Hunter Biden Accused Rudy Giuliani of Hacking His Data, Not Defamation
Ruby Freeman and Shaye Moss’ civil trial against Rudy Giuliani goes to trial tomorrow.
In a number of the scene setters for the trial, people are making claims like this:
In addition to his criminal charges, disbarment proceedings and the lawsuit brought by Freeman and Moss, Giuliani has been sued by various other individuals — including President Joe Biden’s son Hunter — who claim he spread false allegations about them in 2020.
He and one of his lawyers are being sued by Hunter Biden for allegedly mishandling the presidential son’s laptop,
Hunter Biden is not suing Robert Costello and Rudy Giuliani for defamation. He’s not suing Robert Costello and Rudy Giuliani for mishandling “his laptop,” which (even if John Paul Mac Isaac and Rudy Giuliani have told the truth about everything) would never have been in Rudy’s possession.
Hunter Biden is suing the former President’s former personal lawyer and that lawyer’s former personal lawyer for hacking his data. Hunter Biden is suing Rudy for violating the criminal Computer Fraud and Abuse Act: for accessing a computer without authorization or exceeding authorized access.
41. Defendants have violated the CFAA, specifically section 1030(a)(2)(C) of
the CFAA, by intentionally accessing a computer without authorization or exceeding
authorized access, and thereby obtaining information from any protected computer
which, pursuant to the CFAA, is a computer used in or affecting interstate commerce
or communication.42. Defendants have violated the CFAA, specifically section 1030(a)(4) of the
CFAA, by knowingly and with intent to defraud, accessing a protected computer
without authorization or exceeding authorized access, and by means of such conduct
furthering the intended fraud and obtaining one or more things of value.
We will have to wait to see whether he can prove that claim. But particularly given that Hunter has since been charged with 12 criminal charges by a US Attorney appointed by Trump, let’s be clear what the claim is.
Hunter Biden has accused Rudy Giuliani of violating the criminal hacking statute.
One reason people make this mistake all the time — on top of the non-stop Fox News propaganda about this — is they think of the laptop like this:
The laptop, as it was brought to John Paul Mac Isaac’s shop, is better thought of like this.
There were dick pics on the laptop (I’m using artistic license in my choice of dick pics).
There were emails, including emails hosted by Google and emails tied to Hunter Biden’s iCloud account. But the laptop also included on it the means to get into Hunter’s iCloud account and at least some of his Google accounts.
There were other digital keys on the laptop and probably enough bank data to get into financial accounts.
And there was the contents of an iPhone, stored in encrypted form. As I’ve described, I first went down this rabbit hole — the entire Hunter Biden rabbit hole — when I read Gary Shapley’s description that the FBI needed a password to access some of the content, the content from the phone, on what was an actual laptop. That’s when I realized that anyone who accessed the encrypted contents of that phone without a warrant might be at risk for CFAA charges.
Several of the people who’ve been offering up Hunter Biden data confess, openly, that they broke the encryption on that phone.
In other words, no matter how all that stuff got put onto Hunter’s laptop, and no matter how it got brought to John Paul Mac Isaac’s shop, and no matter whether JPMI was perfectly in his legal rights to take possession of the laptop itself — all things that are very much contested — the laptop included the means to get into other data, data hosted in the cloud, to which neither JPMI nor anyone else had authorized access.
And then the blind computer repair man, after having chosen to copy that hard drive that, contrary to his claims was a removable hard drive, by cutting and pasting it and reading it along the way, packaged that all up on a hard drive and sent it, without Hunter’s consent, to the then-President’s lawyer.
We don’t know what kind of hard drive JPMI used — he said he constructed his own, to make it untraceable.
Instead of buying external drives from a local store, where the purchase might be traced back to me, or online, which also could be traced and moreover might lead to damage in transit, I built my own.
It took about a week to collect all the pieces and clone the drive from the store’s backup server. In essence, I created a copy that was as close to the original drive as possible.
As I have shown, at a time when Rudy says he (or Robert Costello) were in possession of that hard drive that had on it means to access several of Hunter’s cloud accounts, an email Hunter sent in 2016 was resent, showing some alterations.
Hunter Biden is not accusing Rudy Giuliani of saying things about him that aren’t true. Hunter Biden is accusing Rudy Giuliani of accessing data — whether on a hard drive copied from a laptop or in the cloud — to which he did not have legal access.






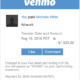
And the fact that JPMI tried to make it untraceable seems to this not-a-lawyer the action of someone who knew that his actions were illegal, or at the least improper and likely to create problems for himself. Why is he not included in the lawsuit?
Hunter is countersuing him on the defamation suit filed against Hunter and others. Per Denver Riggelman, they obtained the drive that JPMI was sharing with everyone else as part of that process, which would have been a necessary precursor to suing other people for hacking, bc then you’d have the baseline of what was really on the drives.
Suit and countersuit on a stupid defamation suit? Ugh.
Well, let’s see. JPMI accused Hunter of defaming him in a single statement in which Hunter didn’t mention JPMI’s name.
And as a result, Hunter was able to get the drive that allows him to sue other people.
I’ll take that swap.
Yes, but a civil tort suit over it is dumb.
Legally? Yup. Tactically? Nope.
Because it makes the rest–the lawsuits for CFAA, on which discovery will not be as risky for Hunter–possible.
Assuming these statements are true, the computer repair store already had some form of backup of this customer’s h/d’s contents on its server, which means there was no legitimate business reason for it to make a further copy that was accessible by anyone other than the computer and h/d’s legitimate owner, which may not have been the person who dropped it off at the store.
It seems considerably less than kosher for a legit computer repair service to go out of its way to create a supposedly untraceable h/d, and then download onto it a customer’s data, in order to distribute it to one or more third parties, without the data owner’s permission, regardless of whether the computer and its physical parts were deemed abandoned. If the business owner suspected foul play for some reason, it should have contacted the relevant law enforcement agency from the get go.
I’d be talking to a lawyer if the repair guy did that with my computer. (I did once need a drive copied, for solid reasons.)
He’s also mistaken if he thinks that would make the drive untraceable. Unless he went down component level and built it in a clean room. Most likely he just used an off the shelf enclosure and put the drive (HDD or SSD) inside. I’m still wrapping my head around why he would go through the trouble since the ones doing the trace would be law enforcement. Plus, everybody knows he gave a copy to Rudy, so what’s the point?
And why not buy from a, um, non-local store? That would obfuscate things unless he was afraid of LE tracking the S/N of the device through the distributor and going through a whole bunch of other steps to find out where it was sold. If LE was willing to put those hours in then chances are there would be other evidence to follow too.
But, as you say, everyone knew that he had the laptop so the whole thing is tending towards moot. Doing extended OpSec for the sake of it seems to be a complete waste of time (like building a secure device and then logging in to Facebook on it) but these folks all seem to be morons, one way or another.
Best & brightest!
I was thinking, why not go to a Best Buy or Egghead and pay cash for a drive? Or have a proxy do it?
Like you said, it sounds exactly like he bought an enclosure and stuck a random hard drive in it (one pulled out of some junk computer most likely), then copied “Hunter’s” hard drive to it. Making this out as some process that would take a week is silly.
Factor in when the stars aligned properly, the timing for when the orbital mind control laser satellites are in the Earth’s shadow, when “they” aren’t monitoring you phone, etc, etc, etc and a week starts to look like really fast turn around!
And we’re worried about deep-fakes of documents, pictures, movies, etc. This has all the marks of amateurish black hats and arbitrary messing with data and credentials. Even Putin and his direct henchmen would be more careful to obscure their deeds. I can hope that JPMI gets a chance to testify under oath to a legitimate committee (obviously not R-run). I’m sure he can weave a lot of tales and perhaps a bit of truth.
LOL Team Putin doesn’t need to do much to obscure their deeds (and quite often don’t as the 2018 poisoning of Sergei Skripal by novichok showed). They just need to sow fear, uncertainty, and doubt, and given the discombobulated US news media ecosphere, it doesn’t take much FUD to do sustained damage.
I think JPMI will only generate more FUD unless he is managed with expertise.
Exactly!
And Putin knows that the “discombobulated US news media ecosphere” provides fertile and receptive ground for Team Putin and Trump to propagate their fear, lies and propaganda.
To me, the real offense was committed by Murdoch and his NY Post for misrepresenting the contents of the laptop into something it clearly wasn’t. The initial story contained promises of “smoking gun” evidence and “secret emails”. There were definitely plenty of steamy photos and videos exposing Hunter Biden’s personal vices. But as far as proof of shady deals, influence peddling, bribes, and corruption, the laptop has been all smoke and no gun since its release.
This strategy goes along with the GOP’s longstanding SOP of quantity over quality. They argue that Hillary got rid of 30,000 emails so there must have been crimes among them. They say the Clintons had hundreds of contacts with influential people who contributed to the foundation, therefore they were selling access. Now they say: Look at all of the emails Hunter and Joe exchanged with Hunter’s business associates. And the media never challenges it. They just go along for the ride.
“The SARS! The bank records! The WhatsApps! See, that proves they are corrupt.”
But no matter how high you stack something, N times zero still equals zero. Why can’t the media ever point out that inuendo is not guilt?
Today, for example, on Meet The Press, Welker was operating as a given that Hunter Biden profited off his father’s name. That may be so, and it’s certainly what the right wants everyone to believe. The absurdity, however, is that Kristin was talking to Mitt Romney at the time. She must know that Mittens is the obscenely wealthy son of George Romney and the father of venture capitalist, Tagg Romney. It is infuriating that they don’t understand, or care, they are using a double standard.
The hypocritical chutzpah is just-off-the-bus-from-Podunk startling. If HB profited off of his – and his dad’s – name, that’s on HB, not Joe Biden. So long as HB did not ask Joe to do anything unethical, and Joe didn’t, he was probably happy to help his struggling son.
Mitt Romney, for example, probably hadn’t the slightest hesitation to profit from his dad’s name, or any objection to his son profiting off of his, Ditto for every other Southern politician, including Matt Gaetz. It’s such SOP for thousands of successful families, we needn’t bother asking the Bushes, Murdochs or Rockefellers about it. Would anyone, including a college admissions officer, have given Don Jr or Eric the time of day if the Don weren’t their dad? Would Jared Kushner have gotten into Harvard without his dad’s name, or been given $2 billion in Saudi money “to manage” were it not for his father-in-law’s? It’s startling when a child refuses the honor – and when the mainstream media pretends that that ain’t so.
MacIsaac is one word. Sorry, it’s just driving me nuts every time I read something about the laptop.
[Welcome to emptywheel. Please choose and use a unique username with a minimum of 8 letters. We are moving to a new minimum standard to support community security. Because your username is far too short it will be temporarily changed to match the date/time of your first known comment until you have a new compliant username. Thanks. /~Rayne]
Seriously, that is your abiding concern?
An abiding concern which also appears to be false given
LinkedIn profile
“John Paul Mac Isaac
Owner of The Mac Shop
Johnny Mac’s Delaware State University
Wilmington, Delaware, United States
160 followers 117 connections”
And the said John Paul Mac Isaac uses that form of his name in posting videos about himself and his interactions with the FBI on YouTube [- link available] under the title “The Truth- John Paul Mac Isaac”
Sigh
OK, so the dude is a crackhead but the rest of the MacIsaacs on the planet, spell it as one word. And I know he’s one of us because I’m related to him, distantly.
Your point has been noted.
So has your OCD, which cannot remain your username here. See your first comment here in this thread.
Well I think you’ll find that
Richard “Steve” Mac Isaac, father of JPMI was commissioned in the US Airforce under that name in 1970, retired as a Colonel in 2000, played a part in the “laptop saga” and still inhabits the planet.
Can’t trust any family where Steve is somehow a nickname for Richard!
It would bug you if it were your last name.
Lol, that is his problem, not mine. I’ll take how he has spelled it. thanks for the help.
No, it wouldn’t. Really, it wouldn’t.
Uniform spelling of names is very much a modern phenomenon. My family name is Kane because a great-great-grandfather was an Irishman whose name was O’Kane. The O’ got dropped somewhere along the way. But as to spelling, the Kanes are the same mob as the Canes, the Cains, the Caines and for that matter also the Keans, the Keanes, the Keens and the Keenes and also the Cahans. And to each of these can be attached the O’ prefix.
One’s spellling of one’s own name is usually a matter of historical accident.
Evans, Evins, Evons, Evens…and it was originally pronounced with a long “E” spelled I, so also Ivans, Ivens, Ivins…
Why didn’t they ask Evans? :-)
[snerk] ROFLMAO
(I’ve read that one, thanks.)
Gunter Gleiben Glauchen Globen…
De(a)f Le(op)pard rocks.
Yvens?
You should be more concerned, then, that Gary Shapley not only spelled it wrong, but referred to JPMI’s father and JPMI differently.
I think JPMI may spell it the way he does to better proft off his name as a Mac specialist. His choice.
“… intentionally accessing a computer without authorization or exceeding authorized access …”
How difficult will it be for Hunter to prove this? In a normal world, when I take my laptop in for repair, I assume that the fixer will need to at least get to the home screen, perhaps log in, or view programs that are not password protected. Beyond that, who knows? But, sending a copy of the hard drive off to a third party who is definitely not a “repair person”? That strikes me as being ripe for a quick judgment.
The computer here would be an iPhone, a backup of which was stored on the hard drive in question. No matter who had permission to access the laptop’s drive, using data found on that drive to then access the iPhone backup would be quite wrong.
That’s not necessarily the model with Rudy. It is the model with Garrett Ziegler, one of the people who did brag about cracking that PW, whom Hunter has also sued.
Hunter does not have to “prove” anything, he is the presumed innocent defendant.
But Hunter Biden is suing those who his lawsuits maintain illegally accessed his personal information. In that case, it is his counsel’s burden in civil courts hearing his lawsuits to prove that this illegal access was committed.
Civil cases require a lower standard (preponderance of evidence) rather than beyond reasonable doubt. Besides, one of the defendants even posted online on how he got around the encryption.
I guess we can assume that Rudy, Costello and the gang are not going to be charged with CFAA violations. The reasons why escape me.
I like how your pic illustration shows both the capital D and the small d in it.
How is this not also embezzlement — the fraudulent use of personal property entrusted to another person? Or is this crime superseded by the unauthorized access act?
[Welcome back to emptywheel. Please use the same username and email address each time you comment so that community members get to know you. You have commented previously here as “Greg Worley” and “Greg WorleyNever,” the latter possibly being a typo. Please pick a name and stick with it every time you comment. /~Rayne]
Embezzlement is a crime, the unlawful taking of personal property entrusted to a holder, but belonging to another, with the intent to deprive the owner of its use. (A related civil wrong is conversion.) The parties vehemently disagree about whether the computer became the property of the repair shop by reason of abandonment.
But the physical computer is worth a pittance. The much bigger issue is the alleged unlawful access to HB’s personal data, which would have remained his, regardless of who owned the physical computer.
It really was a revelation to me when Marcy noted the likely hacking of Hunter Biden’s laptop may have been due to or augmented by the hacking of his iCloud account. That allowed all kinds of nefarious things to occur that wouldn’t have otherwise. It is very instructive to note that none of the charges that Hunter Biden is currently facing, were surfaced because of the exposure of his digital data, thanks to JPMI’s perfidiousness.
And because of JPMI’s grubby fingers ‘making a copy’ of the laptop, I have no doubt that Lowell can’t get that financial ‘evidence’ (much of the other stuff too) tossed for lost traceability, leaving precisely nothing for Weiss to charge for taxes. Between that and Bobulinski, I don’t see much left for Weiss, did I miss something?
Questions about some of the data released. Miranda Devine’s Laptop From Hell cites data I haven’t seen in the Marco Polo set, and Marco Polo doesn’t seem like someone who holds back, that they put everything out they have.
Example of the data in question:
a) Hunter’s diaries going back at least 2010, unclear to me if digital or handwritten
b) group texts sent by Ashley on 11/11/16, while I believe the Marco Polo set of texts goes back sometime in 2018 at the earliest
So:
1) were these items released by Marco Polo and I missed it?
2) does Marco Polo have access to these items as well but held back?
3) does Devine have access to data Marco Polo does not have? Such as a second laptop/hard drive or a separate data breach?
3a) if yes, does she explain the source and I just missed it?
4) do these data items appear anywhere else such as WashEx, Daily Mail, etc?
I don’t know the answer to any of these questions. I haven’t compared the datasets.
I seem to remember the first release of any “evidence” from Rudy was a screen cap that had “sent from my iphone” on it. Couple of security guys pointed it out right away, and said exactly as Marci has…hacked account. They also pointed out it had a modified date too..
Did they use Cellebrite?
Vish BURRA talks about “essentially tryin to create an October surprise” in Manhattan
with GIULIANI, KERIK and BANNON starting in August 2020:
https://nitter.net/mrspanstreppon/status/1731309163165229453
Dec 3, 2023 · 1:47 PM UTC
Links to:
Vish Burra Discusses His Pivotal Role In Unveiling The Hunter Biden Laptop From Hell
https://piped.video/watch?v=meNoGhSEKus
12/7/22 Dinesh D’Souza Podcast
TRANSCRIPT of above VIDEO:
Danielle: [unclear] welcome to the podcast Vish BURRA. Vish is a journalist. He’s done some really cool things with Steve Bannon. He’s actually present and part of the Hunter Biden laptop story, which is what we’re gonna talk to him more about today. So, Vish, thanks for joining us.
BURRA: Thank you for having me, Danielle, it’s always a pleasure [unclear]
D: Oh, great. Well I’m very excited to talk to you because we’ve been talking a little bit today about the Twitter story about Elon Musk kind of revealing this information um regarding Hunter Biden’s laptop and the suppression of that whole story, but I wanted to talk to you because you had a very pivotal role in this, and a very um kind of like behind the scenes role, but was a really big part of the laptop being discovered and um information being published, and I know that we have like a lot of like mutual friends involved in the same story. But I wanted to have you on so you could tell us a little bit just about kind of how did you get pulled into this, how did you first find out about the laptop?
[1:04] BURRA Yeah, so, at the time ahh around August to September of ahh 2020, I was working on the uh War Room podcast with Steve BANNON, I was his producer. And ah at that time he had just been arrested on the boat, remember? Ah, there was that issue during 2020, which he was pardoned for. And after, umm, and after he came back out, he ah looks at me and he says ah pack your stuff, we’re goin to New York, we don’t know when we’re coming back.
And so one, and so we’re you know living in this hotel, ah by St. Patrick’s Cathedral, for like you know almost, almost two months. And um you know dur, in the first week that we’re there, ah I’m driving him back and forth to Rudy Giuliani’s place all day, and I’m, I’m just like hey what’s going on, you know what are we doing, what’s the operation up here? And he said look you can’t tell anybody but I think we have Hunter Biden’s laptop. And at which point I said hey you know Steve I used to be a software professional before I got into politics before I got inta any of this stuff, so if you need help with you know the laptop I’ll you know I’ll see what I can do you know? And at which point he was like you know what he got me a copy of it and then said make this thing your best friend.
And I eventually you know become the sort of chief navigator for him of the of the laptop and uh I also end up learning how to make a copy of it so I could so I become one of the people that is actually able to create more copies of this and distribute more copies of this as well. So, in that time you know as I’m helping him put to, you know we we had the laptop and there’s a ton of information right two hundred fifty gigabytes worth, but we have to we only have about two months before the election happens and we are essentially tryin to create an October surprise.
And so while we’re here while we’re in Manhattan co you know basically extracting and researching the information that’s available on the laptop I called it the Manhattan project cause we were essentially creating a a nuclear political weapon um that’s you know we need ta uh once we had stories that we thought were there [air quotes] which was originally the Ukraine story, then there’s the bigger China story um and then there’s obviously all the lude pictures and all that controversy of like you know his his ah off field active Hunter Biden’s off field activities.
But once we got to the point where we had the stories ready you know working with Steve working with Rudy working with Bernie Kerik ah that’s when we had to figure out you know how are we gonna deploy this information into the ah actual ether you know?
And that’s Steve’s first ah ah ah strategy was let’s go to the Daily Mail which the Daily Mail gets the most clicks online and so that would be the best sort of non-partisan [air quotes] ah avenue to ah publish that story. When the Daily Mail contact that we had basically said no I’m not gonna run with this story that’s when we were faced with a problem where else can we go that would make this story believable? [D: Right] And so now, when that happens I I’m thinking how can we solve this problem, and I remember [unclear] I had and her name is Emma Jo Morris, and at the time Emma Jo Morris was the politics editor at the New York Post. And I had met her previously about a couple years before that while I was a software professional while I was just posting memes on Facebook, we randomly atted each other on Facebook and she’s like I love your memes they’re base they’re esoteric, they’re all this stuff and ah we should meet up and hang out and we immediately became best friends. And she was working on ah Hannity show at the time.
So I turned around to Steve at the time I said hey do you have any problem with publishing in the New York Post? He said no actually I’m open to that I was like look I got a friend named Emma Jo Morris she’s really good, we can trust her why don’t we pitch it to her? And he said are you sure we can trust her. I was like Steve, she’s on our side, we’re good. And that’s when he’s like OK send me her number. I texted Emma like hey Bannon’s about to call you, you need to pick up. And that’s when you know the Steve basically called her and said I got the story of a lifetime. And the rest is history, right?
Now ah it’s just Emma Jo Morris is is is one a my dear dear friends and she’s so brave for even for even going through with this story and you know there was a whole lot of consternation that she went through just in trying to validate the story and just tryin to come to a a state of being able to believe it or not, to put her name on it and publish it through you know one of the oldest newspapers in America. People forget that the New York Post is a two hundred year old institution that was founded by Alexander Hamilton, one of our nation’s founding fathers. [D: Yeah] And so you know people don’t realize that that there was a lot that still went behind validating the whole thing, and Emma Jo Morris and Miranda Devine ah were at the forefront of pushing that through um New York Post. [D: Yeah, so] [6:08 END]
Thanks for the transcript, harpie, this is just so…*face palm*
The casual off-the-cuff reference to criming boggles my mind. “… Ah, there was that issue during 2020, which he was pardoned for. …” Like, no big deal that conspiracy to commit mail fraud and money laundering thing.
One thing I want to point out: the vague reference to location using St. Patrick’s Cathedral-NYC while not citing Rudy Giuliani’s specific address neatly redirects attention from the facts that 1) Kushner’s 666 5th Avenue is just around the corner 0.1 mile from St. Patrick’s, and 2) Trump Tower is about 5 blocks or 0.3 miles from St. Patrick’s. I’m sure it’s all just a coincidence, as is the location of the Grand Havana Room cigar bar in 666 5th Avenue where Manafort met Konstantin Kilimnik in August 2016. It’s just a really small world.
*face palm* for sure…lol! I decided to just type what I heard, and not try to clean it up [punctuation etc.] for legibility. uggg
I particularly liked:
And that’s when you know the Steve basically called her and said I got the story of a lifetime. And the rest is history, right?
OY!
Thanks for catching that typo, zscore. I have heard the term used, but appreciate finally having a definition [of sorts].
lol knowyourmeme has come in handy for research purposes
Quite a fairy tale situation Burra describes, just the chaos magic of sending out memes and voila the opportunity of a lifetime appears out of nowhere.
* based not base
https://knowyourmeme.com/memes/based