DOJ’s Minor Desperation with MalwareTech
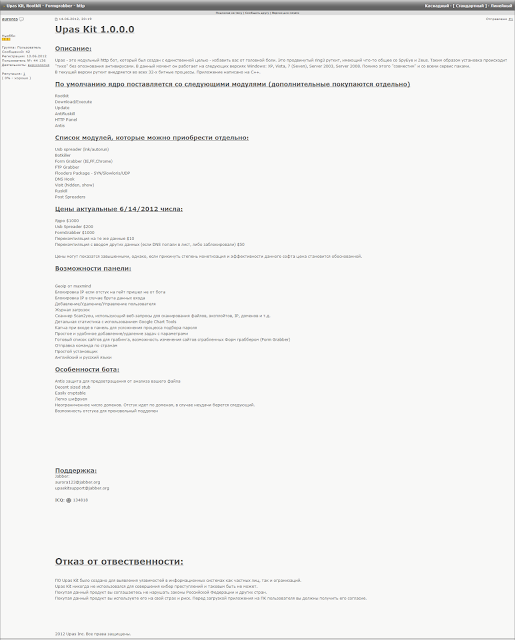
Best as I can tell (this is way not my forté — this was done with the help of S — so please recreate my work), this screen shot shows “auroras” selling UPAS Kit 1.0.0.0 on June 14, 2012.
June 14, 2012 was before Marcus Hutchins turned 18.
Some of the Russian translates as:
Upas is a modular http bot, which was created for the sole purpose – to save you from a headache. This is an advanced ring3 rootkit that has something in common with SpyEye and Zeus. Thus, the installation is “quiet” without recognition by antiviruses.Currently it works on the following versions of Windows: XP, Vista, 7 (Seven), Server 2003, Server 2008. In addition, it is “compatible” with all service packs.
[snip]
The Upas Kit was created to identify vulnerabilities in information systems of individuals and organizations.
Upas Kit has never been used to commit cyber crimes and it can not be so.
Buying this product, you agree not to violate the laws of the Russian Federation and other countries.
Buying this product, you use it at your own risk. Before downloading the application to the user’s PC, you must obtain its consent.
The support address is [email protected]. This matches the UPAS Kit described in Marcus Hutchins’ superseding indictment.
“UPAS Kit” was the name given to a particular type of malware that was advertised as a “modular HTTP bot.” UPAS Kit was marketed to “install silently and not alert antivirus engines.” UPAS Kit allowed for the unauthorized exfiltration of information from protected computers. UPAS Kit allowed for the unauthorized exfiltration of information from protected computers. UPAS Kit used a form grabber and web injects to intercept and collect personal information from a protected computer.
All of which is to say that when the superseding indictment describes the following as overt acts in the conspiracy to violate CFAA and to wiretap, it describes code placed on sale before Hutchins turned 18.
On or about July 3, 2012, [VinnyK], using the alias “Aurora123,” sold and distributed UPAS Kit to an individual located in the Eastern District of Wisconsin in exchange for $1,500 digital currency.
Now, as I said yesterday, it’s not clear what UPAS Kit is doing in the superseding indictment. Alone, the coding behind the listing above necessarily happened while Hutchins was a minor and the sale itself happened over five years ago. So the government can only present it as part of a conspiracy sustained by more recent overt acts, like the sale of Kronos in 2015, arguing they’re part of the same conspiracy, which extends the tolling (but doesn’t change Hutchins’ birthday).
Given the claim that he lied to the FBI in his Las Vegas interrogation, however, I think they’re suggesting that when he admitted to coding a form grabber, but not the one in Kronos, he was lying about knowing that this earlier code got used in Kronos.
Chartier: So you haven’t had any other involvement in any other pieces of malware that are out or have been out?
Hutchins: Only the form-grabber and the bot.
Chartier: Okay. So you did say the form-grabber for Kronos, then?
Hutchins: Not the form-grabber for Kronos. It was an earlier one released in about I’m gonna say 2014?
In other words, to get this admission into trial, the government is going to claim he was lying about knowing there was continuity between UPAS and Kronos in a way to deny any more recent involvement, even though they’re on the record (though Dan Cowhig’s statements to the court) that he had admitted that.
Which further suggests the evidence they have that he actually coded Kronos itself isn’t that strong, and need to rely on code that Hutchins coded when he was a minor to be able to blame this malware on him.





Part of their case is this idea of some kind of string dump via something of something which had the ASCII that says KRONOS (or Kronos? kronos? some other combo?) and made the claim only the author of kronos could ID it.
man hexdump man hd Now look at the output of something with the hd -c flag and ask ‘would only the creator of the object being hex dumped would be able to understand?’ Because that question is part of what FBI agent Chartier and his gallery posse is claiming “proves” their claims.
Something like this perhaps.
https://en.m.wikipedia.org/wiki/NSAKEY
Correct. They showed him a string and he didn’t recognize it but did recognize the word Kronos. That was one of the discussions in court that got some response from the peanut gallery.
And, of course, no one could have taken code he wrote as a minor and over the years incorporated new bits to make it do other things. It absolutely positively had to be a series of continuing illegal acts by Hutchins sufficient to make the statute of limitations irrelevant.
Tucker Carlson is a piece of work.
Conflates spygate with CI.
Will not let Painter explain.
Constant interruption.
Why does anyone talk to Fox talking heads?
Make sure you in vote 6 months.
Make sure you vote. No excuses.
I do not want to hear any bullshit. Just vote.
Ok, So I may be out of my realm here but, Can someone please explain why this analogy is not correct?
I write a sentence that says, “The President should surely ……” That sits around for a while and then a person then takes my sentence and adds more words such that the sentence now sounds threatening. The person who is caught publishing those words says he just got it from me and maybe added a few other words before publishing. Using the present DOJ rationale, am I now a member of a conspiracy?
Is it really that simple?
Humpty Dumpty logic.
https://en.m.wikipedia.org/wiki/Humpty_Dumpty
When I use a word,” Humpty Dumpty said, in rather a scornful tone, “it means just what I choose it to mean—neither more nor less.”
“The question is,” said Alice, “whether you can make words mean so many different things.”
“The question is,” said Humpty Dumpty, “which is to be master—that’s all.”
Shorter story. This is about Zeus malware and varients.
First spotted in 2007. Code ‘leaked’ in 2011.
Relies on http websites (not https) and javascript.
Via ad servers, easy to inject the attack into ones browser.
Then the attacker can steal credentials.
Sure looks like this is an attack on MH to provide cover. I do not believe it is to provide cover for FBI, BTW.
C’mon, Randy, fess up.
Guccifer 2’s West Coast Fingerprint
https://theforensicator.wordpress.com/2018/05/29/guccifer-2s-west-coast-fingerprint/
[Attribution is hard. But when one is trying to falsely attribute, one may leave metadata]
http://g-2.space/
https://theforensicator.wordpress.com/did-guccifer-2-plant-his-russian-fingerprints/
The choice of the RTF file format is unusual and surprising. RTF has not been in wide use for over 25 years. In fact, Word 2010 deprecated support for RTF. RTF is the only format that will retain the embedded Russian error messages that are found inside the final 1.doc document.