Today in the Ben Wittes (And Friends) Utter Lack of Self-Awareness File: Family and Friends Edition
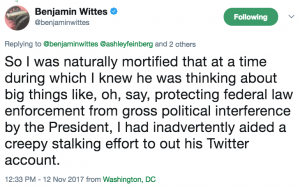
This morning, Ben Wittes called Ashley Feinberg’s discovery of the Twitter account that Jim Comey had himself disclosed the existence of publicly, “a creepy stalking effort.”
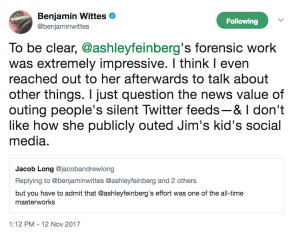
Shortly thereafter he went on to backtrack a bit, calling Feinberg’s work “very impressive,” but then pitching his privacy concern as pertaining to Comey’s adult-aged son.
Later in the day he defended against claims he was “being mean” to her by pointing to the time she used his name to get Comey to click on a test phish.
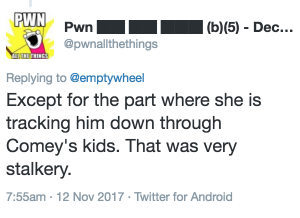
Then Matt Tait weighed in, reaffirming that tracking Comey down through his adult-aged son was very stalkery.
Ultimately, though, they (and Susan Hennessey) end up asking what the news value of Feinberg identifying Comey’s Twitter account was.
Let’s review, shall we? We’re talking about whether it is acceptable for a journalist to use public means (facilitated by a loophole in Instagram), hopping through a public figure’s 22-year old son, to find the public figure’s Twitter account, which he revealed in a televised appearance.
And not just any public figure. This is Jim Comey, the man who, in 2004, declined to reauthorize a bulk Internet metadata dragnet (Comey showed no such compunction about reauthorizing a phone metadata dragnet), only to run to the FISA Court and tell Colleen Collar-Kotelly that she had no discretion but to approve it.
And thus was born the legal codification of the definition of “relevant to” that holds that the metadata of all Americans can be considered “relevant to” FBI’s standing terrorism investigations, the definition that, two years later, would be used to justify collection aspiring to obtain the metadata of all phone calls placed in this country. Not just those who talk to terrorists, but those who talk to the people who talk to them and the people who talk to those who talk to those who talk to them. Including their children.
The Internet dragnet (and the upstream collection that replaced it) collects things like what people get tagged or favorited in Instagram and Twitter accounts — precisely the kind of metadata that led Feinberg to identify Comey’s account.
But that’s not all that’s “relevant to” whether there is any news value to using publicly available metadata to identify a Twitter account that Comey himself revealed.
In 2014, when Jim Comey headed the FBI, DOJ’s Inspector General argued for at least the second time (with the first including practices that occurred while Comey was DAG) that FBI should not be obtaining all records associated with the Friends and Family account of a target.
[T]he significance of the FBI’s request for “associated” records is that the FBI has sought and in some cases received not only the toll billing records and subscriber information of the specific telephone number identified in the NSL, but also the toll billing numbers that belong to the same account — such as numbers in a group or family plan account — without a separate determination and certification by the FBI that the additional records are relevant to an authorized international terrorism investigation. Yet before the FBI may specifically request in an NSL the records of a subject’s family member or partner, Section 2709 would require an authorized official to certify that such records are relevant to a national security investigation. (158)
That is, DOJ’s IG had to tell the FBI for the second time, when Comey was running it, that they shouldn’t be collecting the phone records of a target’s mom or (dependent aged) child or girlfriend because they were associated with accounts relevant to an investigation.
The FBI accepted DOJ IG’s recommendation to ensure that records “associated to” those “relevant to” investigations not be collected, but had only implemented it thus far on the non-automated side of NSL submissions by the time of the report.
Now that we’ve reviewed Jim Comey’s great tolerance for using three hop metadata records as an investigative technique (if not the more targeted collection of records “associated to” those “relevant to” investigations) as well as the mind-numbing definition of what constitutes “relevant to,” let’s return to the context of his discussions about social media. While the Twitter revelation served as evidence for a story that he’s non-partisan, the Instagram one he likes to tell serves to support his claim to care about privacy. Here’s the quote Feinberg included in her piece, but Comey has made this speechlet numerous times over the years.
I care deeply about privacy, treasure it. I have an Instagram account with nine followers. Nobody is getting in. They’re all immediate relatives and one daughter’s serious boyfriend. I let them in because they’re serious enough. I don’t want anybody looking at my photos. I treasure my privacy and security on the internet.
Nobody is getting into his Instagram account (with its loophole permitting people like Feinberg or FBI agents to get to his metadata), Comey said. With respect to content, that seems to be true.
Presumably, he also believed nobody was getting into his Twitter account that at that point just one person — the weak link, Ben Wittes — had followed.
He was wrong.
Jim Comey’s understanding of his own well guarded privacy was overblown, in part because of the inherent insecurity of the platforms he uses and in part because of the OpSec practices of his friend and his son’s friend. I don’t think Comey much cares — in his business, the likelihood that a dumb associate might thwart otherwise admirable operational security (especially on the part of a 22-year old) of a target is a blessing, not a curse.
But it is an awesome illustration of the power and danger of this metadata soup that, under Comey, the government got far more access to.
Now, in threads where I’ve made this argument, people have rightly pointed out that the power of the FBI (which gets far more metadata) and a reporter is somewhat different, as might be the necessity for avoiding any chains involving children. Though the frequency with which Trump and his associates’ own (admittedly older) spawn get included in stories of his corruption demonstrates how important such connections are, even for journalists.
But the contention that FBI’s contact chaining and a journalist’s contact chaining are that different is belied by Comey’s own reaction, his first tweet ever.
Not only did he say he wasn’t mad and compliment her work, but he posted the link to FBI jobs.
I’d say Jim Comey sees a similarity in what Feinberg did.
I’m all in favor of protecting the accounts of children from such contact chaining — and am really not a big fan of contact chaining, generally. But those who, like Comey and Wittes and Hennessey and Tait, have championed a system that endorses at least two hop chaining irrespective of who gets hopped, not to mention those who’ve tolerated the collection on family members in even more targeted surveillance, I’m not all that interested in complaints about the privacy of a 22-year old son.
Or rather, I point to it as yet another example of surveillance boosters not understanding what the policies they embrace actually look like in practice.
Which is precisely why this “doxing” was so newsworthy.
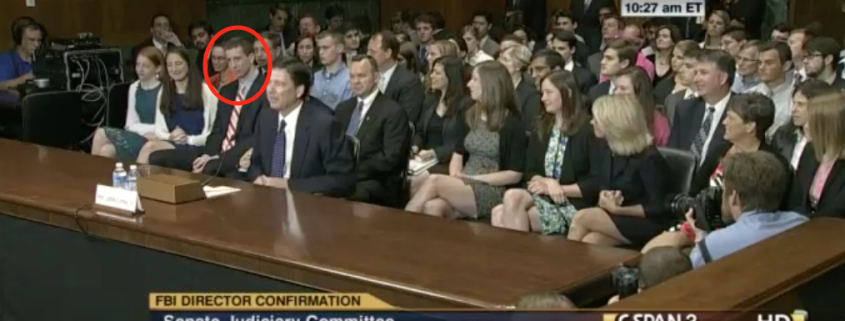
Update: For the benefit of Al, I’m including this link to Comey introducing his children (Brian was 19 at the time, his youngest was 13) at his FBI Director confirmation hearing in 2013; a screencap is above. It sounds like he did the same at his DAG hearing 10 years earlier.
So if you’ve got a concern about their safety you might want to talk to the Senate about the practice of featuring families during confirmation hearings.
Update: Here we are Monday and Gates and Manafort still haven’t found anything liquid to put up as bail. Not only that, but in a filing raising a potential conflict with one of Gates’ money laundering expert lawyers, prosecutors reveal Gates is trying to have his partner from a movie-related firm’s brother serve as surety while also doing so for the partner.
Marc Brown, the brother of defendant Steven Brown, was proposed by Gates as a potential surety despite the facts that they seemingly do not have a significant relationship, they have not had regular contact over the past ten years, and Marc Brown currently serves as a surety for his brother Steven in his ongoing criminal prosecution in New York. In an interview with the Special Counsel’s Office on November 16, Marc Brown listed as a reason for seeking to support Gates that they belonged to the same fraternity (although they did not attend the same college) and that, as such, he felt duty bound to help Gates. Of note, Marc Brown’s financial assets were significantly lower, almost by half, than previously represented by Gates.





Moreover, Comey seems to have been nowhere near as bugged as ?
But, Comey bit on a phish
https://www.gizmodo.com/heres-how-easy-it-is-to-get-trump-officials-to-click-on-1794963635/
It is a tad hard to get past the issue that a journalist failed to note that the subject of her investigation had himself publicly revealed what she purports to reveal. In that regard, her “news” would not appear to be news at all. That factual background is something Wittes himself should have been aware of if he intended to make a public stink about it. Both would appear to be guilty of negligent “journalism”.
That said, you point out a delicious irony: some of the staunchest supporters of government surveillance seem to think they and their peers are immune to its scope.
I wonder what Mr. Wittes would say about the scope of private information sharing – setting aside for now its collection – through such venues as Equifax’s Work Number. Some “50,000” corporate and public sector employers share the most intimate information about your employment history and financial circumstances with Equifax. It is pooled with other aggregated information, all of which is far more detailed than most employees would imagine, let alone approve of.
The latter isn’t relevant to this many billions a year shadow industry, because humans and information about them are its products; there is no customer or contractual arrangement with them. The only customers are other businesses, whose primary concern is to do whatever is most profitable.
So, naturally, American corporations have successfully lobbied their government and essentially prohibited it from implementing European-style digital rights laws that would protect their citizens personal information. Common in Europe and many countries elsewhere, those laws give people the right to know what information about them is collected, by whom, for how long, and for what purposes. It allows them access to such information, to verify its accuracy and to correct inaccuracies. They require that the information be stored and processed according to high standards of physical and virtual security.
In the US, Equifax can, for example, lose copies of its data files on 145 million people, while only having to suffer through formal apologies, the loss of a few marginal executives, and implementation of inadequate improvements to the way it physically and virtually secures the information it claims to have exclusive rights over. It even makes its half-ass attempt at a cure an opportunity to profit from its uninformed human products. And that’s all without shining a light on its business model or practices. You’d think it was a Wall Street bank.
Very interesting. I saw the twitter spat between you and Susan H, and I wasn’t sure what to think. This was very informative.
Remember that the VPPA law that protects the privacy of video rental records was in response to a Supre Court nominee’s prurient habits being exposed.
That’s incorrect. It was in response to Bork’s entirely pedestrian records being exposed. You’re thinking of Clarence Thomas, whose (alleged) viewing habits became a confirmation hearing issue, but not because they were revealed by a rental establishment.
https://epic.org/privacy/vppa/
It is an “all your clicks be ours” world. Hear tell that anyone can buy ultimately identifiable information web history from CA, google/Yandex, facebucks, twitterFSB and and now your very own ISP provider. As SLF says “cause cookies”. And to add just about every link posted here probably has at least passive honeypot capability. And what document/data type does not have phone home capability?
CWA, two failure to launch Americans and 3 British very young teenagers managed to hack both Brennan and Clapper and pass stuff on to Assange.
Point being, Comey, his son and everyone else knows or should know their history has been bought by the press, the political operatives, the corporate big data folk and a number of foreign actors.
For context, it’s not just anyone’s son, it’s the son of a law enforcement officer who has throughout his career put some powerfully dangerous and unsavory people away. There is very solid justification for not publishing the identity of families of prosecuting officers and judges.
In the Philippines, absolutely, although the risk there is that it is the government’s dislike of a judge’s opinion that would put her family in jeopardy, and the gubmint already knows who they are.
Mr. Comey has been a public figure for so long, information about his family has long been in the public domain. You might also consider how much startlingly intimate information is available on the Internet to any business – legitimate or not – that has a computer and a credit card. The information “disclosed” here adds no exposure that wasn’t already there.
As I will note above, in both his DAG and FBI Director confirmation hearings, he introduced his children (only 3 were over 18 for the latest one). If the criminals want to find his kids, that’s where they’ll turn to first.
The NOLA U.S. Attorney’s office had 5 murder convictions thrown out (which happened to be 5 NOLA police who killed 2 unarmed people post-Katrina) because a prosecutor and senior aide had posting about the case under pseudonyms in blog comments and under newspaper articles. A lot of people with fancy titles and positions need to grow up about what is and is not public. Pro tip: The social in social media means the public can see you.