In Support of Ben Wittes
Over at Lawfare, Ben Wittes does some brainstorming about what other databases the Chinese may be hacking after ingesting all its OPM winnings. He thinks they might target:
- FDA New Drug Applications
- VA patient records
- Visa applications (State Department)
- Export control applications (Commerce)
- SEC investigative files
For each description of why he thinks they might be juicy targets, he ends with this statement:
Fortunately, the [XXX] Department is a highly competent counterintelligence agency with first-rate cybersecurity expertise, whose employees are scrupulous about cybersecurity and never do business on their own email servers. I am sure it is fully competent to protect these records.
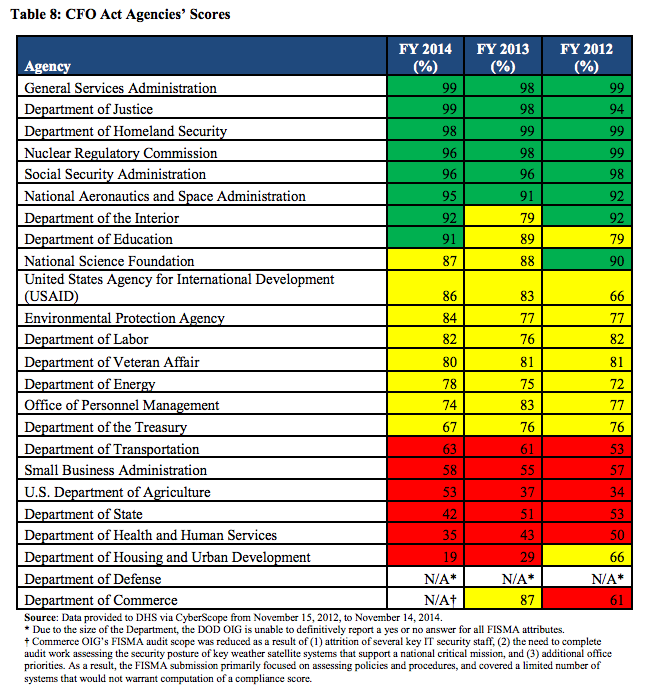
As it happens, there’s plenty of support for most of Wittes’ speculative targets, especially if you consult this year’s FISMA report from OMB.
Several of the agencies — especially the State Department, but also especially Commerce — rated very poorly in OMB’s summary of the Inspector Generals reviews from last year.
I’d add two agencies to Wittes’ list: USDA (China has allegedly been stealing seed corn, so why not Ag records?) and Treasury generally (though in some other areas Treasury is pretty good, and it has mostly been “hacked” via old style means — including PII “spillage” — of late).
This list is particularly notable, however, given that the debate over CISA is about to start again. Both Treasury and Commerce are among the agencies that get automatic updates of the data turned over under the law. But their security is, in some ways, even worse than OPM’s.
Update: Paul Rosenzweig takes a shot. He picks CFIUS, NRC, FERC, state license DBs, and university research. There is some correlation with weak agencies there, too.


Why should the Chinese have to choose, when they can have them all?
Pretty soon, we’ll face up to having to do things on paper again.
I still have two typewriters here.
.
Ain’t analog great?
Insider traders’ files, to make the big bucks first without anyone knowing it. Mafia dons’ files, so the Chinese mob can take over an ongoing source of tribute. Maps showing municipal water system intake pipe locations, so we can be dosed with Communist fluoride against our will. Bill Belichick’s brain, to end up with twice-stolen information. And perhaps most valuable of all, that super double secret file in E! that contains the answer to the question, “Why do people watch the Kardashians?”
A couple years back I read a brilliant article (New Yorker?) about the huge amount of effort it took for a team of super-bright civilian computer geeks to fix the Obamacare website after the government had run it into the ground. I shudder to think what it would take to bulletproof the US’s databases.
Mr. President. The pilot has lost control of Air Force One.
Not a problem; our government is basically a driverless vehicle anyway.
At the risk of sounding like a Cassandra why should we assume that they are waiting? Given that the OPM hack happened some unspecified time ago we have no reason to believe that they have been idle since then and attacking sooner before people are on notice would be sound tactics.
You’re starting from a non-established fact and moving outward. I expect better from you, Marcy. To wit, you’re assuming China did this. Why?