Three Things: No News Isn’t Good News
[NB: check the byline, thanks. /~Rayne]
This last several weeks have made the media look really bad. You’d think after several key stories broke there’d be more and deeper coverage but nope.
U.S. media, Congress, and the citizens who elected them each own some of the media fail. Why aren’t we demanding more protection of our personal data in order to protect our democracy?
~ 3 ~
The New York Times published a story on March 28 about the acquisition of the former LIFE magazine assets and the defunct magazine’s resuscitation.
Life Magazine Will Come Back to, Well, Life
The investor Josh Kushner and his wife, Karlie Kloss, have struck a deal with Barry Diller’s media company to revive it as a regular print title.
By Andrew Ross Sorkin, Ravi Mattu, Bernhard Warner, Sarah Kessler, Michael J. de la Merced, Lauren Hirsch and Ephrat Livni
Nowhere in this puff piece a mere 404-words long written by at least one of seven contributors on this byline mention that Josh Kushner is Jared Kushner’s brother.
Nowhere in this heavily-laden beat sweetener is it mentioned that Josh and Jared share ownership of a problematic real estate management company, and that both met with Saudi and Qatari officials during the Trump administration.
Nowhere in this fluff is financing mentioned. Apparently it never occurred to one or more of seven journalists to ask if brother Jared contributed financing or guidance in any way.
We, the readers, are apparently supposed be very happy an attractive model and her now-billionaire spouse are reviving an old American media institution. We’re supposed to assume Kushner and Kloss are wholly financing this project out of their own pockets through their Bedford Media holding out of an appreciation for LIFE.
Why ever would we want to know more? As if we’d expect news from NYT.
~ 2 ~
It’s as if the Ronna McDaniel scandal never happened. There’s been no reported news about her since NBC canned her after MSNBC personalities protested her hiring on air.
I’ve been watching for any news about separation from Creative Artists Agency, who dropped her the same time she was terminated at MSNBC. CAA didn’t keep her on, as if they felt there was no hope of future contracts for her at all, even with right-wing news media.
Nada, not a word has emerged about CAA’s rejection. Just a spattering of op-eds in favor or against McDaniel’s separation from NBC.
One thing which has gone utterly unnoticed by journalists covering U.S. politics and media: a French conglomerate acquired majority interest in CAA last September, with two other foreign firms retaining substantive interest in the firm.
The Pinault Group closed on the deal while Singapore-based Temasek and Shanghai-based CMC Capital retain minority interests.
There are plenty of reasons for McDaniel to have lost her gig on NBC as well as her representation by CAA, like being an unindicted co-conspirator in Trump’s effort to defraud the U.S. and deny U.S. voters their civil rights.
But it doesn’t hurt to ask if foreign interests played a role in her representation or loss thereof. Perhaps a French-owned company doesn’t care to keep a talent who supported a NATO-undermining former president’s attempt to overthrow the U.S. government.
~ 1 ~
For decades there have been restrictions on foreign ownership of broadcast media. It’s about time we began to ask why we don’t have similar restrictions on social media, when social media has become a primary source for news in the U.S. for nearly half of Americans.
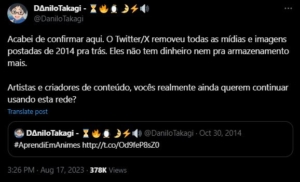
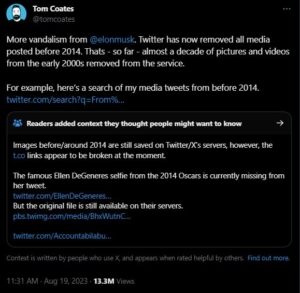
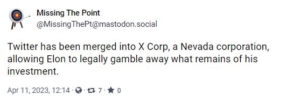
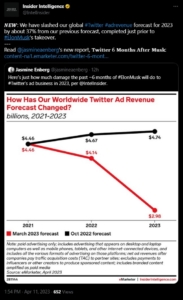
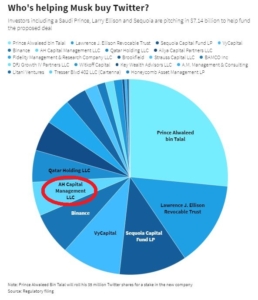
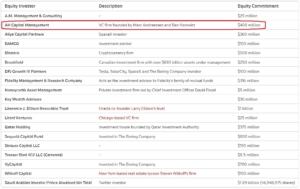
Twitter’s acquisition by Elon Musk, funded substantially by foreign interests, is one example. Since its sale, the former Twitter has become one of if not the largest source of misinformation and disinformation in U.S. media consumption. It’s difficult not to assume this is the reason Musk’s financial backers ponied up the money for an otherwise money-losing business.
Grindr, a social media platform for gay and bisexual men, and transgender people, was launched in the US in 2009. A majority interest was sold to a Chinese gaming company, Kunlun Tech Co. Ltd. in January 2016. Kunlun sought a buyer for Grindr after Committee on Foreign Investment in the United States (CFIUS) notified Kunlun in March 2019 its foreign ownership of Grindr posed a national security threat.
Now many are watching stock price vacillations for Donald Trump’s Truth Social social media platform, owned by Trump Media & Technology Group Corp. (TMTG), the entity which succeeded the former special-acquisition corporation Digital World Acquisition Corp. (DWAC). DWAC had been associated with Chinese-owned ARC Capital and China Yunhong Holdings, both of which had some role in financing DWAC.
TMTG has been under investigation by the Department of Justice since 2022 for possible money laundering after TMTG had received a loan from Paxum Bank, partially owned by Russian Anton Postolnikov. It’s not clear why TMTG was able to list on a U.S. stock market exchange given the possibility this loan may have violated sanctions against Russian interests.
TikTok is owned by a Chinese firm and its users’ data is stored in China. It’s not the content but the location and control of U.S. users’ data which is and has been most problematic, though it’s easy for TikTok’s Chinese parent to manipulate what U.S. users will see including misinformation and disinformation. Trump’s former Treasury Secretary Steve Mnuchin has been trying to pull together a consortium to buy TikTok, but TikTok may have no interest in selling out, and it’s not clear if Mnuchin will end up seeking more foreign investors as Elon Musk did.
If Mnuchin – who met with Middle Eastern leaders during his stint as Treasury Secretary and departed with $1 billion in Saudi cash for his Liberty Strategic Capital fund — manages to pull off buying TikTok, what will he do with users’ data since the future business model is unclear at this time. Will he sell it to offshore buyers including hostile nation-states since there are few restrictions now preventing such sales? TikTok would be as much of threat under such a business model as it is now.
We need federal legislation to regulate not only users’ data privacy – all social media created by U.S. users should be kept inside the U.S. – but to limit control of social media firms by foreign owners, especially hostile nation-states.
Why was Grindr, of all the social media platforms which have been sold in whole or part to overseas parties, the one which drew attention from CFIUS? Especially after Twitter had been infiltrated by multiple Saudi spies, one of which were prosecuted before Musk made an offer to buy the platform? What foreign spies now have access to U.S. citizens and users’ personal data after Musk shit canned so many of Twitter’s pre-acquisition personnel?
This isn’t a First Amendment issue. It’s regulation of commerce, and commerce conducted inside the U.S. relying on U.S. citizens and residents as consumers and data sources shouldn’t pose a threat to national security.
~ 0 ~
This is an open thread. In addition to media criticism, bring your stray cat and dog topics here.