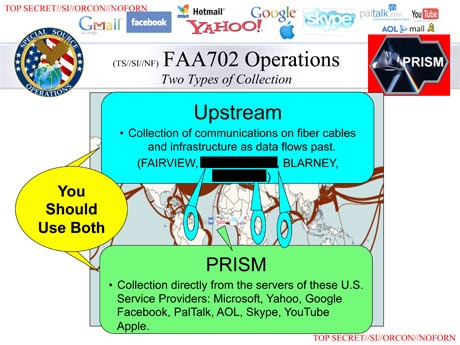
The No-Technologist Technology Review Panel
In addition to the four people ABC earlier reported would be part of Obama’s Committee to Learn to Trust the Dragnet, Obama added … another law professor, Geoffrey Stone. (Stone is [see update], along with Swire, a worthwhile member. But not a technologist.)
What’s fucking crazy about the committee is it has zero technologists to review a topic that is highly technical. Obama implicitly admits as much! He sells this committee for their “immense experience in national security, intelligence, oversight, privacy and civil liberties.” National security, intelligence, oversight, privacy, civil liberties. No technology.
On August 9, President Obama called for a high-level group of experts to review our intelligence and communications technologies. Today the President met with the members of this group: Richard Clarke, Michael Morell, Geoffrey Stone, Cass Sunstein and Peter Swire.
These individuals bring to the task immense experience in national security, intelligence, oversight, privacy and civil liberties. The Review Group will bring a range of experience and perspectives to bear to advise the President on how, in light of advancements in technology, the United States can employ its technical collection capabilities in a way that optimally protects our national security and advances our foreign policy while respecting our commitment to privacy and civil liberties, recognizing our need to maintain the public trust, and reducing the risk of unauthorized disclosure.
The President thanked the Members of the Group for taking on this important task and looks forward to hearing from them as their work proceeds. Within 60 days of beginning their work, the Review Group will brief their interim findings to the President through the Director of National Intelligence, and the Review Group will provide a final report and recommendations to the President. [my emphasis]
So in spite of the fact that the White House highlights technology in its mandate, that didn’t lead them to find even a single technologist.
Also: Cass Sunstein.
Also: the Committee does, in fact, report its findings through James Clapper, the guy whose programs they will review, they guy who lied to Congress.
At least the White House isn’t promising — as Obama originally did — that it will be an “outside” “independent” committee.
Update: Egads. I take back what I said about Stone, who said this in June.
[W]hat should Edward Snowden have done? Probably, he should have presented his concerns to senior, responsible members of Congress. But the one thing he most certainly should not have done is to decide on the basis of his own ill-informed, arrogant and amateurish judgment that he knows better than everyone else in government how best to serve the national interest. The rule of law matters, and no one gave Edward Snowden the authority to make that decision for the nation. His conduct was more than unacceptable; it was criminal.