91% Fewer Terrorist Sympathizers with Twice the Cash and 48% More Surveillance
 A number of people have pointed to this report showing that the terrorist threat is grossly overblown. Not only does it show that Robert Mueller was overselling the risk of Muslim-American radicalization in the early days of of the War on Terror, and he and Janet Napolitano and Peter King and others continue to do so.
A number of people have pointed to this report showing that the terrorist threat is grossly overblown. Not only does it show that Robert Mueller was overselling the risk of Muslim-American radicalization in the early days of of the War on Terror, and he and Janet Napolitano and Peter King and others continue to do so.
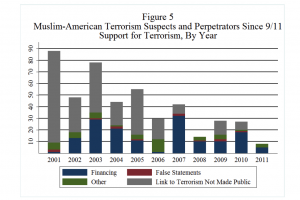
Twenty Muslim-Americans were indicted for violent terrorist plots in 2011, down from 26 the year before, bringing the total since 9/11 to 193, or just under 20 per year (see Figure 1). This number is not negligible — small numbers of Muslim-Americans continue to radicalize each year and plot violence. However, the rate of radicalization is far less than many feared in the aftermath of 9/11. In early 2003, for example, Robert Mueller, director of the Federal Bureau of Investigation, told Congress that “FBI investigations have revealed militant Islamics [sic] in the US. We strongly suspect that several hundred of these extremists are linked to al-Qaeda.”1 Fortunately, we have not seen violence on this scale.
[snip]
These and similar warnings have braced Americans for a possible upsurge in Muslim-American terrorism, which has not occurred. Instead, terrorist plots have decreased in each of the past two years, since the spike of cases in 2009.
Threats remain: violent plots have not dwindled to zero, and revolutionary Islamist organizations overseas continue to call for Muslim-Americans to engage in violence. However, the number of Muslim-Americans who have responded to these calls continues to be tiny, when compared with the population of more than 2 million Muslims in the United States5 and when compared with the total level of violence in the United States, which was on track to register 14,000 murders in 2011.6
But, as Kevin Drum emphasized, the number of Muslim-Americans indicted for supporting terrorism–rather than engaging in a plot–has declined steadily over the last decade.
But while discussing how overblown the threat from Muslim-Americans in this country is, we ought to look at another report, too–perhaps this one, bragging about how much the FBI has changed in the last decade. Because along with visualizing how much more the FBI is spending–more than twice as much–it also notes the FBI has increased surveillance 48% over the decade (and that’s separate from the surveillance the NSA and Homeland Security and local law enforcement have put into place).
In other words, it’s not just that Muslim-American support for terrorism has declined. But it has declined even while we’re spending far more resources looking for it, and we’re just not finding it, much.

 One of the most telling anecdotes in this
One of the most telling anecdotes in this