FBI Seems Confident in the Granularity of Their Capitol Cell Tower Dumps
In the grand scheme of schemes leading up to the January 6 insurrection, Larry Stackhouse appears to play a minuscule role. Like over a hundred other people, according to his arrest warrant, he walked inside the Capitol and now, weeks after his colleagues reported him to the FBI, he is getting charged with misdemeanor trespassing as a result.
I’m interested in him, though, because of the evidence against him. First, there are the co-workers who, because of their obvious exhaustion with Stackhouse’s vocal support for Donald Trump, might be easy to discredit:
On approximately February 5 and 11, 2021, a witness (“W 1”) was interviewed by law enforcement. WI reported to law enforcement that it was “common knowledge” among those who worked with Larry Stackhouse (“STACKHOUSE”), that STACKHOUSE had entered the Capitol on January 6, 2021. WI stated that STACKHOUSE had called out of work on January 5 and 6, 2021 and that STACKHOUSE had previously been reprimanded at work for displaying political signs and attires in support of former President Trump, which violated their employer’s policies. WI initially stated that STACKHOUSE had been identified by his employer as being associated with “hate groups” from his social media, but later clarified that the employer had no information that STACKHOUSE supported hate groups. Rather, STACKHOUSE was a strong supporter of President Trump who had expressed that support at work in a manner inconsistent with the employer’s policies.
Unlike most referring friends, families, and disgruntled colleagues that serve as witnesses for these affidavits, W1 doesn’t claim to have seen Stackhouse post anything to social media from his trip.
The affidavit does cite social media from Stackhouse. But it’s a picture posted to Telegram from outside the Capitol, which is not a crime.
The affidavit cites “videos and images” from inside the Capitol showing Stackhouse, but the only one included is not all that clear.
The only other piece of evidence substantiating the affidavit — the one I’m interested in — is the claim that Stackhouse’s phone was picked up on an AT&T cell site consistent with being inside the Capitol.
According to records obtained through a search warrant which was served on AT&T on January 6, 2021, in and around the time of the incident, the device associated with cellular telephone number ***-***-6199 was identified as having utilized a cell site consistent with providing service to a geographic area that includes the interior of the U.S. Capitol building.
Given the date, this must be a cell tower dump — the FBI didn’t have their first tip on Stackhouse until a month later (which would also mean the FBI obtained that dump on the day of the attack). And while the FBI uses careful language that a cell tower dump only shows what the service area includes, using it as the third data point to substantiate an otherwise thin arrest warrant suggests they’re pretty confident that it includes only the Capitol (because, again, standing outside is not a crime).
Likewise, the FBI used cell site data (this time, from Verizon) to substantiate an otherwise thin part of the affidavit against someone who does matter to grander schemes: Roberto Minuta, the Oath Keeper who went from providing “security” for Roger Stone to storming the Capitol.
Minuta is charged with three crimes: Obstruction of the vote count (easily substantiated with parts of the larger Oath Keeper conspiracy) obstruction of the investigation for deleting his Facebook account on January 13, and the trespass crime everyone gets charged with.
There are unsurprisingly, given the focused attention to the Oath Keepers’ movements that day, more pictures of Minuta inside or existing the Capitol than of Stackhouse, tied together by the goggles Minuta wore and, in several frames, his Oath Keeper badge.
At least in what the FBI chose to reveal in this affidavit (other filings suggest they have far more collected on him and a range of his associates), the other piece of evidence included proving that Minuta entered the Capitol — rather than yelled at cops outside — is his use of a Verizon cell site consistent with being inside the Capitol.
Eventually, Minuta unlawfully breached the Capitol building itself. According to records obtained through a search warrant, which was served on Verizon, the cellphone associated with XXX-XXX-4147 was identified as having used a cell site consistent with providing service to a geographic area that includes the interior of the United States Capitol building on January 6, 2021, the day of the attack on the Capitol.
Unlike with Stackhouse, the government needs to ensure Minuta’s prosecution is water-tight, as he is a key link between the raid itself and Trump flunkies like Roger Stone, and he and several of the Oath Keeper defendants have already shown a desire to undermine the entire premise of the investigation.
As I have noted elsewhere, the granularity of the cell tower data is a critical factor in assessing the privacy impact of its use in the investigation (reiterating that reported broader cell tower dumps taken in an effort to identify the elusive pipe bomber do pose more concern). And these claims will undoubtedly be tested.
Still, the FBI seems to have confidence that these cell sites were not just serving traffic “consistent with” being inside the Capitol, but probably even “exclusive to” being inside.
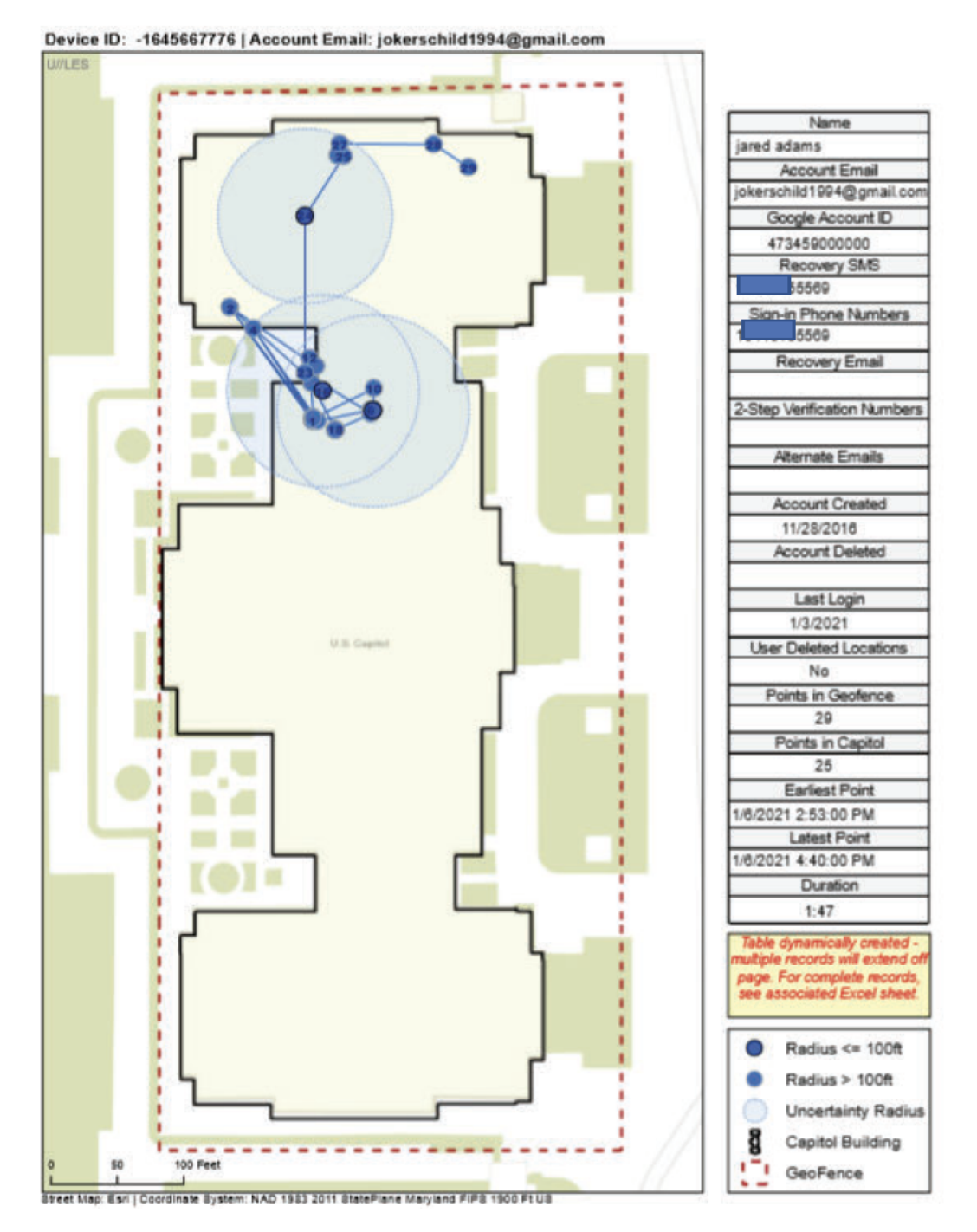
Update: In an arrest affidavit for Jared Adams, arrested for trespass crimes, the FBI conveniently included a map of how the Google GeoFence works, as well as a description of how they moved from Instagram to Adams’ Google account.
First they used his Instagram to get his Gmail account.
Instagram records confirmed that the Instagram account jokerschild1994 is associated with ADAMS, with an e-mail address of [email protected], and T-Mobile phone number ***-***-5569. Records provided by Facebook (username jared.adams.35325) include the same e-mail address and phone number. Records lawfully provided by Google reveal that the mobile device associated with [email protected] belonged to a Google account registered in the name of Jared Hunter ADAMS. The Google account also lists a recovery SMS phone number that matches ***-***5569, the same number as identified above. Information from law enforcement databases indicates that ADAMS lives in Plain City, Ohio. The FBI reviewed ADAMS’ application for an Ohio driver’s license, which contains the same phone number (***-***-5569)). In addition, three managers of apartment complexes where ADAMS either lived or applied for an apartment between 2017 and July 2019 also confirmed his phone number.
Then they used the Google account to geolocate Adams within the specific space of the Capitol (using, as earlier affidavits relying on Google GeoFence have, GPS, WiFi, and Bluetooth).
According to records lawfully obtained from Google, a mobile device associated with [email protected] was present at the U.S. Capitol on January 6, 2021. Google estimates device location using sources including GPS data and information about nearby Wi-Fi access points and Bluetooth beacons. This location data varies in its accuracy, depending on the source(s) of the data. As a result, Google assigns a “maps display radius” for each location data point. Thus, where Google estimates that its location data is accurate to within 10 meters, Google assigns a “maps display radius” of 10 meters to the location data point. Finally, Google reports that its “maps display radius” reflects the actual location of the covered device approximately 68% of the time. In this case, Google location data shows that a device associated with [email protected] was within the U.S. Capitol from approximately 2:53 p.m. until approximately 4:40 p.m. for a total approximate time inside the U.S. Capitol of one hour and 47 minutes. Google records show that the “maps display radius” for this location data was less than 100 feet, which encompasses an area that is partially within the U.S. Capitol Building.
As illustrated in the map below, the listed locations encompass areas that are partially within the U.S. Capitol Building during 2:53 p.m. until 4:40 p.m. Specifically, Google location data shows that a device associated with [email protected] was within the U.S. Capitol at the times and locations shown in the map below (at the locations reflected by each darker blue circle), with the “maps display radius” reflected in the map below (as reflected in a lighter blue ring around each darker blue circle). In addition, as illustrated in the map below, the listed locations were entirely within areas of the U.S. Capitol Grounds which were restricted on January 6, 2021.
This reflects the same 68% confidence as an earlier use of the Geofence.
The FBI then used the GeoFence information to pull security footage showing him in the place where Google said he was. They then got his former roommate to ID him from a photo.






I suspect the tower dump information is good because there are probably picocells all throughout the complex to improve reception in what would be an indoor and highly connected area, which would mean the “towers” dumped are actually miniaturized towers spread throughout the building. It won’t be good enough for single room but is almost certainly good enough for in the building.
And records showing individual devices being handed off to various cells within the complex should be persuasive.
Typo: “inside or existing”
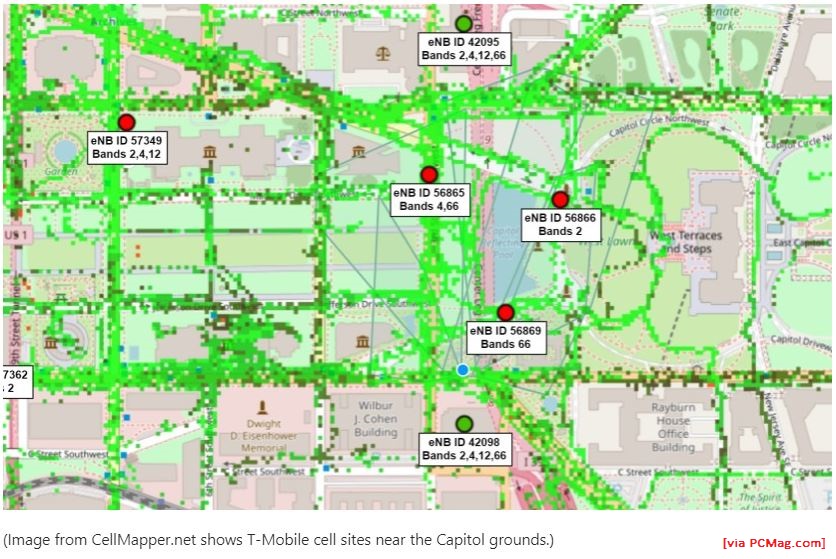
Femtocells, most likely. This graphic from CellMapper via PCMag shows cell phone traffic around the Capitol building from one of the major carriers. Note the lack of traffic in the Capitol itself. Maps showing traffic from the other major carriers show a similar “hole” of traffic in the Capitol building itself.
The question I have is whether the likely femtocells are owned by the Capitol Building complex and Congress, or if they are provided by a carrier under contract. Would change request/subpoena process a bit and how that info could be FOIA’d.
The Capitol has a metal roof over much of the structure which must interfere with some signals. Not certain how well signal moves laterally in/out of the building, but the “hole” in the map suggests there’s something different going on inside the building. If there are femtocells in use AND they’re based on Linux systems, there’s a syslog recording traffic. Can’t say with certainty but it may even record traffic attempting to connect which doesn’t actually go through, and may record different kinds of pings requiring network access — like GPS. I have to believe there’s some sort of authentication process inside the building which could be transparent to guest users (Marcy having been in the Capitol might know more about the way cell phones worked — if users had to agree to TOS to attach as guests to a network inside or no, for example).
Could explain why there’s a high degree of confidence about the data: the government may own it if it’s on government-owned/-operated/-contracted network equipment.
So you’re saying the Capitol is wearing a tin foil hat .. :~)
The Architect of the Capitol is listed as a reference customer for an in-building Distributed Antenna System (https://www.morcom.com/in-building_wireless.html), which might suggest it’s all in-house rather than contracted out.
The metal roof is less relevant than the walls being made of stone: cell signals, particularly 3G and 5G, really don’t like going through thick materials. Hence why there’s (almost certainly) a DAS and cells inside the Capitol, making it trivially easy to snarf IMEIs of everyone there.
I serviced a few picocells back in the day, and I would fully agree with CJ’s thoughts on this.
Yeah, Matt Blaze said as much back in January. But I keep getting pushback from people in the privacy community questioning that, which is nutty.
Who questions Matt Blaze on shit like this?
If it was only using commercial cell tower data, I’m flummoxed how a person would determine a person was INSIDE The Capitol (and not just in the area of). I am dying to see how they figured it out.
“Note that the uncertainties that result from coarse spatial granularity cannot be overcome because of the fixed number and distribution of cell towers, whereas the temporal granularity of individual footprints can be improved. Instead of enforcing subscribers to make more phone calls, different collection methods, such as active pinging, can help reduce the uncertainties between two consecutive footprints” — Zhao, “Cell Towers as Urban Sensors”
Cell phones also have GPS devices inside, so the cell-phone tower data might include the GPS coordinates of the cell phones which were in use. In a modern smartphone the GPS only stops working if you deliberately turn it off.
AL, the Capitol building has its own cell tower, with multiple cellular sites nearby
One cellular base station includes multiple cell sectors. According to CellMapper, a Verizon site just off the West Lawn of the Capitol has 12. Another two blocks south adds eight more. One a few blocks north adds five.
AT&T appears to have six sites near the Capitol grounds with two, three, four, five, and nine cells respectively. Cellmapper shows six T-Mobile sites, with five, five, five, five, nine, and nine, respectively. I also see seven Sprint sites, with eight, six, four, three, three, three, and three, respectively.
https://www.pcmag.com/opinions/why-cell-networks-cut-out-at-the-us-capitol-riot
Holy cow! I had no idea that area was lit up like that! So it sounds at least possible to use analytics to make a convincing portrait of the movement of the insurrectionists.
Given the 100 user-limit per tower cited in the article, for dense urban use, that does not seem to be “lit-up.” I suspect, though, that after 9/11, DC is lit up in more ways that any other town. But I do wonder if that’s as many cell towers as cover all of SE DC, along with the NE, a famously under-served part of the district.
The Capitol has femtocells inside the building, since cell signals don’t like going through big hunks of stone, which is what the building’s made of. If you’re connected to one of those, you’re almost certainly inside the building.
Or some variation on a micro cell, either of which would yield very precise location data.
I’ll add that femtocells basically use low power short range base stations to provide service to a small area. They are making a virtue out of the resulting range limitations – since the maximum number of users in a cell is limited by available radio spectrum, a dense configuration of femtocells can provide service to an area containing many users – this is known as “spectrum reuse” in the engineering community.
The bottom line is that if your cell phone is known to have used a specific femtocell, then your location is also known within a short distance, even without using any of the other possible localization techniques.
Note to future insurrectionists: Remember to disable all communications networks during the earliest stages of the revolt. Also what century you’re living in.
Refer to Luttwak (1968/2016). Honestly, have these people never even done the basic reading for the course?
On reflection, guess I should be grateful for that.
I’m betting there were insurrectionists who knew what they were doing and didn’t have a cell phone (or other electronic device) on their person tracking their every move.
Agreed. Of course, we owe thanks to the insurrectionists taking pictures and videos of other insurrectionists :-)
Too bad most hadn’t already been vaccinated. (microchip. just kidding!)
If only someone could spread “good” conspiracy theories that would produce behavior beneficial to society. For example, what if visiting a website such as Parler or Telegram infected your phone, making it easier for the government to monitor you? Only the microchip in the “Bill Gates vaccine,” designed to identify for the government the meek “followers” who are “not fire breathing Patriots,” will protect you from unwanted government attention! Getting a COVID vaccine is the best way to “blend in with the masses.”
And while we’re at it, what if cigarette butts are secretly impregnated with all the childhood vaccines? The government’s sneaky way of vaccinating people who want their natural immune system to stay strong by avoiding all science scams? Best to collect all those butts off the sidewalks (with gloves to prevent accidental unwanted vaccination!) and put them in trash cans!
[-pdaly. Uggh! My computer has started autocorrecting me!]
[Lol, this is the second time I have fixed yer name, what’s going on here?? – bmaz]
We know, for example, that Ethan Nordean left his cell phone at home, in the drawer, and turned off for his trip to DC. Surely he wasn’t the only one who thought to take that precaution. Of course, he had some other Google device with him, and was tracked using their geofence. And there were pictures.
JVO, you’re certainly correct. We know about walkie-talkies in use, for example, and the videos show people using hand signals and flags to communicate.
Paul Van Riper infamously playing part of “Iran” utterly destroyed US in US Millennium Challenge 2002 wargame through use of analogue communications — bike courier and instructions to suicide bomber cells coded via mosque minaret call to prayer chanting.
With such reliance on digital communications today, a plotter using mildly decent communications security and staying off digital devices probably has good chance of remaining undetected to wreck havoc.
Somehow, what you describe, using old school analogue technology to defeat a vastly more powerful opponent, brings to mind 19 guys with box cutters…
With so many calling for a 9/11 style commission, we can save the money and already write the conclusion: yet another failure to imagine. Malarkey!
I have never believed they only had box cutters. All the hijackers flew from smaller airports to major ones. Each one of those airports had 4 digit coded luggage storage whereby airport employees could have easily left other items for the hijackers to pick up.
I used these storage lockers a great deal prior to 911 to dump my stuff and take transportation into the cities in question.
I never saw definitive proof presented in the 911 Commission report; they just said how and what weapons were brought aboard and people took it as fact.
If you want to make yourself feel vaguely ill, look up and compare the costs of the 9/11 Commission investigation vs. the Whitewater (aka BJgate) “investigation”.
9/11 investigation: $15M
$250K “Whitewater” land deal: $52M
And why on earth did Cheney/Bush refuse to testify under oath, would only testify together and would not allow a transcript of the interview?!? Odd behavior, imho.
But really, what does it say about US priorities when Bill Clinton’s BJ investigation is 3.5 more important than 9/11?
Incompetence, lack of forethought and planning have been hallmarks of the Trump Era.
So is the refrain, next time we will probably face a more formidable adversary.
p.s. I want a bumper sticker that says, “Democracy is Messy. Just like Birth.”
“it’s a picture posted to Telegram from outside the Capitol, which is not a crime.”
Was there ever an order to clear the Capitol Grounds, which would have subjected anyone remaining to arrest?
The ACLU has this layperson’s explainer for protests which notes that law enforcement can order dispersal in riot situations, which was the case here, but it doesn’t get into the details of how enforcement needs to proceed, and I don’t have a good idea if it was practical on 1/6.
https://www.aclu.org/know-your-rights/protesters-rights/
I have to confess that if I were on a jury for someone who was ONLY charged with misdemeanor trespassing, I’d have at least a little sympathy for the defendant. Yes, most of them knew that what they were doing was criminal, but once the first “wave” had plowed through and dismantled the barricades and broken through the Capitol doors, people were more or less marching past a bunch of very restrained police officers to get inside the building. When you’re doing something that you say you don’t realize is criminal, and the police are literally watching you do it without even SAYING anything, much less trying to stop you, it would be hard to tell when you went from “marching” to “trespassing”.
Is that an utter horseshit defense? Yep. You may not know where the line is, but you can be reasonably sure that entering the Capitol itself is trespassing. But if there’s an “intent” clause in the statute (and I have no idea if there is or isn’t), I’d be open to believing that you were far too stupid to realize that what you were doing was a crime.
Raechel Genco was charged for *being on restricted grounds _outside_*. She had also watched as her boyfriend and others forcibly broke through the police barricades (and bf is charged with assaulting an officer; he also went inside. They got onto her case after recognizing her while arresting him at her home). So while her case has some unique characteristics as to knowingly being in a restricted outdoor area, some of the argument they make (they rely also on an “AREA CLOSED” sign) might speak ~ some to your query.
https://extremism.gwu.edu/sites/g/files/zaxdzs2191/f/Raechel%20Genco%20Criminal%20Complaint.pdf
There’s a typo in the Complaint (text says to see Figure 4 below: it’s Figure 3, which they never otherwise enumerated).
Thanks, I think that suggests the kind of case they are bringing against people who were present when barriers were breached.
I’m curious, though, in the aftermath whether police made any attempt to declare the threat to the Capitol and lawmakers had reached the point where anyone remaining on the grounds were required to disperse or face arrest.
My understanding is that there are standards for notifying people present and police can’t simply speak once inaudibly into a bullhorn for it to count, like what happened when Trump walked to Lafayette Square. I don’t know if the police at the Capitol made this attempt, or if they had the means to do it, for that matter.
They gave such loudspeaker warnings at or ca. 6pm for the curfew (to leave the grounds or face arrest); it was by early in the five-o’clock hour that they were using flash-bangs and tear gas to get people off the steps — perhaps verbal warnings were given prior to those tactics being used. As to anything else, not sure.
When the police start defending a barricade, or using flash-bangs and tear gas, I think it’s safe to believe that you could be arrested and tried for entering that area. You might get off on some technicality or other, but a bunch of police pushing people away from a fence should allow an otherwise intelligent person to know that passing that barricade is legally risky.
I read an article soon after the day of the insurrection that said one of the first things the DCMPD did when they came on scene was to announce that it was a restricted area. Of course it was probably not heard by the riotous crowd, but at least those particular t’s were crossed.
Just the 6PM curfew. The handful of people who were arrested that day were mostly curfew violations.
I’m probably naive about this but just based on my own interaction with my smartphones, they do seem to send out enough metadata when they both, ping cell towers and connect with a tower to make calls, stream selfies and such, to accurately geolocate my phone down to almost a room level. I think the triangulation with the various cell towers also helps. If that information is available to the various law enforcement agencies upon subpoena, it would appear that relatively accurate geolocation of individual cell phones is easy to come by.
I worked on a case a few years back involving cells and the software. This was when the “picocells” were still the Next Big Thing.
They can pinpoint off picocells in 3 dimensions to the exact floor the subject phone is on and within well under 5 meters. In some circumstances, within less than one meter.
Don’t forget, too, to the extent some of these offices have wifi-enabled office equipment, like printers and laptops and all that, every one of those pieces of equipment will be linked to the router and the router will be picking up every smartphone, too. Even if the smartphone can’t get access to the network through that router (passwords, n’at), the router knows the phone is there.
The hardest part of this exercise will be for the government’s techies to suss out who’s where when because there are so many phones in the room. It’s not like they’re hunting a single drug dealer in a city block.
Isn’t the wifi connection only made if the phone has that enabled? At least that’s true of my router, although I realize it’s an extremely limited example.
The machines will know the other machines are nearby. For purposes of recovering information for tracking, that’s sufficient.
Another reason to not have a wireless office?
At one point I drove a bucket-truck and worked on outdoor routers, all of which had GPS devices. They were mounted on street lights, electrical poles, etc., and one of the most fascinating things you could do is tell the devices to continuously show their current GPS position to a higher-than-usual number of digits. And the GPS positions were changing constantly; they would change when the wind blew or a big truck drove by. So it’s not ridiculous to imagine that if it’s transmitting enough digits a cellphone in someone’s pocket would reveal their breathing.
The key to making this happen is to order the GPS to show ten or more digits, so instead of LAT 34.234 it shows LAT 34.234120321238. At that point things get really interesting.
So forget a GPS device showing what room you’re in. It will show the observer that you took a deep breath or scratched your nose. All this being said, I don’t think anyone has written a program which interprets GPS signals to this extent, but it’s very possible to track someone to the centimeter.
After thinking about this a little, I wrote an email to Eric Raymond, the current maintainer of the Linux GPSD (that is, the low-level program for GPS sensors.) I’ll be curious what he has to say about the issue.
I heard back from Mr. Raymond, who states that unless you’re using survey-quality GPS the best you’re going to get is 5 meters accuracy, and everything else is noise. Something like breathing or heartbeat is under the wavelength of GPS. So apparently I was misinterpreting what I was seeing when working with those pole-mounted routers.
So my bad.
I’m not sure Mr. Raymond told you everything. Survey-quality GPS can involve a base station (router in this case) which is programmed with it’s exact location. It then compares it’s known location to it’s approximate GPS acquired location and applies that difference to the rover (cell phone) location. The changes you saw in the router location were probably variations in the accuracy of the fix. LAT to 5 places like a typical automobile GPS is about one meter of resolution.
GPS pretty much doesn’t work in buildings, especially massive old multistory buildings like the Capitol so thanks all for the lessons on how to be located on the inside with a phone!
Fascinating, thanks.
Adding: was aware of hyper-acute spatial locationing (dealing w/stationary objects) but never thought of the movement part (implications).
The utility company I worked at used GPS with 8 decimal places: locations to a few centimeters. Which, if you’re trying to find a valve in the dark during a rainstorm, or a fire, or right after a mudflow, is the kind of accuracy you need. Normally, 6 places will put you close enough.
Amazing stuff from EW and commenters. I’m running for my dictionary; “picocells” and “graularity”. BTY, Perhaps”exiting the capital” not “existing”.
Another term … from the Firm!
“Ooh, ooh, ooh, ooh
Well, I’m not uptight
Not unattractive
Turn me on tonight
‘Cause I’m radioactive
Radioactive”
https://youtu.be/3973tfsllqw
Prosecutors Say The Oath Keepers’ Leader Directed Followers During Capitol Riot
“Come to the South Side of the Capitol on steps,” Stewart Rhodes allegedly instructed on Jan. 6.
https://www.buzzfeednews.com/article/kenbensinger/prosecutors-describe-role-oath-keepers-leader
March 9, 2021, at 1:28 a.m.
WaPo has the filing here:
U.S. v Thomas Caldwell government memo opposing release
https://www.washingtonpost.com/context/u-s-v-thomas-caldwell-government-memo-opposing-release/97b39a1e-ee85-417c-831a-2bb036b35b5a/
Page pdf 10/22:
Thanks, y’all!
LOL!
Marcy on twitter 1:54 PM · Mar 9, 2021:
[No offers for taking over cooking yummy dinner duties…though… ;-P ]
LOL I just saw that, too.
From bmaz twitter, Elias/Levine on AZ GOP trying to make the Thursday before election day the postmark deadline for ballots: up until the 2020 elections, in PA the ballot had to be _received_ by 5pm the Friday before election day — then the most restrictive law in the country (we also didn’t have the No Excuse option, either). Can attest that that was an easy way to get disenfranchised should an emergency come up.
Scoundrels, every last one of them.
… trying to push through this draconian nonsense.
I’m not sure this even passes AZ or that Ducey would sign it. That is just speculation, of course.
I hope you’re right, and it would seem like there’s less political will/derring-do to ruin a nice mail ballot program that people have relied on and enjoyed for awhile. But the GOPers in GA, AZ, PA etc, are so rabid to dismantle any progress in voting rights that it can be hard to predict. (Heck, the only thing stopping them here from a complete reversal of our briefly expanded franchise — no excuse mail ballots/ voting before election day, receipt of votes thru election night, etc. — is their lack of veto-proof majority. I mean they were just effectively suing themselves for that which they’d prior happily voted during the bonkers-palooza election suits.)
Trump is a drug…
That would make a good commercial…
“This is your brain.”
***close up of, say, an intact egg***
“This is your brain on Trump.”
***close up of said egg, being smacked with a hammer***
Film it to the tune of Roxy and we’ve got a winner.
Maybe the exploding wet egg-over-light funk will have die-hards and Qanoners alike smacking their heads, “What was I thinking?”
Do we know if investigators cracked an encrypted app, or did someone (someone in custody or an informant) turn over a phone or texts as evidence?
I’ve never used one of these apps, I assume one of its features is to hide the identity of those included on group texts, would that extend to location data when a text was sent or received?
Messages on the app are encrypted end to end. But it’s much easier for the government to hack. What they’re doing here is getting pings off the phone and it’s GPS system locating the phone. Using the app will cause more information to and from the towers. But the information they’re doing here is geolocation of the phone.
[via nycsouthpaw]:
https://twitter.com/alanfeuer/status/1369362027307823109
1:58 PM · Mar 9, 2021
I haven’t found a link for the doc, yet.
Damn, I just missed this when I commented. They didn’t use whatever repeating equipment they had inside the Capitol after all, or they’re using it only to validate to themselves that the *commercial* information they’ve collected is accurate.
This idiot Jared Adams must have had location services on his phone turned on, or there was some other commercial content relying on Google location content phoning home the entire time, giving the FBI an opportunity to use Google location info. Image here from CitizenLab’s John Scott-Railton’s tweet thread:
It’s labeled a geofence here, but I wonder who decided to call it that? Does Google have an area it defines commercially as a geofenced zone? or does the Capitol have a geofence defined by either its internal network or its network provider?
Rayne,
I’m not sure how the term got defined here, but ‘geofence’ is used elsewhere as well. One area is in autonomous vehicles such as drones where the flight control software has GPS defined areas that are described as ‘no fly’.
An example would be a commercial airport. So if a pilot wanted to fly a drone equipped with the flight control into airport airspace, the software would sense the ‘fence’ and not proceed.
Thanks, Fran. I know what a geofence is — the question is who/what defined the one on the map? Who/what prevented the cell traffic inside the Capitol from showing up on CellMapper?
[Answering here rather than below.]
The FBI would have defined the region on the map in their request to Google; see e.g. https://nlsblog.org/2021/01/08/google-data-and-geofence-warrant-process/. Presumably those specific boundaries were chosen to tightly enclose the building, making it really easy to demonstrate that someone was inside it or within the enclosing restricted area, and therefore presumably breaking the law on entering either region without authorization; choosing a larger zone would complicate that.
The reason someone running CellMapper outside the Capitol can’t see the femtocells inside is simply that the building itself prevents the low-power signal from exiting — which is why they’re needed in the first place to get signal inside. Same reason you can’t see any inside the Pentagon (which almost certainly has them) or most other large buildings you take a look at, etc. (For a counterexample where you can see one, take a look at Building 41 at Google’s headquarters, which apparently has an AT&T femtocell inside — presumably someone had CellMapper running while at the office.)
If someone was running CellMapper while inside the Capitol, then they’d be visible; it’s just nobody has done it. There’s nothing special about the Capitol itself in this respect.
Which gets to my point that there’s other network traffic data from *inside* the Capitol building. Whatever ran through the femtocells/picocells must have been captured on a syslog somewhere — whose log is it? Does that explain the confidence the FBI has, a secondary source confirming the location of the perps by their IMEI and metadata, while the information they’re sharing with the public is the commercially available material which the public should expect their social media/ISPs to obtain?
FBI is pointedly avoiding discussion of Capitol building networks, whether data or video surveillance.
There’s at least one person on LinkedIn whose job includes running 4G LTE and enterprise wi-fi networks for the Architect of the Capitol. That suggests they’re running it in-house now (the House, at least, used to contract out: https://www.politico.com/story/2007/02/house-ends-cell-phone-licensing-deal-002910). If so, Congress would have the logs and presumably handed them to the FBI to do their thing, and everyone who brought their phone is busted … even if the feds haven’t got around to actually knocking on their doors yet.
In the alternative, if it’s contracted out, either Congress tells the provider to give the logs or the FBI does paperwork to get them, which might take a competent agent … maybe an hour to write? Either way, same result.
On the third hand, if it’s actually run by the telcos, it turns into doing the same paperwork they do routinely for tower dumps, so … a couple hours?
If I were running the Capitol’s wi-fi network, I don’t know if I’d bother collecting MAC addresses from base stations (is there even public wi-fi in the building?); while it might be interesting for intrusion detection, it’s probably better to treat it as an untrusted network rather than granting any privileges to devices on it, even for a secured “enterprise” network. If there are logs, they’re likely less useful than the cell ones anyways….
It’s not clear to me that the question of who actually owns & runs the Capitol’s cell network is especially interesting for the investigation (though as you noted, advertising might be a very different story): if they’re at all competent, the FBI got the records that evening or the next day and it’s just a question of whether they needed to get a judge to sign for them. I’d expect they’re going to try to keep it as quiet as possible: why confirm anything about your capabilities if you can readily parallel-construct? Same story with hi-def video.
… though now that I think about it, the nice thing about wi-fi is that you could have better logs available than with the cell network: think DNS lookups and IP traffic flows, none of which you’d get for the cell traffic. Again, would I want to log any of this from an intentionally-open wi-fi network with lots of transient visitors that just dumps all the traffic onto the public internet? Meh.
On the enterprise ones, though? Maaaaybe. (Though in principle, none of the unauthorized attendees should be able to get on those in the first place….)
“Geofence” is just a generic industry term for a set of coordinates enclosing a space; in this case, that box, which would have been specified by the feds in the order they sent to Google to get the data. It doesn’t have a deeper meaning here.
See my reply to Fran above. It’s not the word, it’s what is labeled, why it’s labeled, who/what labeled it.
New footage of BOMB suspect:
FBI releases new images of DC pipe bomb suspect
A reward for information leading to the arrest of a suspect stands at $100,000.
https://abcnews.go.com/Politics/fbi-releases-images-dc-pipe-bomb-suspect/story?id=76341036
March 9, 2021, 3:00 PM
https://www.fbi.gov/wanted/seeking-info/suspected-pipe-bombs-in-washington-dc
That’s super interesting. They’re wearing glasses. Any idea what (possible landmarks/tall clock?) they are craning up at (or pretending to for the sake of that coming pedestrian)?
In the new RNC part of the clip, their shoulders look broader. But all the stretching suggests strained/weak (thin) back muscles, possibly peeved by the backpack and or too-big shoes (some odd prancing at times, like an ill-fit).
Just wanted to share some camera facts. I once put a camera in the mouth of a furnace (@3000 F),honest, it was an off the shelf $400.00 unit. The factory rep told me I can see a man on the sun in a row boat! The point being this, under less demanding conditions you can see the persons facial features with there back to a window looking in the lens and the full sun blasting in the window behind them! The clarity was stunning and I got the info I needed for the customer.
But wait, there’s more! I had a high end FLIR unit (night vision) stolen costing $50,000.00. It was a backup to a system and it could do some incredible things in very low light conditions.
If backpack boy/girl was anywhere near a high end system (gov), they can read the label on a garment.
You are aware that your tool exploits could make for a TV show plot-point/ stabilizing feature, right. Like Macguyver- meets- Columbo or something.
I noticed they (gov) did give us a smidge better resolution in some of the images. I’ll assume they’re keeping the good stuff for court.
Right you are. Gov is holding back, that Im sure. What do you get when you put the internet, Big data, fibre optics, cameras, and SAS in bag and shake it up?
I dont know but jeeesh it scares me.
Btw, my nick name at work was GUS. Electrical term for “general use switch”. :)
ahhh, SAS. Remember when they kept teasing an IPO [don’t threaten me with a no-lose opportunity] — which never came.
Just look at them now … [counts fictitious pension accrued from tiny initial investment]
To me it almost looks like these are two different people. The RNC person looks taller, leaner and yes, seems to have broader shoulders. The person in the first vid looks a little more dumpy around the middle — maybe the same person wearing more clothes under that hoodie? And what’s with the shoes? That person looks like s/he is walking in high heels, which we know isn’t the case. Shoes too big?
Yes! That’s the first thing that came to mind, too, what I was getting at with “prancing” — looks like someone walking in high heels who’s not used to it, so —> ? shoes too big, ? +/- lifts; or like how a dog/cat walks when trying to get something off its paws (see rosalind below). (I felt there was something about the shoes looking too big/clunky in the earlier vids, too). That would contribute to back pain (all the stretching).
Interesting suggestion about a layer change. Maybe they were even wearing one of those ‘fat pads’ used in film/theater around the middle towards disguise. Just changing shoes (attachments), clothes, unloading the bombs, having a steeled presence can change gait and habitus so much.
I still want to know what they are (pretending to) look up at (also could be looking for a signal/person in a two-story residence). [ETA: had assumed they were looking at some landmark such that it was socially acceptable for that pedestrian to see them do that, otherwise it seems weird to make such a show of doing so. Maybe the pedestrian wasn’t visible then.]
One other thing: they kept fussing at their hair- / hoodie-line / glasses* arms area in a way that reminded me of how a woman or someone with longer hair tucks in fussy strands. I suppose they could have had on a wig or cap. (Can’t get the video to replay to check, but this was around the time the pedestrian had passed, maybe they became self-conscious.)
*I saw the glint of eye coverings — could instead be goggles.
There were reports the bomber had attached ice gripper sole attachments like Yak Track to the shoes to avoid leaving shoe prints. The story being that they were walking on like studded soles.
Not knowing how those attachments would affect someone’s gait (northern California girl here) — this makes sense, actually.
To me it looked like they were wearing sport shoes unlaced/loosely laced with the tongues up — they walked ‘funny’ as if they were trying to keep too-loose shoes on, perhaps shoes that weren’t their own but borrowed.
Those look almost like “platform” sneakers. Harder to walk in, tend to change your gait. They’d make you look more feminine when walking.
greengiant & PJ: this issue with the shoes/appurtenances is like waiting through a forever-commercial in a bad episode of Forensic Files (you know the details are coming… let’s get on with them) Certainly these mysteries will be solved, and hopefully on a much faster-than-Ted K-case timeline (else- Surveillance State — What is it Good For?).
Interesting… when I thought about it, it looked like the person was taking something off under his/her/their hoodie. Thus, the shrugging shoulders.
Looked like adjusting bra straps.
Just dropping in cold here, with something kind of nutty that occurred to me while watching the video…what if the DNC person had another backpack [worn backwards] under their jacket?
someone on twitter raised an interesting possibility re. the shoes. he suggested in the first video the suspect is wearing “walkable ice skate guards” (see below), it’s like a chunk of plastic that attaches over the skate and is awkward to walk in. then in the second video the suspect is sitting on a bench and looks to be changing shoes. in the next video the suspect is walking more normally and seems to have on shoes that are lower to the ground.
https://i5.walmartimages.com/asr/391d9232-142e-43ae-ac54-d3782c9769bc_1.b2739f9ef8fb79a36c77dda94bc674ea.jpeg
I wonder why the FBI does not give an approximate height for this person. The stone fence in front of the first house on South Capitol St. where he/she pauses could be used to estimate height. Then when he/she moves on, there is a very slight stumble near the beginning of the first concrete steps, before moving on to the second house. Is this because the shoes are too large (as you speculated they might be, Eureka) or because the person is awkward or nervous? Or maybe the sidewalk is uneven or the backpack throws them off balance. I wonder what they were doing with their hands after they set the backpack down. Did they put on or, maybe, adjust glasses?
At the end of the clip, near the Capitol Hill club, there is a metal post with a street sign. That would be an easy way to determine an approximate height.
Tracy Lynn (along with the person straining to look for something/someone, maybe a signal — if that was not a show) has me wondering now if there was more than one person involved, maybe a hand-off. Since the FBI states the model of shoe*, they could give an estimated height like you say with landmarks, and they do not. Are there multiple estimates on file …
*as someone pointed out several weeks ago on twitter, the shoe models (as worn versus as identified) don’t quite match — could be a knockoff model (very popular in some parts) or a team version.
Or it could be someone who already has a case file. And the FBI doesn’t want to provide leading information. They might prefer people to provide information independent of that.
Based on the info from OpenCellID (here: https://opencellid.org/#zoom=18&lat=38.889746&lon=-77.00988 ), geolocation inside the Capitol is going to be very precise. There are several cell sites within the Capitol. Depending on how they are placed, they may even be able to determine what floor people were on and when.
Yes.
What I said upthread: they can pinpoint in three dimensions to the exact floor the phone is on and, in the x-y plane, to within a few meters. In some instances, depending on the location and equipment, to within one meter or less.
That is not “new” tech – it’s at least one, maybe two, generations old. It’s just the density of the coverage that will give that fine-grained resolution.
4 UMTS and 1 LTE inside the building, none newer than 2018 — very interesting. Wonder why these don’t show up on the CellMapper site? Thanks for sharing that.
I’ve done some work with online marketing and what can be done nowadays. It’s pretty frightening. You can do geo-fencing advertising that’s accurate to a level that’s hard to believe. A Toyota dealership can send ads, discounts and enticements to people that are across the street at the Honda dealership and keep sending ads for a number of days.
If you want to advertise to a convention, buying space, having a booth, buying space in the convention program can cost quite a lot of money, not to mention staying at the hotel. You can do push advertising to everyone that is at the convention center for the days of the conference and not have to be a vendor.
If you’re a bail bondsmen, you can send push ads to people waiting in the lobby of the prison. And yes, you can target just the lobby and entrance where visitors would be and not the rest of the prison.
Heck, ambulance chasers (ouch) can send push ads to people in the ER and ER waiting room along with follow on ads for a number of days. They can do push ads when the injured people are at physical therapy offices.
I was talking to someone who handled the national campaign for a tire company. He said they learned that if the person lived within 3 miles of the tire store, they were going to be coming in, whether they had a coupon or not. So they offered coupons and discounts to people that were doing searches for new tires, but not if they were within three miles of a store.
Digitally they can pinpoint with an amazing sense of accuracy.
You’re grasping the implications, though, about the Capitol? That specific audiences like members of Congress and/or staffers can be reached with highly-targeted adverts which may promote certain viewpoints about content under debate inside the Capitol building?
That’s a good point. I was mainly saying the technology exists to pinpoint *exactly* where phone users are, down to a specific room. Thus indicating the granularity that the FBI can use with knowing the location of the phones.
Disturbs me the potential exists not only to influence debate and votes outside of the public’s view while inside the Capitol, but that a specific audience could be targeted and followed using geofencing and ad tech if a 3rd party bought carefully worked adverts.
Why bother with tweeting locations as Rep. Boebert did when one can find specific members of Congress by their phone’s response to ad tech?
That is somewhat disturbing. They can’t push information at them, but they can do banner ads they’ll see and the wording of the banner ads can influence even if they don’t click on it.
Of course, that implies that legislators votes can be changed by logic or reason…
A more effective tack is targeting staffers who actually do the research and drafting.
Depending on if they’re using Gmail for personal stuff, information might actually be pushed at them directly into their mail box.
If they surf specific news sites regularly like OAN/Breitbart/Fox, whatever ads appear on those sites could contain influence material which isn’t strictly marketing content. What I don’t know is how the beacons used by ad tech might convey info back to whomever/whatever is at the other end.
I killed all weather apps because I know they were obtaining my location even with Google Location shut off, so Google isn’t the only source — just relevant here because of this one particular complaint against alleged insurrection participant Jared Adams.
The nearest cellphone tower is perfectly good location for a weather app. Simply knowing which city you’re in is probably good enough.
But the weather app sells the data, the ad buyer goes to Google and asks for all persons within X distance of that tower, then Google finds the person depending on what services they have turned on — and it happens seamlessly, in real time. That’s how I figured out it was the weather app selling data. I turned off all location into, stripped off all my apps, reloaded them one by one and watched at what point Google ad content started getting too close to me.
Bingo, a weather app must have been selling my data, and a local automotive service company located less than a mile away must have used data through them to buy Google Ads to find a potential customer.
It’s not just weather apps, either, sometimes not even apps; ex. most DIY folks have no idea that ACE Hardware probably makes money selling data obtained through persistent cookies they park on devices when they visit their website. Fuckers. I won’t buy anything from them ever again.
In the case of Jared Adams, I’m surprised they didn’t use more information from Instagram, a wholly owned subsidiary of Facebook, both of which may park persistent cookies and web beacons on people’s devices.
The 68% confidence is presumably assuming a normal distribution, with +/- 1 standard deviation.
Acting United States Attorney Jennifer Arbittier Williams announced an initiative created under her auspices aimed at anticipating and preventing mass violence, the Threat Intervention and Prevention (TIP) Network. It involves a Core Team of threat-assessment experts from multiple law enforcement agencies available to train, apprise, and consult-on-demand Community Team members (businesses, schools, medical facilities, community and religious groups, etc.) within EDPA. While I’m unaware of (new) similar programs elsewhere, this one’s timely as relates to many discussions here. As Williams writes, people generally don’t “snap” — there are signs. Signs include more knowable precipitating events such as a firing or — unmentioned, which I find troubling as it’s the most well-known danger, and perhaps our biggest public health problem — a woman leaving a violent partner or related domestic violence.
Via flyer linked at DOJ:
On one hand this is law enforcement expanding into social services. On the other, our society might need programs like this because of all the fucking gungloriousness.
Peruse various facets of the DV-mass violence problem here (sadly, this is a pre-filled search suggestion):
https://duckduckgo.com/?q=domestic+violence+mass+shooter
And to be clear, dyadic violence or individual women’s / family members’ deaths are the proportionate horrors that must be addressed beyond the fact that DV perpetration history predicts mass violence and that mass violence events are domestic violence events half or more of the time.
*stated the prediction (sensu statistical) backwards; replace with “is associated with”
The latest mass violence suspect in the news was arrested today in STL, and the case is a two-fer warning as to the eminence of domestic violence _and_ modern American hyper-neolocality/mobility — thus a boundary-defying problem as well. Sean Lannon is suspected of beating to death his friend in NJ while being wanted in connection with the deaths of four others in New Mexico, including his ex-wife.
Looking at the original topic, and then the stream of information in the comments, a few things struck me.
Somebody in the insurrection world is taking notes here. We (the U.S.) can’t *not* prosecute, so the investigative steps will by laid out in public. A lot of unforced errors were committed by the primary actors. Those were compounded by errors made by “friendly forces” (individuals / groups who were sympathetic to the “cause” but weren’t under the operational control or coordination of the primaries). Like any other evolutionary process, the life forms caught up in this event will tend to either wither away or will become stronger and smarter. Some of the folks deeply compartmentalized in that world are not at all surprised by the evidence that was so freely given up…They’ll be listened to now.
Part of the above will be a tightening down on the technology used during future domestic insurrection / demonstration operations. The wireless carriers’ business models depend on your phone autonomously and continuously maintaining “situational awareness”. If cel phones are used in the future, expect to see more burner phones in play, with minimal linkage to email – and that likely to be through a series of shell email accounts. Even traditional U.S. adversaries (and “friends”) will be watching this process and taking notes. [And anticipating remarks here: If you have the resources, you ALWAYS review / analyze the real world operations of others. If everything that you find out is stuff that you already knew, then good on you.]
This also illustrates the importance of recent EW topics discussing the apparent complacency or inappropriateness of actions taken by some elements of the FBI and DHS with regard to domestic terrorism and the abundance of pre-event open-source indicators and warnings. This stuff is only going to get more difficult as the bad people become fewer, but smarter.
And on a personal note: It continues to be a pain in the backside to periodically go through my phone and tablet to review which apps are trying to track my location. I wonder if broader public awareness of the level to which their location and demographics are being monetized will have any play in discussions about privacy in a world of Facebook, Google, and their ilk.
I think you’re exactly right. There will be a splintering of the extremist groups with the weekend warriors people that are playing at being hardcore decide they really don’t want to go to jail, while the dedicated ones go underground, becoming more serious with greater operational security, integrating everything that was learned. They’ll become a smaller group that is more dangerous and more difficult to detect.
Fortunately, they’ll become suspicious of each other and they’ll tear each other apart with paranoia, shrinking their size even further. What’s left will be truly dangerous.
Amazing work and analysis on the telemetry and physics of cell phone traffic in and around the Capitol on January 6th by EW and contributors!
Marcy:
John Scott-Railton notes that PERSON FIVE in the Joshua JAMES complaint
looks like it may be MINUTA.
JAMES: https://courtlistener.com/recap/gov.uscourts.dcd.228471/gov.uscourts.dcd.228471.1.1.pdf
The photo on page 12 of the JAMES complaint, linked above, is similar to the photo on page 8 of the MINUTA complaint:
https://extremism.gwu.edu/sites/g/files/zaxdzs2191/f/Roberto%20Minuta%20Criminal%20Complaint%20and%20Affidavit_Redacted.pdf
Sorry…here’s the Scott-Railton link:
https://twitter.com/jsrailton/status/1369659870383902723
As Scott-Railton notes in that thread, there were lots of phone calls between JAMES and PERSON FIVE,
AND also, some between JAMES and Kelly MEGGS.
…and just now, Marcy retweeted Dan Friedman of Mother Jones:
https://twitter.com/dfriedman33/status/1369706391460528137
12:47 PM · Mar 10, 2021
I wonder how they’ll deal with the inevitable defense: I didn’t go inside, I just loaned my phone to someone who did.
That’s assuming, of course, that they’re not captured in photos or video in the building.