Happy Delaware Laptop Day, for Those Who Celebrate
If I read the docket correctly, in a courtroom in Delaware today, Judge Robert Robinson will hear John Paul Mac Isaac’s motion to dismiss and Hunter Biden’s motion for summary judgement in the suit and countersuit over whether JPMI was legally entitled to first snoop through and then start disseminating data from a laptop JPMI claims to believe was dropped off by Hunter Biden, and whether a single statement Hunter Biden made about possibly being hacked that didn’t even name JPMI could be considered defamation.
Because CNN and Politico will also be arguing their motions to dismiss against the blind computer repairman in a follow-on to the same hearing, we might get some press coverage of the hearing. If not, it’s possible that a hearing that has the possibility of roiling 40 months of relentless Murdoch propaganda and both criminal cases against Hunter Biden will go uncovered.
No dick pic sniffer can control their glee that Hunter Biden has a deposition before Congress next week; they don’t seem to give a shit — or, even know — that a hearing that may determine the legal status of the laptop is happening today.
To mark the day, I wanted to return to a few details from Hunter Biden’s reply motion to compel from the other day.
First, on pages 3-4 in the section rebuking David Weiss for calling Keith Ablow’s photo of a photo of a table saw and sawdust a picture of Hunter Biden’s cocaine, the filing includes the text exchange explaining the photo.
2 The message excerpt on the following page is found on the data image provided to Mr. Biden by the prosecution (iPhoneXS_Chat_00000132). There is no Bates stamp for this material as discussed in Mr. Biden’s opening motion. (See Mot. at 18.)
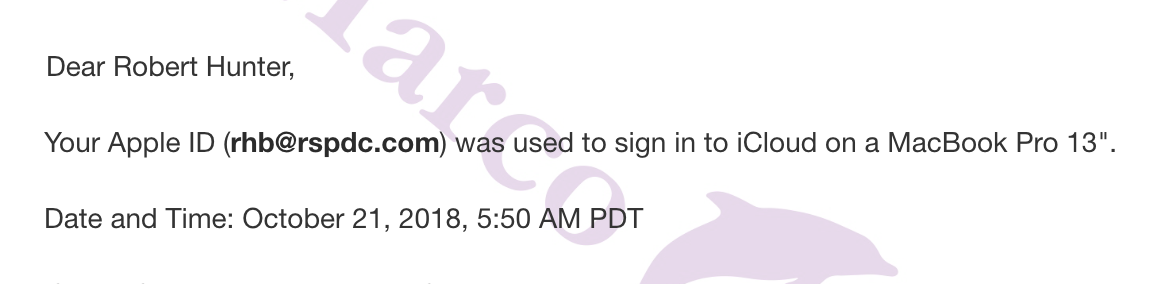
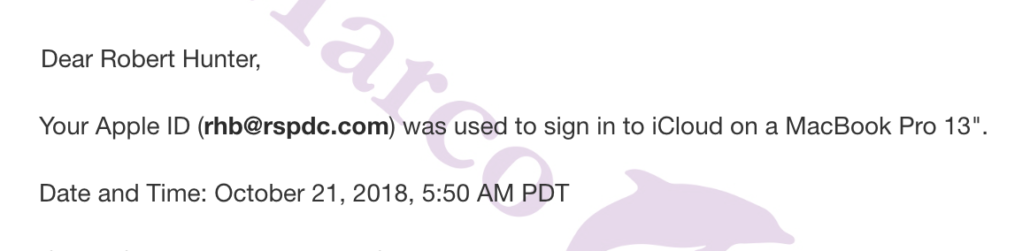
The text appears to come from the iPhone XS that Gus Dimitrelos described as being encrypted on the device, along with a handy password stored right there on the laptop. Readers who have been following my voyage down the Hunter Biden rabbit hole will remember it all started when I read Gary Shapley’s notes indicating that the FBI, too, used a password discovered on the laptop to access the phone.
Laptop — iphone messages were on the hard drive but encrypted they didn’t get those messages until they looked at laptop and found a business card with the password on it so they were able to get into the iphone messages [my emphasis]
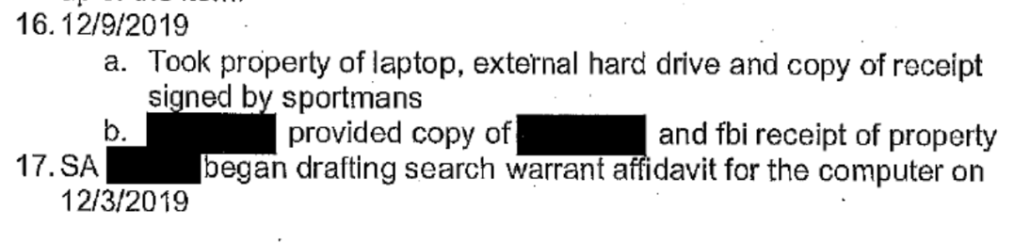
I opined at the time that, while the FBI might get away with accessing this encrypted device without a separate warrant, anyone else who accessed it — as Garrett Ziegler keeps confessing he did — may have committed a CFAA violation. Curiously, though, the FBI did get separate warrants for all the other devices backed up separately. That’s what the July 10, 2020 warrant did: permit the FBI to access four device backups that were already in hand, but that were separate backups.
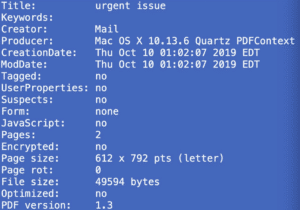
Not this phone, though, the phone on which the photo of the photo of the table saw and sawdust that David Weiss claimed was cocaine might be found.
So on pages 3-4, Abbe Lowell explained that one place you might find Keith Ablow’s photo of the photo of the table saw and sawdust that Weiss misstook for cocaine was on a phone that was encrypted when the FBI first got the laptop.
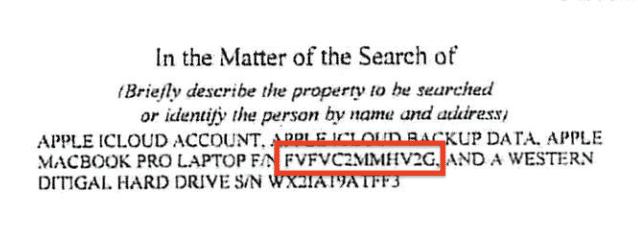
Starting 16 pages later, Lowell returned to his request that prosecutors actually describe where they found particular pieces of evidence. Lowell explained that, yes, while it is true that last August he asked for an exact copy of the laptop, which “will be needed, for example, to challenge the chain of custody, provenance, or likely tampering with the data before it came into the possession of the government,” he also expected that prosecutors would provide some roadmap for where they’ve found things.
The prosecution mixes apples with oranges in charging that Mr. Biden is being “dishonest and misleading” in objecting to what the prosecution contends was a laptop it obtained being produced in the native format that he requested (Opp. at 19), but that is disingenuous. To be sure, Mr. Biden asked for an exact copy of the laptop so it could be examined in the same way in which it was originally found, which is helpful in making a forensic examination of the laptop. That will be needed, for example, to challenge the chain of custody, provenance, or likely tampering with the data before it came into the possession of the government.
However, this motion seeks something more—something traditionally provided in discovery. The crux of Mr. Biden’s complaint here is that the prosecution has not supplemented that production with an index or some other means that would identify which of the vast materials on the laptop the prosecution believes are relevant to this case. The request for the forensic copy is not the same. If the prosecution is claiming that it has not indexed the 220 gigabytes of data (which would be an odd statement), then it needsto say that, and, as with other requests, the dispute will end. If it does have what it normally has with vast amounts of e-data, without providing more, the defense is in a needle in a haystack situation.
Then he noted that the labels Derek Hines used for where investigators found things weren’t all that helpful, because those “titles [] are not even remotely descriptive of what they contain.”
This amount of mixed media data in this tech age is difficult to navigate. The text messages and photos cited by the prosecution in its motions, for example, are difficult to locate. They are “buried” in a convoluted collection of different backup folders and files and are not stored in one streamlined digital backup or application. The messages and photos cited come from “Apple iCloud Backup 01”; “Apple iTunes Backup”; “Apple iCloud Backup 04”; and “iTunes Backup (iPhone 11),” titles that are not even remotely descriptive of what they contain. (See DE 86-1.) For this reason, Mr. Biden requested an index of material (which the prosecution has now clarified it does not have), or Bates stamps for that which it had cited. (Opp. at 19.)
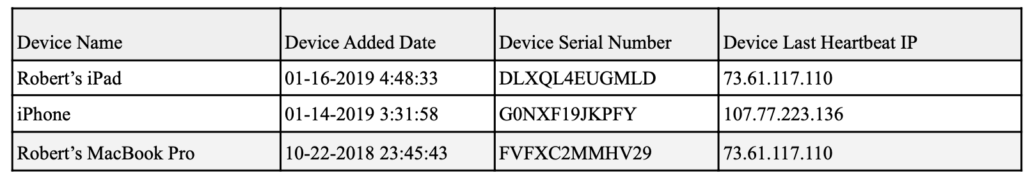
And not just what they contain, I’d add. The label, “iTunes Backup (iPhone 11),” which is where Hines described finding the photo of a photo of a table saw and sawdust almost certainly couldn’t be what Hines described it as — an iPhone 11 — because (as zscoreUSA noted) Apple didn’t announce the iPhone 11 until September 10, 2019, after the laptop was dropped off at JPMI’s shop and after a warrant was served on Apple.
I asked David Weiss’ spox about this, but it was another of a growing stack of questions of mine to which he didn’t even bother responding.
And Abbe Lowell — curse you! — isn’t much more help. Given his response that prosecutors have now fulfilled his request for guidance on where they found things, he must know whether iTunes Backup (iPhone 11) is that iPhone XS that was encrypted on the hard drive, but he’s not telling either.
In his opening motion, Mr. Biden merely requested, following the prosecution’s citation to myriad text messages and photos in its responses, that the prosecution indicate where on the image it provided Mr. Biden could find those referenced materials. (Mot. at 18.) The reason for this request was straightforward at the time: defense counsel could not locate certain of the messages and photos given the broad date ranges used by the prosecution to describe them (e.g., photos taken “Prior to October 12, 2018”; messages sent “prior to his gun purchase”; and photos taken “During November and December 2018”). (DE 86-1.) Mr. Biden appreciates that with the Exhibit filed with its opposition, the prosecution has now fulfilled this part of his request.
But Abbe Lowell did say this: at a meeting in August of last year, the first time when Lowell asked for a complete copy of the laptop (he had to ask again a month later), prosecutors told him that they had “independent sources” for everything helpful to their case.
As to the meeting between Mr. Biden’s counsel and prosecutors in Wilmington on August 29, 2023 (Opp. at 19), Mr. Biden notes that prosecutors indicated, during that meeting, that they possess “independent sources” for any material on the laptop device that would be helpful to the prosecution’s case, presumably referring to material subpoenaed from third parties, such as Apple, Inc. or various cellphone carriers. For this reason, it was curious to Mr. Biden’s counsel when reviewing the prosecution’s response that it elected to cite to and quote from messages and photos contained on the device it possessed (lacking any Bates stamps) rather than from those “independent sources” included in the discovery produced to the defense. That is precisely why Mr. Biden requested the prosecution indicate where on the device he could find the quoted messages and referenced photos, and why he suggested these files were “left buried” among a set of voluminous files that, as made clear now, span multiple iPhone, iTunes, and iCloud backups. (Opp. at 19 (quoting Mot. at 17).) Nevertheless, Mr. Biden appreciates the prosecution providing the folder locations of the messages and photos it referenced. [my emphasis]
Remember: when they said that on August 29, 2023, they still had never obtained a warrant to search the laptop, or any of Hunter’s Apple content, for that matter, for evidence to support the gun crime. They also had not, and still have not, indexed the laptop so they know what is on there and how it got there.
And prosecutors are still saying that everything they need is available on Hunter’s iCloud account. Sort of. In the passage of the response where Hines raised this August 2023 request, he insisted that, “the primary source of evidence in this case is the evidence obtained from the defendant’s Apple iCloud account, which was produced to the defendant in a readily searchable format.”
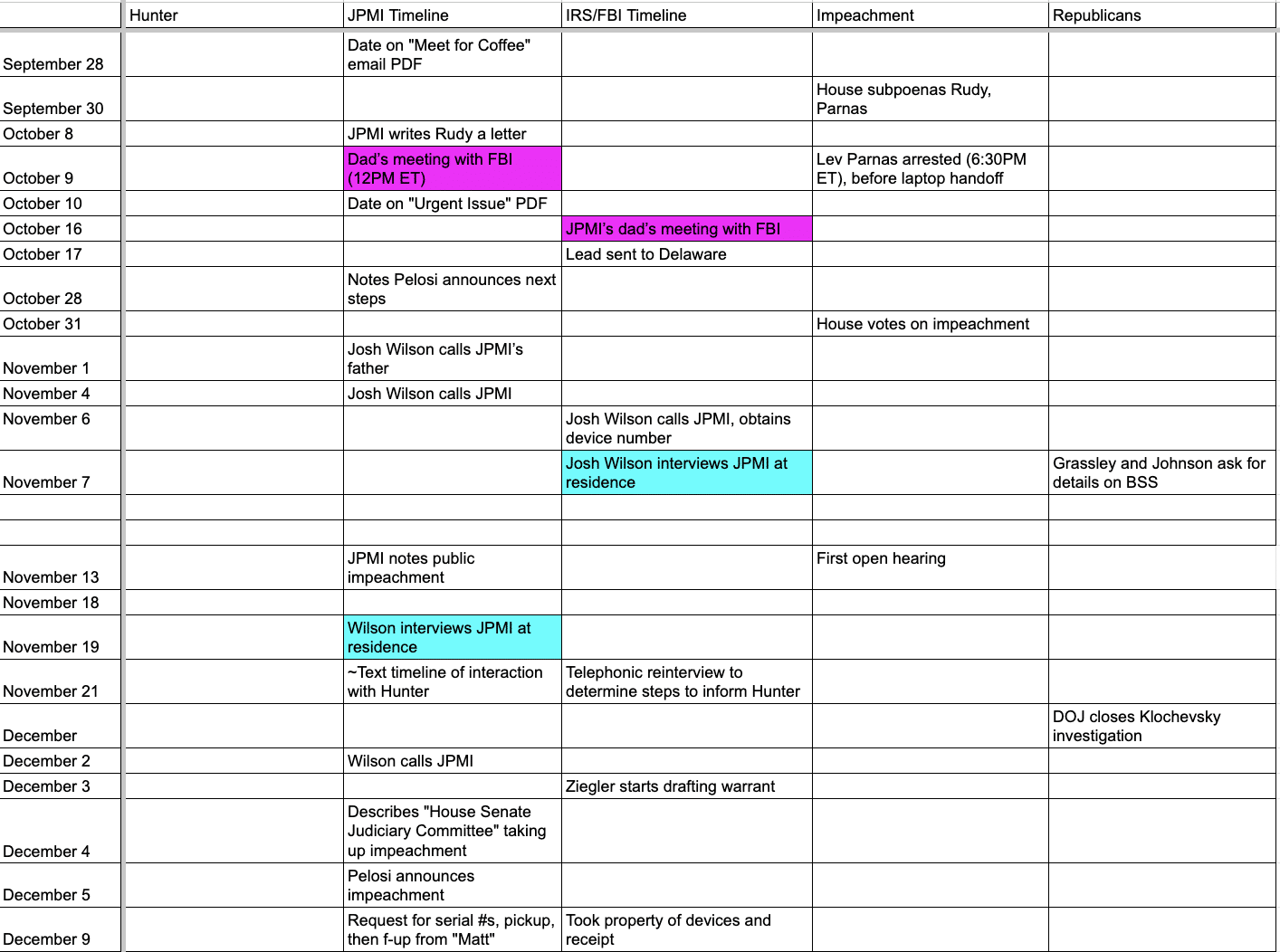
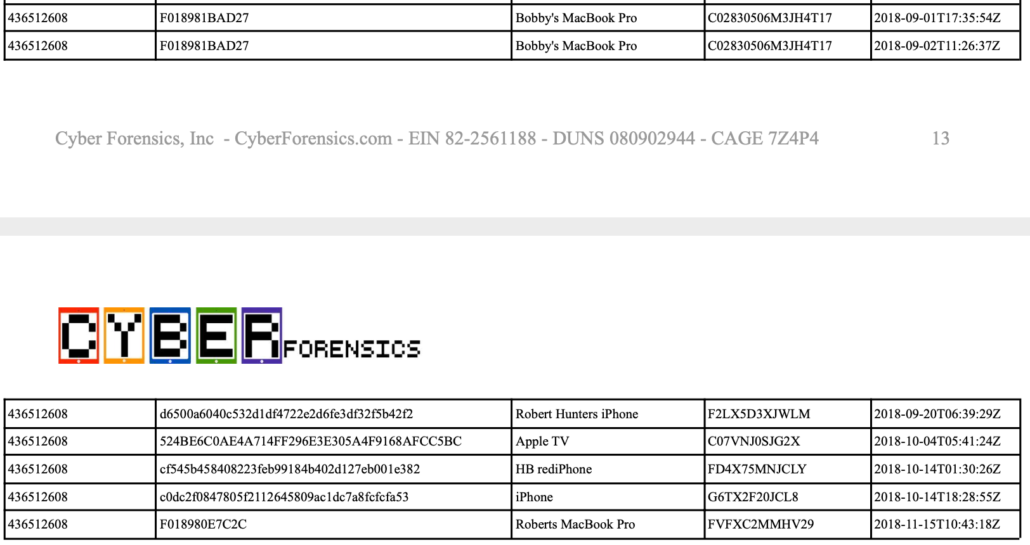
No. No it is not. Here’s my updated table of what Hines included in his exhibit, updated so that the photo of a photo of a table saw and sawdust appears where it temporally belongs, showing that an iPhone XS received a text from Keith Ablow on November 20, 2018, the same day that some anomalous activity was happening with Hunter’s droidhunter account and in a period when an iPad attributed to Hunter was otherwise sending (but with just one exception, not necessarily delivering) a whole bunch of texts about being an addict. I’ve highlighted the records that don’t include hex numbers and aren’t obviously sourced to one of the iCloud backups for dramatic effect. Lowell’s comment seems to confirm that Derek Hines sourced the highlighted records to the laptop.
In addition to the sawdust photo and one of a box that, a new commenter noted is also not from Hunter, it is from Hallie, and even if it indicates drug use, it is much earlier drug use, the most important texts to the government’s case, the ones between Hunter and Hallie while he possessed the gun, appear to be sourced to the laptop.
So in August, at a point when prosecutors had never gotten legal permission to search the laptop for evidence of gun crimes, they nevertheless assured Abbe Lowell that everything they needed was available via verifiable sources. And then this month — just days before a Delaware court may resolve the matter of whether JPMI owned the laptop when, he claims, an FBI agent told his father to lawyer up because, “You may be in possession of something you don’t own” — Hines claimed that, “the primary source of evidence in this case is the evidence obtained from the defendant’s Apple iCloud account, which was produced to the defendant in a readily searchable format.”
And then he sourced the most important texts to his case to the laptop — a source that not only isn’t readily searchable, but is not even indexed.
Happy Delaware laptop day, everyone. Things might start to get interesting.
Update: The docket reflects that Judge Robinson reserved judgment on Hunter Biden’s motion for summary judgment and CNN and Politico’s motions to dismiss.
Update: NBC’s Gary Grumbach did a thread on the hearing. By his description, Hunter Biden will kill the suit against him easily (unsurprisingly, as he didn’t even mention JPMI’s name). But Grumbach didn’t include much of what must be a legal discussion about JPMI’s decision to release the information to Rudy.
Update, from comments: A detailed local report on the hearing, providing the detail that the biggest problem for Hunter’s claims are that he waited too long to sue.
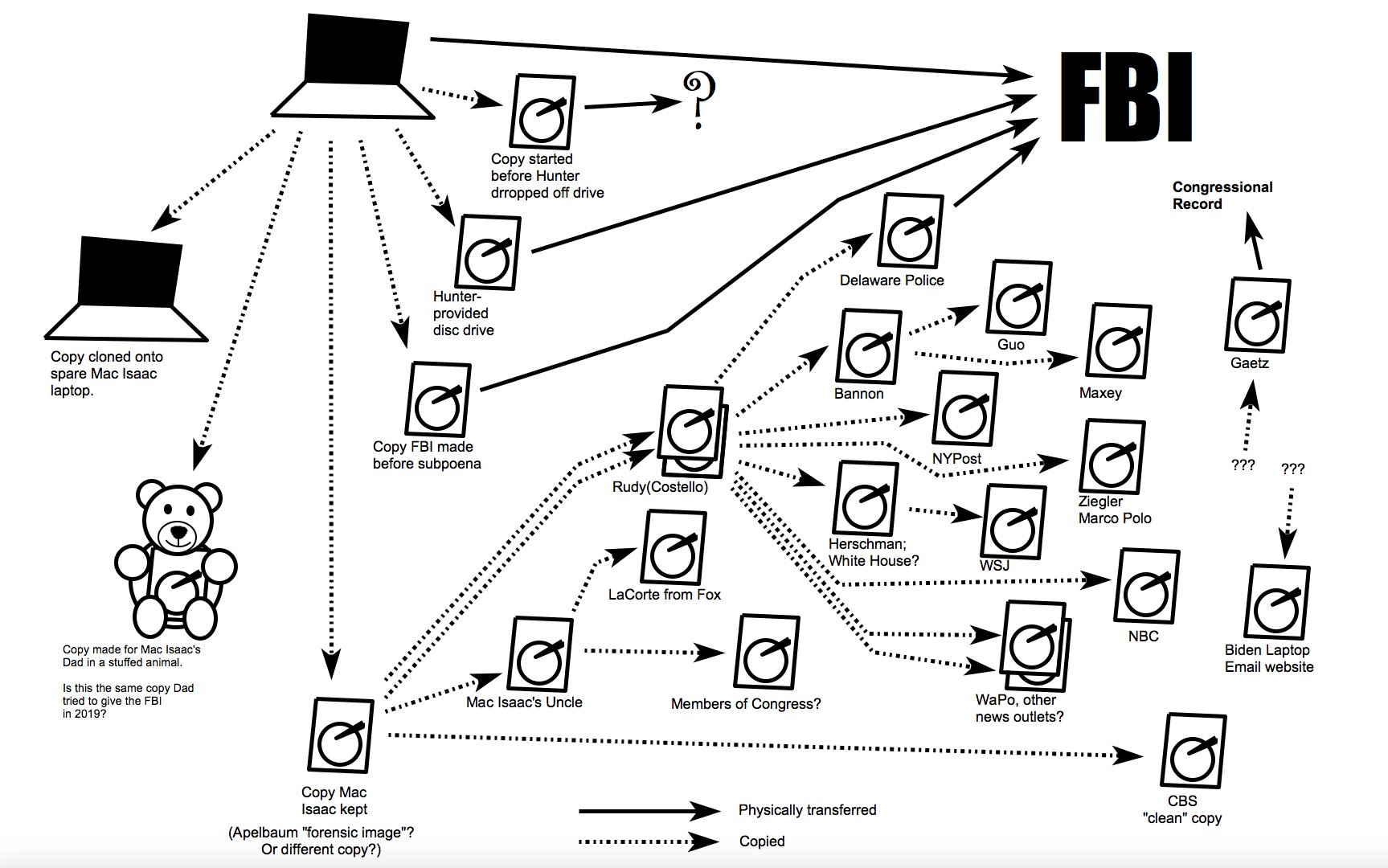
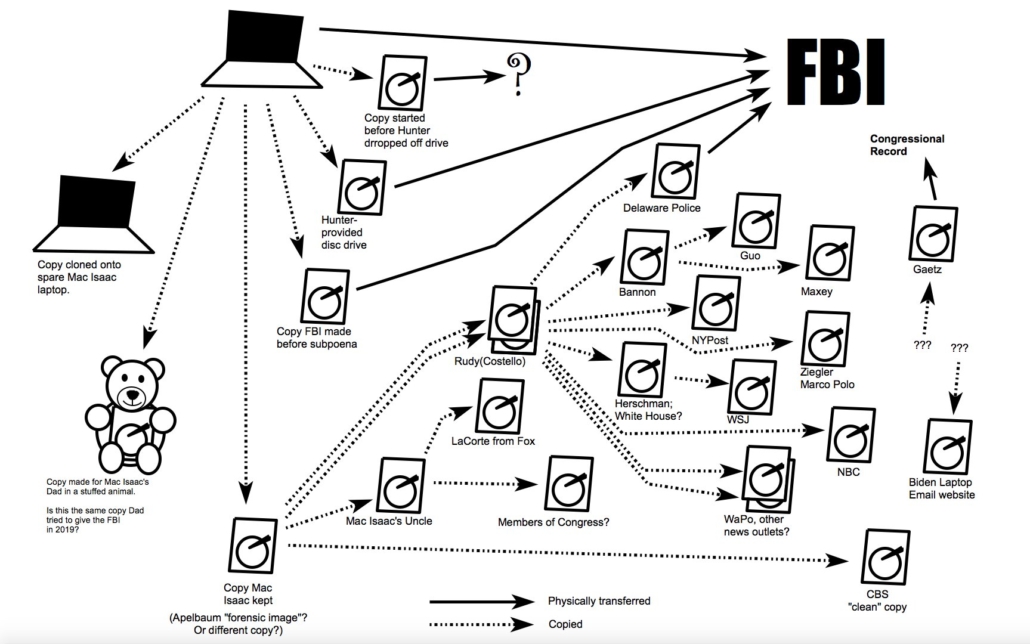
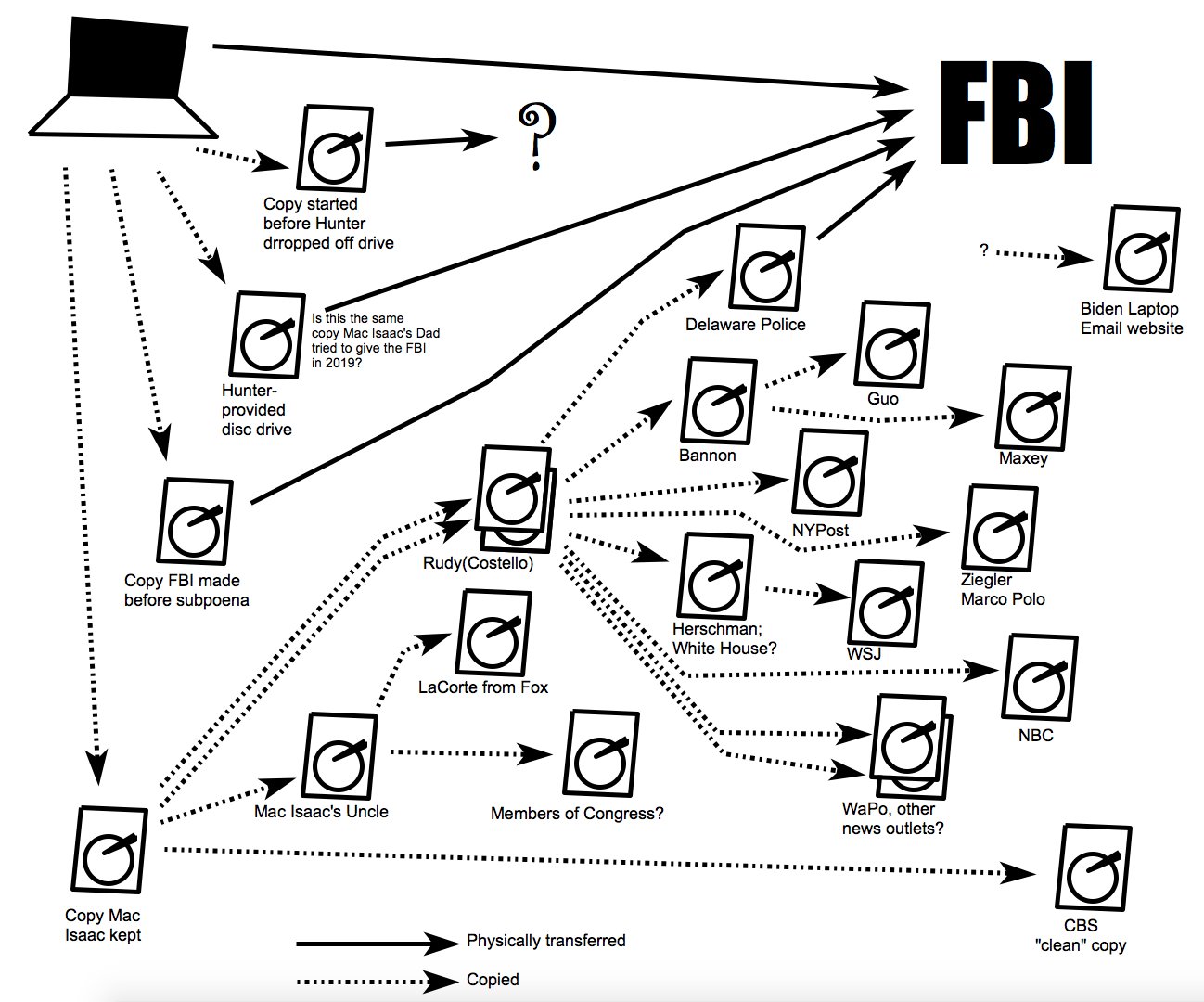
Illustration of all the dissemination implicated in today’s hearing from Thomas Fine.
Click here for Hunter Biden’s Eight Legal Chessboards including links to all filings and schedules for other cases, including the Delaware lawsuit.