How the Deep State Taught Stephen Miller to Love Socialism
Recent reporting suggests that the CIA — more than Trump’s other top intelligence advisors — continues to give the President unvarnished advice. And by yoking that advice to spectacular covert operative success (and probably a good deal of boasting to the press), the CIA seems to be building value with Trump and his stupider advisors (with the exception of the deliberately stupidest, Steve Witkoff).
Remain in Ukraine
Take Ukraine. A recent profile of how the US betrayed Ukraine describes the CIA has remained there fighting.
But there was a counternarrative, spooled out largely in secret. At its center was the C.I.A.
Where Mr. Hegseth had marginalized his Ukraine-supporting generals, the C.I.A. director, Mr. Ratcliffe, had consistently protected his own officers’ efforts for Ukraine. He kept the agency’s presence in the country at full strength; funding for its programs there even increased. When Mr. Trump ordered the March aid freeze, the U.S. military rushed to shut down all intelligence sharing. But when Mr. Ratcliffe explained the risk facing C.I.A. officers in Ukraine, the White House allowed the agency to keep sharing intelligence about Russian threats inside Ukraine.
CIA didn’t just remain in Ukraine collecting intelligence. They’ve played a role in Ukraine’s spectacular success in using drone attacks to degrade Russia’s security.
In June, beleaguered U.S. military officers met with their C.I.A. counterparts to help craft a more concerted Ukrainian campaign. It would focus exclusively on oil refineries and, instead of supply tanks, would target the refineries’ Achilles’ heel: A C.I.A. expert had identified a type of coupler that was so hard to replace or repair that a refinery would remain offline for weeks. (To avoid backlash, they would not supply weapons and other equipment that Mr. Vance’s allies wanted for other priorities.)
Russia no doubt understands the CIA remains intelligent (heh) and focused on its original adversary. When they recruited Witkoff to manage Trump’s capitulation, they specifically ordered him not to bring CIA.
Steve Witkoff, a billionaire real-estate developer and longtime golfing partner of Donald Trump, was just days into his job as the new president’s special envoy to the Middle East when he received a tantalizing message from the crown prince of Saudi Arabia.
Vladimir Putin was interested in meeting Witkoff—so interested that he might consider releasing an American prisoner to him. The invitation came from a Kremlin moneyman named Kirill Dmitriev, using the de facto Saudi ruler, Mohammed bin Salman, as an intermediary.
There was just one thing: Witkoff would be expected to come alone, without any CIA handlers, diplomats or even an interpreter, a person familiar with the outreach said.
And Witkoff, obedient to Putin’s demands, continues to refuse CIA briefings.
Witkoff has declined multiple offers from the CIA for a briefing on Russia.
[snip]
Ahead of his trip, the CIA offered to brief Witkoff; he declined. Nor was he accompanied by an interpreter: He had been told that Russia’s president wouldn’t allow him to bring another person into the meeting.
A White House official said he participated in multiple briefings before his first trip to Russia, including Trump’s intelligence briefing. The CIA regularly briefs him on other issues like Gaza—but not Russia.
Inform Trump that Ukraine did not strike Russia
The thing is, the ability to provide accurate intelligence and (I assume this was more important) really cool attacks that make the attacker look strong appears to be increasing the CIA’s value to Trump.
Not only did CIA conclude (unsurprisingly) that Putin was lying when he recently claimed that Ukraine had attempted to target his residence,
The CIA has assessed Ukraine was not targeting a residence used by Russian President Vladimir Putin in a recent drone attack in the north of his country, according to US officials, undercutting an assertion the Russian leader had made to President Donald Trump in a Monday phone call.
The CIA’s director John Ratcliffe briefed Trump on the assessment Wednesday, the officials said.
Russia had publicly raised allegations Ukraine attempted to hit Putin’s home Monday, and Trump told reporters Putin had told him of it over the phone. At the time, the president said he was troubled by the reported action, seeming to believe the Russian leader even as Ukraine strenuously denied it was behind any such attack.
“I don’t like it. It’s not good,” Trump said, describing himself as “very angry” upon hearing the claim.
But in the wake of Ratcliffe’s briefing, Trump has repeated that conclusion.
President Donald Trump on Sunday told reporters that U.S. officials have determined that Ukraine did not target a residence belonging to Russian President Vladimir Putin in a drone attack last week, disputing Kremlin claims that Trump had initially greeted with deep concern.
Russian Foreign Minister Sergey Lavrov last week said Ukraine launched a wave of drones at Putin’s state residence in the northwestern Novgorod region that the Russian defense systems were able to defeat. Lavrov also criticized Kyiv for launching the attack at a moment of intensive negotiations to end the war.
The allegation came just a day after Ukrainian President Volodymyr Zelenskyy had traveled to Florida for talks with Trump on the U.S. administration’s still-evolving 20-point plan aimed at ending the war. Zelenskyy quickly denied the Kremlin allegation.
Trump said that “something happened nearby” Putin’s residence but that Americans officials didn’t find the Russian president’s residence was targeted.
“I don’t believe that strike happened,” Trump told reporters as he traveled back to Washington on Sunday after spending two weeks at his home in Florida. “We don’t believe that happened, now that we’ve been able to check.”
Sure, this is just one instance, one single time when Trump believed his own spooks over Putin. But given that Trump first started to parrot obviously bullshit Russian claims eight years ago, in Helsinki, the fact that Trump would accept CIA’s judgment and in the process withstand an obvious attempt to pull Trump back towards capitulation, the instance feels momentous.
Venezuela central to success of operation
And given the CIA’s role in delivering one of the most sadistic thrills of this term, Trump may have no way back.
NYT dedicated an an entire story to describing how CIA (probably assisted by the $50 million reward the FBI offered) recruited someone within Maduro’s government who shared details of the dictators pattern of life.
The American spy agency, the people said, produced the intelligence that led to the capture of Mr. Maduro, monitoring his position and movements with a fleet of stealth drones that provided near constant monitoring over Venezuela, in addition to the information provided by its Venezuelan sources.
The C.I.A. had a group of officers on the ground in Venezuela working clandestinely beginning in August, according to a person familiar with the agency’s work. The officers gathered information about Mr. Maduro’s “pattern of life” and movements.
It is not clear how the C.I.A. recruited the Venezuelan source who informed the Americans of Mr. Maduro’s location. But former officials said the agency was clearly aided by the $50 million reward the U.S. government offered for information leading to Mr. Maduro’s capture.
Given how volatile things are in Venezuela, the CIA may not be able to sustain this person’s loyalty (or life, not least because Trump has made it a lot harder to support assets in various ways).
But for now, the CIA is taking credit for a key role in one of Trump’s only successes — and Trump is boasting of their work (again, in ways that may get assets in the field killed).
Advise Trump to keep regime members
Even before that success, though, CIA advised — and Trump heeded their advice — to stick with a Maduro loyalist to govern after his snatching. WSJ reports that senior Trump officials asked for this analysis weeks before the snatch.
Senior Trump administration officials commissioned the CIA to undertake the analytical assessment and debated it during discussions about day-after plans for Venezuela, the people said. The people familiar with the assessment said they were unsure of the precise date it was produced.
The report was briefed to Trump in recent weeks, according to two of the people.
The assessment didn’t describe how Maduro could lose power, or advocate for removing him, but attempted to gauge the domestic situation in Venezuela in the event that he did, people familiar with it said.
The intelligence report, the people said, cited Rodríguez and two other top Venezuelan regime figures as possible interim rulers who could keep order. The people familiar with the assessment didn’t identify the other two officials, but besides Rodríguez, the two most influential power brokers are Interior Minister Diosdado Cabello and Defense Minister Vladimir Padrino.
This advice may well backfire in the near term. It is undoubtedly the case that a Chavista will have far more ability to sustain order. But particularly given Trump’s belated realization that the oil won’t pay for itself — and the US government will have to subsidize oil development, it will very quickly sour at least some of the people most excited by this invasion, the Cuban-American community.
And ultimately, the Administration has gone all in with Chavistas who rule through brutal repression, as Stephen Miller said in that batshit interview with Jake Tapper where he also repeatedly said that Venezuela is an island.
For those who may be indicted, the best choice they can possibly make is to be part of a constructive decision-making process for the future of Venezuela. The best decision they can make is to cooperate fully and completely with the United States to be part of building this brighter future for Venezuela.
When Miller envisions cooperating with the other people who were indicted, he’s stating that he’s happy to cooperate with Diosdado Cabello, who has been far more involved in the day-to-day trafficking than Maduro, and who is very much an ideological Chavista.
Stephen Miller went on TV — around the same time as Trump said he was going to give welfare to oil companies so they could benefit Venezuela — and bragged about working with precisely the socialists he has defined his entire existence in opposition to.
John Ratcliffe’s CIA, the Deep State! after building Donald Trump’s trust over a year, convinced Stephen Miller to love socialists.
Ratcliffe bypassed the DNI gatekeeper
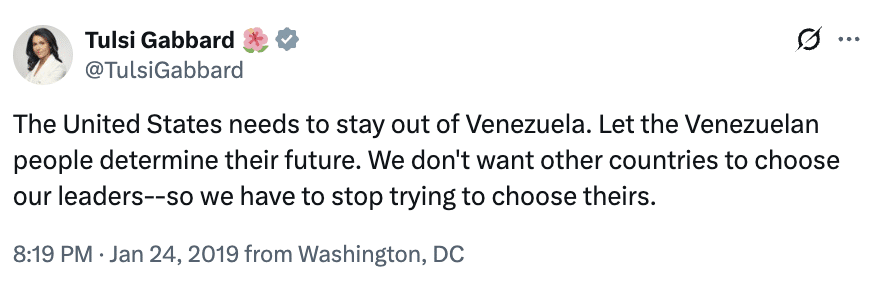
Meanwhile, Tulsi has remained silent since the snatch.
Leaving people to mock her past statements predicting precisely what is happening in Venezuela.
Tulsi almost lost her job in advance of the Iran strikes after posting a video warning of World War III.
It’s not necessarily a good thing that Tulsi’s skepticism is being supplanted with Ratcliffe’s willingness to go big on covert operations. Both of them suck. Neither can offer wise counsel to Trump (but both likely know Venezuela is not an island).
But at least some reality has begun to seep into Trump’s thinking.
Update, January 8: Sure enough, Bloomberg reports that Tulsi was systematically excluded from the planning for Venezuela.
The White House excluded Director of National Intelligence Tulsi Gabbard from months of planning to oust Nicolas Maduro because her previous opposition to military action in Venezuela cast doubt on her willingness to support the operation, people familiar with the matter said.
The move to cut Gabbard out of the meetings was so well-known that some White House aides joked that the acronym of her title, DNI, stood for “Do Not Invite,” according to three of the people. They asked not to be identified discussing private conversations. A White House official denied there was any such joke.
As a Democratic congresswoman in 2019, Gabbard said the US needs to “stay out” of Venezuela, and as recently as last month she railed against “warmongers” pushing the US into conflict.
The exclusion was the latest evidence of long-running tension over Gabbard’s role in the Donald Trump administration, and has underscored how the president’s decision to oust Maduro — despite campaigning against starting new wars — has widened fissures not only among his MAGA supporters but also within his team.
Tulsi’s people even pointed to that hilarious tweet to push back on this story.
A senior intelligence official pushed back against the characterization that Gabbard had been excluded, saying she provided intelligence that helped the overall mission, even if it was less operational and more analytical. An ODNI spokeswoman referred Bloomberg to a social media post Gabbard wrote Tuesday lauding servicemembers for the operation’s “flawless execution” of the move to capture Maduro.
“President Trump promised the American people he would secure our borders, confront narcoterrorism, dangerous drug cartels, and drug traffickers,” she wrote. The post broke a days-long silence after other top national security officials cheered the operation in press conferences, TV interviews and on social media.