NSA Continued Double Dipping at SWIFT Even After It Was Exposed
One of the most contentious Snowden revelations — first reported on September 8, 2013 by Globo and then repeated a week later by Der Spiegel — was that NSA’s Tailored Operations group was hacking SWIFT, the international financial transfer messaging system. It was contentious because when the servers moved to Europe, the US and EU negotiated access for the US, access with protections for Europeans that happened to be oversold.
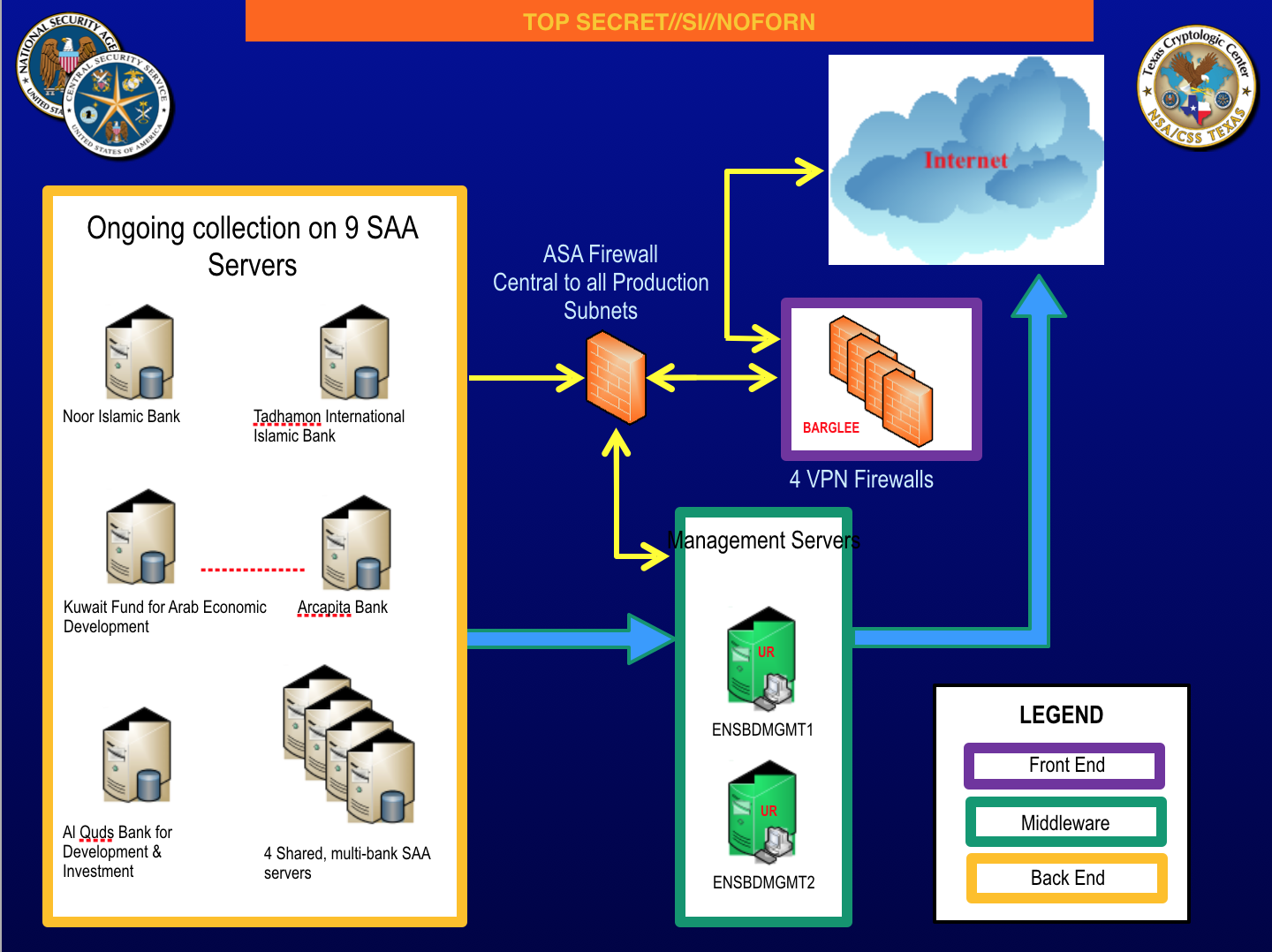
Shadowbrokers just released its second set of NSA files in a week. This set includes far more interesting documents than the batch released last week. Most significantly, it includes details on NSA’s thorough pawning of SWIFT. Whereas the SWIFT files from Snowden, which were never released publicly, seemed to date from 2011, the most recent files released today, including one dated October 17, 2013, appear to date to a month after the first public Snowden reports that NSA had targeted SWIFT. In addition, it includes files showing NSA targeting a SWIFT EastNets engineer in Belgium.
A number of people have been arguing that the mostly Middle Eastern financial institutions that seem to be the focus here — things like the Al Quds Bank for Development and Investment — are legitimate intelligence targets. And they are, within the framework of NSA’s spying in the US. But that ignores that the US had an agreement in place about what legitimate targets were (which, according to MEPs who tried to oversee the agreement, were violated anyway). Also, a number of our Arab allies may not be too happy to see their own banks targeted.
Both last week’s release and this week’s cite Trump’s suddenly volatile foreign policy. “Maybe if all suviving WWIII theshadowbrokers be seeing you next week.” By releasing files that remind Europe that the US continued to flout multilateral negotiations, SB may be trying to make continued adventures more difficult for Trump.
Update: Security researcher Matt Suiche did a more detailed post on how much this release endangers SWIFT.
Update: Shadow Brokers has long made a show of asking for Bitcoin for all this. But these SWIFT files alone (to say nothing of what appear to be multiple Windows 0days in this release) would have been at least as valuable.
Even more interesting, remember that the US threatened to kick Russia out of SWIFT in 2014, which led Russia to build a redundant system in case it were ejected from the cooperative. Even the Trump Administration has floated making sanctions more stringent. If Russia ever were targeted in such a way, it seems these files would be invaluable. And yet they got leaked, for free. To my mind that’s one of the best pieces of evidence yet that Shadow Brokers is not Russian.
Update: EastNets, the primary target in the SWIFT files, issued this statement:
No credibility to the online claim of a compromise of EastNets customer information on its SWIFT service bureau
The reports of an alleged hacker-compromised EastNets Service Bureau (ENSB) network is totally false and unfounded. The EastNets Network internal Security Unit has run a complete check of its servers and found no hacker compromise or any vulnerabilities.The EastNets Service Bureau runs on a separate secure network that cannot be accessed over the public networks. The photos shown on twitter, claiming compromised information, is about pages that are outdated and obsolete, generated on a low-level internal server that is retired since 2013.“While we cannot ascertain the information that has been published, we can confirm that no EastNets customer data has been compromised in any way, EastNets continues to guarantee the complete safety and security of its customer’s data with the highest levels of protection from its SWIFT certified Service bureau”Hazem Mulhim, CEO and founder EastNets.



Hi Marcey,
It wasn’t a SWIFT engineer, it was EastNets, who offer an umbrella service for some banks to access SWIFT. Matt Suiche hints that it is significant that they are in Belgium and the SWIFT HQ is in Belgium, but SWIFT Belgium is development and admin, nobody in Belgium has access to the network. The developers have to travel to an ops centre and even then they don’t get anywhere near the servers as they have to work through in-house operators. This is the equivalent of a bank being hacked, except this time it’s all the banks that use EastNets.
Well, for two decades now, I have been saying that Windows is insecure by design. And as usual, most exploits seek that easier target. And as some will attempt to argue, ‘well, there are more attacks on Windows than other platforms because there are more Windows machines on the net. Doh!’
And therein lies most of the problem.
For something like SWIFT, there is *NO* reason it should have to run on Windows.
The functionality can be done on Linux.
Matt Suiche:
“Unfortunately, as long as companies would not really understand the technical origins of cyber security issues — or worse deny them — those issues will still exist and potentially put critical nation infrastructure at risks.”
http://fortune.com/2016/09/26/swift-hack/
Might have been the cia getting a little lunch money for a project?
Yes sounds safe to me. Amerika want the Russian out of swift but with billions in fees at stake swift added a Russian & China central banker to the board. Poked Amerika in the eye for sure.
The Russian system is up and running and is tied to China and other major trading partners making harder for nsa and cia to watch what going, on poor babies.
“when you come to a fork in the road, take it.” – Yogi Berra
Lots of people are now at that fork, and have stopped. Wondering which way to go. Perhaps the wear on the lanes at the fork indicate the most travelled path, so they pick that assumming that the majority was probably right, and safety in numbers. Perhaps on their cell phone, asking someone else for advice. Perhaps thinking that maybe they should turn around a go back to somewhere else. Perhaps they can really admit to themselves that they are truly lost.
This is the situation today with regard to staying on the Microsoft road.
Many over the years have come to this fork, but continued down the Microsoft road. They took the wrong fork.
They were not really on a road that led to somewhere that they wanted to get to. They where really in a maze of Microsoft roads, that lead to each other. The only forks were actually upgrade roads, but they are all toll roads and the driver still remains in a twisty maze of passageways, all different.
Which leads me to how this is on topic.
All of the dumps recently are heavy on exploits that target the Microsoft platform. Most are older exploits, but we are seeing more recent stuff, albeit not super recent. But the trend is clear, and there likely numerous zerodays for Windows10. They just are not public. YET.
And we know lots of companies and governments that are stuck with Microsoft because of lockin and legacy applications that can not be easily converted to open standards.
They are stuck at the fork. They can not turn around and go back.
But because of these exploits now visible to the public, there have to be millions and millions of IT people, that now realize that there are at the proverbial fork in the road.
What would be desirable from a pure security perspective is more platform diversity. More taking the good fork even if it appears less traveled, or ignoring who they called on their cellphone to ask for direction (consultant).
We need more of:
“Nobody goes there nowadays, it’s too crowded”. – Yogi Berra
The majority is not always right, and there is no safety in numbers when it comes to platform. At this point, being in the Microsoft crowd is actually a negative. In fact, it may be fatal to not leave the Microsoft ‘Vending Machine maze’. Also, with these exploits becoming public, companies will be under heavy pressure from shareholders worried about risk.
Ironically, the exploits now being public, may actually result in many IT people being too scared to take the fork in road, and instead will spend major money on the upgrade road. But it is a toll road (license fees).
I believe we are at a seminal event in the history of IT, and therefore the future of the planet.
Will enough people take the fork in the road?
Or will too many stick to the easier exploitable platform and continue to pay the tolls?
“You can observe a lot by just watching” – Yogi Berra
Love the Yogi Bera quotes!
Seems like this tweet is under burial attack:
Retweet by @x0rz, originally by @GossiTheDog
Guys your network diagrams and SWIFT Alliance passwords are in the dump, you might want to look into it. (link: https://twitter.com/EastNets/status/852912656130244608) twitter.com/EastNets/statu…