft. Boeing is a federal contractor. If workers can’t safely blow the whistle on manufacturing quality problems with aircraft our defense personnel and our elected officials rely on, purchased with our taxpayer dollars, what good is the First Amendment?
~ ~ ~
What all of this has to do with labor is fairly clear in the original article published in Leeham News. I can’t add more to what’s been written.
But all of this could be worse in time depending on how Boeing addresses solutions in concert with cost controls.
One thing the public should know more about is the impact AI will have in manufacturing environments, especially ones in which both adherence to specifications and safety are tightly linked.
Four days after the Alaska Air Boeing 737 Max 9 lost its door mid-air, there was a report about a vulnerability found in Bosch brand cordless, handheld pneumatic torque wrenches which are used in the automotive industry. The wrenches are programmed to ensure nuts are tightened to specification and operate using Wi-Fi.
What are the chances that similar vulnerabilities may exist or be introduced into aerospace manufacturing, compounded by the increasing amounts of AI used in automation?
Let’s say a certain aerospace manufacturer gets its shit together and fixes its corporate culture and procedures so that all parts are tracked and all actions and omissions are likewise accounted for and documented as it builds aircraft.
What could happen if the no-longer-missing bolts are over- or under-tightened because of a vulnerability like the one in Bosch’s Rexroth’s NXA015S-36V-B wrenches?
It’s not enough to analyze and remedy existing quality and safety problems; future problems must be anticipated at the same time.
~ ~ ~
Since I began drafting this post this morning, The Seattle Times has reported on Boeing’s door problem, mentioning the comment left at Leeham News. You’ll want to follow up with this story as aerospace manufacturing is journalist Dominic Gates beat; he’s covered other similar stories like the ongoing Boeing 737 challenge.
In fact, if you read the comments at Leeham News you’ll see Gates as well.
Yet another example of why well-moderated news sites’ comments can be important.
This is NOT an open post. Please stay on topic in comments.


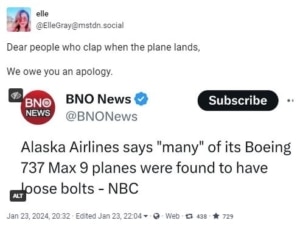
![[image via bazbizSF via Flickr]](https://www.emptywheel.net/wp-content/uploads/2016/01/NewYearsResolutionCoaster_BazaarBizarreSF-Flickr.jpg)
![[graphic: Live radar from 15-AUG-2015, via @FlightRadar24]](https://www.emptywheel.net/wp-content/uploads/2015/08/Flightradar24_Flights_15AUG2015-300x209.jpg)