FISA “Physical Searches” of Raw Traffic Feeds, Hiding in Plain Sight?
I’m still trudging through NSA’s reports to the Intelligence Oversight Board, which were document dumped just before Christmas. In this post, I want to examine why NSA is redacting one FISA authority, starting with this section of the Q1 2011 report.
During that period, the reports grew to have a bit more structure (this may have been Matt Olsen’s doing, who took over as NSA GC in 2010). Here’s what that Q1 2011 report looks like:
- Violations
- EO 12333 violations
- FISA violations
- Unauthorized data retention
- Consensual collection
- Unauthorized retention of COMSEC
- Computer Network Exploitation (aka hacking, a section which is always entirely redacted and keeps growing in size)
- Counterintelligence
- Intelligence-related
- OIG Inspections
- Substantive changes to Intelligence Oversight
- Changes to directives and policies
- Procedures
The key change, though, is that the FISA section breaks down by authority, like this, as seen in the Q1 2012 report, which is the most complete example of this
- NSA/CSS Title I FISA
- [redacted]
- BR FISA (phone dragnet)
- PRTT (Internet dragnet)
- FAA
- 702
- 704
- 705(b)
After that Q1 2011 report, every single report has that redacted category in the same spot, and every single report redacts it (though I suppose it is possible that whatever is redacted there changes).
I wondered, briefly, if that meant NSA was using a secret authority, some new program that egregiously interpreted a law in a way no one could imagine, just like NSA redefined Section 215 and PRTT. But I don’t think that’s right.
Rather, I think NSA is making a rather pathetic effort to hide that it uses FISA’s physical search provision to obtain emails and other data “stored” in the cloud.
Remember that intercepts (50 USC 1806, which is subchapter I of FISA) and physical search (50 USC 1821, which is subchapter II) are different authorities under FISA, each requiring notice to defendants, though they are usually noticed in the same filing (as here to Reaz Qadir Khan). While it’s possible the redacted authority instead designates a different agency (remember that FBI is the front end on a lot of Internet collection), the analysts referred to in these sections are described as NSA analysts. So I suspect it distinguishes between the two types of individualized FISA orders. And it’d be hard to believe there were no IOB violations under 1821, so it must be there somewhere.
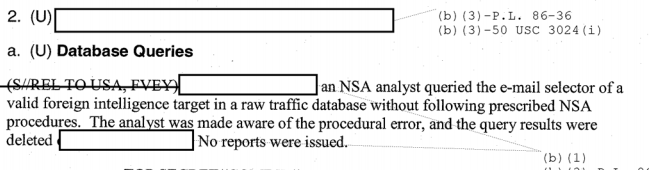
Further, I suspect NSA is hiding what appears in some of these reports as a redacted unclassified detail because the descriptions make it clear NSA is querying out of raw traffic databases.
Here’s a summary of the violations noted for this redacted authority:
Analyst queries email selector of valid foreign intelligence target in raw traffic database without following procedure.
Analyst erroneously targets email selector.
Nothing to report.
Nothing to report.
Analyst cleaning out a newly assigned office found a FISA-derived document from some time ago.
Data was sent to a server that was not authorized to hold FISA data.
NSA discovered 12 analysts had access to a database for which they had not completed required training.
A routine audit revealed an analyst had made two poorly constructed queries.
“An NSA analyst mistaken accessed [redacted] data. The analyst was authorized to view [redacted] data but had not completed the minimization training required by the FISC order. Access to the data has been restricted to database administrators while database capabilities to restrict access are reviewed.”
NSA notified DOJ that a number of queries had not been reviewed. NSA analysts have been reviewing and reconciling past queries.
An auditor discovered that an analyst had run a database query that included something impermissible.
An NSA analyst discovered an overly broad database query.
An auditor determined an analyst had queried a raw traffic database before conducting required research.
An NSA analyst forwarded information in an email the analyst was no longer authorized to receive.
Nothing to report
“An analyst executed a query of identifiers provided to NSA by [redacted] with a high risk of terrorist connections.” He appears to have been unaware of something about the query and so destroyed the results.
Analysts may have been able to see data they did not have authorization (training) to see.
These all seem query driven. And at least some of them access “raw traffic databases.” Mind you, there are some Title I violations that also include raw traffic databases (see the database violations in Q2 2011, Q2 2012, and Q1 2013, as well as the unauthorized retention and access violations in Q4 2012, though the retentions violation discusses “authorizations” and so may cross authorities).
There are not, however, any discussions of tasking and detasking violations under the redacted authority, which are the most common kind of violation under FISA. That either suggests the redacted authority collects no communications in real time (which would accord with my understanding of how the NSA has been using physical searches to get data stored on a cloud) or it is not dependent on US presence (which might mean this access data collected overseas on people in the US).
Note, there are also no mentions of telephony traffic under the redacted authority, whereas many, though not all, of the Title I authority violations involve phone traffic (which of course would be harder to get from a stored location).
The other thing the comparison of Title I with this redacted authority makes clear is that there is a special set of minimization procedures for the authority.
This is just a guess, but I’m wondering whether what this redaction hides is the use of physical search orders to permit the search of XKeyscore data, which may either be collected here or overseas. If so, it’d be an interesting question of whether a 5 to 30 day buffer represents communication stored in a physical space.
In any case, given that NSA is hiding reference to an authority that is clearly marked as unclassified, it seems ACLU ought to be able to convince a court to liberate the reference.
Defense attorneys barely realize the government uses physical search orders to get cloud content. If they’re using it to do something like access a temporary XKS buffer, then it would raise really interesting Fourth Amendment questions. Which may well be why NSA is hiding it.


Thank You plain site is always best on the intrertubles
Considering what you are presenting in the scope of this article:
.
https://www.techdirt.com/articles/20141224/14510929524/when-fisa-court-rejects-surveillance-request-fbi-just-issues-national-security-letter-instead.shtml
.
it is surprising they are trying to hide it when they can ask their friendly cohorts to get it for them. Maybe that inter-agency cooperation has some limits too.
No offense but that’s a dumb article. The IG Report was originally released years ago–we’ve known about it since then and FBI claims to have fixed this. There are other concerns about NSLs that have replaced them.
Oh, I agree, the article is waaaay past its shelf life’s expiration date. The ideas raised though that the IC is worried about actual accountability happening is strange given how the options for oversight are quickly closing down. That article is an inept reminder, but still a reminder.