Behind the Arrest of Putin’s Pen-Tester, Vladislav Klyushin
There’s a gratuitous passage in the March 20, 2021 complaint charging Vladislav Klyushin, Ivan Yermakov, Igor Sladkov, Mikhail Irzak, and Nikolay Rumyantev with conspiracy to violate the Computer Fraud and Abuse Act. It describes that Klyushin — the guy just extradited to the US on the charges — possessing a picture of Alexander Borodaev and Sergey Uryadov posing in front of Scotland Yard in London.
Thus far, it’s unclear who the guys in the picture are, other than customers of M-13’s “investment services,” for which they paid extortionate 60% commissions to benefit from the insider trading scheme allegedly run by Klyushin and Yermakov. But, in addition to alerting Klyushin to how many of his personal files the FBI has obtained, folks back in Russia will have a taste of the kind of information at risk now that Klyushin is in US custody.
That is, this passage, and a host of others in the charging documents, appear designed to maximize the discomfort of a number of people involved, as much as justifying the arrest and extradition of the guy who led a company that provided services that amount to information operations to Vladimir Putin. As the DOJ presser explained,
M-13’s website indicated that the company’s “IT solutions” were used by “the Administration of the President of the Russian Federation, the Government of the Russian Federation, federal ministries and departments, regional state executive bodies, commercial companies and public organizations.” In addition to these services, Klyushin, Ermakov and Rumiantcev also allegedly offered investment management services through M-13 to investors in exchange for up to 60 percent of the profit
The insider trader scheme works like this: Klyushin (the guy in US custody) and Yermakov (a key person involved in the 2016 DNC hack, described in DOJ’s press release as a “former” GRU officer), along with one other guy from M-13, area accused of hacking at least two US filing agents to obtain earnings reports before they were officially released. They conducted trades for a handful of clients — along with Borodaev and Uryadov, Boris Varshavskiy is mentioned. Klyushin also conducted trades for himself. The three M-13 figures were indicted on conspiracy, hacking, wire fraud, and securities fraud charges on April 6, 2021, an indictment that formalized the extradition request for Klyushin, who had already been arrested in Switzerland.
Then there are two apparent private citizens who live in St. Petersburg, Michail Irzak and Igor Sladkov. They were indicted on May 6, 2021 on conspiracy to hack and hacking charges, along with securities fraud. That indictment (like the complaint) focuses on some different trades than the Klyushin one (and because neither is likely to be extradited anytime soon, the second indictment may shield some portion of evidence from discovery).
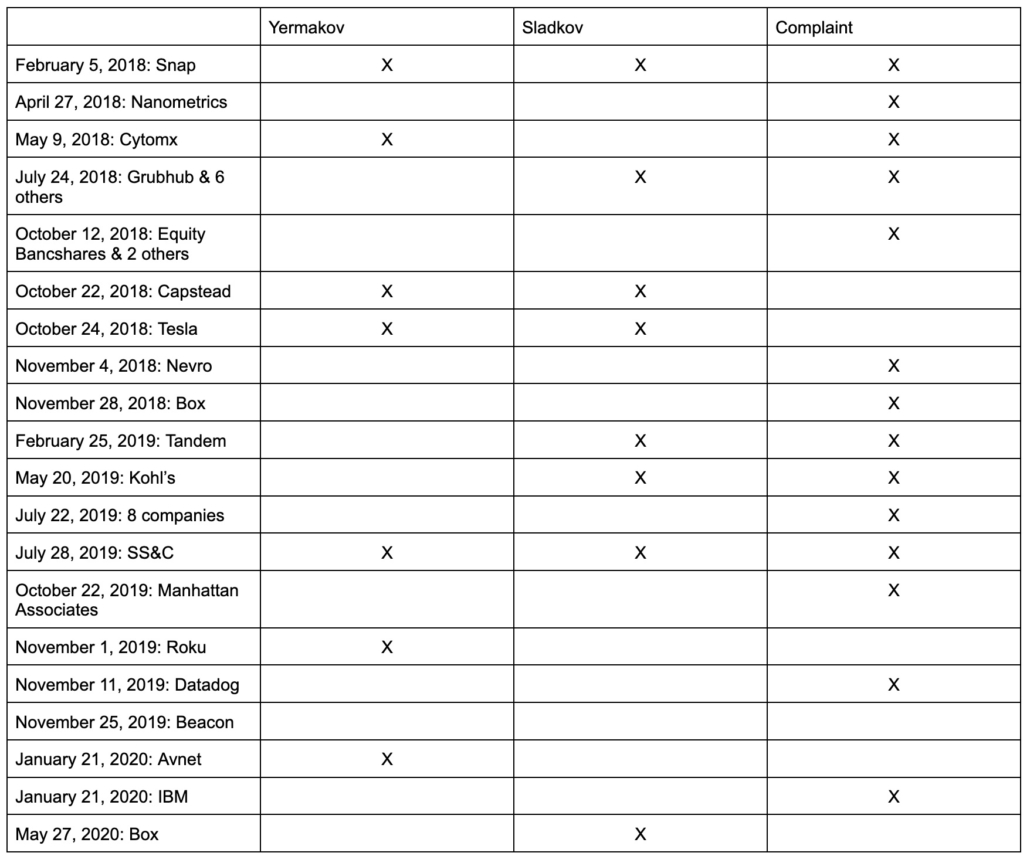
Actions attributed elsewhere to Yermakov are attributed to Co-Conspirator 1 in that indictment, and it is on that basis that Irzak and Sladkov are exposed to the hacking charges. Irzak and Sladkov don’t appear to have been paying the extortionate 60% fees that the other M-13 clients were, which makes me wonder whether Yermakov was helping buddies get rich on the side. Worse still, Sladkov had some epically bad operational security; the indictment describes he had in his possession pictures showing:
- A picture of a black Acer computer, with a blue Russian Olympic Committee sticker over the camera, showing a press release with Snap’s 2017 earnings that was not released publicly until 8 hours later.
- A picture showing the same Acer computer with the same blue sticker showing his own trading activity on BrokerCreditService on May 2, 2018
- A picture taken on July 24, 2018 at 2:05PM (ET) showing himself and Irzak sitting at a brown table; Irzak had Facebook running at the time, which showed him to be in the vicinity of Sladkov’s house
- A picture dated July 25, 2018 showing him trading in a bunch of shares the earnings reports of which had been illegally accessed the day before
- A picture dated October 14, 2018 showing a hand-written note instructing to “short” three shares, which Irzak did short two days later
In other words, Sladkov documented much of his insider training in photographs (perhaps to share the instructions with Irzak), and left all those photographs somewhere accessible to the US government.
If Yermakov was sharing this information with these guys without permission, then Sladkov’s role in providing the US government really damning information that would form the basis for an arrest warrant for Klyushin, then things might get really hot.
But it’s not like Klyushin or Yermakov did much better. In addition to the pictures of the clients, above, and some screencaps that got sent showing trading activity (though with less obvious evidence of insider trading), there’s a bunch of messaging from both, including an oblique reference to messages Yermakov and Borodaev sent on November 19, 2020 that have nothing to do with the context of the indictment but happens to be after the US election. There are even pictures Klyushin shared with Yermakov, “showing a safe that contained growing stacks of U.S. one hundred dollar bills.”
Yermakov appears to have used one of his messaging accounts via multiple devices, because on December 3, 2018, when he “forgot telephone at work,” he was still able to message Klyushin about closing out a trade. Using the same messaging app across platforms would offer one means of compromise, especially if the FBI had gotten into Yermakov’s device updates. The indictment doesn’t mention a warrant for such messaging that you would expect if it took place on Facebook.
Again, this indictment seems to aim to cause discomfort and recriminations based on information in US possession.
But then there’s the question of how it came about, how it landed in Massachusetts rather than DC (where the lead FBI agent is from) or NY (where the trades get done) or Pittsburgh, where one of the prior indictments against Yermakov was done.
The indictments and complaint base the MA jurisdiction on the fact that the culprits used a VPN that used a server in MA on several occasions. At a presser the other day, Acting US Attorney Nathaniel Mendell suggested the case had been assigned to MA because of its good securities prosecution teams.
As to how it came about, purportedly, the story starts in January 2020, when two filing agents allegedly hacked by the men, FA1 and FA2, reported being hacked at virtually the same time. Someone had used an FA1 employee’s credentials on January 21, 2020 to access the earnings data for IBM, Steel Dynamics, and Avnet before those results were publicly announced the following day, but no similar transaction noted with respect to F2 (indeed, a list of accesses involving F2 have a gap from November 2019 through May 2020). The investigation determined that FA1 had first been hacked by November 2018 and that FA2 had first been hacked by October 2017.
FA1 and FA2 discovered this compromise just months after the third M-13 employee, Rumyantev, was blocked by his Russian-based brokerage account for suspicious transactions. Months after FA1 and FA2 reported their compromise, Rumyantev and Klyushin lied to a Denmark bank that they were working entirely off of public information. By that point, in other words, banks in at least two countries were onto them.
Then, the story goes, the FBI investigated those hacks — through domains hosted by Vultr Holdings to a hosting company in Sweden to a user account under the name Andrea Neumann. From there, the FBI tracked back through some Bitcoin transactions made in October and November 2018 to the IP address for M-13 where they just happened to discover one of the very same hackers that was behind the 2016 hack of the DNC was also behind this hack. Mendell sounded pretty sheepish when he offered that explanation at the press conference.
Perhaps it’s true, but another key piece of evidence dates to actions Yermakov took on May 9, 2018, when he was under very close scrutiny as part of the twin investigations into his role in the hacks of the DNC and doping agencies, but before the first indictment against him was obtained.
Based on a review of records obtained from a U.S.-based technology company (the “Tech Company”), I have learned that on or about May 9, 2018, at 3:44 a.m. (ET), an account linked to ERMAKOV received an update for three native applications associated to the Tech Company. Records show that the May 9, 2018 application updates were associated to IP address 119.204.194.11 (the “119 IP Address”).
Based on my review of a log file from FA 2, I learned that on or about that same day, May 9, 2018, starting at 3:46 a.m. (ET)–approximately two minutes after ERMAKOV received application updates from the Tech Company–the FA 2 employee’s compromised login credentials were used to gain unauthorized access to FA 2’s system from the same 119 IP Address, and to view and/or download earnings-related files of four companies: Cytomx Therapeutics, Horizon Therapeutics, Puma Biotechnology, and Synaptics.7 All four companies reported their quarterly earnings later that day.
It would be rather surprising if the FBI agents investigating the DNC hack had not at least attempted to ID the IP associated with Yermakov’s phone (or other device) back in 2018. Whether or not they watched him engage in insider trading for years after that — all the while collecting evidence from co-conspirators flaunting the proof of their insider trading — we may never learn. The discovery on this case, featuring evidence explaining how the FBI tracked the insider trading of Putin’s pen-tester, will certainly feature a number of law enforcement sensitive techniques that Klyushin would love to bring back to Putin.
But it’s possible these techniques were what the FBI used to target these guys four years ago now, and the insider trading that Yermakov was doing in addition to whatever he spent the rest of his time doing has now provided a convenient way to bring Putin’s pen-tester to the United States for a spell.
Update: Included the pictures of the safe included with his detention memo, as well as earnings reports from Sladkov’s computer. Note the detention memo says the latter came from an ISP.





Good Morning EW,
If this case has been percolating along for awhile now, do you think the timing of the extradition is in any way linked to applying pressure on Putin either related to cracking down on Russia’s safe haven for ransomware attacks or perhaps to create some leverage on Ukraine?
Or is the timing of the extradition entirely coincidental to other U.S. / Russia issues?
Putin has been rattling his saber lately. From a diplomatic point of view, now would be a good moment to suggest to him that he has vulnerabilities which could leave him exposed to serious consequences for any moves he might make.
rattles- a usual summer Wednesday of back yard gardening there are four fighters heading toward the coast… back from morning walk, counted six…
Need see this as more than saber rattling. Putin is wagging the dog at home right now because the pandemic makes it clear he’s useless as a leader; he needs to change the subject and to take advantage of his long-term destabilization of NATO countries while he still has healthy troops. He has a very narrow window of opportunity to stir shit and obtain his objectives which includes Ukraine as a buffer zone.
Everyone bitching about the U.S. not providing the globe with unfettered access to IP needs to chill the fuck out. This is the scenario I suspect some people predicted would happen: Russia’s homegrown vaccine is ineffective for Omicron, as are other non-mRNA vaccines. Without a secure infrastructure to manufacture and dispense mRNA vaccines, there would be rampant theft to obtain mRNA for Russian troops. Tight IP control may be a key means to slow ramp up of Russian military at Ukraine’s border.
Yea, agree. Depressing and distressing because it’s a rock vs a hard place for sure, since there’s no new Iron Curtain going to fall on Sleepy Joe’s watch.
https://www.nytimes.com/2021/12/21/world/europe/russia-military-putin-kremlin.html
Unfortunately vladimir vladimirovich is a resourceful fellow. The man is a cornered rat and right up against it, reminds of Jimmy Cagney at the end of White Heat — dangerous guy with nothing to lose, and he’s trading on it. But even if things end badly West has to hold the line, because vlad don’t own the young Ukrainians. Not yet anyway
https://www.youtube.com/watch?v=OjzKiEs_pHI
Re: Putin, words like “Short, victorious war” come to mind. Hopefully someone in Russia knows better.
Short victorious war in the dead of winter with troops sickened by viral plague. Way to set up the next Russian revolution.
I see Navalny tweeted about the media situation in Russia looking very Fox+Newsmax about the glorious leader. Except the truth finds a way.
Would like to know what intelligence did with “Putin’s Wallet” once they arrived in Portugal. It’d be unfortunate if sanctions found said wallet, hmm?
Well done…
Putin is a killer, period.
Putin has one goal.
To implode America as the old KGBer knows what destroyed the Soviets..
Stupidity…
We are not immune from “the stupid 101.”
Trump won an election with the assistance of a foreign adversary, in the oil business.
Russia sent 27 million to death to defeat the Nazis.
Patton was correct about Russia as Ike was about US.
It can’t be a response to Russia’s pressure. He was arrested in March, possibly only because he went to Switzerland on a trip, possibly vacation. It just took this long for the extradition to go through (and somehow his attempt to appeal a second time was shortchanged, so it actually could have dragged on).
I do find it interesting that the complaint was obtained 9 days after Garland took over, but that, too, could just be a matter of opportunism tied to his trip to an extradition jurisdiction.
Thanks for the clarification, I appreciate it!
Holy shit. Never take a ski trip…you might end up in a cell in Boston, of all places?
Russians and Americans have been doing a lot more than skiing in Switzerland since WWI. Ask Allen Dulles. But it’s pretty amazing that a long-arm statute allows a defendant to be prosecuted in a jurisdiction solely because it is home to a VPN’s internet server. FFS. If only states would use the same approach for obtaining jurisdiction over tax cheats.
Has any link arisen, GRU to Wikileaks?
If both companies reported discovering the hack at the same time, that strongly suggests one of the following scenarios:
1. An exploit became public and their IT department discovered the breach.
2. An IT vendor (e.g. Microsoft) noticed something wonky and tipped them off.
3. The NSA (or other govt agency) was watching the attackers and tipped them off.
I’m really curious which one it is in this case.
The only big public reveal that I recall from January 2020 was the Citrix vulnerability that got a lot of play because the Census Bureau got hacked with that one.
Yeah, I was trying to think back to whether there was an exploit. They don’t say much about what it was, besides basic phishing.
I think it’s also possible that F1 realized they were hacked, which led FBI to ask F2 whether they had been.
For a sense of how much money is in that safe, a ream of paper has 500 sheets. Conservatively, one of those shrink wrapped packs of $100 bills is $50,000, meaning the safe on the right has over a million bucks in it, possibly a lot more.
It’s possible they’ve padded those stacks with smaller bills. But that’s still a lot of cash in one place. You can see why laundering becomes so important. Physically handling and storing that kind of cash becomes really hard.
“You can see why laundering becomes so important. Physically handling and storing that kind of cash becomes really hard.”
Donald Trump believes that’s why God created casinos. But even there, he couldn’t get it right. Bankruptcy in the casino business takes a certain talent.
You shut down money laundering operations once you’ve met a target or people are getting suspicious.
In his case, too dim to understand how businesses work, even if he was laundering money.
The same kind of talent required to bankrupt not one, but three consecutive oilfield services companies during an unprecedented oil boom. That’s what his Republican predecessor did.
Looks like newly minted US Attorney Rachel Rollins is going to have an opportunity to show us all what she can do. I don’t believe she is going to look at this as a low-level, victimless crime the way some might want her to.