
John Roberts Subjects America's School Children to the Whims of a Wrestling Promoter
John Roberts just gave a billionaire wrestling promoter accused of letting an employee sexually exploit boys a green light to start destroying local school programs around America. That's a political battle Trump's opponents should pick up with relish.

The Allies Of the Billionaires
We weaken the filthy rich by attacking their allies.

Breathing Room: What's in Your Shopping Cart?
How the hell are food shortages and food insecurity making America great again?
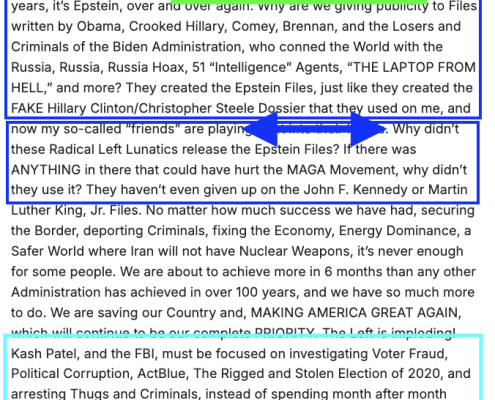
Jeffrey Epstein Is about Trump's Failing Ability to Command Attention
It doesn't matter why Trump's super power of commanding and redirecting attention is failing with the Jeffrey Epstein scandal. If that power fails with his base, it will make it far harder for him to continue to avoid accountability as his policies destroy their lives.

Fridays with Nicole Sandler
We talked the Big Ugly, Trump's tariffs, and Trump's effort to distract from Jeffrey Epstein.

Trump's Deep State Can't Even Deep State Competently
Because conspiracy theorist turned Deputy Director of the FBI, Dan Bongino, couldn't find experts in digital forensics and chain of custody at an agency that employs thousands of such people, all the squabbling members of Trump's Deep State trying to end the Jeffrey Epstein conspiracy theories have made it far, far worse.

Children Died to Own the Libs
"Dead in the water," they joked at a Kerr County commissioners meeting when discussing a flood alert system. But sure, DEI must be the reason why children were sacrificed to flood waters.

"Fuck You:" Todd Blanche Continues to Flopsweat over Emil Bove's Contempt
Todd Blanche's brief presence at a March 14 meeting appears to coincide with two things: Redactions in Erez Reuveni's whistleblower complaint, and the impetus for Emil Bove to start threatening to tell judges to fuck off.
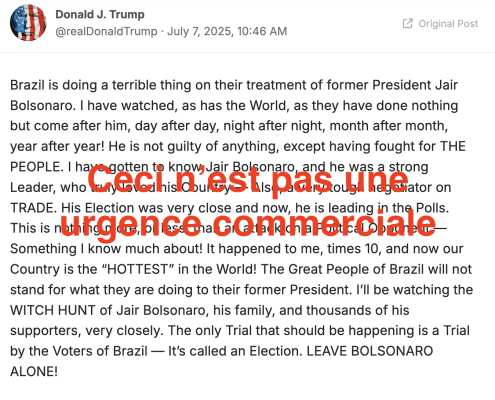
Trump's Coffee for Coup Accountability Emergency
Donald Trump wants to impose a 50% tax on coffee in an effort to prevent coup accountability for Jair Bolsonaro in Brazil. That may make it far easier for courts to affirm a court ruling that his tariffs are unlawful.

Expecting Legislators to Lead the Resistance Is a Category Error
You shouldn't want Hakeem Jeffries and Chuck Schumer to lead the political movement opposing Trump, not least because that movement needs to be far broader than the Democratic Party.

"Are You Still Talking about Jeffrey Epstein?"
More than perhaps any moment of his ten year career, Trump just lost his cool -- about a Jeffrey Epstein question -- because he is helpless to dictate the focus of attention.

Pam Bondi Admits She Must Fire Kash Patel and Dan Bongino
If the joint DOJ/FBI memo declaring there's no there there to the conspiracy theories Kash Patel and Dan Bongino fueled is true, then Pam Bondi must demand their resignation for discrediting the Bureau.

How Trump Plans to Dodge Accountability Again
Trump's policies have and will get people killed. Will we find a way to hold him accountable, this time?

Seeing Language as a Tool of Authoritarianism
When you speak on social media, are you saying or are you doing?

Three Things: Hope Within Us
This could be us, rowing together. Hope is your paddle.

No Kings Day Reflections from an American-Irish in the Home of Her Ancestors
On this No Kings Day, remember that America is a tapestry of from-ness that Kings failed to stamp out.

The Anti-Democracy Project Of John Roberts
John Roberts doesn't believe in our system of checks and balances.

POS BFB in da' House: Be Water, My Friend
The situation in the House is fluid. We should be, too — keep calling your representatives.

The Sound of Teeth on Bone: Leopard Eating Leopards [UPDATE]
Keep your hands and feet inside the cab, stay clear of the leopards as they begin to gnaw on their own.

Making America Gross Again: Big Fugly Bill Hits the Senate Floor [UPDATE]
The Senate votes this morning on the Big Fugly Bill. Contact your senators and tell them not to vote for this POS BFB.
