After Trump Spent Four Years Inviting Russia to Hack the US, Russia Allegedly Did Just That
Yesterday, Reuters revealed that the same vulnerability used to steal FireEye’s Red Team tools was also used to spy on Treasury and Commerce’s National Telecommunications and Information Administration, which administers the Internet. Then WaPo revealed that Russia’s APT 29 hacking group is believed to be behind the compromise. Multiple outlets — including FireEye itself — revealed that the hack had used a vulnerability in SolarWinds IT monitoring software identified in the spring. FireEye explains the hack has targeted, “government, consulting, technology, telecom and extractive entities in North America, Europe, Asia and the Middle East,” (presumably reflecting what they’ve seen in their clients as they respond to their own compromise). And CISA issued an emergency directive aiming to stem the damage in agencies beyond just Treasury and NTIA (among SolarWinds’ other US government clients are DOJ and two nuclear labs, as well as Booz Allen, which might as well be US government). Later today, Reuters confirmed that DHS had also been targeted. State, NIH, and parts of the Pentagon have also been targeted.
Let me make clear before I start that thus far, this is nation-state spying, without the kind of sabotage we’ve seen from Russia in the past (if it is indeed Russia). Russia would do what they did with this vulnerability with or without Trump in office (indeed, I have a suspicion their overt hacks of the US will go up under President Biden, mostly because Trump didn’t need any help damaging the US government). While the full scope of the victims is not yet known, it’s quite clear that hackers targeted a slew of entities, governmental and not, with this campaign. So having Trump in office in no way created this campaign nor chose the target.
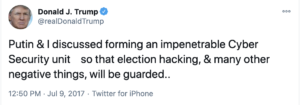
Nevertheless, it is the case that the President of the United States, as a policy matter, has gone to great lengths to make it easier for Russia to minimize the costs of hacking the US.
Almost four years ago, Mike Flynn called up the Russian Ambassador and asked him not to box the Trump Administration in in the wake of President Obama’s effort to hold Russia accountable for interfering in our elections, in part by hacking multiple participants in it, from both parties. Vladimir Putin complied with Flynn’s request, taking no steps in response. Not only did Sergey Kislyak make sure Flynn knew that his request had played a key role in Putin’s decision, but he told Flynn that the Trump Administration and Russia were on the same side, targeted by sanctions aiming to incur a cost for Russia’s actions. “I just wanted to tell you that we found that these actions have targeted not only against Russia, but also against the president elect.”
Well before Kislyak had suggested to the 30-year intelligence veteran that Russia and Trump were on the same side against establishment America, Flynn had already taken steps to hide his actions, perhaps because some Transition members, like Marshall Billingslea, objected to the pre-inauguration outreach to Russia.
When the whole thing got leaked to the public, Flynn lied even to the Vice President-Elect about his outreach.
But Trump appears to have been in on the secret. “The boss is aware” of Kislyak’s earlier requests of the Administration, Flynn told Kislyak on December 31, 2016. Indeed, Flynn made the first call that he would later lie about from Mar-a-Lago, while Flynn, “worked all day with trump from Mara lago,” as KT McFarland bragged in real time.
When the FBI interviewed Flynn about those calls a month later, he lied about the requests he had made of Russia. But he appears to have told a remarkable truth about one thing. “With regard to the scope of the Russians who were expelled,” from the US in retaliation for interfering in a US election, the FBI agents who interviewed him wrote, “FLYNN said he did not understand it. FLYNN stated he could understand one [diplomat expelled as a persona non-grata], but not thirty-five.” General Flynn, a thirty year veteran, thought an appropriate response to a systematic assault on American democracy was to kick out one suspected spy.
Months later (though this would not be revealed until years later), the newly installed President would make it clear he agreed with his short-lived National Security Advisor. In his first face-to-face meeting with representatives from Russia as President on May 10, 2017, President Trump told Foreign Minister Sergey Lavrov that he was unconcerned about Russian interference in the election that had made him President, because the US had historically done the same in other countries. Trump’s officials would take efforts to hide the most embarrassing aspects of that meeting (including that Trump shared highly sensitive Israeli intelligence with the Russians), first by altering the MemCon of the meeting and then having Trump’s new National Security Advisor, HR McMaster, give, “a misleading account of what happened during TRUMP’s meeting with LAVROV.” And Russia would have known that Trump and McMaster were lying.
Before Trump would tell Russia, to their face, that he didn’t much mind that Russia had hacked American democracy, he started dismantling the United State’s ability to prevent further hacks. That started with an effort to prevent the FBI from investigating why Flynn had reached out to Russia to undermine sanctions and (as a sentencing memo approved by Bill Barr’s DOJ would later explain) who ordered him to do so. The day Trump learned the FBI had interviewed Flynn, he asked FBI Director James Comey for loyalty. Then, after Trump fired Flynn — ostensibly for lying to the Vice President — he then privately asked the FBI Director to, “let[] this thing go, to let[] Flynn go.” After Comey testified publicly to Congress about the investigation, Trump fired him.
A long line of people would follow Comey out the door, many of them experts on Russia or counterintelligence or cybersecurity. Trump invented reasons in most cases (reasons that, as with Comey, sharply conflicted with his own views about Hillary Clinton). The obvious real reason had to do with retaliation for investigating him. But in those firings and resignations, Trump got rid of numerous people who had long fought Russian organized crime (like Andrew McCabe and Bruce Ohr), and counterintelligence experts like Peter Strzok. Before and after his impeachment, he got rid of other Russian experts like Marie Yovanovitch and Alexander Vindman. Even those who left of their own accord, like Fiona Hill, were demonized for their true testimony under subpoena.
The most remarkable moment came in July 2018, shortly after the Mueller team indicted Russia’s hackers for their attack on our democracy, when Trump met Putin in Helsinki.
Days before the meeting — though possibly after he had been warned the indictment was coming — Trump announced that he and Putin were talking about cybersecurity cooperation.
Then at the actual summit, with Putin displaying Trump like a soggy trophy, Trump sided with Putin’s denials over the US intelligence community in part because of conspiracy theories about the DNC server.
My people came to me, Dan Coats, came to me and some others, they said they think it’s Russia. I have President Putin. He just said it’s not Russia.
I will say this: I don’t see any reason why it would be. But I really do want to see the server but I have confidence in both parties.
I really believe that this will probably go on for a while, but I don’t think it can go on without finding out what happened to the server. What happened to the servers of the Pakistani gentleman that worked on the DNC?
Where are those servers? They’re missing. Where are they? What happened to Hillary Clinton’s emails? 33,000 emails gone, just gone. I think in Russia they wouldn’t be gone so easily.
I think it’s a disgrace that we can’t get Hillary Clinton’s 33,000 emails.
I have great confidence in my intelligence people, but I will tell you that President Putin was extremely strong and powerful in his denial today and what he did is an incredible offer.
He offered to have the people working on the case come and work with their investigators, with respect to the 12 people. I think that’s an incredible offer. Okay? Thank you.
That is, after a lengthy meeting with Putin, Trump simply decided — perhaps because he had to decide — that Russia had not attacked the US at all. His solution, per Putin’s suggestion, was to send people who had been investigating Russian crimes to Russia, something that has gotten people killed in the past.
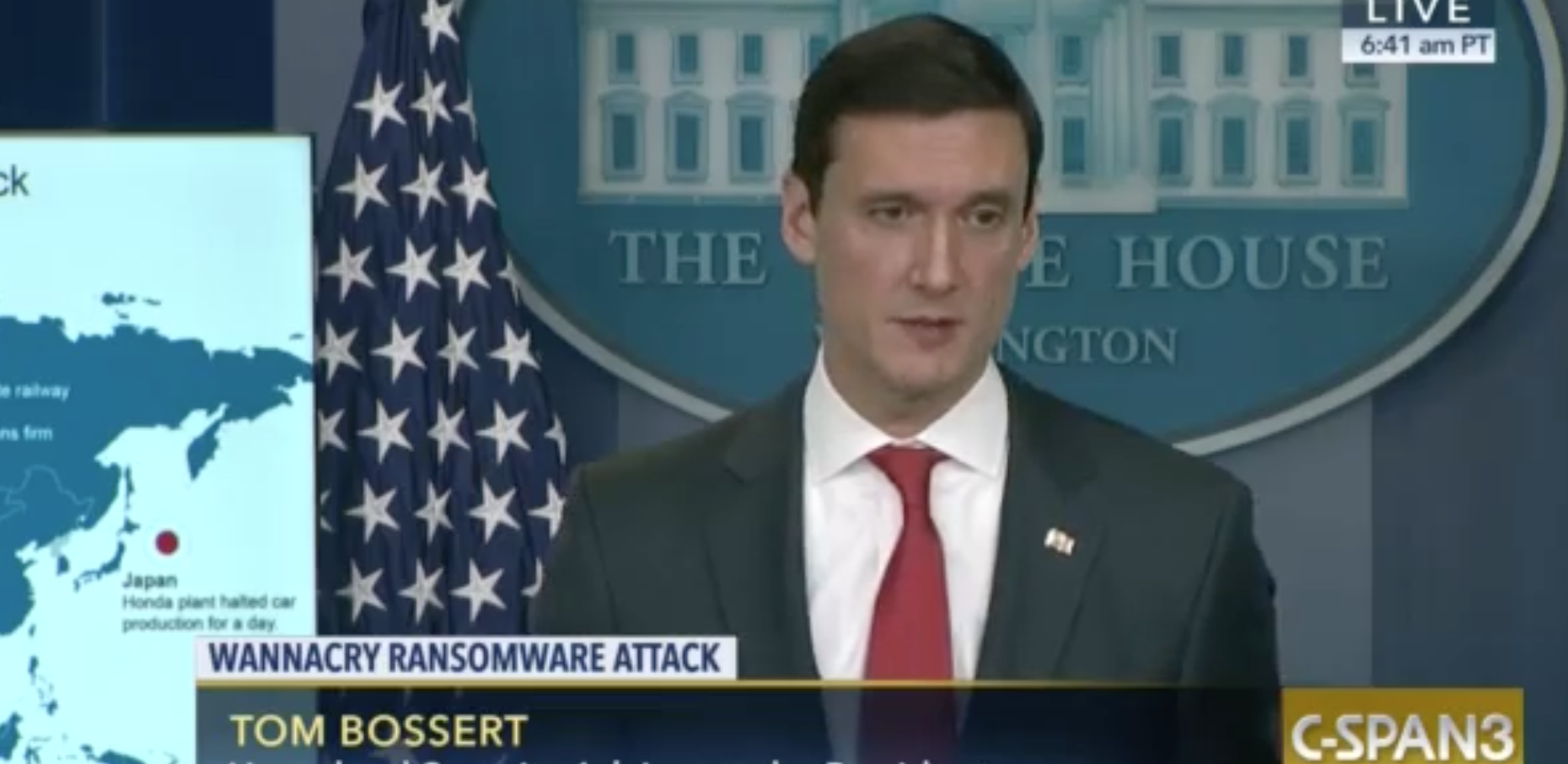
Meanwhile, Trump started dismantling the cybersecurity defenses built up during the Obama Administration. The first day John Bolton started as Trump’s third National Security Advisor, experienced cybersecurity guy Tom Bossert was fired as Homeland Security czar.
President Donald Trump’s homeland security adviser, Tom Bossert, was fired Tuesday as the president’s new national security adviser, John Bolton, consolidates power in the White House.
On Monday night, Bossert was socializing with current and former U.S. Intelligence officials at a conference in Sea Island, Georgia, and a source close to him told NBC News that the adviser was unaware of any intention at the White House to seek his resignation, and that he had no plans to quit.
“New team,” the source said, without further explanation.
Bossert was called in to Bolton’s office early Tuesday morning and told that he was being fired, according to a source with direct knowledge.
Trump’s associates may have figured out that Bossert had provided key details about the events at Mar a Lago in December 2016; he also appears to have provided emails to Mueller’s team that helped them to get those of others like Jared Kushner and Steve Bannon.
Rob Joyce, a top NSA expert, was moved back to the Agency a few months after Bossert left. So even as Bolton was downgrading the pandemic expertise within NSC, he was also eliminating top cybersecurity talent.
That was done because Bolton is a power hungry asshole. But Trump continued eliminating cybersecurity expertise (even beyond that ensuring secure elections) in a fit of pique after the election. At a time when this hack would have already started, Trump fired the head of CISA, Chris Krebs, along with a deputy because they refused to back his conspiracy theories about the election. Politico reported that, in Krebs’ absence, “There is ‘massive frustration with CISA on a sluggish response to agency breaches.'”
Cybersecurity was one area where Trump’s team really was every bit the match of Obama’s — if not better. But Trump fired or removed key people one after another.
Similarly, also in a fit of pique, Trump put one after another unqualified flunky in charge of the entire Intelligence Community, first Twitter troll Ric Grenell and then resume fluffer John Ratcliffe. He did so, in substantial part, because they would ensure that Congress would not get briefed on threats from Russia. He also did so to ensure documents that purportedly undermined the case that he had been elected with Russian help would be released to the public. Under the two men, the government released documents that might have revealed key details about sources and methods to the Russians, both on how they collected on the Russian Embassy and on how quickly the CIA picked up certain pieces of intelligence in summer 2016.
Finally, things have come full circle. After Flynn blew up a perfectly good plea agreement (I’ll show in a few days he still would have been better off with that) largely in the service of making unsubstantiated claims of abuse refuted even by Barr’s DOJ along the way, Barr needed to help him out of the legal pickle and jail time his shitty defense attorney Sidney Powell got him into. As part of that effort, the Attorney General of the United States moved to dismiss the prosecution based off a claim (one that conflicted with a filing submitted by his own DOJ months earlier) that Flynn did nothing wrong by calling up Russia to undermine sanctions imposed, in part, to punish them for a hack. The case was so weak, the team trying to invent excuses for why Flynn shouldn’t be prosecuted for lying to hide his attempts to undermine sanctions on Russia altered documents. And that still didn’t work.
And so, along with a Thanksgiving turkey, Trump pardoned Mike Flynn, his first act of lame duck clemency, for Flynn’s service in protecting Trump from accountability for, himself, undermining those sanctions. Trump came into office telling Russia not to worry about hacking the United States. Trump told them explicitly, to their face, not to worry about hacking the United States. And in pardoning Mike Flynn, Trump made it clear that Russia should not worry — about Trump at least — about hacking the Untied States.
We will presumably get more certainty in days ahead about whether Russia did this hack, as well as the many key targets of it. The real question, however, will be whether Trump will be held accountable for inviting it to happen.
Update: The NYT describes analysis pointing out that Trump continues to sow conspiracy theories about voter fraud while remaining silent about getting pwned by his buddy Putin.
Analysts said it was hard to know which was worse: that the federal government was blindsided again by Russian intelligence agencies, or that when it was evident what was happening, White House officials said nothing.
But this much is clear: While President Trump was complaining about the hack that wasn’t — the supposed manipulation of votes in an election he had clearly and fairly lost — he was silent on the fact that Russians were hacking the building next door to him: the United States Treasury.
Updated with link to Politico and expanded list of targets.
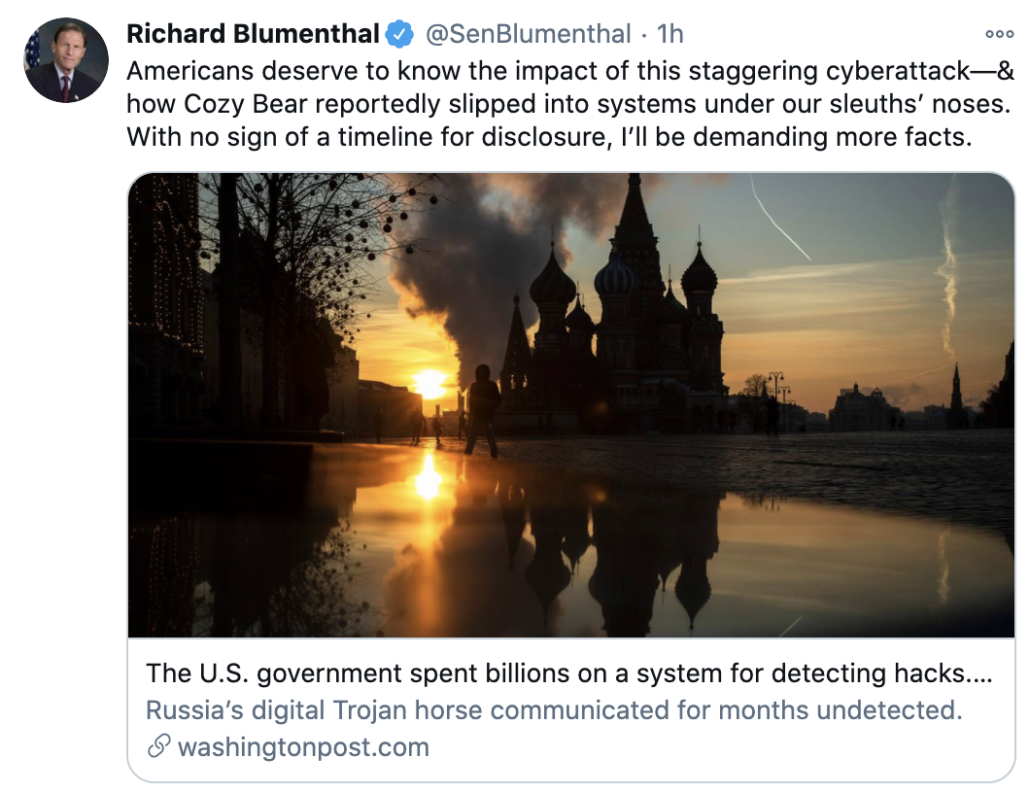
Update: Richard Blumenthal, after attending a classified briefing on this compromise, has repeatedly attributed it to Russia.
Mike Pompeo has similarly stated, as fact, that Russia did it.