Mike Rogers Doesn’t Exculpate Trump on “Collusion” Like Trump Once Thought
On Monday, House Judiciary Committee made available two sets of documents I’ve already covered:
- The contents of the Crossfire Hurricane binder, as released
- A cherry picked selection of 302s from investigations into leaks about Trump’s ties to Russia (see my post here)
On Tuesday, Tulsi Gabbard announced she was stripping the clearance of 37 current and former spooks, in a thinly veiled political purge. NYT provides background on some of the people Tulsi purged, including Vinh Nguyen, who was purged because he allegedly pressured Tulsi’s so-called whistleblower to affirm conclusions in the 2017 ICA, but who had remained in active service as a crucial contributor to NSA’s quantum computing efforts until this purge. This purge clearly places loyalty to Trump over America’s most crucial intelligence efforts.
Add these 37 people to the long list of those who been purged in service of Trump’s invented grievance about the 2016 election:
- Fire many of FBI’s top Russian experts at the FBI.
- Retaliate against experts.
- Expose recent CIA recruits.
- Appointment of Tulsi Gabbard, Kash Patel, and John Ratcliffe as top spies, all of them Useful Idioms for Russia.
- Fire more of FBI’s top Russian experts at FBI.
- Elimination or down-grading of programs used to reign in Russia, including FARA, FCPA, Foreign Influence Task Force, and KleptoCapture.
- Assign an incompetent idiot, Steve Witkoff, to carry out negotiations with Russia.
- Refocus of organizations fighting hacking and foreign election interference.
- Fire two top officials on the National Intelligence Council.
- Fire six professionals at National Security Counsel, followed by Alex Wong and eventually Mike Waltz — a number of whom were more hawkish on Russia.
- Reassignment of many experts on the National Security Counsel.
- Fire NSA Director Timothy Haugh and NSA General Counsel April Doss.
- Quantum computing expert Vinh Nguyen, Shelby Pierson, who had warned about Russian tampering in the 2020 election but had been serving in a senior position at National Geospatial-Intelligence Agency, and at least one other active spook, along with 34 others.
I’ll return to the way that Tulsi continues to use the hoax about Russia as an excuse to purge those who might contest Russia. The degree to which Russia has milked Trump’s grievances to destroy US capabilities against it is one of the reasons I view the 2016 operation as the most successful intelligence operation of recent history.
But for now, I want to show how these two efforts work in tandem, but also show that Tulsi’s purge actually helps to confirm that Trump “colluded” with Russia in 2016.
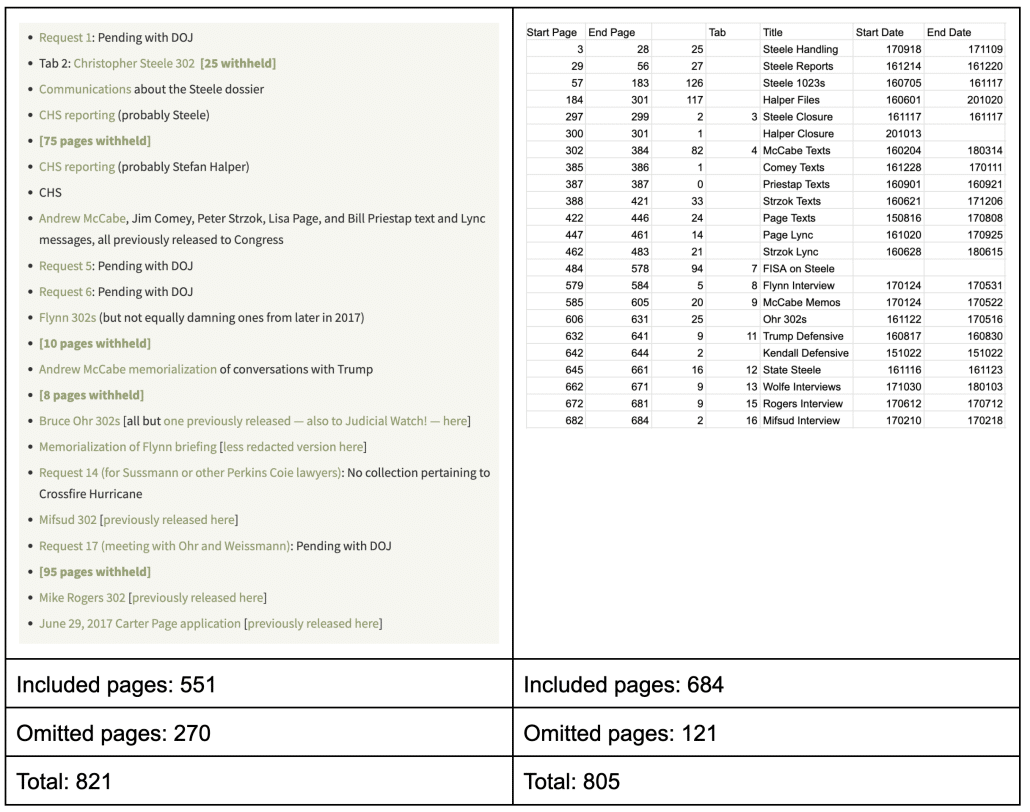
Back in 2023, I did a post on the releases to Judicial Watch (release 1, release 2) of the Crossfire Hurricane binder, which led me to conclude it was one dumbass binder. In that post, I developed a rough list of what was included in the binder, what was withheld from JW under FOIA, and what was listed as pending when Trump created the binder in 2020. We can compare my earlier list with what has been currently released, which I put into a table here.
These are close to but not quite matching documents. There were 270 pages omitted entirely from the JW FOIA (I noted only the larger chunks of withheld documents in my list). The current release omits the June 29, 2017 Carter Page FISA application, which is 121 pages.
That leaves roughly 16 pages that were in the original Crossfire Hurricane binder (as reflected in the JW FOIA) not reflected in the current release, though most if not all of those pages reflect the tracking of requests Trump made to DOJ, some of which appear in the current release as Tab numbers, some of which had not been fulfilled by the time Trump’s team put together the binder in January 2021. Two are identified: Request 14, for materials on Michael Sussmann or other Perkins Coie lawyers, and Request 17, for a meeting between Bruce Ohr and Andrew Weissmann about money laundering. Three, Requests 1, 5, and 6, are not identified.
I’ve put more analysis below, which addresses how badly cherry picked this binder was. In addition to intentionally burning Christopher Steele and Stefan Halper, as well as FBI’s informant confidentiality promises, this binder told a Russian spy story, not the story of the investigation.
But for now, I want to focus on the Mike Rogers 302 which had previously been released in heavily redacted form as part of Jason Leopold’s FOIA in 2020. The comparison of the two releases all but confirms that only Rogers’ 302 was included in the binder, even though Robert Mueller interviewed all of Trump’s top spooks back in 2017. The inclusion of Rogers, but not Rick Ledgett, likely helps to explain why Ledgett was purged along with 36 other people yesterday.
The 302 doesn’t help Trump’s current case all that much.
For example, it records that Rogers was the one who, “suggested the information [from the Steele dossier] be included in an annex or appendix rather than in the nearly one page summary he had seen.” That is one of the alleged crimes at the core of the HPSCI report, here attributed to the guy Trump treated as his most favorable government witness in 2020.
Some of the rest of the interview undercuts claims that Crossfire Hurricane investigators were trying to harm Trump. Notably, Rogers remained ignorant of the Mike Flynn prong; but he also explained that the collection on Flynn would have targeted the people he spoke with.
Much of the rest of the interview — and the reason, I suspect, why Trump included this in his dumbass binder — focuses on a March 26, 2017 conversation that Trump had with Rogers, which was the subject of public reporting in 2017, including a Nakashima/Entous story that was likely of interest to the leak investigation. It includes this language:
According to ADM Rogers’ recollection of the call and the memo, President Trump expressed frustration with the ongoing investigation into Russian interference, saying that it made relations with the Russians difficult. ADM Rogers noted that when President Trump speaks, he tends to talk in long strings and it is not immediately clear what he expects to be answered and what is rhetorical. The President often doesn’t pause for an answer before continuing to talk. During the call, President Trump disagreed with definitive assertions that the Russians were responsible for the hacks and said it was impossible to tell who was actually responsible for the hacking. He also said it was making it hard for him to deal with the Russians, and asked ADM Rogers what he thought. ADM Rogers acknowledged it was does make relations difficult, but then explained in detail, but at a high level, the intelligence supporting ADM Rogers’ confidence, and the rest of the community’s, that the Russians were behind the hacks. President Trump stated they would have to “agree to disagree” on the matter. [two lines redacted under Other Government Agency redaction] President Trump then asked ADM Rogers if he would say “that” publicly. ADM Rogers interpreted “that” to mean [one line redacted under Other Government Agency redaction]. ADM Rogers told President Trump he could not do that, as he did not and could not discuss USPERs in unclassified settings. President Trump did not ask him to “pushback” on the investigation itself, but he clearly did not agreement with the assessment of the Russian involvement.
This passage is not all that helpful to Trump either. The FBI released this even as Tulsi is attempting to undercut claims that Russia did the hack-and-leak, but it reaffirms IC certainty that Russia was behind the hack. It proves Tulsi is lying now!
It also makes it clear that Trump went to great efforts to clear the way to fulfill his commitments to Russia in 2017, with no success.
That Rogers interview took place one day before Rick Ledgett’s interview, the 302 for which remains mostly redacted.
The Mueller Report explains (in a section likely pertinent to Edward Gistaro’s inclusion on Tulsi’s purge list as well) why having just Rogers’ side of this exchange would be of interest.
On March 26, 2017, the day after the President called Coats, the President called NSA Director Admiral Michael Rogers.347 The President expressed frustration with the Russia investigation, saying that it made relations with the Russians difficult.348 The President told Rogers “the thing with the Russians [wa]s messing up” his ability to get things done with Russia.349 The President also said that the news stories linking him with Russia were not true and asked Rogers if he could do anything to refute the stories.350 Deputy Director of the NSA Richard Ledgett, who was present for the call, said it was the most unusual thing he had experienced in 40 years of government service.351 After the call concluded, Ledgett prepared a memorandum that he and Rogers both signed documenting the content of the conversation and the President’s request, and they placed the memorandum in a safe.352 But Rogers did not perceive the President’s request to be an order, and the President did not ask Rogers to push back on the Russia investigation itself.353 Rogers later testified in a congressional hearing that as NSA Director he had “never been directed to do anything [he] believe[d] to be illegal, immoral, unethical or inappropriate” and did “not recall ever feeling pressured to do so.”354
347 Rogers 6/12/17 302, at 3-4.
348 Rogers 6/12/17 302, at 4.
349 Ledgett 6/13/17 302, at 1-2; see Rogers 6/12/17 302, at 4.
350 Rogers 6/12/17 302, at 4-5; Ledgett 6/13/17 302, at 2.
351 Ledgett 6/13/17 302, at 2.
352 Ledgett 6/13/17 302, at 2-3; Rogers 6/12/17 302, at 4.
353 Rogers 6/12/17 302, at 5; Ledgett 6/13/17 302, at 2.
Rogers claimed Trump made no ask of the NSA Director, but he only gets there by claiming that you can never tell when Trump is making an ask. Ledgett claimed that this was the most “unusual” thing he had experienced in 40 years serving the country, which is probably why he chose to document it.
Now consider those two redactions. Per the WaPo story that led to this interview, the ask was a request to deny evidence of “collusion,” which Rogers deferred by saying “he did not and could not discuss USPERs in unclassified settings.”
Trump made separate appeals to the director of national intelligence, Daniel Coats, and to Adm. Michael S. Rogers, the director of the National Security Agency, urging them to publicly deny the existence of any evidence of collusion during the 2016 election.
Coats and Rogers refused to comply with the requests, which they both deemed to be inappropriate, according to two current and two former officials, who spoke on the condition of anonymity to discuss private communications with the president.
[snip]
“The problem wasn’t so much asking them to issue statements, it was asking them to issue false statements about an ongoing investigation,” a former senior intelligence official said of the request to Coats.
But Rogers’ answer — and the redaction — only makes sense if they were speaking of specific evidence of “collusion,” not the absence thereof. The quote to WaPo makes it clear that the source believed there was affirmative evidence of “collusion.”
That is, the redaction strongly suggests that Trump asked Rogers not to deny “collusion,” but to deny that the intercepts NSA had implicating Trump’s closest aides (and likely his son and son-in-law, though NSA may not have discovered all of those yet) confirmed “collusion.”
So on Monday, Jim Jordan celebrated the release of a Mike Rogers 302 the redactions to which suggest Trump asked Rogers to lie. And on Tuesday, Tulsi purged the guy who testified he found that disturbing.
Additional analysis
Carter Page FISA: As noted above, one of the main withholdings from the current document set that was in the binder on January 19, 2020 is the final Carter Page FISA, which had already been sequestered by FISC at that point. We have every reason to believe at least one version of the full binder went to Mar-a-Lago. That strongly suggests that a sequestered copy of the Page document was found at Mar-a-Lago in the August 2022 search. That, in turn, may help to explain why Kash Patel had to plead the Fifth when testifying to the Jack Smith grand jury: because if that FISA application did go to Mar-a-Lago, then it reflected material over which the FISA Court had special handling instructions, a separate crime.
George Papadopoulos doth protest materials: The binder’s treatment of George Papadopoulos is rather stunning. First, there’s the inclusion of the Joseph Mifsud 302, which like the Papadopoulos 302s from the same period — which are not included — admits to some of their contact, but obscure other parts. There’s nothing credible about this 302, but it is presented as if it helps Trump’s cause.
Meanwhile, the treatment of the Stefan Halper files is wildly uneven. It includes backup materials and the 302s describing how Halper got asked to reach out to Carter Page and others (it also reveals that Halper and Peter Navarro were buddies). The materials include much, if not all, of Halper’s conversations with Carter Page. But the single solitary scrap of his reporting from conversations with Papadopoulos is a cherry picked fragment declassified for House Republicans. But it leaves out Halper reporting in which, for example, Papadopoulos discussed monetizing his access to Trump, an effort that underlay his relationship with Sergei Millian. In short, there are vast swaths of the investigation into Papadopoulos left out here, with just Mifsud’s 302 included as stand-in, as if that exonerated Papadopoulos.
Christopher Steele materials: At least a hundred pages of Christopher Steele materials were withheld from the JW FOIA:
- 25 pages of 302s
- 17 pages of materials on Steele’s communication with State Department people
- The 95-page validation document for the Steele dossier
The latter is the most interesting to me, because it is incomplete. As one example, there’s a section about whether there was corroboration for the claim that Trump had agreed to intervene in Ukraine. It mentioned the platform changes and part of Trump’s July 21 comments about NATO, but does not mention that he publicly stated he would consider recognizing Russia’s annexation of Crimea. And while the date of this report is not marked, it also includes no comment about the discussions between Paul Manafort and Konstantin Kilimnik about carving up Ukraine, nor does it mention the floated offer to Michael Cohen.
Similarly, the table is rightly critical about references in the Steele dossier that purport to rely on Millian. But they don’t mention that Millian was saying some of the things about Trump publicly that got recorded in the dossier.
And another timing issue: The table claims there’s no corroboration that the Kremlin was involved in the dissemination of the John Podesta material. There was never a time in 2017 when that was true.
Perhaps the most interesting bit about the Steele material, however, pertains to the John Durham investigation. In many ways, this binder reflects what Durham was asked to investigate. But no Igor Danchenko materials were included in here. That’s fairly stunning, given the extent to which right wingers later incorporated Danchenko’s reporting into their conspiracy theory. All the more so given that the binder makes a big deal that Steele and Stefan Halper were closed for cause, but does not mention Danchenko, who was closed in the same period that Halper was, and for the same reason (that right wingers exposed his tie to the FBI).
David Kendall defensive briefing: One testament of the degree to which this binder was the roadmap for Durham is the defensive briefing given to Hillary Clinton’s lawyer, David Kendall, about a Turkish influence operation in October 2015. Defensive briefings make up a big chunk of the Durham report, which attempted but failed to show that Hillary was more favorably treated. The inclusion of it is all the odder given that when Trump and Mike Flynn got a defensive briefing, the FBI did not yet know that Flynn was a willing participant in a parallel Turkish influence campaign.




![[Photo: National Security Agency, Ft. Meade, MD via Wikimedia]](https://www.emptywheel.net/wp-content/uploads/2017/08/NationalSecurityAgency_HQ-FortMeadeMD_Wikimedia.jpg)