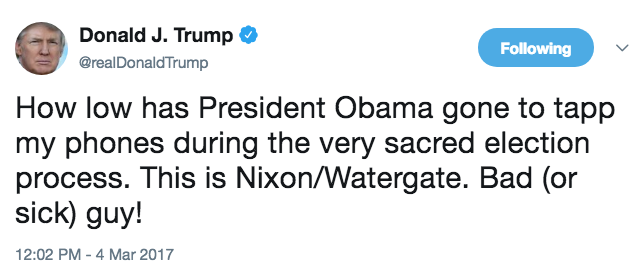
On the TS Ellis Show and the Lies about Lying
The last words in the transcript of the hearing held Friday in Paul Manafort’s Eastern District of Virginia bank fraud and tax crime case go like this:
THE COURT: Mr. Asonye, I’m glad to see you here.
MR. ASONYE: I’m glad to see you as well, Your Honor.
Uzo Asonye is an Assistant US Attorney in EDVA who has prosecuted fraud cases before TS Ellis. Mueller’s team added Asonye to the EDVA case at the suggestion of Ellis. Ellis returned to his pleasure that Mueller had heeded his suggestion several other times over the course of the hearing, starting from his first comment after Michael Dreeben introduced himself.
THE COURT: Okay. And, Mr. Asonye, I’m glad to see you here. I indicated that the special counsel should have local counsel, and that’s you.
[snip]
MR. DREEBEN: The second point here is that we are within the Department of Justice. To the extent that Mr. Manafort is suggesting that we’re analogous to the independent counsels that operated under the old statute, that’s not right. Our indictment was reviewed and approved by the Tax Division, by the National Security Division. We operate within a framework of the Department of Justice. We’re not different from the U.S. Attorney’s Office in that respect. We’re all part of the same Department of Justice.
THE COURT: You resisted my suggestion to have someone here, and Mr. Asonye showed up. When did you ask Mr. Asonye to join you?
[snip]
MR. DREEBEN: Thank you, Your Honor. We took your admonition to heart, and we are very happy to have Mr. Asonye join us.
THE COURT: Good. I think that’s important for communications as well. Plus, you never know. If you have to try this case, you will have to try it before me. Mr. Asonye has some experience here. Is that right, Mr. Asonye?
MR. ASONYE: Yes, Your Honor.
THE COURT: And before me as well.
MR. ASONYE: Yes, Your Honor.
THE COURT: So he can tell you some interesting things.
[snip]
THE COURT: Of course, the difference is that if you did assign it to the Eastern District of Virginia, it wouldn’t come, Mr. Asonye, with a $10 million budget; would it?
You wouldn’t know that though, because most of the reports from the hearing have focused on exchanges like this, from Fox News:
Mueller’s team says its authorities are laid out in documents including the August 2017 scope memo – and that some powers are actually secret because they involve ongoing investigations and national security matters that cannot be publicly disclosed.
Ellis seemed amused and not persuaded.
He summed up the argument of the Special Counsel’s Office as, “We said this was what [the] investigation was about, but we are not bound by it and we were lying.”
He referenced the common exclamation from NFL announcers, saying: “C’mon man!” [my emphasis]
To be sure, Ellis was undeniably confrontational with Dreeben, in this and several other exchanges. But the Fox line, which it picked up from early reports, tells a distorted view of the hearing (even ignoring Ellis’ well known schtick of being confrontational in the court room).
First, the Fox representation is factually inaccurate in two ways. Here’s the transcript of the exchange Fox claims to have quoted directly.
DREEBEN: So it is not really appropriate to assume that the (b)(i) description is the factual statement that the regulations contemplate.
THE COURT: Well, I understand your argument, but let me characterize it and see if you find it as satisfying as you appear to indicate that you think it is: We said this is what the investigation was about. But we’re not going to be bound by it, and we weren’t really telling the truth in that May 17 letter.
I don’t watch pro football, but I used to enjoy the program that came beforehand where a bunch of players would get on and essentially make fun of everybody. But they would put on some ridiculous thing, and then they would all say in a chorus, Come on, man. [my emphasis]
Ellis was referring, explicitly, to the May 17 letter appointing Robert Mueller as special counsel and not, as Fox suggests, the August 2 Rosenstein memo that lays out what the Deputy Attorney General had included in Mueller’s scope by that point in time. The distinction is significant for the matter before the court, a two-part argument Manafort made that 1) the initial Mueller appointment was limited to Russia’s tampering and obstruction thereof, but the permission in the appointment to investigate anything “arising out of” that Russia investigation — which this prosecution had to be — was improper, and 2) that the August memorialization of Mueller’s authority incorporating the Ukrainian money laundering did not authorize this indictment because Mueller had improperly claimed the pre-existing investigation arose out of, rather than was subsumed into, the Russia investigation.
In a dispute in which the first issue is the memo appointing Mueller, Ellis is accusing Rosenstein of not incorporating everything he appointed Mueller to do in his May 17 statement, which Dreeben explained was done to hide the scope of the counterintelligence concerns from targets. That’s a claim backed by the government’s brief and the public Rosenstein testimony it cites.
Recognizing the need for confidentiality about the investigation, id. at 30, the Acting Attorney General “discussed that with [the Special Counsel] when he started” and has continued to have “ongoing discussion about exactly what is within the scope of his investigation,”
[snip]
The regulations do not provide that the factual statement must be made public.
The government brief argues that, because of his role in the campaign and his ongoing ties to Russians — including Oleg Deripaska, by name — the Manafort investigation falls under the original grant of authority. They make the “arises out of” argument only secondarily.
[E]ven assuming that paragraph (b)(i) does not cover all of the conduct charged in the Indictment—and, in the government’s view, it does—the conduct would fall within the scope of a matter that “arose or may arise directly from the investigation.”
Ellis’ concern that Rosenstein didn’t lay everything out in that first memo or might be hiding an ulterior motive of flipping Manafort go to two concerns that Dreeben (and Asonye’s presence) addressed head on. First, Ellis was concerned the Mueller team might be asserting it had unlimited power.
What we don’t want in this country is we don’t want anyone with unfettered power. We don’t want federal judges with unfettered power. We don’t want elected officials with unfettered power. We don’t want anybody, including the president of the United States, nobody to have unfettered power. So it’s unlikely you’re going to persuade me that the special prosecutor has unlimited powers to do anything he or she wants.
Though (again, given his reputation for beating up the side he plans to decide with) this line might be better understood as Ellis wanting to demonstrate a concern with the possibility that Mueller might think he has unfettered power.
Note, he includes the president in there.
Ellis also misstated, right as the discussion started, that the special counsel was not the government.
Let me ask the government — or not the government — the special counsel a few questions, Mr. Dreeben.
In correcting Ellis’ suggestion Mueller was not representing the government, Dreeben clarified that the Special Counsel was not operating under the Independent Counsel law that Ellis had elsewhere raised and seemed to be thinking of when suggesting they didn’t represent the government.
This is not the Independent Counsel Act that Your Honor was referring to in the conference that you spoke of. This is not a separate court-appointed prosecutor who’s operating under statutory independence. We are within the Department of Justice. We’re being supervised by an acting attorney general who has conferred upon us specific jurisdiction and who regularly is in a position to describe to us the metes and bounds of that.
To further establish this point the government notes — in both their brief and the hearing — that the Mueller team worked closely with the rest of DOJ in bringing the charges.
As explained above, every key step in this case has been authorized by the Acting Attorney General through ongoing consultation. Additionally, under the applicable rules, the Tax Division approved the tax-related charges. See 28 C.F.R. § 600.7(a) (Special Counsel must comply with DOJ rules, regulations, procedures, and policies); USAM § 6-4.200 (Tax Division must approve all criminal tax charges). And the Senior Assistant Special Counsel in charge of this prosecution is a long-time, career prosecutor with the internal authority to conduct this prosecution, separate and aside from his role in the Special Counsel’s Office.
While Ellis certainly made a public show of scolding the Mueller team claims, he did so in a hearing bracketed by his observation that Mueller had already done something — bring in Asonye — to assuage Ellis’ concerns about operating outside of normal DOJ procedure.
And while I hesitate to predict how Ellis will rule, I find the bracketing of the entire hearing with a focus on Asonye significant for two reasons. First, Ellis’ proposed remedy, if Mueller’s investigation were invalid, was to have EDVA prosecute the case (to which Downing suggested that that would make the search of his storage facility and home invalid, which for better and mostly worse is not how fourth amendment rulings work).
THE COURT: Let’s assume for a moment your argument that this delegation is in some way illegal. Why isn’t the right result simply to give to the Eastern District of Virginia’s U.S. Attorney’s Office — give it back to them and let them prosecute this indictment? Why isn’t that the right result?
MR. DOWNING: Well, the right result may be for the Department of Justice to finish the investigation they had started and make a determination as to whether or not to charge Mr. Manafort. But if, in fact, this order is defective, then Mr. Mueller did not have the authority of the U.S. Attorney to conduct a grand jury investigation, to get search warrants, or to return and sign an indictment.
THE COURT: All right. I think I understand.
Additionally, although many Manafort partisans view Ellis’ order that Mueller’s team give him an unredacted copy of the August 2 Rosenstein memo laying out everything that could be investigated as of that date as victory for Manafort, that actually falls far short of what Downing wanted, which was to have any other documentation showing the discussion behind appointing Mueller and approving subsequent steps thereafter.
MR. DOWNING: Just briefly, Your Honor. The one thing we would ask this Court to do before deciding the motion before the Court is to ask the government for what anybody who has had any experience with the Department of Justice knows exists, which is the written record. Where is the written record before Mr. Mueller was appointed? Where is the written record about the decision —
THE COURT: What do you mean by the written record?
MR. DOWNING: Mr. Rosenstein had a process he had to go through in order to determine that there was a conflict that gave rise to the appointment of special counsel, the specific matter that the special counsel was going to investigate in any additional jurisdiction he granted. It would all be written down somewhere. That’s how the Department of Justice works.
[snip]
THE COURT: All right. Is that what you’re — the record of identifying the conflict?
MR. DOWNING: I believe identification of the conflict, the matter that needed to be referred to a special counsel in order to — because of the conflict and the scope of the special counsel’s investigation, including any additional jurisdiction.
THE COURT: The May and August letters are the scope.
MR. DOWNING: That’s after the fact. You would expect that the Department of Justice, especially Mr. Rosenstein, would have had a memo before.
THE COURT: Why do you say that?
MR. DOWNING: Because in the Department of Justice generally, just in any situation —
THE COURT: Did you serve in the department?
MR. DOWNING: Fifteen years, five of which was under Mr. Rosenstein’s management. Mr. Rosenstein is a stickler for memos being written, for there to be a written record for the actions of the Department of Justice
In Rosenstein’s testimony and the government’s brief, they actually identify what the latter documents are: Urgent Reports documenting each major step, surely including the two searches on Manafort’s property.
The Special Counsel has an explicit notification obligation to the Attorney General: he “shall notify the Attorney General of events in the course of his or her investigation in conformity with the Departmental guidelines with respect to Urgent Reports.” 28 C.F.R. § 600.8(b). Those reports cover “[m]ajor developments in significant investigations and litigation,” which may include commencing an investigation; filing criminal charges; executing a search warrant; interviewing an important witness; and arresting a defendant.
So Downing specifically asked for (though not by name) the documentation that would have shown the back and forth discussions between Mueller and Rosenstein (and would have reflected Mueller’s compliance with the Urgent Reports requirement.
And Ellis didn’t grant that request. He asked only for the August 2 memo, not the Urgent Reports. That’s unsurprising — asking for the latter would have been a fairly breathtaking incursion on prosecutorial discretion.
But that suggests, at least thus far, Ellis is treating what he’s seeing as proper exercise of prosecutorial discretion.