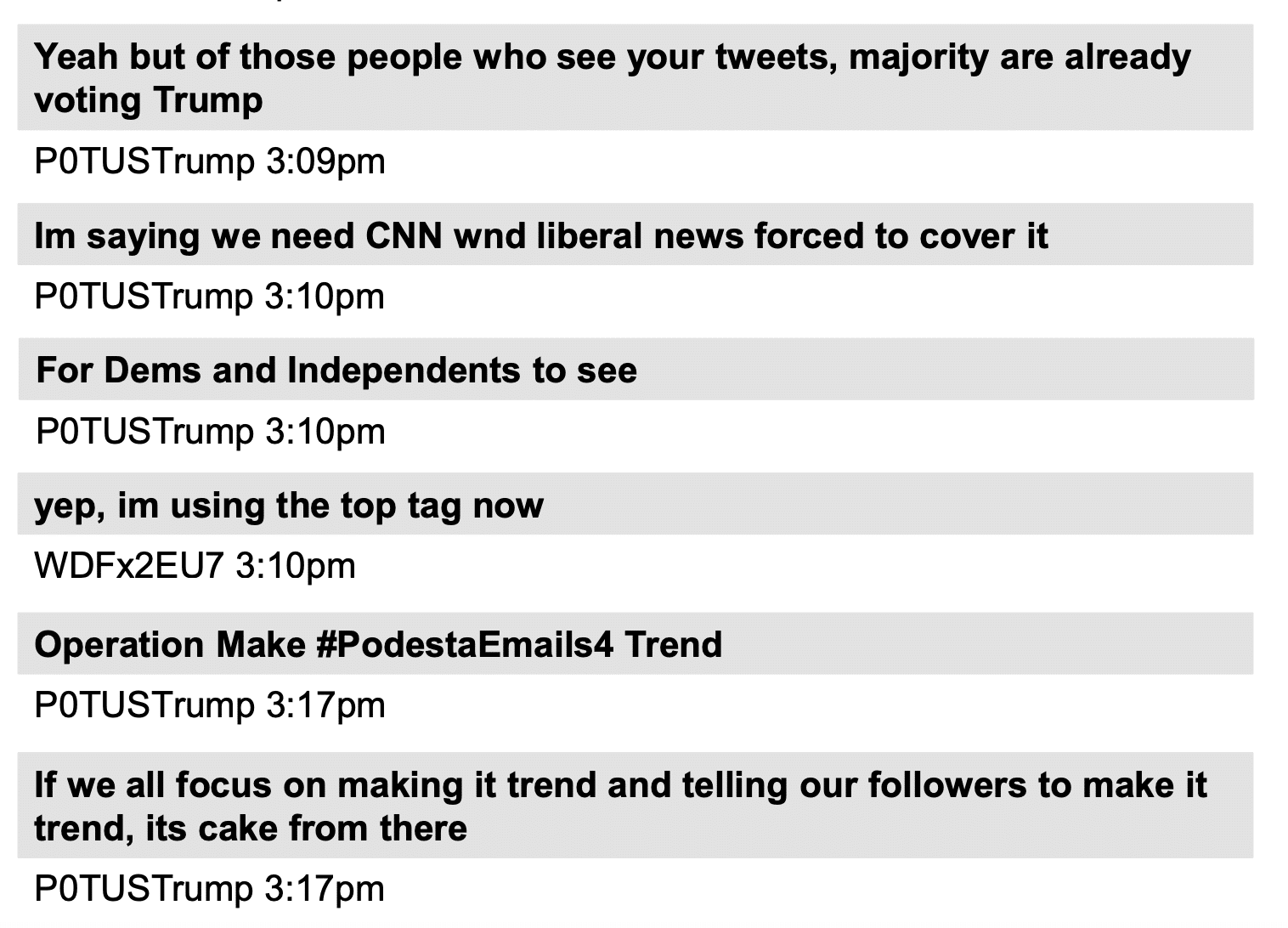
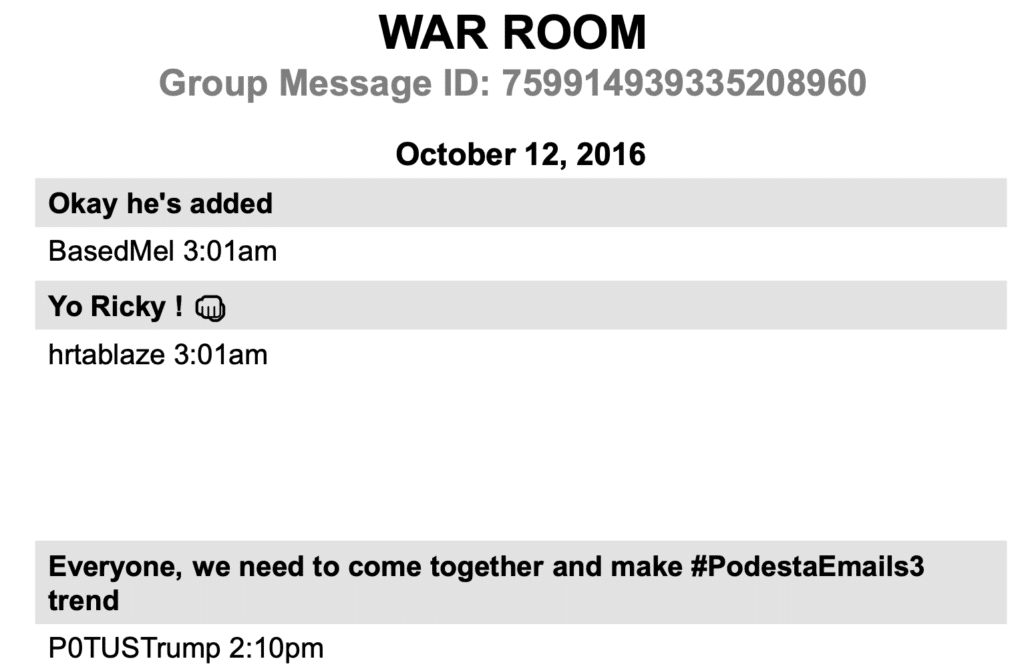
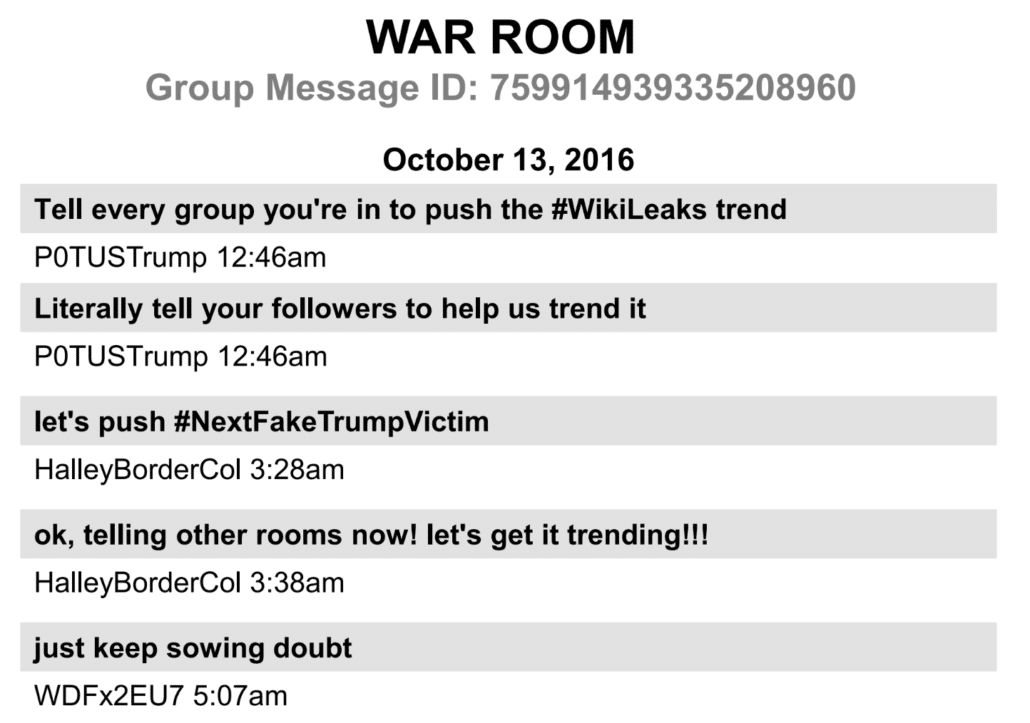
In Attempting To Claim WaPo Doesn’t Chase Rat-Fucks, WaPo Lies about Chasing Rat-Fucks
I’m the rarity among lefties who supports the decision of Politico, WaPo, and NYT (thus far) to not publish the actual files that a persona suspected to have ties to Iranian hackers sent them. That’s true, partly because I think this hack could be even more dangerous than the one of Hillary. But it’s also true because of the opportunity cost that publishing stolen documents incurs.
I prefer Kamala Harris’ message to remain the affirmative message she’s running on, and to the extent that those outlets are doing reporting like the story further developing the suspected $10 million payment via Egypt to Trump, I’d like them to continue to pursue real reporting, as well.
One of the real impacts of the files Russia hacked in 2016 is that they distracted journalists from harder work, work about what a corrupt man Trump is. Campaign reporters are already distracted too easily by nonsense stuff; they don’t need any further distractions from their day job.
That said, reporters don’t have to publish the actual documents to address something that is clearly newsworthy about the files. As Politico explained, the main thing the persona has sent so far was a draft of the vetting document for JD Vance and Marco Rubio.
A research dossier the campaign had apparently done on Trump’s running mate, Ohio Sen. JD Vance, which was dated Feb. 23, was included in the documents. The documents are authentic, according to two people familiar with them and granted anonymity to describe internal communications. One of the people described the dossier as a preliminary version of Vance’s vetting file.
The research dossier was a 271-page document based on publicly available information about Vance’s past record and statements, with some — such as his past criticisms of Trump — identified in the document as “POTENTIAL VULNERABILITIES.” The person also sent part of a research document about Florida Sen. Marco Rubio, who was also a finalist for the vice presidential nomination.
Note, this mirrors one of the first things Guccifer 2.0 released in 2016: Hillary’s oppo dossier on Trump. So in addition to its use of an AOL account, this persona is adopting another of the Russian persona’s tactics.
Again, I’m cool with outlets sitting on the dossier itself. But the content of it is newsworthy. That’s because after JD Vance’s rocky rollout, both donors and Trump himself are asking whether vetters were surprised by Vance’s misogynist public statements.
Over the past two weeks, Mr. Trump has fielded complaints from donors about his running mate, JD Vance, as news coverage exploring Mr. Vance’s past statements unearthed — and then exhaustively critiqued — remarks including a lament that America was run by “childless cat ladies.”
Mr. Trump dismissed out of hand donors’ suggestions that he replace Mr. Vance on the ticket. But Mr. Trump privately asked his advisers whether they had known about Mr. Vance’s comments about childless women before Mr. Trump chose him.
 I’d also like to know if Trump’s vetting team knew of the pictures of JD wearing drag while at Yale, which have become the subject of memes on social media.
I’d also like to know if Trump’s vetting team knew of the pictures of JD wearing drag while at Yale, which have become the subject of memes on social media.
Whether the dossier was comprehensive matters (particularly given that a law firm also involved in Trump’s criminal defense completed it). It matters, most of all, because Trump has swapped the mediocre Ivanka as his primary familial advisor for the incompetent Don Jr, and the failson had a key role in picking JD.
So it would be newsworthy to reveal the scope and the thoroughness (or not) of the vetting document.
That said, I think every outlet that is sitting on these documents, particularly if they’re withholding details about any oversights in JD’s vetting document, owes the public an explanation of why they’re adopting a double standard as compared to their poor choices from 2016.
WaPo, which is trying to hunker through controversy about Will Lewis’ possible role in covering up Murdoch’s phone hacking, tried to do that yesterday. Matt Murray boasted that outlets were taking a breath, and then went on to claim that the vetting document isn’t newsworthy because the six-month old vetting document isn’t, “fresh or new enough.”
“This episode probably reflects that news organizations aren’t going to snap at any hack that comes in and is marked as ‘exclusive’ or ‘inside dope’ and publish it for the sake of publishing,” said Matt Murray, executive editor of The Post. Instead, “all of the news organizations in this case took a deep breath and paused, and thought about who was likely to be leaking the documents, what the motives of the hacker might have been, and whether this was truly newsworthy or not.”
[snip]
“In the end, it didn’t seem fresh or new enough,” Murray said.
WaPo even attempted to address something virtually all discussions about using rat-fucked documents in the context of the suspected Iranian hack do not: the treatment of the Hunter Biden laptop, the most innocent provenance explanation for which is that, after pursuing a laptop from foreigners with ties to Russian intelligence for a year, Rudy Giuliani received just such a laptop out of the blue from a blind computer repairman.
Here’s what WaPo claims about how reserved news organizations were with the hard drives described as the Hunter Biden laptop.
News organizations have been tested since 2016. Wary of (1) hacked materials since then, many proved reluctant to report on the contents of Hunter Biden’s laptop out of concerns that they were the result of a hack. As the conservative press latched on to (2) allegedly incriminating emails found on the computer in the final weeks of the 2020 campaign, more mainstream outlets did not join in a 2016-style frenzy over the material, and Facebook and Twitter limited distribution of a New York Post story about the laptop.
An analysis by The Post nearly two years later confirmed the authenticity of many of the emails on the laptop and found no evidence of a hack. [my annotation]
Note the two reasons alluded to in this passage, both of which show up in Murray’s claimed explanation for sitting on the JD Vance dossier. There were two concerns, according to the WaPo:
- Was the laptop “hacked”?
- Did the “allegedly incriminating emails” prove what the NYPost claimed they did?
Then, in the next paragraph, WaPo addresses just one of those two issues, whether the hard drive copied from a copy of a laptop, was hacked. WaPo claims, falsely, that the linked story describing the results of Jake Williams and Matt Green’s analysis “found no evidence of a hack.”
For starters, that’s a category error. This is a copy of a copy of a laptop, not the laptop itself. What their analysis attempted to assess was the authenticity of the emails on the laptop — but two different security researchers were only able to do so for a fraction of the emails. This analysis made no attempt to assess whether the stuff on the laptop was packaged up from authentic files (or from a combination of authentic and doctored files). Far more importantly, given details of Hunter’s cloud accounts, it did not assess whether people besides Hunter Biden had access his cloud data (evidence at his gun case described that not just his mistress, Zoe Kestan, accessed his cloud data, but his drug dealers accessed at least his bank account).
But it did find that the copy of a copy of a laptop lacked marks of reliability and did include files placed there by someone other than Hunter Biden.
Most of the data obtained by The Post lacks cryptographic features that would help experts make a reliable determination of authenticity, especially in a case where the original computer and its hard drive are not available for forensic examination. Other factors, such as emails that were only partially downloaded, also stymied the security experts’ efforts to verify content.
[snip]
In their examinations, Green and Williams found evidence that people other than Hunter Biden had accessed the drive and written files to it, both before and after the initial stories in the New York Post and long after the laptop itself had been turned over to the FBI.
[snip]
“From a forensics standpoint, it’s a disaster,” Williams said. (The Post is paying Williams for the professional services he provided. Green declined payment.)
[snip]
Neither expert reported finding evidence that individual emails or other files had been manipulated by hackers, but neither was able to rule out that possibility.
[snip]
Analysis was made significantly more difficult, both experts said, because the data had been handled repeatedly in a manner that deleted logs and other files that forensic experts use to establish a file’s authenticity.
“No evidence of tampering was discovered, but as noted throughout, several key pieces of evidence useful in discovering tampering were not available,” Williams’ reports concluded.
There are several details, disclosed subsequent to the story, that it lacks: It doesn’t talk about the ways the story John Paul Mac Isaac’s attorney told WaPo conflict with the story JPMI would tell in his book (one very significant conflict pertains to the date when JPMI reached out to the FBI). It doesn’t describe that JPMI himself disavowed some of the content on the Jack Maxey hard drive, the one shared with the WaPo. It doesn’t describe that Hunter has sued Garrett Ziegler and Rudy Giuliani for hacking him (the former survived Ziegler’s motion to dismiss; the latter was dismissed pending the end of Rudy’s bankruptcy; as far as I know, Hunter has not yet renewed the suit against Rudy given the imminent dismissal of Rudy’s bankruptcy). It doesn’t describe that in court filings, Abbe Lowell affirmatively claimed that the data on the laptop itself — not the copy! — had been compromised before being shared with the FBI.
Defense counsel has numerous reasons to believe the data had been altered and compromised before investigators obtained the electronic material from Apple Inc. and The Mac Shop, such that the Special Counsel’s claim that the underlying data is “authentic” (id. at 4) and accurately reflects “defendant’s Apple Macbook Pro and [] hard drive” (id. at 2) is mistaken.
Mr. Biden’s counsel told the Special Counsel on May 10, 2024 it agrees not to challenge the authenticity of the electronic data the Special Counsel intends to use with respect to it being what law enforcement received on December 9, 2019 from John Paul Mac Isaac (owner of The Mac Shop), and from Apple on August 29, 2019 and in a follow-up search on July 10, 2020. (Mot. at n.3.) However, Mr. Biden cannot agree this electronic data is “authentic” as to being his data as he used and stored it prior to Mac Issac obtaining it.
WaPo relies on a two year old story that has been significantly preempted to claim that the copy of the copy of the laptop was not hacked. The story never made such a claim, and the claims it has made have been undermined since.
But there’s an even more telling aspect of WaPo’s self-satisfied claim that reporters gave up their rabid addiction for rat-fuckery after 2016. It doesn’t address whether the laptop subsequently became newsworthy.
There’s good reason for that: Because after the election, WaPo did embrace the laptop, even the doctored one they got from Maxey, as part of a years-long campaign of dick pic sniffing. Their lead dick pic sniffers, Matt Viser and Devlin Barrett, even made shit up when disgruntled IRS agents released details that raised questions about the integrity of the original copy. Since then, prosecutors themselves have described that the extraction of the copy of the laptop they received — the one whence all the data that sloppy reporters call “the laptop” came — is 62% bigger, measured in terms of pages, than the laptop itself. There are potentially innocent explanations for why the hard drive purporting to be a copy of the laptop would not match it, but those explanations would conflict with JPMI’s explanations for how he made the copy. And, scandalously, the FBI never made an index of the laptop, and Judge Maryellen Noreika allowed it to be used in the trial against Hunter without ever even assuring that the forensic reports on the extraction of the two devices matched what got certified to her in a court filing.
And WaPo is not alone in its continuing addiction to relying on a copy of a copy of a laptop with such provenance problems. Just yesterday, NYT’s Ken Vogel did a story that relied on the laptop which basically said, Hunter Biden asked the Commerce Department for help on Burisma but it blew him off (unsurprisingly, Vogel also struggles with the court filings on which he bases his news hook). Four years after Vogel’s chum Rudy Giuliani released the laptop, three weeks after Joe Biden dropped out, NYT is still reporting the absence of news in an 8-year old email as news, precisely the kind of attention suck that rat-fuckers seek when they provide stolen documents to people like Vogel.
Again, in my opinion, WaPo is right not to publish the JD Vance dossier, though that’s different than using it to assess whether there were big gaps in the vetting of Trump’s unpopular running mate.
But WaPo is telling fairy tales about whether mainstream outlets gave up their fondness for rat-fuckery.
They did not. For four years, they have been utterly addicted to the rat-fuckery of the laptop, to the exclusion of reporting on all the details that should raise cautions disclosed since then.
And as such, the decision not to embrace this rat-fuckery, however correct it might be, is a double standard.