Department of Energy: CyberSprinting Backwards
Earlier this week, I noted that of the seven agencies that would automatically get cybersecurity data shared under the Cyber Information Sharing Act, several had similar or even worse cyberpreparedness than the Office of Personnel Management, from which China stole entire databases of information on our cleared personnel.
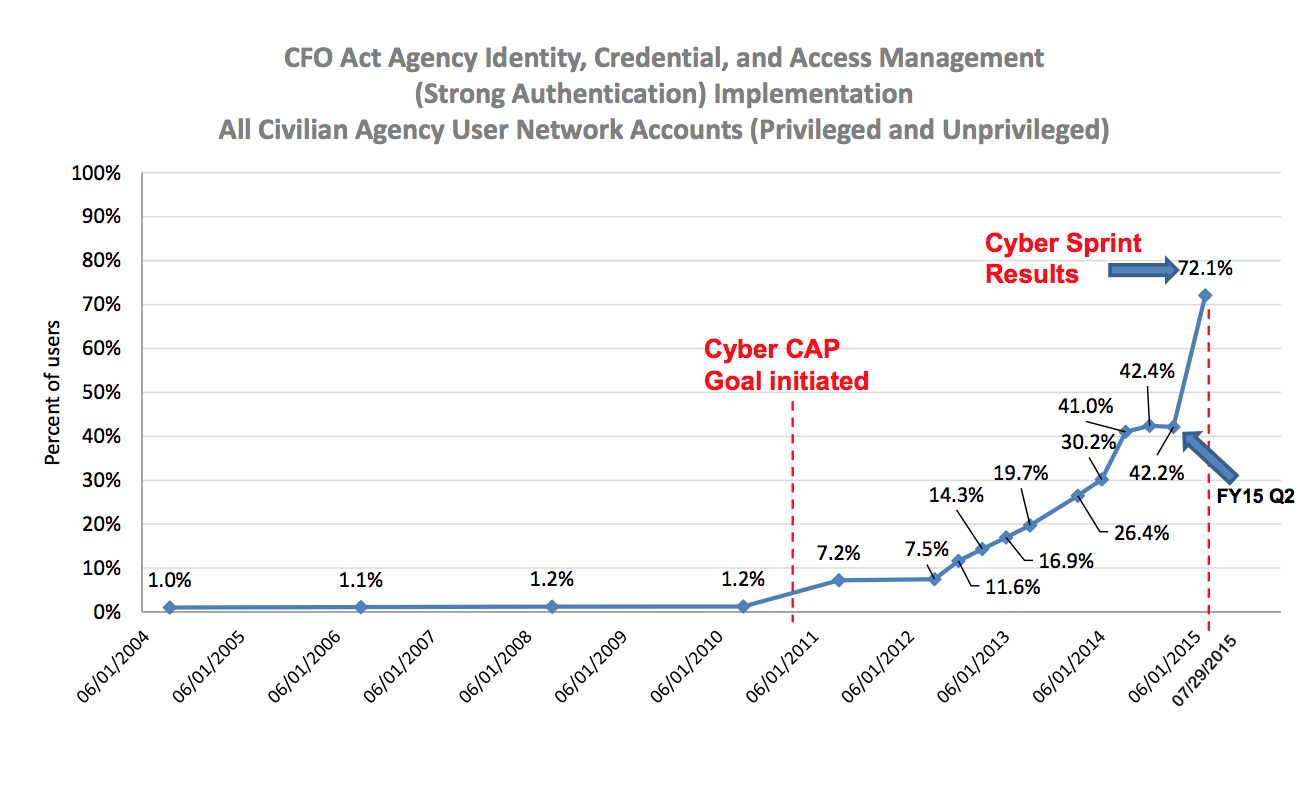
To make that argument, I used data from the FISMA report released in February. Since then — or rather, since the revelation of the OPM hack — the Administration has been pushing a “30 day sprint” to try to close the gaping holes in our security.
Yesterday, the government’s Chief Information Officer, Tony Scott, released a blog post and the actual results, bragging about significant improvement.
And there have been significant results (though note, the 30 day sprint turned into a 60 day middle distance run), particularly from OPM, Interior (which hosted OPM’s databases), and — two of those CISA data sharing agencies — DHS and Treasury.
Whoa! Check out that spike! Congratulations to those who worked hard to make this improvement.
But when you look at the underlying data, things aren’t so rosy.
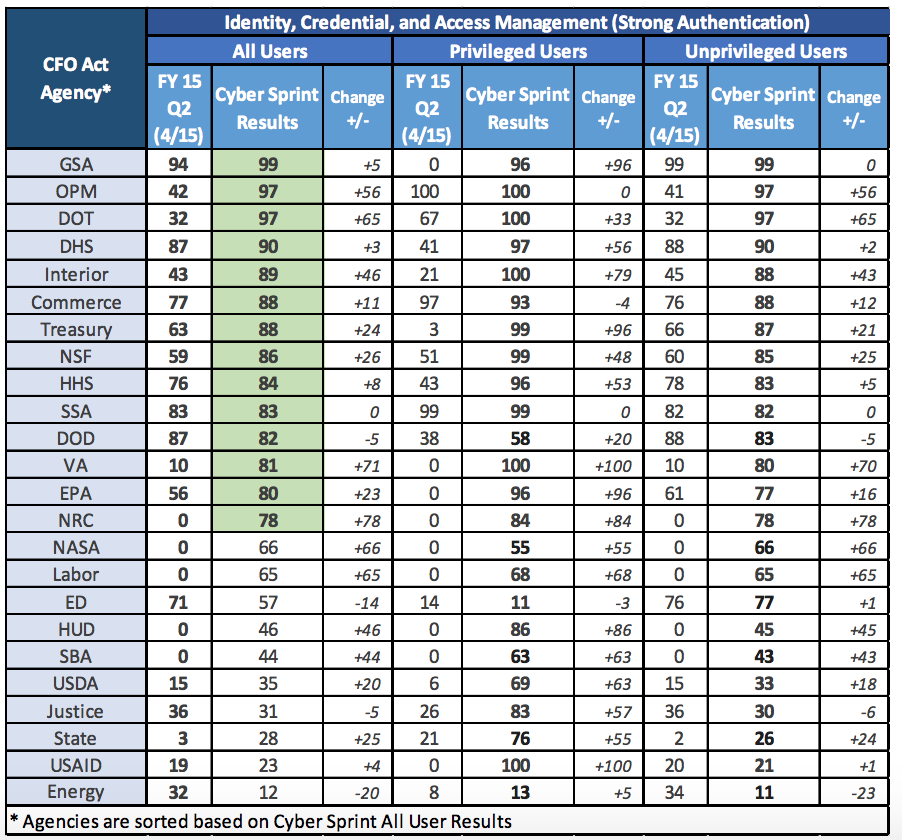
We are apparently supposed to be thrilled that DOD now requires strong authentication for 58% of its privileged users (people like Edward Snowden), up 20% from the earlier 38%. Far more of DOD’s unprivileged users (people like Chelsea Manning?) — 83% — are required to use strong authentication, but that number declined from a previous 88%.
More remarkable, however, is that during a 30 day 60 day sprint to plug major holes, the Department of Energy also backslid, with strong authentication going from 34% to 11%. Admittedly, more of DoE’s privileged users must use strong authentication, but only 13% total.
DOJ (at least FBI and probably through them other parts of DOJ will receive this CISA information), too, backslid overall, though with a huge improvement for privileged users. And Commerce (another CISA recipient agency) also had a small regression for privileged users.
There may be explanations for this, such as that someone is being moved from a less effective two-factor program to a better one.
But it does trouble me that an agency as central to our national security as Department of Energy is regressing even during a period of concerted focus.


quote”But it does trouble me that an agency as central to our national security as Department of Energy is regressing even during a period of concerted focus.”unquote
Their 1985 fax machine was running out of ink when DOE received the memo.
Where it was supposed to print “30 day sprint”, it printed “3 day print”. The operator wasn’t about to spend 3 days waiting for a fax.
any rapid change (up or down) in any federal agency’s numbers about anything almost certainly have to do with changes in “accounting” rules.
whatever consequential changes – in both rules and human behavior – promoting greater security have actually occurred to date will require time and more sophisticated data.
but this is useful information to have to begin to keep an eye on improving govt security.