As We Face Our Current Emergency Let’s Not Forget How (and Who) Our Last One Contributed to This One
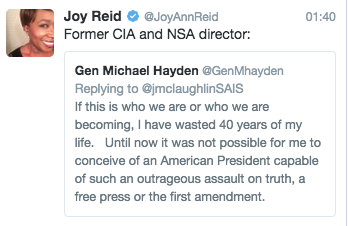
All over Twitter yesterday, people introduced this Michael Hayden tweet decrying Trump’s “assault on truth, a free press or the first amendment” by emphasizing that he served as CIA and NSA Director.
They seem to forget that, in the name of supporting expansive executive authority, Hayden lied to Congress, targeted Thomas Drake for his unclassified communications with the press about Hayden’s support for profiteering contractors, and attacked journalists who have covered the Snowden leaks.
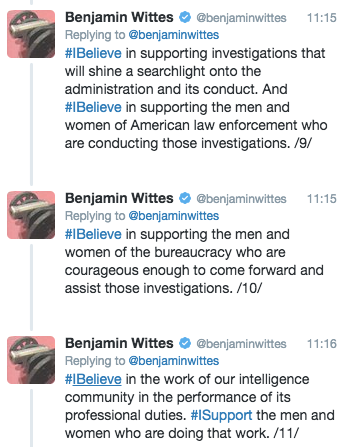
Also on Twitter, Ben Wittes wrote a long thread, advocating that “Americans do not need to be actively contesting right now across traditional left-right divisions” so long as “Americans of good faith collectively band together to face a national emergency.”
In a thread that singles out the First Amendment (though not, predictably, the Fourth), Wittes imagines two main entities that might conduct investigations into Trump: law enforcement and “men and women of the bureaucracy who are courageous enough to come forward and assist,” though he follows quickly with a generalized profession that this non-partisan truce he has unilaterally declared also involves supporting the spooks.
Having declared a truce on “important foreign policy questions,” he then emphasizes we have to keep our promises abroad.
And also we have to keep promises about rights.
The two, together, have set off a debate about what our national emergency really is — where Trump came from.
Remarkably, I’ve seen few pointing back to this remarkable Adam Serwer piece on the whiteness that got Trump elected. As he lays out, Trump got elected because white voters cared more about restoring “traditional” race, sex, and class roles than about all the horrible things Trump espoused.
Trump’s great political insight was that Obama’s time in office inflicted a profound psychological wound upon many white Americans, one that he could remedy by adopting the false narrative that placed the first black president outside the bounds of American citizenship. He intuited that Obama’s presence in the White House decreased the value of what W. E. B. Du Bois described as the “psychological wage” of whiteness across all classes of white Americans, and that the path to their hearts lay in invoking a bygone past when this affront had not taken place, and could not take place.
That the legacy of the first black president could be erased by a birther, that the woman who could have been the first female president was foiled by a man who confessed to sexual assault on tape—these were not drawbacks to Trump’s candidacy, but central to understanding how he would wield power, and on whose behalf.
Americans act with the understanding that Trump’s nationalism promises to restore traditional boundaries of race, gender, and sexuality. The nature of that same nationalism is to deny its essence, the better to salve the conscience and spare the soul.
Serwer’s piece is absolutely required reading.
But his exposition largely focuses on the domestic aspect of white supremacy. This paragraph is one of the few that focuses on the last emergency people like Wittes and Hayden screamed un-self critically about, the never-ending war on terror.
In the meantime, more than a decade of war nationalism directed at jihadist groups has shaped Republican attitudes toward Muslims—from seeing them as potential Republican voters in the late 1990s to viewing them as internal enemies currently. War nationalism always turns itself inward, but in the past, wars ended. Anti-Irish violence fell following the service of Irish American soldiers in the Civil War; Germans were integrated back into the body politic after World War II; and the Italians, Jews, and eastern Europeans who were targeted by the early 20th century’s great immigration scare would find themselves part of a state-sponsored project of assimilation by the war’s end. But the War on Terror is without end, and so that national consolidation has never occurred. Again, Trump is a manifestation of this trend rather than its impetus, a manifestation that began to rise not long after Obama’s candidacy.
And there’s no mention of white supremacy’s foreign counterpart, American exceptionalism, which has long led (white male) Americans to believe America had somehow earned its wealth and prestige without, at the same time, hurting the well-being of others around the world, one which has made Trump’s instinct to demand capitulation from other countries so popular.
Both are, after all, about assuming the capitulation of brown people is the natural order we deserve, whether in our neighborhoods or on the other side of the world.
I raise all this because, in addition to the whiteness problem Serwer lays out, I do think the exceptionalism and expansive executive power that Hayden and Wittes have championed are part of what created this emergency as well. Those who created and sustained that last emergency — those who insisted we needed exceptional measures the last time, exceptional measures that gave Trump far more tools with which to violate norms and persecute enemies — want us to divorce this emergency from their own actions that contributed to it and may make it harder to recover from.
By all means, those who newly admit problems with expansive executive power are welcome to join those of us who’ve long been fighting it. But I’m not sure why everyone wants them to take the lead.