James Comer’s Dick Pics Hearing Just Became an Alleged Stolen Laptop Hearing
As I have repeatedly pointed out, the first thing that James Comer chose to do after becoming Chair of the House Oversight Committee was to schedule a hearing about why he can’t look at non-consensually posted pictures of Hunter Biden’s dick on Twitter.
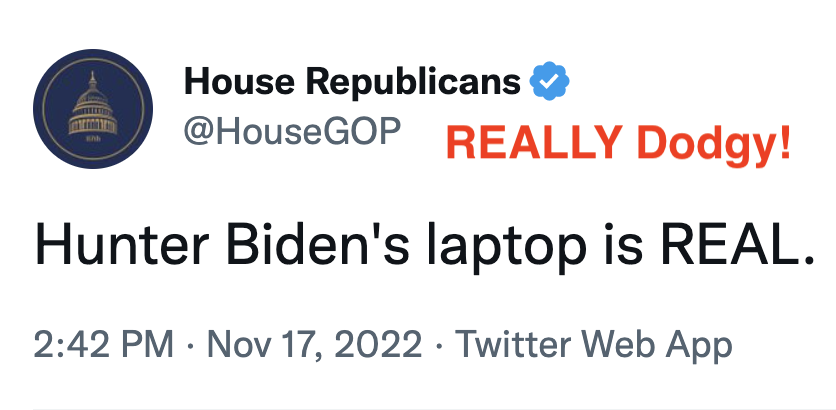
In letters asking former Twitter executives Jim Baker, Yoel Roth, and Vijaya Gadde to testify next week, Comer described the substance of the hearing to be about their, “role in suppressing Americans’ access to information about the Biden family on Twitter shortly before the 2020 election.” As Matt #MattyDickPics Taibbi has helpfully revealed, some of the “information about the Biden family” that Twitter suppressed Americans’ access to before the election were nonconsensual dick pics, including a number posted as part of a campaign led by Steve Bannon’s buddy Guo Wengui.
Certainly, the Twitter witnesses, who themselves have been dangerously harassed as the result of #MattyDickPics’ sloppy propaganda, would be within the scope of Comer’s stated inquiry to explain why a private company doesn’t want to be part of an organized revenge porn campaign, even if a Congressman from Kentucky wants to see those dick pics.
But Comer’s campaign also just became about something else: Twitter’s decision to suppress a story based off a laptop that its purported owner claims was unlawfully obtained.
As several outlets have reported (WaPo, CNN, NBC, ABC), Hunter Biden has hired Abbe Lowell, who has written letters to DOJ, Delaware authorities, and the IRS, asking for investigations into those who have disseminated the materials from the alleged laptop (though Lowell made clear that no one is confirming any of the versions of the laptop). Those included in the letters are:
- John Paul Mac Isaac (whom a prior lawyer, Chris Clark, had already referred to SDNY)
- Robert Costello, who first obtained the laptop from Mac Isaac
- Rudy Giuliani
- Steve Bannon
- Garrett Ziegler (who plays a key role in the January 6 investigation but who now hosts the content as part of a non-profit)
- Jack Maxey (who provided the “laptop” to multiple outlets)
- Yaacov Apelbaum (whom Mac Isaac claimed had helped to create a “forensic” image of the laptop)
The lawyers also sent a defamation letter to Tucker Carlson for a story since proven to be false.
These letters aren’t likely to change what DOJ, at least, will do about the laptop. They’ve had the Mac Isaac copy in hand for some time, and the earlier SDNY referral would likely go to the same people already investigating the theft of Ashley Biden’s diary.
Ziegler may be an exception. DOJ likely already has interest for his role in January 6, the invitation to conduct an investigation may give reason to look more closely.
Eric Herschmann is not, according to reports, on these letters but he was even pitching “laptop” content while working at the White House.
But the public coverage of this will undoubtedly change the tenor of next week’s hearing. At the very least, it will validate Yoel Roth’s concerns in real time that the NYPost story was based on stolen data. It will, retroactively, mean that the NYPost story was a violation of Twitter’s terms of service agreement.
None of (the coverage of) these letters describes a key detail: How the Oversight Committee got the copy of the laptop they claim they have. These criminal complaints are broad enough that they likely include at least a few people involved in the channel via which the Committee obtained the laptop, meaning that the Committee would be — is — harboring data from a private citizen that he claims was illegally obtained.
Significantly, the letters include false statements to Congress among the crimes raised (probably with respect to Mac Isaac). Given that Comer’s actions are premised on what Mac Isaac has claimed (and as several of these stories note, Mac Isaac’s story has changed in significant ways, and never made sense in the first place), the allegation may give the Committee further reason to exercise caution.
At the very least, it’ll give Democrats on the Committee plenty to talk about in next week’s hearing.
I thought it would take some doing to top kicking off one’s chairmanship by having a hearing to complain about non-consensual dick pics. But having a hearing to complain that stolen private information wasn’t more widely disseminated may top that.




If Democrats on that Committee have any sense, they’ll coordinate using the time to lay out how this is about Republicans demanding the right to post “revenge porn” about 6,000 separate times.
Dems should move to have the hearings un-televised due to the graphic nature of the content and the inclusion of full-frontal male nudity as part of the evidence. Comer would be furious at the thought of losing his big TV opportunity.
HOW is everything…but EVERY.THING. tangled up together?!?!?
https://twitter.com/joshtpm/status/1620493649036599297
1:46 PM · Jan 31, 2023
BURRA worked with BANNON on his War Room show, and that got him connected with MAGA’s like GAETZ, who placed a copy of the laptop into the Congressional Record.
GAETZ later interviewed BURRA: “You were essentially BANNON and GIULIANI’s Indian tech guy.”
Ohhh…..
Precisely
Obviously, I’m not commenting based on specific knowledge, but for most of the time I’ve been reading stories about what the Trump White House was like from the inside, I’ve had an overwhelming sense that Trump simply complained about whatever he wanted to have happen in front of everyone, and everyone responded by rushing to please the king(*), without talking to anyone else who heard the same complaints, because they all viewed each other as rivals, and without ever once wondering, “is making this thing Trump wants to happen my job, or is someone else supposed to be doing it?”
I can imagine that the Trump campaign was the same way, because there doesn’t seem to have been much space between the Trump campaign and the Trump White House.
If Trump had noticed or cared that the people who were trying to please him were bunched up like 6-year-old soccer players, and actually managed them, we would be in a MUCH worse place now, because so much more damage could have been accomplished.
(*) “Will no one rid me of this turbulent / troublesome / meddlesome priest?” IS attributed to a king, right? Trump seems to have the same management style as Henry II of England.
Re: “Trump simply complained about whatever he wanted to have happen in front of everyone, and everyone responded by rushing to please the king, without talking to anyone else who heard the same complaints, because they all viewed each other as rivals”.
This is the management style of dictators everywhere. It’s how Hitler’s inner circle worked. His flunkies called it “working towards the Fuehrer,” and the point of having flunkies compete with one another is so the dictator retains ultimate decision-making power. Moral constraints have to be thought about; have to be recognized; working towards the Fuehrer focuses the flunky on “what to do,” thus delaying recognition, and pushing thought into the background of one’s daily tasks. Scum, all of them (including Henry’s knights; an aristocracy is just a better-organized, hence more durable, mafia).
Yes, the management style was working toward the Fuehrer, trying to figure out what he would want next. Even when he didn’t say. Significant. that Trump’s people ended up using the same approach.
“The Fuehrer”? Really? Please do not bring that kind of shit here.
Seems to me that FentFent was referring to the original Adolf Hitler, and commenting that Trump’s management style is similar to Adolph’s. Not using Fuehrer as a nick name for Trump.
In either case, plain talk would serve better than this, avoiding Godwin’s law. We need to focus on the topic of this post and not get sidetracked into devolutionary chatter which sucks up time and space.
Well, there you go. The description of Trump’s alleged management style is absolutely reminiscent of Hitler’s, as anyone familiar with Hitler knows. But here we go, with weak liberals falling all over themselves to divert attention from the disgusting Republican misuse of these photos, to obsess over some utterly infantile reservations about whether pointing out an obvious truth is a violation of “Godwin’s law,” and therefore far more atrocious than the Republicans’ smear campaign. We see this over and over again. Republicans have licensed themselves to spread the most nauseating lies about Democrats, while Democrats are afraid to speak the truth for fear some right wing jackass in the back of the room is going to start braying.
You could simply call it fascism and focus on the post instead of blah-blah-blah bitching at the choir.
I’m bloody tired of babysitting you folks who can’t stay focused on the post itself, especially drive-bys with three comments under their belt — that’d be you — who think they can police this place.
Especially when Hair Furor is much more apt
This. Well stated.
On the other hand, Henry managed to establish trial by jury (cut the church out of the court business) and somehow managed to get Peter O’Toole to portray him twice. Don’t go slagging on Hank.
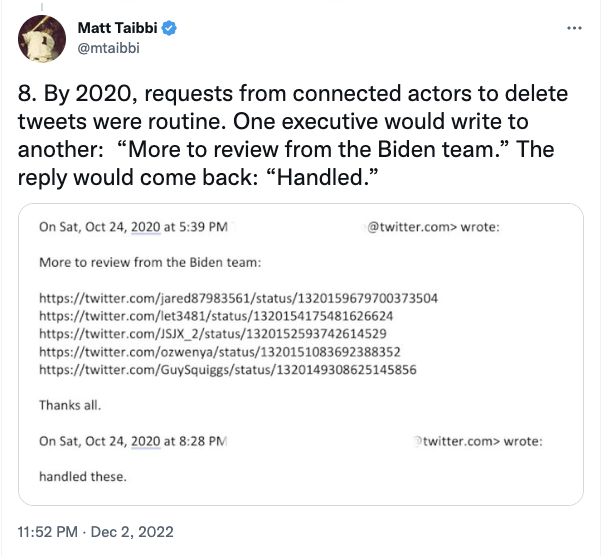
LOL there’s how the loop was closed on manufacturing evidence and delivering it. It’s almost comic relief.
And this got me wondering if there might be connections between SANTOS/BURRA and the Conservative Partnership Institute [CPI], whose founder, Jim DEMINT says in a promotional video:
They have also been expanding their production studios.
https://www.emptywheel.net/2023/01/04/watching-the-circus/#comment-977411
There is a MISTAKE in that thread! I linked a letter from CAP and NOT from CPI.
The letter is from CAP, not CPI as I said in that thread.
CAP and CPI are both effectively front organizations for the Council for National Policy. And CNP is the answer to your question about how everything is tangled up together.
Thanks, William, for suggesting that easy way to think of it. It’s like a metastasizing blob.
What is an “Indian tech guy”? Is that an actual thing people say, or is it just some random blarp out of Gaetz?
Yes, people say this. India recognized pretty early that its large population of relatively well educated English speakers gave it a competitive advantage in the international technology industry. India has pursued a pretty effective national policy to support that. India and the Indian diaspora are a real powerhouse in tech. With that success comes a whole host of stereotypes.
Exactly. In the 80’s the large US based medical equipment company I worked for had Indian s/w people doing most of the work. Due to the 12 hour time difference a few Indian engineers would be in USA at all the meetings and then tell the actual coders in India what the next steps were and when we came in the next morning the latest rev was in hand!
[Welcome back to emptywheel. Please choose and use a unique username with a minimum of 8 letters. We are moving to a new minimum standard to support community security. It’s been quite a while since you commented last, you may have missed this gradual rollout. We also have many users named “David” or “Dave” making a unique name important. Thanks. /~Rayne]
The problem, though, is that Indian ethnicity has nothing to do with Burra’s role and relationship with Bannon and Giuliani. Malaysia, Philippines, Indonesia, Burma as well as India are big technology exporters from Southeast Asia — having origins from any of those locations just wouldn’t matter. Gaetz’ comment about Burra’s ethnicity is racist.
What matters to this thread is Gaetz knew Burra and his relationship to Bannon and Giuliani. How close does Gaetz have to be to the core of several conspiracies to know their tech guy. That’s not even a question.
Of course, the committee will be doing *both* of these, which will top doing either one alone.
Agreed. It will be interesting to see what media coverage says the committee is investigating, which isn’t quite the same thing.
Also complicating the process is Hunter Biden’s point that this is regarding a laptop that has no chain of custody along with his personal information blasted all over the world. His attorney is proceeding along a path toward litigation, which while the Comer clown show won’t be affected, the non-RWNM press would actually have to acknowledge when court events happen.
Perfectly explained.
Why do I always get the feeling these skirmishes serve as a look left throw right strategy? Do these folks do any real work for their donors besides trying to own the libs? Seems intended to distract. From what?
Oh, look; income inequality in the US has reached record levels. Now about these pictures of Hunter Biden…
Intended to distract from literally everything they do because it’s becoming clear that being unethical or perhaps even criminal is now part of the vetting requirements to run as a Republican.
Trump’s documents, fake electors, inciting a riot that spilled into the Capitol, extorting Ukraine, Anthony Devolder, etc. etc. etc.
ETA: Gaetz paying minors for sex, Jim Jordan administrating an abuse scandal at OSU, MTG stalking and harrassing survivors of school shootings, Richard Burr’s insider trading… the list goes on and on I could edit this post in perpetuity.
The tale of the blind computer shop owner and his interactions with the FBI and with Giuliani is indeed bizarre. It strains credulity.
And yet, Mac Isaac has produced a document apparently bearing Hunter Biden’s signature and in accordance with which Biden agreed that the equipment “after 90 days of notification of completed service will be treated as abandoned and you agree to hold [______] harmless for any damage or loss of property.”
https://www.yahoo.com/video/fbi-veteran-conducts-signature-analysis-010500694.html
How does one reconcile this with the claim that the laptop was stolen?
Of course, this will be a major point in the hearing. Meantime, what do people think?
Hi there. Again. There may or may not be a “hearing”. What uninvolved “people think” is irrelevant.
Where did you come from to be injecting this garbage into our blog? Why, and exactly who are you?
Why should anybody here care? The answer is, without anything, they should not.
I personally enjoy reading what thoughtful and informed “people think” – Marcy in particular – even if they are writing on topics with which they are “uninvolved,” such as this one. I assume this blog has a comments section in order to foster further thought and discussion amongst a broader community that may be equally “uninvolved” in the topics at hand. I thought Patient Observer made a good point: the laptop repair story strains credulity, but I’ve not seen that Hunter Biden or any body else has called the repair-shop-story a hoax. How should we make sense of that? My greatest frustration with this site is the incessant incivility of the comment moderation. I appreciate your banning or calling out trolls, but the too-frequent hostility towards seemingly good faith commenters makes me cringe. If you think we’re all stupid and unworthy, you can always shut down the comments. Otherwise a modestly gentler approach would be welcome. Thanks in advance for your consideration. Have a nice day.
[Welcome to emptywheel. Please choose and use a unique username with a minimum of 8 letters. We are moving to a new minimum standard to support community security. Please also avoid policing contributors and moderation in future comments. Thanks. /~Rayne]
I left emptywheel.net (was a daily reader) for the last year specifically because bmaz’ rude and unnecessary commentary. It actually insults EW readers to have the gatekeeper yelling at honest commentary. Sometimes he is spot on, but rarely needed. I returned to EW because I could no longer follow Marcy on Twitter. I know you don’t need my opinions, and don’t owe me anything but bmaz’s junkyard dog bullying style is driving at least this person away from your site, which could perhaps be one of my favorites.
Then stick to reading the posts and stay out of comments. Problem solved, because your comments like this one don’t help matters.
Every family needs at least one beloved curmudgeon -bmaz is ours. I agree, let’s stay focused on the post – which was excellent (as always)
Your assertion, bmaz, that “what uninvolved ‘people think” is irrelevant” is quite interesting!
Is not this discussion forum precisely for the sharing of information by and thoughts of uninvolved people? I mean, where exactly is the logic? What exactly is the standard?
Here are perhaps the most straightforward answers to your “Why should anyone care?” question:
1. Understanding is a good thing in its own right. The sharing of thoughts on tricky questions is a path toward understanding.
2. If one is in a discussion with a MAGA person who, following Mac and Bannon, counter the “stolen” charge by pointing to the document, it is helpful to have a well considered reply.
So here is my further question for you, bmaz: Why do you dismiss as “garbage” a topic that is certainly pertinent to any discussion of the “stolen laptop” question? Is it in your view irrelevant? Why not simply give an opinion on it?
Yeah, thanks for your elucidation as to “understanding”.
Take your Hunter Biden “stolen laptop” shit and start your own blog. It is not going to happen here via you.
Mac Isaac also couldn’t identify the person who brought the laptop in, didn’t get any identifying information from them, not even a call-back number, and apparently gave it to the first person who asked about it.
So, why should we trust *anything* claimed abut it?
I always fly across the country to leave Macbook laptops with incriminating evidence on them in the hands of blind independent computer shops and then leave them there.
[obscure computer shop in a strip mall that I couldn’t find without a map]
PJ and Unabogie: Isaac Mac’s store is in Trolley Square, Wilmington, one of the first business areas one comes to on your way into Wilmington from “Chateau Country” where Joe’s House is located.
Although Hunter lived in LA, he had grown up in Wilmington and his father still maintained a home there. Around the time the laptop was delivered to Isaac Mac, recently divorced Hunter had been in or ending a relationship with his dead brother’s widow. Before he became ill with brain cancer, Beau was the AG of Delaware. Beau and his wife lived in Wilmington. She had worked as a guidance counselor at Archmere Academy, the Catholic school where Joe, Beau and Hunter attended high school. So, it isn’t implausible that Hunter could have dropped his non-functioning laptops off at Isaac Mac’s store.
There are a zillion places in L.A. that fix Macs, not counting Apple stores. He didn’t have to take it across country. (And since there is zero evidence that he did, or that he was the one who left it at Mac Isaac’s store, I don’t buy the story you’re trying to push.)
I’ve yet to see a plausible explanation for how Hunter Biden might choose a random, obscure repair shop for multiple laptops, leave his very incriminating files there, and then fail to pick them up when called about them. If, as you say, he was staying just up the road from the shop, then why leave them and not pick them up?
But if you then say he was too far to conveniently pick up his property, then why choose that shop in the first place? None of the story makes sense.
What does make sense to me is that they hacked the files some other way and then made up the story of the laptop. That’s a simple story that matches the facts much better.
Thomas A. Fine narrowed down the manufacturing date of the laptop:
https://mstdn.social/@[email protected]/109672883025453676
(made in 2018, ended up in repair in 2019)
It seems very odd that someone would take their machine even if damaged outside warranty to some rinky-dink shop rather than an Apple store given the age of the device. This has been a huge flaw with the story being peddled by the right-wing influence op.
Indeed, the more useful question is why Hunter would not seek a warranty repair, unless it wasn’t Hunter that dropped it off. Any warranty repair with Apple products would have included notice back to its owner (Hunter or someone else) for invoicing, etc. so my suspicion is that the laptop (if it is Hunter’s) was at best already stolen goods (whether or not it was Hunter’s is irrelevant) when it reached the repair shop.
Recall the Project Veritas diary scoop that they had to walk back when it was clear it was a stolen item. That was another ‘smear Biden’ project so there is some consistency in motive to hit at Joe via his kids and relatives.
Rayne, PJ and Unabogie: I lived in Wilmington where Hunter and Beau grew up and lived. DE is a small place. I happen to know that Hunter’s children (though I heard of them as Joe’s grandchildren) went to elementary school a 5 minute drive from Trolley Square, which is on the way to the affluent residential areas. I’ve been to Trolley Square many times and Hunter certainly has been there too. The nearest Apple store is south of town in Christiana Mall, a 15-20 min or more drive from the affluent North Wilmington communities where Joe and perhaps his sons lived.
I’ve moved and have no personal knowledge of where Hunter and Beau lived. Wikipedia says Beau lived in Wilmington. After Beau died, Hunter had a relationship with Beau’s wife (another Wilmington native) from 2016 to 2019, and was divorced in 2017. My guess is that Hunter was frequently living in Wilmington during this period, possible at Joe’s house (where info from the laptop says he paid some bills for maintenance.) Of course, he also had lived in LA with his first wife after leaving Wilmington, and is now reputedly living with his second.
Thus, it is plausible that Hunter COULD have dropped off his laptops at Isaac Mac’s in Trolley Sq. The apparent insignificance of this place is not a good reason to reject Isaac’s story
Just as you reasoned here that a dinky repair shop in Trolley Square shouldn’t be ruled out, somebody likely thought the same thing about dropping off manufactured materials in a way which encourages the right-wing to turn on its “firehose of falsehoods” and make it difficult to counter because look, it’s sooo obvious just the way you explained it.
But thanks for carrying their water for them and amplifying here, without any hard evidence to make the case.
Sorry Rayne, I’m reporting facts, not carrying water for any point of view. These are facts I happened to know from personal experience, plus some I looked up trying to reject plausibility. Beau Biden was the AG of Delaware and I expected him to have lived with his wife in the capital (Dover), an hour drive to the south. Wikipedia told me they lived in their hometown of Wilmington.
For all I know, bad actors knew Hunter was living in Wilmington and recruited Isaac Mac to entrap Hunter – rather than someone in LA. However, as best I can tell, Hunter chose the sensible legal strategy of neither confirming nor denying ownership of the laptop until he decided on a strategy to respond – in this case by suing Mac and Giuliani (and thereby confirming the laptop was his?)
If I were selling a point of view, I’d say both the laptop in October 2020 and the Steele Dossier in October 2016 were equally dubious unconfirmed material from the political opposition and neither should have been published immediately before an election. Especially after Giuliani sat on the laptop for at least a month, making it impossible to validate before the election. That suggested to me Giuliani was afraid the laptop wouldn’t stand up to close scrutiny. Best wishes.
“That suggested to me Giuliani was afraid the laptop wouldn’t stand up to close scrutiny.”
But Hunter lived in Wilmington! Near Mac’s shop! Jesus, pick a side and stick with it. Be more concise while you’re at it.
The question is why did Isaac look into the individual files? He opened individual files which has nothing to do with computer repair. This is like the plumber going through your closets.
Isaac stole Hunter Biden’s personal information.
Not to mention there was nothing criminal contained on the laptop, so what piqued his interest so much that he went to the FBI and/or Rudy with the data?
Or potentially planted information / enabled the ones who did, no one knows for certain. IIRC, there were reports that the laptop isn’t pristine in terms of its preservation, and the chain of custody is likewise suspect. However, it does give Comer a reason to run a hearing (which he would do anyhow) to generate sound bites. Who is on the committee from Team Blue?
He said because the mirror of the drive kept crashing, so he brute forced it and than examined the contents to verify (which he claims were criminal in nature). I imagine the FBI has the original.
Where he possibly broke state law was when he gave copies to others who were not law enforcement without authorization. Any blurb about signing away rights to unclaimed personal property before a year elapsed (specified in state code) probably wouldn’t hold up in court. And also perhaps why the FBI subpoenaed the laptop, though that could be chain of custody.
First off “ harmless for any damage or loss of property.”
There’s a big difference between personal property and personal information stored on that property. Second off and more important, “after 90 days of notification of completed service” Hunter was never notified that service had been completed because Isaac did not have contact information to notify him.
That still doesn’t give authorization to share that private information to anybody other than law enforcement.
TITLE 11
Crimes and Criminal Procedure
Delaware Criminal Code
CHAPTER 5. Specific Offenses
Subchapter III. Offenses Involving Property
§ 935. Misuse of computer system information.
A person is guilty of the computer crime of misuse of computer system information when:
(1) As a result of accessing or causing to be accessed a computer system, the person intentionally makes or causes to be made an unauthorized display, use, disclosure or copy, in any form, of data residing in, communicated by or produced by a computer system;
Merchant disclaimers are only as good as the law allows. If I drop off a PC, laptop, or cell phone and forget to claim it, the merchant may be entitled to claim ownership of the abandoned device itself, but should they be able to legally take everything that resides on the device? Should they be able to take my home security code and clean out everything in my house? Or my banking PIN and wipe out my checking and savings balances? It’s beyond logical to believe that every email on the laptop was written from that specific laptop and saved only there. Likewise, all texts, photos, and videos that are being spread in the echosphere were probably originated on some other device that Biden did not leave in Mac Issac’s possession. It’s like if Hunter Biden left his wallet with some abandoned dry cleaning. The dry cleaner may be able to keep the clothing, the wallet, and maybe even the cash, but they shouldn’t be able to max his credit cards and post naked pictures that might have been left in a pocket or in the wallet. There are limits to what is covered by any merchant disclosure.
Original disposition of laptop should be easily resolved by either (1) contract law versus tort law (and/or possibly both) if there was a service agreement in place that addressed handling, return and abandonment, or criminal law; if latter, Hunter should have timely filed police report disassociated from the timeline of the political ratf’king op.
IF it was his laptop. AFAIK, all that Hunter has acknowledged is that some of the information released publicly might be his. Now that Biden has a new attorney, we may get some more answers under oath or admissions in letter responses.
That’s a really, really good point.
I half expect the Twitter execs to avoid questions because they no longer have access to their corporate email addresses/files… Which wouldn’t be unfounded.
[Welcome back to emptywheel. Please use the same username each time you comment so that community members get to know you. This is your second user name; you commented previously as “Time Enough.” If you “AintGotTime” to use the same username, then don’t you don’t have enough time to comment. Thanks. /~Rayne]
“Ain’t too proud to blog”
It’s funny to me that none of those four articles cited bring up who Abbe Lowell is and the significance of hiring him.
It’s as if the Yankees signed Shohei Ohtani but a newspaper article buried the mention and said nothing about his record, referring to him only as a right handed pitcher being added to the rotation.
Abbe Lowell: Ugh.
https://www.refinery29.com/en-us/2019/03/228301/ivanka-trump-lawyer-email-michael-cohen-testimony-changes-moscow
He’s a classic adversarial system lawyer. He’s represented some awful people, but he’s the kind of attorney who will defend a client regardless of ideology and a Democrat won’t need to worry he’ll represent anyone else’s interests. He’s no Sidney Powell, both in terms of competence and responsibility to his clients.
“…a Democrat won’t need to worry he’ll represent anyone else’s interests.”
We’ll have to agree to disagree on this one.
https://www.motherjones.com/politics/2021/06/abbe-lowell-is-the-go-to-lawyer-for-embattled-politicians-now-he-faces-a-controversy-of-his-own/
Hey, Abbe is an extremely good lawyer. Don’t shit on him because of who hires him.
This transfer of ownership of the laptop is dangerous to Mac Isaac. He may be entitled to the hardware but not the data written on it like a bank account number and password. If true, repair people could wipe out people’s accounts with impunity. If he were an honest businessman and not ideologue he would have erased or destroyed hard drive. Isaac has an invasion of privacy issue.
I can make the case that he stole personal information. You can make repair commands without opening individual files. When I purge my files to optimize my computer, I do not open an individual Word or Excel document. And, neither does Geek Squad.
I agree with all of that, freebird.
The idea that in the normal course of seeking to repair a damaged laptop a technician would go snooping into the contents of its files struck me as bizarre and suspicious when first I encountered Mac’s explanation for his actions.
Interesting. I ALWAYS assume a computer repair tech will go through the files on a computer I left with them. It’s why I almost never do that, or else encrypt all important stuff before dropping it off.
That would be the ideal scenario, Steve13209. Problems requiring a professional repair, however, often involve one’s being unable to do just that–that is, frozen or locked out.
If my house were burning down, I would not begrudge the fireman finding me naked.
You would be mad if the firemen took a picture of you and posted it on line after they put out the fire. This what they are doing to Biden.
You’re making an awful lot of assumptions. Not prudent.

We have some very naïve community members who’ve apparently forgotten controversies like that about Geek Squad employees snitching to the FBI.
See: https://www.npr.org/sections/thetwo-way/2018/03/07/591698708/fbi-used-paid-informants-on-best-buys-geek-squad-to-flag-child-pornography
And techs are quite likely going to need to go through files — perhaps not opening them all but possibly hunting down bad drivers, .dlls, .exes, so on — in order to solve problems like MitM and malware infections. Encrypt data files on an external drive, not on the desktop/laptop for this reason.
All my .exes live in .texas.
I’ll see myself out.
I’m surprised you beat punaise to that. LOL
And here I always thought it was:
All my .exes live in tech says.
that’s Pretty Damn Funny.
I do not think it has ever been established with any amount of certainty that the physical laptop is Hunter Biden’s nor that he dropped it off for repairs. Neither Biden nor his attorney have conceded this to be truth. It is evident that some (not all) of the data is authentic and from Hunter Biden’s personal devices and is found on the hard drive that has been copied and passed around. What has not been established is how that data was obtained or by whom, only that it was not authorized by Mr. Biden.
PS Rayne, I have changed my name to conform to the 8 letters or more.
[Thanks for updating your username to meet the 8 letter minimum. /~Rayne]
This thread seems to get to the one thing that has been a concern to me since this “Hunter Biden laptop” saga began, and that is the broken and probably illegal “chain of custody” associated with this device (we know it isn’t a laptop anymore) and the data thereon. A repairman can’t just start browsing files on a customer’s device that has been left for repair, let alone make copies or “mirror” or “image” the data on the device without consent. Let alone give the data to someone else’s attorney to do who-knows-what with the information that has been pilfered! Also, what are the escheat laws in Delaware? You can’t just claim unclaimed property for your own without going through certain procedural and governmental channels. This Mac Isaac dude is a thief at best and conspiratorial fascist asshole at worst and I hope he is personally sued by the Biden family for millions.
He could well be both.
Zinsky 123, I agree with much of what you say here. However, with regard to the making of data image copies of devices I’d like to add a few observations and an analogy that, while not necessarily succinct per se, I hope clarifies some of the issues between physical recovery, ownership, and data rights to found or abandoned devices…
Data recovery technicians regularly make images of data from devices where the original device media or file systems are damaged in some way. This is not unusual. It’s done to ensure that the data is retained for the owner of the device. Often, in a diligent shop, this image copy will be made as soon as it becomes apparent that immediate recovery or repair of the device’s media storage and/or file system is going to be difficult or problematic. Doing this sooner means reducing likelihood of further accidental or procedural loss of the data in further recovery/repair attempts. A reputable shop will either give the copy to the customer once the work is done of it the device is deemed irrepairable or easily replaceable. This image/data copy benefits the customer in that instance.
What is unusual, and illegal in most instances I can think of, is using such copy-images for anything other than the actual recovery and return of that data to the legal owner of that data. And, yep, you do not automagically get full use legal rights to data on a device simply because the ownership of the physical device has devolved to the shop after a period of time. The legal possession and right of use to the physical device is not controlling for the data on the device.
As an easier to understand analogy, say you found an “abandoned” digital camera on the street. You take the camera to the police station. No one appears to claim legal ownership of this found device over the next year and, under the laws of the state and county in which you found the camera, you then claim legal ownership to the camera, taking legal ownership. Now you have legal ownership of the physical camera, and any images that were stored on it are now in your legal possession as a matter of fact. However, the >contentare notmight< have had a legal claim of possession of the physical device. Maybe. But he did not have a sudden right to use the found data on the device for purpose of defamation or invasion of privacy. And, while I'm not a lawyer, I'd certainly imagine that most fair courts in this country would rule against the owner of the shop if there's a solid case made for of that shop owner having improperly exploiting any "found" data on the device for purposes of defamation and/or political expediency.
Is the material created on the laptop protected by a copyright, whether expressed or not? I’ve heard that if you write and create something a copyright exists. I gather that having a copyright is one thing and enforcing it difficult.
Copyrights typically extend to the creator of any original work regardless of whether a copyright is expressed.
But it would appear that the right to privacy is of primary concern here.
There are so many things at stake here you could just about run down any list of rights from the Charter of the Forest to the Bill of Rights to Biblical rants about justice and check off one thing after another, from persecuting the victim of the crime to chain-of-custody issues, to libel, to slander, to the right to cross-examine to bearing false witness… I think the Right of Estover and Immanentizing the Eschaton may also be involved her in one fashion or another…
Suffice to say the Republicans have wizzed on the electric fence and I’m eagerly awaiting their upcoming “Have you no sense of decency” moment.
Perhaps, but I was trying to be quite specific.
The potential violations of federal statute cited by Abbe Lowell (18 U.S.C. § 1030, 18 U.S.C. § 2701 and 18 U.S.C. § 119) are all predicated on “the Unauthorized Access, Copying and Dissemination of Mr. Biden’s Personal Information” (i.e. violations of his right to privacy).
Beyond that and joking aside (plus I’m sure bmaz will correct me if I’m wrong) someone stole Hunter’s laptop or hard drive or files, then someone received the stolen laptop/hard drive/files, and I’m guessing there were accessories to those crimes, then if false material was inserted into whichever of Hunter’s files he actually created there’s a fraud upon Congress/the courts/the prosecutor or whomever may have handled the files in an official capacity, so there’s room for a ton of charges if anyone’s inclined to make them… at this point the laptop is the Katamari Damacy of crime, just rolling from one Republican to another and picking up felonies and misdemeanors as it travels.
Sorry for the unseriousness, but there’s a level of silliness here that’s really hard to ignore; Hillary Clinton’s server repeating itself as farce.
Well, the giveaway is the insistence that there is something nefarious in all of this without being able to point to anything like actual evidence. HRC, CRT, ANTIFA, etc., all over again and the MSM is falling for it again.
Thank you for introducing me to two new terms.
Perhaps in response to all this confabulation, someone could invoke the Rule against Perpetuities?
What do the dropped-off laptop caper, Trump’s insistence on the “stolen election”, and the Russian invasion of Afghanistan have in common? They were ill-conceived and clumsily executed “special operations, they failed to achieve the desired results, and the perpetrators keep doubling down on the failing strategies. Brings to mind the kind of person who thinks other people are chumps and that they can force people to believe what they want. People who don’t take no for an answer. People like Putin, for example.
They also share the achievement of “secondary” goals (chaos, damage, distraction) while failing at ostensible primary goals. Other people’s lives are upended/ruined/sacrificed, with accompanying loss of time and treasure and minimal immediate personal consequence.
Wasteful, short-term thinking. Bannonite chaos monkeys running amok. The repeated “special operations” and double-downs only make sense as a long-term strategy if the chaos itself (always at the expense of others) IS the goal.
Do these development now mean that Hunter Biden has admitted the laptop was his? Did he admit to recklessly abandoning it in Isaac Mac’s store?
According to what I have read (sorry, don’t remember where), H. Biden’s lawyers have said he did NOT leave the laptop at the computer store and that SOME of the material being circulated as having come from the laptop (specifically, from the hard drive) is his.
Per Hunter Biden’s own lawyer that SOME appears to be quite a lot.
From Abbe Lowell’s letter to DOJ:
200 gigabytes is about as much as most laptops can hold. There’s also no evidence in that letter that all of that was Biden’s.
I don’t quite understand the apparent desire of some to minimize the mass dissemination of Hunter Biden’s personal information.
Sure, while some of the data appears to have been titivated for public consumption, much of the data was in fact Hunter Biden’s. Yet none of that data, titivated or otherwise, appears to be particularly damning, despite the inevitable Republican sound and fury.
To my eyes the scandal here is that private data belonging to the son of the POTUS was illegally accessed, disseminated, and exploited for political and monetary gain, and that agents of the FPOTUS were deeply involved.
And yet, as Marcy aptly points out, the chair of the House Oversight Committee seems most concerned with why Twitter didn’t post Hunter Biden’s dick pics.
Excellent summation. The problem is like other influence ops before this one — take the DNC server hacking. The right-wing including Trump himself made it about the server and a demand to see it rather than about the hacking and who/what was behind it. Any time the hacking itself came up, it was redirected to the server: where was the server, why didn’t the DNC turn it over, so on.
Except there was no single server to turn over. The demand became the second wave of the attack, attempting to obstruct the DNC’s operation by insisting its server was turned over.
This influence op has a similar second-wave obstruction effort in that the House GOP has and will use it as a means to redirect attention from Biden getting anything constructive done. It becomes an excuse to badger and hector Biden to reduce his effectiveness by forcing response after response. The redirection needs to be titillating (not titivating) for this to work. And lo, it becomes about dick pics, and about the dick itself rather than the privacy of the dick’s alleged owner.
Is there anything on record confirming Comer’s specific interest in the Dick picks, or is it merely an insinuation ?
It’s also an inference. See BREAKING: JAMES COMER JUMPS RIGHT ON HUNTER BIDEN’S DICK PICS.
No.
Besides the Dick Pics, do we know of anything else on the laptop GOP intends to run with? Alleged ties/ attempts to involve his dad in business deals, i.e. Burisma? No one doubts GOP operatives would try to place incrimination info on the computer. That don’t mean they did. Besides the dick pics, anything else on it that might expose Hunter? What else might they alledge because right now they look stupid. Any trustworthy sites that explores what else the GOP thinks they have- why/ how the laptop can be weaponized?
If there was anything actually damaging on this laptop, we would already know about it. The GOP are desperate for anything they can get to smear POTUS, and so far all they’ve come up with is drivel.
“That don’t mean they did. ”
https://www.washingtonpost.com/technology/2022/03/30/hunter-biden-laptop-data-examined/
That WaPo report last year said “In their examinations, Green and Williams found evidence that people other than Hunter Biden had accessed the drive and written files to it, both before and after the initial stories in the New York Post and long after the laptop itself had been turned over to the FBI.”
The WaPo researchers couldn’t even verify that all the data they were examining – which had passed through Rudy Giuliani’s hands – even came from a single disk drive.
The FBI has the original drive. But the ‘data’ which is being passed around to the press and other individuals to make fun with, is not verifiably from a disk image. Any number of people could have had access to it to titivate it for public consumption.
“The GOP are desperate for anything they can get to smear POTUS, and so far all they’ve come up with is drivel.”
That’s it in a nutshell. They’ve been so desperate for years they’ve allowed themselves to be compromised by hostile countries who offer to help create smear material one way or another. In 2016 it was “But her emails” and in 2020 it was “But his son’s laptop” when “But his son’s job in Ukraine” didn’t catch fire.
Now we have to pick apart how this particular influence operation was supposed to work to derail Biden in 2020, again in 2022, and into 2024 because they’re not done.
I think you coined a word there, btw, with “titivate.”
“Titivate” has been around for a while, maybe since 1805.
I see that now — it’s definitely an obscure word. https://www.etymonline.com/search?q=titivate
I guess that depends on your circles. My wife uses it all the time, when gardening. It was new to me, till I met her.
My circle consists of quite a few fans of 17th-19th century British, American, and French literature. I have yet to run across tivitate. Apparently I need to run into a specific group of gardeners.
Certainly in use when I was in primary school, though I can’t remember if I heard it first from my mum or the nuns.
Thank you for educating me about areas of doubt on the data’s authenticity.
I can’t point you to a trustworthy discussion, but yes, the GOP intends to run with Joe Biden’s alleged corrupt involvement in Hunter Biden’s business deals (influence peddling, that Joe Biden pressed for Shokin to be fired in order to protect Hunter and Burisma, Hunter funneling CEFC China Energy $ to Joe Biden, etc.). Jim Jordan (not trustworthy): “As more evidence comes out, it’s clear that Joe Biden’s relationship to Hunter Biden’s shady business dealings are worse than we ever thought.” A quick search of the NY Post (also not trustworthy) will tell you some of the emails the GOP will highlight.
You wanna talk stupid?
Here ya go. Meet George Santos’ Director of Operations.
https://youtu.be/meNoGhSEKus
It’s plain to me that much of this discussion is by folks that know absolutely nothing about Apple hardware (and software). Mention of “dlls” and “drivers”, etc. is evidence of that fact. Everything about an Apple computer is “proprietary” and Apple only. Nothing resembles PC hardware. And, Apple doesn’t allow just anybody to access parts for Apple computers. If a motherboard, or a keyboard, or a screen or touchpad is bad, it is only available from Apple, and Apple only allows “Apple partner” shops to work on their computers, and not just any computer repair shop can be an Apple Partner. To be one requires a vetting and auditing process, and it is strict. If you don’t believe me, visit the Apple web site and ask for assistance for getting an Apple repaired. Nobody, and I mean nobody, goes to a mall computer shop that is not an Apple partner in order to get a macbook that costs north of $2000 repaired. Now, more about Apple internals, because a lot of posters really should know this–it’s testable, as an old prof used to tell me. Since 2016, the macbook pro ssd (the ‘hard drive’) has been SOLDERED ONTO THE MOTHERBOARD. Before that, the ssd was plug-in, but the pin-outs were Apple only–only an Apple HD would plug into an Apple macbook. With the advent of the soldered-on ssd, it became impossible to replace. If a macbook pro is unbootable (implied by ‘water damage’), the ONLY way to access the ssd was by using an Apple proprietary tool that ONLY Apple has (not the Apple partners), and even then only if the laptop is still under warranty or if the owner has an Apple Care policy. Standard Apple policy is to replace the motherboard (with the soldered-on ssd), and that is only available via Apple. This blind computer guy, whose name happens to be ‘Mac’ is a fraud, pure and simple. The story is concocted, and only plausible to those that know nothing about Apple hardware and nothing about Apple repair policies.
Welcome to emptywheel. Long unbroken blocks of text — like your comment at 341 words — do not encourage ready uptake of material. Please break into smaller paragraphs, keeping overall comment length as close to 100 words as possible. Many of our readers are on mobile devices and long paragraphs are challenging to read on small screens.
” Since 2016″
Well yes.
But do we know the model and age of *this* device?
Because I personally replaced the HDD with an SDD in my own Macbook Pro, 2013 vintage, which I was happily using until mid-2022. (Apple computers never die, they just get repurposed :) ) I’m not a computer hardware tech, just a software tech.
However, it being Apple means it’s very unlikely that Hunter Biden would have taken it to a non-Apple repairer, simply because non-Apple repairers tend to botch Apple repairs (in my experience.) If he wanted data recovered, there are specialist services which can do that specially.
So we have a wealthy man who live in California with a damaged Apple device which he could have had replaced/repaired under household insurance, apparently without a backup, taking it to a non-specialist non-Apple repairman on the other side of the country to do a specialised job.
It’s *possible*. But it adds to the implausibility of the entire story.
Certainly if Biden was trying to hide evidence of criminal activity on his Macbook, this would be the last thing I would do with that computer.
Exactly! If you’re Hunter Biden with a broken laptop you don’t cross the country to visit an obscure computer repair shop, you buy a new one and download your backups off of Apple’s cloud. The talked-about scenario is only believable if the shop was right across the street from Hunter’s hotel or something.
Actually an Apple MacIntosh is not proprietary – much of the software is FreeBSD Unix (an Open Source distribution with freely available source code) with the MacIntosh Graphical User Interface on top, such that most Linux/UNIX-based Open Source programs are available and widely used in the MacIntosh community. But if you open a console, (usually running the Open Source BASH shell) and use ordinary UNIX/Linux commands, you’ll see that it’s mainly FreeBSD under the hood. I’ll also note for the discerning that there are MacIntosh versions of the following standard BSD commands: dd, chown, chgrp, and chmod… I don’t think I need to say more with relation to Hunter Biden’s data.
This also brings up the question of whether the repair-person (if there was in fact such a person) ever really had possession of the Hunter Biden Laptop. What if he had the laptop in his hands for only a few minutes and was able to copy down the necessary information required to download Hunter’s backups off of Apple’s cloud? I realize this is speculation, but I think it’s pretty good speculation: Imagine you drop your Mac Pro into the drink, then take it to a shop. The shop owner says, “Give me your email address and phone number and your Apple ID so I can contact Apple if I need to. Sign here, then get yourself a long lunch and I’ll see what I can do.”
The shop owner realizes that you are Hunter Biden the second he reads the paperwork. Once your back is turned he gets the serial number and MAC Address off the laptop, throws a password cracker at Apple’s Cloud and your backup is now pwned! Or maybe there’s an Apple employee out there who really hates Hunter Biden… there are lots of possible scenarios, all of them more crooked than Trump’s IRS paperwork. But I’m far more inclined to believe some kind of hacking scenario than whatever the Republicans are peddling this week.
If it were legit, yes. But nothing about this says it’s legit in any way.
My suspicion is that someone got ahold of some information from one of Hunter Biden’s computer accounts, and mixed it with all kinds of fraudulent crap. But you’re right: Nobody has proved anything and the whole business may be completely non-legit.
As a fan of Occam I do so appreciate bmaz’ efforts to focus commentary. We who live in Arizona otherwise suffer a deluge of irrelevant emotive “news.” Thanks.
Maybe Hunter did have a Apple Care policy. If he did it adds to the unlikelihood he’d take it to just any shmoe.
Laptop Comer
Pilfer, grab, snatch and plunder,
With the stress Matt Schlapp is under,
Is it really a damn wonder
you may rip more lives asunder?
From Durham to something dumber,
With this next up and comer,
As Nixon might say to Trump’s plumber,
What’s in store for this summer?
Getting down to the nitty-gritty,
Digging dirt, the Dim-Sight Committee,
Like Stone’s “but it ain’t pretty,”
hits rock bottom, what a pity.
I wouldn’t want to speculate
who were the ones to peculate,
That might only germinate
something in the fourth estate.
With frothers & their master foamer,
Will this Mr. Laptop Comer,
such a rich and fertile loamer,
be remembered like a Teapot Domer?
Pluck, pinch, swipe and pillage,
How will this impact our millage?
Don’t you know it takes a village
to contain your sleazy spillage?
Thanks again, SL. “Teapot Domer” needs to join the current lingo.
ew: Eric Herschmann is not, according to reports, on these letters but he was even pitching “laptop” content while working at the White House.
One of many stories about 2020 that I missed at the time…ugh!
Trump Had One Last Story to Sell. The Wall Street Journal Wouldn’t Buy It. Inside the White House’s secret, last-ditch effort to change the narrative, and the election — and the return of the media gatekeepers. // Ben Smith 10/25/20
Web Archive: https://web.archive.org/web/20230206184409/https://www.nytimes.com/2020/10/25/business/media/hunter-biden-wall-street-journal-trump.html
Early October 2020 meeting in McLean, Va
– Arthur SCHWARTZ [advisor of > Junior DON]; meeting takes place in his home
– Current senior adviser to the president, Eric HERSCHMAN [friend of > KUSHNER]
– Former deputy White House counsel, Stefan PASSANTINO
– Former Hunter BIDEN business partner, Tony BOBULINSKI [on phone]
Also makes an appearance in this tale:
– GIULIANI [> NYPost], working with BANNON
A reminder of some of the people involved:
THE PRIMARY THING ERIC HERSCHMANN REMEMBERS FROM JANUARY 6 IS THAT CASSIDY HUTCHINSON WAS WRONG ABOUT THAT NOTE https://www.emptywheel.net/2023/01/20/the-primary-thing-eric-herschmann-remembers-from-january-6-is-that-cassidy-hutchinson-is-wrong/
Also:
7/23/20 Republican National Lawyers Association [RNLA]
creates Lawyers for Trump https://www.rnla.org/lawyersfortrump
Kellye SORELLE worked with this group.
Yuck. Herschmann was allowed to endow himself with a halo during the J6SC hearings. It’s essential to balance that picture with the truth, just as with Barr. Thank you, harpie. For what it’s worth, I missed this at the time too.
1/25/20 BANNON launches “War Room: Pandemic” podcast https://www.mediamatters.org/steve-bannon/steve-bannon-pushing-debunked-claims-about-coronavirus-are-linked-his-billionaire []
Vish BURRA begins working for BANNON on the War Room podcast https://talkingpointsmemo.com/news/vish-burra-george-santos
BURRA is now Director of Operations for George SANTOS [R-NY3]
He is also an Executive of the New York Young Republican Club…yes, THAT one.