Second Impeachment Ahead: Articles Have Been Drafted [UPDATE-3]
[NB: Update(s) at the bottom of this post. /~Rayne]
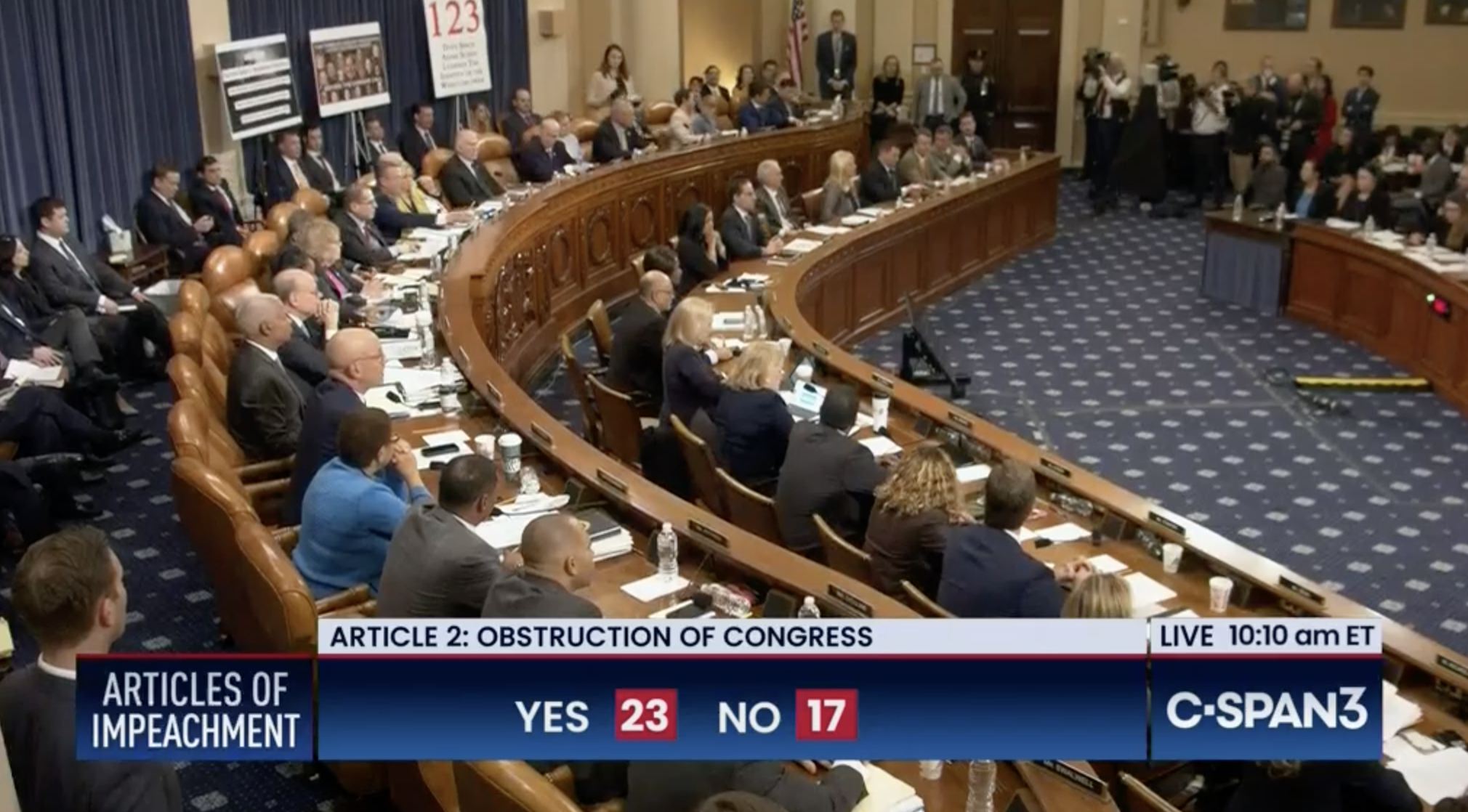
Representatives David Cicilline, Ted Lieu, and Jamie Raskin have drafted articles of impeachment against Trump which are now circulating among House members.
Here’s a transcript:
Resolved, That Donald John Trump, President of the
United States, is impeached for high crimes and mis-
demeanors and that the following articles of impeachment
be exhibited to the United States Senate.Article of impeachment exhibited by the House of
Representatives of the United States of America in the
name of itself and of the people of the United States of
America, against Donald John Trump, President of the
United States of America, in maintenance and support of
its impeachment against him for high crimes and mis-
demeanors.ARTICLE I: ABUSE OF POWER
The Constitution provides that the House of Rep-
resentatives “shall have the sole Power of Impeachment”
and that the President “shall be removed from Office on
Impeachment for, and Conviction of, Treason, Bribery, or
other high Crimes and Misdemeanors”. In his conduct of
the office of President of the United States—and in viola-
tion of his constitutional oath faithfully to execute the of-
fice of President of the United States and, to the best of
his ability, preserve, protect, and defend the Constitution
of the United States, and in violation of his constitutional
duty to take care that the laws be faithfully executed—
Donald J. Trump engaged in high Crimes and Mis-
demeanors by willfully inciting violence against the Gov-
ernment of the United States, in that:On January 6, 2021, pursuant to the Twelfth
Amendment of the United States Constitution, the Vice
President of the United States, the House of Representa-
tives, and the Senate met at the United States Capitol
for a Joint Session of Congress to count the votes of the
Electoral College. Shortly before the Joint Session com-
menced, President Trump addressed a crowd of his polit-
ical supporters nearby. There, he reiterated false claims
that “we won this election, and we won it by a landslide”.
He also willfully made statements that encouraged—and
foreseeably resulted in—imminent lawless action at the
Capitol. Incited by President Trump, a mob unlawfully
breached the Capitol, injured law enforcement personnel,
menaced Members of Congress and the Vice President,
interfered with the Joint Session’s solemn constitutional
duty to certify the election results, and engaged in violent,
deadly, destructive, and seditious acts.President Trump’s conduct on January 6m 2021 was
consistent with his prior efforts to subvert and obstruct
the certification of the results of the 2020 presidential
election. Those prior efforts include, but are not limited
to, a phone call on January 2, 2021, in which President
Trump urged Georgia Secretary of State Brad
Raffensperger to “find” enough votes to overturn the
Georgia presidential election results and threatened Mr.
Raffensperger if he failed to do so.In all of this, President Trump gravely endangered
the security of the United States and its institutions of
government. He threatened the integrity of the democratic
system, interfered with the peaceful transition of power,
and imperiled a coordinate branch of government. He
thereby betrayed his trust as President, to the manifest
injury of the people of the United States.Wherefore President Trump, by such conduct, has
demonstrated that he will remain a threat to national se-
curity, democracy, and the Constitution if allowed to re-
main in office, and has acted in a manner grossly incom-
patible with self-governance and the rule of law. President
Trump thus warrants impeachment and trial, removal
from office, and disqualification to hold and enjoy any of-
fice of honor, trust, or profit under the United States.
It’s narrow in scope, doesn’t require investigation and subsequent hearings, because the act of incitement occurred in public and was recorded on video, distributed over broadcast and cable television as well as the internet.
The inclusion of the phone call to Georgia’s Secretary of State illustrates in most minimal fashion a pattern of behavior and intent.
These articles aren’t the only approach being taken to remove Trump. Earlier today both Sen. Chuck Schumer and Rep. Nancy Pelosi called VP Mike Pence to ask for the invocation of the 25th Amendment:
SCHUMER on invoking the 25th amendment: “Speaker Pelosi & I tried to call the VP this morning to tell him to do this, they kept us on hold for 25 mins and then said the VP wouldn’t come on the phone. So we are making this call public because he should do it and do it right away.”
— Frank Thorp V (@frankthorp) January 7, 2021
They’ve since made public statements reiterating their demand for the 25th Amendment, and for impeachment leading to removal if the 25th isn’t invoked.
NBC reported earlier that Trump is fragile and feeling betrayed:
“The president is in a very fragile mental state right now and he’s not taking well to what’s happening,” Philip Rucker says. “He feels betrayed by his VP … and a lot of admin. officials are very uncertain about what he might do tomorrow.” https://t.co/1md9BRWdyc
— MSNBC (@MSNBC) January 7, 2021
Fuck that. Trump is not the United States; Congress is not elected to fluff one delicate snowflake’s dementia-addled ego.
The United States, however, is now fragile, made so by the gross failings of a malignant narcissist in decline, who has spawned an attack on his own country with seditious incitement.
It’s time for Mike Pence to honor his oath to defend the Constitution by invoking the 25th Amendment.
If Pence should fail the republic yet again, it’s time for Congress to impeach, convict, and remove Trump before he does any further damage to this fragile democracy.
~ ~ ~
UPDATE-1 — 8:20 PM ET —
This is not good. It’s been wholly predictable to those who’ve assumed Trump suffers from a progressive neurological disorder like frontotemporal dementia on top of his malignant narcissism — but still not good.
It’s also increasingly urgent.
BREAKING NEWS: @cnn @Acosta reports GOP sources close to White House say Trump “unstable, ranting and raving” and “bent on destruction in his final days.” We cannot take the nuclear codes away from him. We must take him away from the nuclear codes – before it is too late. pic.twitter.com/u2Czj7bUyA
— Joe Cirincione (@Cirincione) January 7, 2021
We need to hold Trump’s cabinet members accountable — including the “principal officers” of departments like the Acting Director in cases where the Director has left the government — for not demanding the invocation of the 25th Amendment. Pence may be resisting invocation but he’s not the only person responsible for its application and execution.
And if Pence and the cabinet aren’t going to address this, then it’s up to Congress to remove Trump from the ability to hurt this country.
All of them — Pence, the cabinet members and principal officers, members of Congress — have sworn an oath to the Constitution. It’s time to protect and defend it by removing Trump from office immediately.
Call your representative and ask them to support articles of impeachment because Trump has incited seditious behavior against the U.S. and he is acting increasingly unstable.
Call your senators and ask them to convict and remove Trump from office upon the presentation of the articles of impeachment from the House because Trump has incited seditious behavior against the U.S. and he is acting increasingly unstable.
Congressional switchboard: (202) 224-3121 — or use Resist.bot.
Time’s of the essence. Go. Leave word in comments if you’d care to share your experience.
~ ~ ~
UPDATE-2 — 10:42 PM ET —
Update on status of impeachment:
House Judiciary Committee Chair Jerry Nadler supports impeachment and wants it to go directly to the House floor:
I am once again urging that President Trump be impeached and removed from office. We have a limited period of time in which to act. The nation cannot afford a drawn out process and I support bringing articles of impeachment directly to the House floor.https://t.co/xpuFwaLTC0
— Rep. Nadler (@RepJerryNadler) January 7, 2021
Head count is mounting.
Now over 200+ House and Senate members calling for Trump's removal via 25A or impeachment per our ongoing tally by @bkamisar @Ed_Demaria @mel_holzberg.
— Benjy Sarlin (@BenjySarlin) January 8, 2021
The number 200 without context means doodley squat. We need two very specific numbers.
We need 218 House votes, or one more than half of 435. (This may be lower because there are two seats still open IIRC.)
We need 67 Senate votes, or two-thirds of the total 100 seats.
If you manage to reach your representative or senators, ask where they stand on impeaching Trump. Then ask them to support it if they don’t, or thank them if they do.
I hope we have the numbers by morning. What could go wrong the longer Congress drags its feet is incalculable.
~ ~ ~
UPDATE-3 — 12:52 AM ET 08-JAN-2021 —
Two cabinet members, Transportation Secretary Elaine Chao and Education Secretary Betsy DeVos, have tendered their resignations. Chao’s exit is effective January 11; I haven’t checked DeVos’s exit date. Her resignation could have been effective immediately. Former White House Chief of Staff Mick Mulvaney resigned from his role as Special Envoy for Northern Ireland. Four national security aides quit.
A police officer has died of injuries sustained during the Capitol Building riot. That’s more dead police than the entirety of George Floyd/BLM protests during the summer of 2020.
A family member acknowledged the death of a 34-year-old woman who participated in the Capitol Building riot but was crushed to death. She was likely one of the three accidental deaths tallied so far.
Displeased cabinet and staff members, dead police and mob member…not good, but there was something worse afoot.
Read this entire Twitter thread. And then recall the conspiracy against Michigan’s Gov. Whitmer.
WOW: Was there a plan to take hostages? This man is carrying police-style zip-tie handcuffs. And mace(?) pic.twitter.com/np3i1pUc6n
— John Scott-Railton (@jsrailton) January 7, 2021
Several accounts on Twitter have noted the rioters could be sorted into two groups: the tourist mob who did sightseeing and some vandalism, and some crypto-paramilitary persons who were prepared to do more than simply take selfies and smash furniture. They came armed with knives and zip ties and may have had more weapons on their persons. They were better masked than most of the tourist rioters.
There have been videos shared which appear to show Capitol Police actively encouraging the mob. Off-duty officers may not only have participated in the rioting but aided the paramilitary participants.
And there have been repeated remarks about coming back on the 19th — “I’d do it again, and I’d have a gas mask next time.”
We should not forget there were two IEDs found, one at each of the RNC and DNC offices, as well as a suspicious vehicle which has been characterized as mobile bomb factory.
There were elements inside the rioters who wanted to do more damage and possibly seize and hurt members of Congress along with VP Pence.
We don’t know if they left any preparatory materials behind or whether law enforcement did an adequate sweep considering how poorly prepared they were for the breach of the Capitol Building by rioters.
Trump must be impeached before he can encourage worse. His statement this evening suggests he is willing to encourage more seditious acts, like those at statehouses across the country yesterday while a mob rioted inside the Capitol Building.