The Two Intelligence Agency Theory of Handing Trump the Election
There has been a lot written about Russian intelligence agencies allegedly hacking the DNC server and — by leaking it — attempting to influence the election. Some observers have, based on that assumption, called the hack an act of war.
I’m agnostic on whether Russian intelligence did one or both of the hacks, in part for reasons I’m still working through. I’m even more skeptical of some of the claims made about Russia’s motivations in launching this attack to put Trump in the presidency (which is not to say Trump wouldn’t be horrible for a whole slew of other reasons); on that topic, see this Josh Marshall piece and a fact-checking of it. And I’m frankly amused that, after using several other outlets for publicity and to release documents, the hacker(s’) cooperation with WikiLeaks (which irresponsibly released credit card and social security information on Democratic donors, but which almost certainly had its donors investigated by DOJ with the heavy involvement of Clinton after Wikileaks published the State cables) itself is a sign of Russian involvement. Does Russia also run The Hill, the last outlet used by DNC hacker(s)?
In short, there are a whole bunch of claims being made, all serving a narrative that Putin is playing in our elections, with little scrutiny of how you get from one level (what have been described as two separate hacks) to another (to Guccifer 2, to help Putin) to another (with the help of Wikileaks). It’s like the Rosetta stone of Cold War 2.0 paranoia. All may be true, but the case is thus far still fragile.
This post, from Thomas Rid, is the most sober analysis of the claim that Russian hackers hacked the DNC. Even still, there are some logical problems with the analysis (that are sadly typical of the underlying cybersecurity consultants). Take these two passages, for example.
The DNC knew that this wild claim would have to be backed up by solid evidence. APost story wouldn’t provide enough detail, so CrowdStrike had prepared a technical report to go online later that morning. The security firm carefully outlined some of the allegedly “superb” tradecraft of both intrusions: the Russian software implants were stealthy, they could sense locally-installed virus scanners and other defenses, the tools were customizable through encrypted configuration files, they were persistent, and the intruders used an elaborate command-and-control infrastructure. So the security firm claimed to have outed two intelligence operations.
[snip]
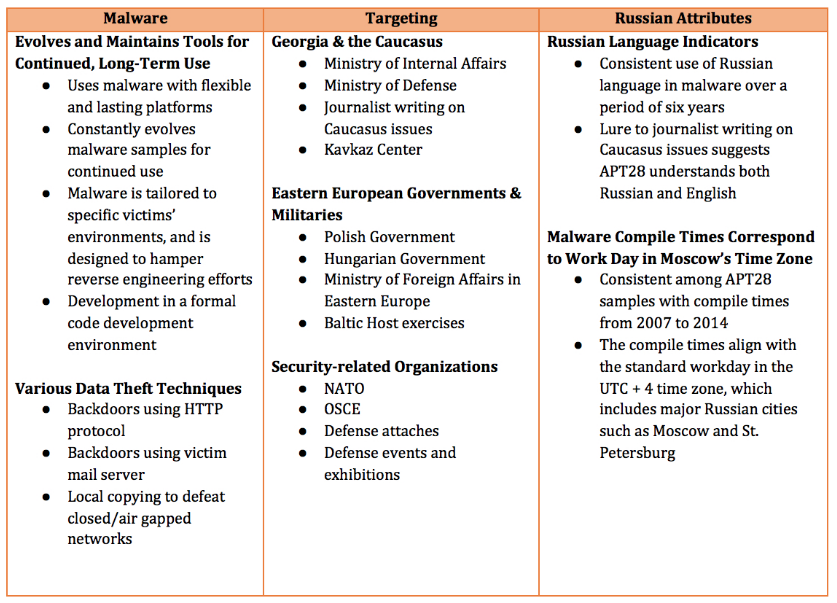
The metadata in the leaked documents are perhaps most revealing: one dumped document was modified using Russian language settings, by a user named “Феликс Эдмундович,” a code name referring to the founder of the Soviet Secret Police, the Cheka, memorialised in a 15-ton iron statue in front of the old KGB headquarters during Soviet times. The original intruders made other errors: one leaked document included hyperlink error messages in Cyrillic, the result of editing the file on a computer with Russian language settings. After this mistake became public, the intruders removed the Cyrillic information from the metadata in the next dump and carefully used made-up user names from different world regions, thereby confirming they had made a mistake in the first round.
They argue (based in part on CrowdStrike’s claims of expertise) both that the hacker(s) were really sophisticated and that they deliberately adopted a Russian name but accidentally left Russian metadata in the files. Particularly with regards to the Russian metadata, you don’t both adopt a notable Russian spook’s ID while engaging in a false flag but then “accidentally” leave metadata in the files, although the second paragraph here pertains to Guccifer 2 and not the Crowdstrike IDed hackers.
If Guccifer were a true false flag, he might well be pretending to be Russian to hide his real identity.
Add to that this post (from June), which notes some confirmation bias in the way that FireEye first attributed APT 28 (which CrowdStrike believes to be GRU, Russia’s military intelligence).
I chose to look at Fancy Bear (APT28 in FireEye’s ecosystem). The most comprehensive report on that threat actor was written by FireEye and released last October, 2014 so I started with that. To my surprise, the report’s authors declared that they deliberately excluded evidence that didn’t support their judgment that the Russian government was responsible for APT28’s activities:
“APT28 has targeted a variety of organizations that fall outside of the three themes we highlighted above. However, we are not profiling all of APT28’s targets with the same detail because they are not particularly indicative of a specific sponsor’s interests.” (emphasis added)
That is the very definition of confirmation bias. Had FireEye published a detailed picture of APT28’s activities including all of their known targets, other theories regarding this group could have emerged; for example, that the malware developers and the operators of that malware were not the same or even necessarily affiliated.
And even if you took the underlying report as definitive, APT 28 was primarily focused on military targets, which by itself ought to raise questions about why they’d go after the DNC.
To make the argument based on targets that APT 28 is GRU you need to do even more adjusting of motivation (though more recent APT 28 attributed attacks are more similar to this one).
But one reason I find the Rid piece sober and useful is it emphasizes something that has been ignored by much of the inflamed reporting. First, even CrowdStrike claims that DNC was hacked twice, by two different Russian entities, which did not appear to be coordinating during the hack. From the CrowdStrike report:
At DNC, COZY BEAR intrusion has been identified going back to summer of 2015, while FANCY BEAR separately breached the network in April 2016. We have identified no collaboration between the two actors, or even an awareness of one by the other. Instead, we observed the two Russian espionage groups compromise the same systems and engage separately in the theft of identical credentials. While you would virtually never see Western intelligence agencies going after the same target without de-confliction for fear of compromising each other’s operations, in Russia this is not an uncommon scenario. “Putin’s Hydra: Inside Russia’s Intelligence Services”, a recent paper from European Council on Foreign Relations, does an excellent job outlining the highly adversarial relationship between Russia’s main intelligence services – Федеральная Служба Безопасности (FSB), the primary domestic intelligence agency but one with also significant external collection and ‘active measures’ remit, Служба Внешней Разведки (SVR), the primary foreign intelligence agency, and the aforementioned GRU. Not only do they have overlapping areas of responsibility, but also rarely share intelligence and even occasionally steal sources from each other and compromise operations. Thus, it is not surprising to see them engage in intrusions against the same victim, even when it may be a waste of resources and lead to the discovery and potential compromise of mutual operations.
And, as Rid points out, the proof that Guccifer is tied to Russia (it would be to GRU or APT 28 if the tie were real, so the less persistent of the two apparently unrelated hacks) is even less clear, though there still is a lot of circumstantial evidence.
The evidence linking the Guccifer 2.0 account to the same Russian operators is not as solid, yet a deception operation—a GRU false flag, in technical jargon—is still highly likely. Intelligence operatives and cybersecurity professionals long knew that such false flags were becoming more common. One noteworthy example was the sabotage of France’s TV5 Monde station on 9/10 April 2015, initially claimed by the mysterious “CyberCaliphate,” a group allegedly linked to ISIS. Then, in June, the French authoritiessuspected the same infamous APT 28 group behind the TV5 Monde breach, in preparation since January of that year. But the DNC deception is the most detailed and most significant case study so far. The technical details are as remarkable as its strategic context.
[snip]
Other features are also suspicious. One is timing, as ThreatConnect, another security company, has pointed out in a useful analysis: various timestamps indicate that the Guccifer-branded leaking operation was prompted by the DNC’s initial publicity, with preparation starting around 24 hours after CrowdStrike’s report came out. Both APT 28 and Guccifer were using French infrastructure for communications. ThreatConnect then pointed out that both the self-proclaimed hacker’s technical statements on the use of 0-day exploits as well as the alleged timeline of the DNC breach are most likely false. Another odd circumstantial finding: sock-puppet social media accounts may have been created specifically to amplify and extend Guccifer’s reach, as UK intelligence startup Ripjar told me.
Perhaps most curiously, the Guccifer 2.0 account, from the beginning, was not simply claiming to have breached the DNC network—but claiming that two Russian actors actually were not on the DNC network at the same time. It is common to find multiple intruders in tempting yet badly defended networks. Nevertheless the Guccifer 2.0 account claimed confidently, and with no supporting evidence, that the breach was simply a “lone hacker”—a phrasing that seems designed to deflect blame from Russia. Guccifer 2.0’s availability to the journalists was also surprising, and something new altogether.
The combative yet error-prone handling of the Guccifer account is in line with the GRU’s aggressive and risk-taking organizational culture and a wartime mindset prevalent in the Russian intelligence community. Russia’s agencies see themselves as instruments of direct action, working in support of a fragile Russia under siege by the West, especially the United States.
Now, again, I’m not saying the Russians didn’t do this hack, nor am I dismissing the idea that they’d prefer Trump to Hillary. By far the most interesting piece of this is the way those with the documents — both the hackers and Wikileaks — held documents until a really awkward time for some awkward disclosures, with what may be worse to come.
But discussions that want to make the case should explain several things: Which of the two agencies alleged to have hacked DNC are behind the operation — or are they both, even though they weren’t, at least according to the report that everyone is relying on without question, apparently cooperating? How certain can they be that the GRU is Guccifer, and if Guccifer is supposed to be a false flag why was it so incompetently done? What explains Guccifer’s sort of bizarre strategy along the way, encompassing both Wikileaks (an obvious one) and The Hill?
Again, I absolutely don’t put this kind of thing beyond Putin. Russia has used hacking to influence outcomes of elections and authority in various countries in the past and the only thing new here is that 1) we wouldn’t already be playing the other side and 2) we’re big and can fight back. But the story, thus far, is more complex than being laid out.
Update: Here’s an amusing debunking of a lot of the metadata analyses.
Meanwhile, after the WaPo story hit the wires the “lone hacker” created his wordpress site and dropped dox as we say on the intertubes. Shortly after the drop people were inspecting, detecting, infecting, and making circles and arrows with captions on the back to describe what you were seeing! … And the conspiracy theory machine went into overdrive. Pwnallthethings made some good comments on the metadata in the dropped dox but really, concluding that this is a Russian disinformation operation from metadata stripped documents on the idea that the machine name was cyrillic for Felix Dzerzhinsky (Феликс Эдмундович) Really? Now that is fucking SOLID work man! Stellar! FUCK LET’S GO BOMB RUSSIA NOW!
NAILED IT!
You know at least Crowdstrike has like actual data, ya know, C2’s, malware, and shit like that. Anything else is totally speculative, I mean even more speculative than most attribution that these companies make with real data! Anyway, I took a look at the metadata on the documents and here is what I have found…
- Much of the data was stamped out in saving from format to format
- Emails of users though were still embedded in the excel files
- The word docs have no more metadata than the Iron Felix machine name save, which, gee, kinda leads one to wonder…
- The image files have no metadata.. none.. niente clean.
- Grizzli777 is just someone who pirates
Yep, not a lot to see there and people are hanging their collective hats on the deliberate placement of Феликс Эдмундович as the machine name to it’s quite OBVIOUSLY being Mother Russia’s exclusive secret services.
*squint.. takes drag of cigarette*
So here’s my assessment…. Maybe Russia did it… OR Maybe this actor is the real thing and happens to want to take credit. The facts that this person(s) reads, writes, has, cyrillic on their machine and names it after the founder of the KGB is as reliable a means to saying it was Russia as it is to say that aliens built the pyramid because people just were fucking too stupid back then!



The Russians have very little interest in the DNC. It is an indication of the self centredness of the US politico-media matrix that it regards these minor internal matters as of international interest.
If Russia cared about stopping the Clinton candidacy it would have released these emails much earlier, before Sanders’ endorsement and in time to be used organising protests at the Convention.
emptywheel wrote,
.
“I’m agnostic on whether Russian intelligence did one or both of the hacks, in part for reasons I’m still working through. I’m even more skeptical of some of the claims made about Russia’s motivations in launching this attack to put Trump in the presidency (which is not to say Trump wouldn’t be horrible for a whole slew of other reasons); on that topic, see this Josh Marshall piece and a fact-checking of it.”
.
1. So, you agree with emptywheel?
.
2. If Putin wanted Trump, why release the emails early, when Sen. Sanders can still get the nomination? He was polling better against Trump than Sec. Clinton.
.
2.1 Are you assuming that there will be no more leaks? Is so, on what basis?
All I know is blaming Putin (and WikiLeaks by association) is awfully convenient for the DNC. It detracts from their own incompetence when it comes to computer security (which should really be the story here) and adds to the fear of Trump, which is apparently the only selling point Team Hillary has. Plus we all know WikiLeaks is an Official Enemy of the U.S. government, in part for making Hillary’s State Department look bad, so why not say they’re in cahoots with Putin?
Great read, extremely accessible.
.
Loved,
.
“It’s like the Rosetta stone of Cold War 2.0 paranoia. All may be true, but the case is thus far still fragile.”
I’ve got to agree with bevin, I’m also convinced that this is all a smoke-screen dreamed up by the Clinton campaign to deflect and redirect the anger about the content of these emails. They’ve made DWS the fall-person for any DNC problems, and now they’re propagating the message that ‘Putin is more afraid of Clinton than Trump’. This would tend to help her campaign, as well as change the topic from the contents of the emails to what bad actors the Russians are. What they DON’T want to do under any circumstances is look at the emails themselves, and talk about how DWS wasn’t doing it for her own personal campaign, she was doing it on Clinton’s behalf. Remember that this wouldn’t be a big deal if the DNC had just been fair, the emails would just be a bunch of boring details about ‘deliver these supplies here…” and “..we need more toner for the laser printer…”
I always fall back to the basic questions of criminal investigation…who has motive, method and opportunity? Does Russia really stand to gain by DNC turmoil? Really? They’d be happiest with another $20/barrel for oil. I think the Clintons are trying to find any alternative narrative (other than rigged DNC) to hang this on, and one that tends to make Hillary look like the ‘tougher on Russia’ candidate is all the better.
I’m not convinced that the Russians weren’t involved, and one cannot ignore Josh Marshall’s observations. While I do not consider the bromance of Trump and Putin to be a key issue, the fact that we all know (even though the Trumpbots don’t care) that Trump has significant issues in his various dealing s is important.
*
The key thing for any sort of intel operation is to be able to leverage your target. If it is one thing that is a silver lining for HRC, the GOP witch hunt has put pretty much everything out there that would be significant enough to force HRC to bend to Putin’s will. In Trump, there is so much slime there between bankruptcies, Mob ties, etc., that Putin (and the Chinese before them with Shrub) can use to get Trump to act against America’s best interest. That Trump has business relationships with the Russians that are not entirely savory is known, and the KGB is well known for its policy to blackmail its targets.
*
This is one of the things so far missed about Trump’s NATO fiasco, it is a clear signal to Putin that the Baltics are fair game. The USA didn’t even recognize the Soviet takeover of the Baltics in the beginning of WW2. If one takes this to its logical conclusion, it also means that the Taiwanese are on their own (and Japan and the ROK as well) because all of these states with whom the USA has mutual defense treaties are for sale at the right price if Trump is elected.
I follow where you’re going, and under normal circumstances, that would all be correct. It’s just that The Donald doesn’t care about slime. Bring up his infidelity, and he’ll either turn it into a bragging point or dump on the woman for her ‘poor skills’. I don’t think that there’s anything that would shame that man or get his voters to change their minds. Remember that he even bragged about being able to murder someone and still get elected. These aren’t normal times.
I’m not convinced that the Russians weren’t involved, and one cannot ignore Josh Marshall’s observations.
You can surely take it with a heaping spoon of salt though.
Two of the easiest ways to gain control of a target involves money and sex. On the latter possibility we have the Donald’s well known series of infidelities over the years. However, I personally think it would be less likely until AFTER the election at which point Trump would have the embarrassment analogous to Silly Billy with the risk that the Congress would impeach him as they impeached Bill Clinton. This scenario of course assumes that Trump can be shamed by a sex scandal (no) and that GOP members of Congress will have consistent standards for morality and outrage (Hahahahahaha – no). So, I think a bimbo eruption (via a KGB “swallow”) will not work as it otherwise would.
*
The money angle, on the other hand is a serious issue for our narcissistic GOP nominee, and the fact that he refuses to open the books makes it clear he feels there is too much to lose relative to the effect of questions on the campaign. In my view this sets up a classic leveraging opportunity for Putin, especially since Donald Jr. has already acknowledged significant Russian holdings and Trump’s ego and id are fully wrapped up in his self-proclaimed business acumen. It would be the worst thing in the world to have it revealed for all to see that Trump was a two-bit con artist who was even more of a business failure than the guy who couldn’t find oil in Texas (Shrub’s Arbusto).
Blaming Russia fits right into their continuing march to war. It is simply to refocus the issue onto another looming issue. It is stupid to think that a hacker residing in a country is working for Putin. Oh, let me back that one up. The US does it all the time. However, where the hacker is from is not the issue. It is subversion of Democracy and a National election that is the real issue.
For those that have known me for years, I will say this. The US and NATO are mad as HELL that Russia has worked out ways to get around the sanctions they placed on the country. They are also angry because Putin agreed to handle the mess in Syria and he actually did. LOL They quickly told him to STOP! Remember, Russia has a huge interest in Lybia, Syria, and Lebanon, due to naval bases and transport. The US and NATO are drumming up war as hard as possible without showing their hand. Just keep this in mind. I am not taking up for Putin. Just trying to make folks more aware of the recent hype and why.
I do not think that the DNC email controversy is all that much, although it is amazingly poor optics to even let DWS into any part of the HRC campaign. Let’s remember that Bernie was not a card-carrying Democrat, he caucused with the Democratic party in Congress. In my view, given the rot and complacency that exists with the establishment DNC members, Bernie’s popularity was a threat to their happy place. Remember that the MSM had to be shamed into inviting him to debates even though he polled 10x better than almost all of the GOP candidates even in the early days.
*
Bernie doesn’t hold back, so while he wasn’t pleased, by what the DNC apparently did he also wasn’t surprised (he’s seen many hatchet jobs attempted on him over the years) and IF he were really as pissed off as many of his supporters are, there is no way that Bernie would stay silent. He also realizes where the true threat to America lies, it’s a Trump presidency.
https://www.techdirt.com/articles/20160725/11391635062/wikileaks-leak-turkish-emails-reveals-private-details-raises-ethical-questions.shtml
See my comment. Another agrees.
My hypothesis is that it was the Russians. This was a warning shot. They are signaling that they have Hillary Clinton’s emails, which would tip the election.
I find it completely credible that Russia was behind the hacks given that Putin established and is controlling a de facto criminal enterprise that has a chunk of money tied up financing Trump’s deals. They’re invested in him. And when I say completely credible, I mean far more than the idea was created by Team Clinton. Exploited, maybe; created, no way.
The next big rat-fuck would be if the hackers have Trump’s tax returns, and leak them.
Applause, celebrations, great rejoicing!