YouGov has a poll showing that “belief in conspiracy theories largely depends on political identity.” For example, it shows that Republicans believe Obama is Kenyan.
It focuses on several things it considers conspiracy theories tied to this election, including pizzagate, millions of alleged illegal votes, and claims about the Russian hack.
Interestingly, it shows that half of Clinton voters believe that Russia tampered with vote tallies to get Trump elected, in spite of the White House’s assurances that did not happen.
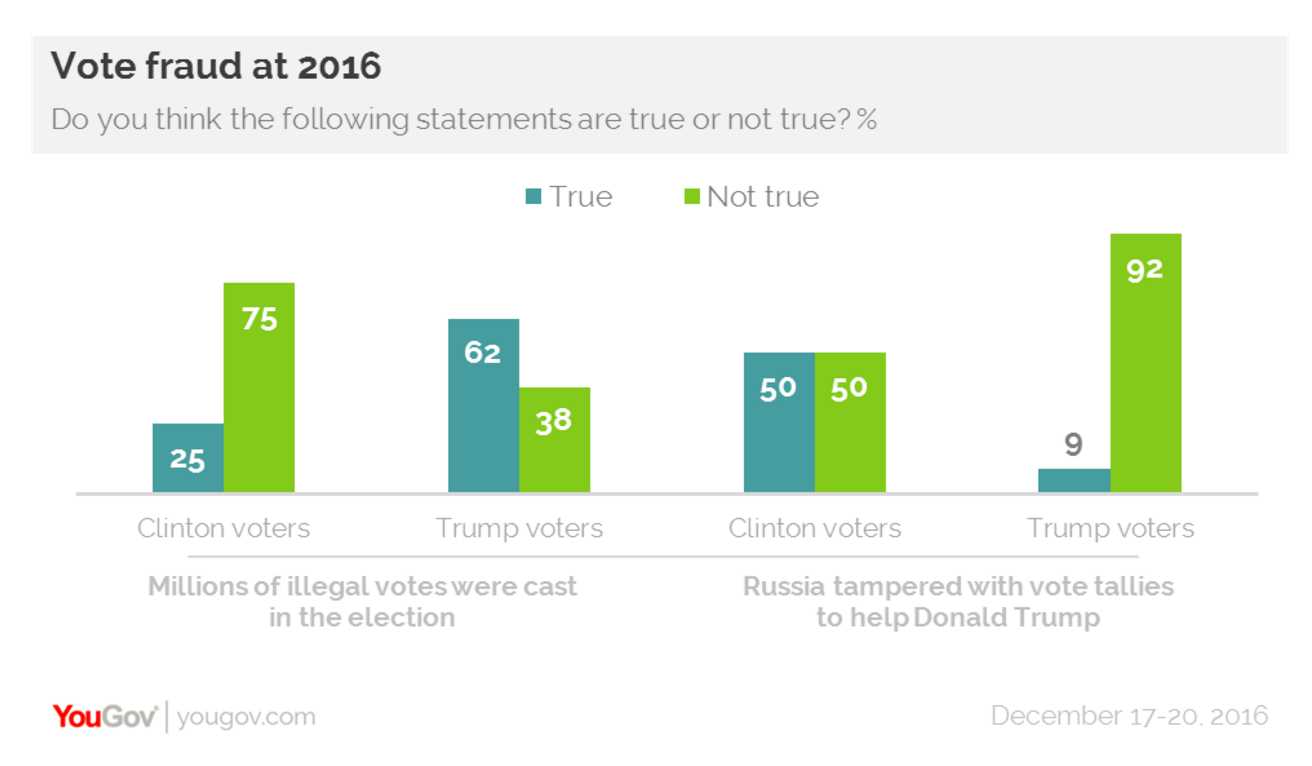
It’s the other tested question about Russian hacking that strikes me as more curious. 87% of Clinton voters believe Russia hacked Democratic emails “in order to help Donald Trump,” whereas only 20% of Trump voters believe that.
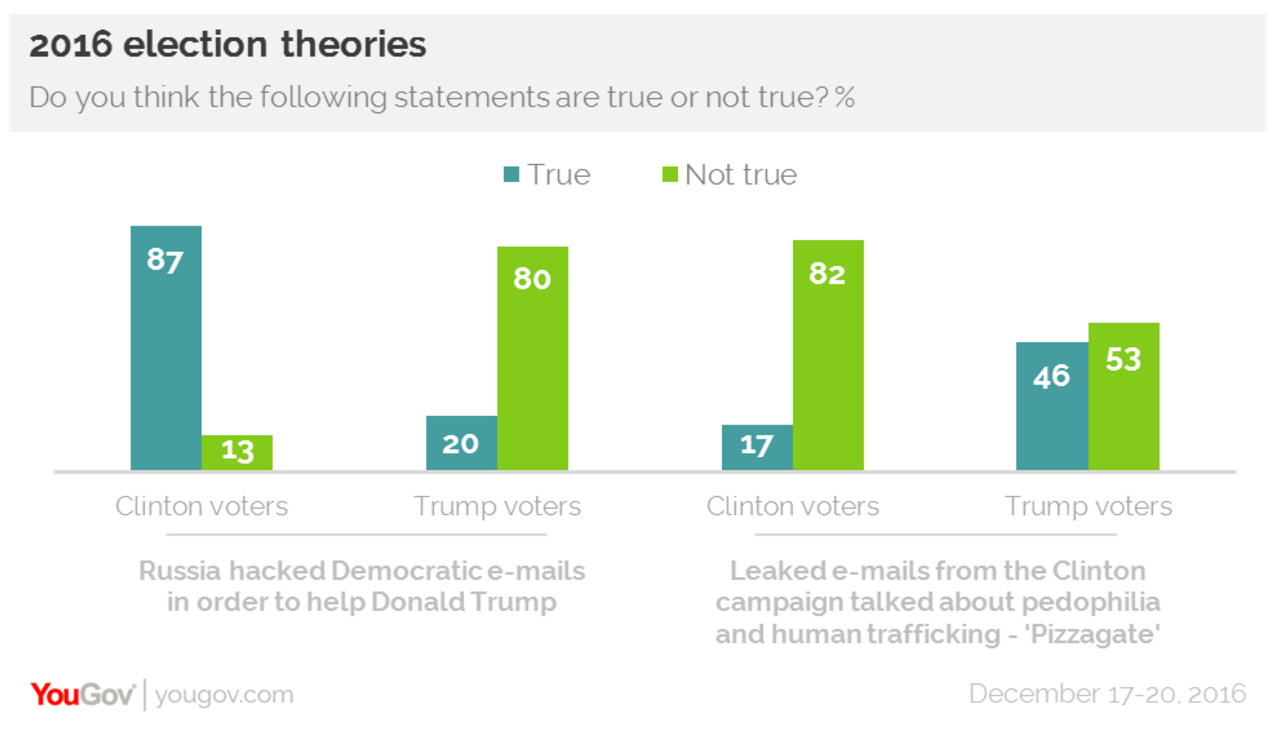
That’s about the result I’d expect. But to explain why this is a conspiracy theory, YouGov writes,
Similarly, even after the Central Intelligence Agency and the Federal Bureau of Investigation reported that Russia was responsible for the leaks of damaging information from the Democratic National Committee and the Clinton campaign and that the hacking was done to help Donald Trump win the Presidency, only one in five say that is definitely true, about the same percentage as believe it is definitely not true.
So YouGov bases this “truth” on a claim that the CIA and FBI “reported that Russia was responsible for the leaks … and that the hacking was done to help Donald Trump win the Presidency.”
Except there has been no such report, not from CIA and FBI, anyway.
There was an official report finding that,
The U.S. Intelligence Community (USIC) is confident that the Russian Government directed the recent compromises of e-mails from US persons and institutions, including from US political organizations. … These thefts and disclosures are intended to interfere with the US election process.
That is, the official report stated that the hack was “intended to interfere with the US election process;” it did not say the hack was done to help Trump.
Moreover, while the report speaks for the entire IC (including the FBI), the report itself came from DHS and ODNI, not FBI or CIA.
It is absolutely true that anonymous leakers — at least some of whom appear to be Democratic Senate sources — claim that CIA said the hack happened to get Trump elected. It is also true that anonymous sources passed on the substance of a John Brennan letter that said in separate conversations with Jim Comey and James Clapper, each agreed with Brennan about the purpose of the hack, which WaPo edited its previous reporting to say included electing Trump as one of a number of purposes, but that’s a third-hand report about what Jim Comey believes.
But that was not an official report, not even from CIA. Here’s what John Brennan said when interviewed about this topic by NPR’s Mary Louise Kelly:
You mentioned the FBI director and the director of national intelligence. And NPR confirmed with three sources that after the three of you meeting last week, you sent a memo to your workforce and that the memo read: There is strong consensus among us on the scope, nature and intent of Russian interference in our presidential elections. Is that an accurate quote from your memo?
I certainly believe that, that there is strong consensus.
Was there ever not?
Well, sometimes in the media, there is claims, allegations, speculation about differences of view. Sometimes I think that just feeds concerns about, you know, the strength of that intelligence and …
And in this case it was reports of tension between FBI and CIA …
… and differences of view. And I want to make sure that our workforce is kept as fully informed as possible so that they understand that what we’re doing, we’re doing in close coordination with our partners in the intelligence community. And so I try to keep my workforce informed on a periodic basis. But aside from whatever message I might have sent out to the workforce, there is, I strongly believe, very strong consensus among the key players — but not just the leaders of these organizations, but also the institutions themselves. And that’s why we’re going through this review. We want to make sure that we scrub this data, scrub the information and make sure that the assessment and analysis is as strong and as grounded as it needs to be.
That quote I read you about the memo that you sent mentioned that there is agreement on scope, nature and intent of Russian interference. And intent is the one that’s been controversial recently, the question of motive. How confident are you in the intelligence on that? It seems like proving motive is an infinitely harder thing than proving that somebody did something. The “why” is tough.
I will not disagree with you that the why is tough. And that’s why there needs to be very careful consideration of what it is that we know, what it is that we have insight into and what our analysis needs to be. But even back in early October when Jim Clapper and Jeh Johnson put out this statement, it said “the intent to interfere in the election.” Now, there are different elements that could be addressed in terms of how it wanted to interfere. And so that’s why this review is being done to make sure that there is going to be a thorough look at the nature, scope and intent of what transpired.
What’s been reported is that the CIA has concluded the intent was to interfere with the election with the purpose of swinging at Donald Trump. Is that an accurate characterization?
That’s an accurate characterization of what’s been appearing in the media. Yes.
Is it an accurate characterization of where the CIA is on this?
Well, that’s what the review is going to do. And we will be as forward-leaning as the intelligence and analysis allows us to be, and we will make sure that, again, President Obama and the incoming administration understands what the intelligence community has assessed and determined to have happened during the run-up to this election.
Why not confirm that that’s where the CIA is on this? Why not confirm if you have the evidence that you believe is …
Because I don’t work for NPR, Mary Louise. I work for the president, I work for the administration, and it is my responsibility to give them the best information and judgment possible.
That is, the CIA Director specifically avoided stating what he or his agency believes the motive to be, deferring to the ongoing review of the evidence, something that Obama also did in his press conference earlier this month.
Q Mr. President, I want to talk about Vladimir Putin again. Just to be clear, do you believe Vladimir Putin himself authorized the hack? And do you believe he authorized that to help Donald Trump? And on the intelligence, one of the things Donald Trump cites is Saddam Hussein and the weapons of mass destruction, and that they were never found. Can you say, unequivocally, that this was not China, that this was not a 400-pound guy sitting on his bed, as Donald Trump says? And do these types of tweets and kinds of statements from Donald Trump embolden the Russians?
THE PRESIDENT: When the report comes out, before I leave office, that will have drawn together all the threads. And so I don’t want to step on their work ahead of time.
What I can tell you is that the intelligence that I have seen gives me great confidence in their assessment that the Russians carried out this hack.
None of that is to say that CIA and (perhaps to a lesser extent) FBI don’t think Russia hacked Democrats to help Trump, as one of several — probably evolving over the course of the election — reasons. CIA surely does (but then it has a big incentive to downplay the most obvious motivation, that Russia was retaliating for perceived and real CIA covert actions against it). FBI probably does.
But there has been no “report” that they believe that, just anonymous reports of reports. The official stance of the Executive Branch is that they’re conducting a review of the evidence on this point.
Perhaps if YouGov wants to test conspiracy theories, it should start by sticking to topics about which there aren’t a slew of anonymous leaks and counter-leaks contravened by public deferral?